1. 引言
Gabizon等人2019年论文《PLONK: permutations over lagrange-bases for oecumenical noninteractive arguments of knowledge》。
相关代码实现有:
- https://github.com/dusk-network/plonk
- https://github.com/barryWhiteHat/plonk_tutorial
- https://github.com/mir-protocol/plonky
- https://github.com/matter-labs/solidity_plonk_verifier
- https://github.com/matter-labs/recursive_aggregation_circuit
- https://github.com/dusk-network/plonk_gadgets
- https://github.com/dusk-network/dusk-blindbid
- https://github.com/Fluidex/awesome-plonk
- https://github.com/Fluidex/plonkit
- https://github.com/zcash/halo2
要点:
(1)与Spartan 中将R1CS中的A/B/C 分别以multilinear多项式表示不同,Plonk中是将circuit中所有门的左侧、右侧和输出分别以多项式 f L , f R , f O f_L,f_R, f_O fL,fR,fO表示。
(2)[BG12]《Efficient zero-knowledge argument for correctness of a shuffle》中的 permutation argument的核心思路为构建双变量多项式:
∏ i = 1 N ( d i − z ) = ∏ i = 1 N ( y i + x i − z ) \prod_{i=1}^{N}(d_i-z)=\prod_{i=1}^{N}(yi+x^i-z) ∏i=1N(di−z)=∏i=1N(yi+xi−z)
利用product argument证明以上关系成立,即完成相应的permutation argument(又称为shuffle argument)。
而Plonk中,是基于lagrange-bases构建的单变量多项式,如test_permutation_compute_sigmas_only_left_wires()测试用例中所示, σ 0 , σ 1 , σ 2 , σ 3 \sigma_0,\sigma_1,\sigma_2,\sigma_3 σ0,σ1,σ2,σ3多项式对应的点值表示满足相应的permutation关系即可:【对应为单变量多项式。】
∏ i = 0 N ( w l i + β ω i + γ ) ( w r i + β ω i + γ ) ( w o i + β ω i + γ ) ( w 4 i + β ω i + γ ) = ∏ i = 0 N ( w l i + β σ 0 ( ω i ) + γ ) ( w r i + β σ 1 ( ω i ) + γ ) ( w o i + β σ 2 ( ω i ) + γ ) ( w 4 i + β σ 3 ( ω i ) + γ ) \prod_{i=0}^{N}(wl_i+\beta\omega^i+\gamma)(wr_i+\beta\omega^i+\gamma)(wo_i+\beta\omega^i+\gamma)(w4_i+\beta\omega^i+\gamma)=\prod_{i=0}^N(wl_i+\beta\sigma_0(\omega^i)+\gamma)(wr_i+\beta\sigma_1(\omega^i)+\gamma)(wo_i+\beta\sigma_2(\omega^i)+\gamma)(w4_i+\beta\sigma_3(\omega^i)+\gamma) ∏i=0N(wli+βωi+γ)(wri+βωi+γ)(woi+βωi+γ)(w4i+βωi+γ)=∏i=0N(wli+βσ0(ωi)+γ)(wri+βσ1(ωi)+γ)(woi+βσ2(ωi)+γ)(w4i+βσ3(ωi)+γ)
circuit wire与 σ i \sigma_i σi之间的permutation关系很巧妙,具体见compute_sigma_permutations()函数。
1)Groth等人2018年论文[GKM+]《 Updatable and universal common reference strings with applications to zk-snarks》,在构建zk-SNARK过程中引入了updatable structured reference string (SRS),扫除了zk-SNARKs实际部署时的一个主要障碍。
2)Maller等人2019年论文[MBKM19]《 Sonic: Zeroknowledge snarks from linear-size universal and updateable structured reference strings》,是第一个可能实用的zk-SNARK,具有fully succinct verification for general arithmetic circuits with such an SRS。但是为了实现fully succinct verification,Sonic方案中构建proof的开销仍然很大。
本文构建的 universal SNARK,具有:
- fully succinct verification
- significantly lower prover running time (fully succinct verifier模式下,group exponentiations的计算量比[MBKM19]少7.5~20倍(具体取决于具体的circuit结构))
与[MBKM19]类似,本文的实现也依赖于 Bayer和Groth 2012年论文[BG12]《Efficient zero-knowledge argument for correctness of a shuffle》中的 permutation argument。【可参见本人系列博客:
- Efficient Zero-Knowledge Argument for Correctness of a Shuffle学习笔记(1)
- Efficient Zero-Knowledge Argument for Correctness of a Shuffle学习笔记(2)
- Efficient Zero-Knowledge Argument for Correctness of a Shuffle学习笔记(3)】
但是,本文专注于 “Evaluations on a subgroup” 而不是 “coefficients of monomials”,因此可简化相应的permutation argument 和 the arithmetization step。
1.1 背景介绍
考虑到zk-SNARKs的实际部署,人们开始关注 可提供 “universal and updatable” 的structured reference string (SRS) 模式。
SRS可用于:
- statements about all circuits of a certain bounded size;
- 在任意时间点,SRS可由新的参与方更新,使得在该时间点的所有updaters中只要由一方是honest的,就可保证整个算法的soundness。
为了简化,本文称具有SRS setup的zk-SNARK为universal的。
同时,若zk-SNARK for circuit satisfiablity 满足以下条件,可称其为fully succinct的:
- 1)preprocessing phase或SRS generation 的run time为quasilinear in circuit size。【其中preprocessing 是指如 [GGPR13] Gennaro等人2013年论文《Quadratic span programs and succinct nizks without pcps》中,允许one-time verifier computation that is polynomial rather than polylogarithmic in the circuit size,从而使得SNARK可用于所有non-uniform circuits,而不仅适于statements about uniform computation。】
- 2)Prover 的 run time为quasilinear in circuit size。
- 3)Proof length为logarithmic in circuit size。【理论上讲,polylogarithmic proof length更自然,但是logarithmic非常好的实现了constant number of group elements,很好的契合了实际使用需求。】
- 4)Verifier 的 run time为polylogarithmic in circuit size。【在很多定义中,仅要求proof size为polylogarithmic,如[GGPR13]中的术语中,若要求proof size为polylogarithmic的同时还要求verifier的run time为polylogarithmic,这样的SNARK是不存在的。】
Maller等人2019年论文[MBKM19]《 Sonic: Zeroknowledge snarks from linear-size universal and updateable structured reference strings》中,第一次实现了a universal fully succinct zk-SNARK for circuit satisfiability——Sonic。
同时在该论文中,提供了Sonic的一个改进版本,可大幅改进Prover的run time,代价是 efficient verification only in a certain amortized sense。
1.2 我们的成果
相比于fully-succint Sonic,我们显著改善了Prover run time。
改进的主要点在于:
- 相比于[BCC+16] Bootle等人2016年《Efficient zero-knowledge arguments for arithmetic circuits in the discrete log setting》,受[MBKM19]中的计算启发,实现了更直接的arithmetization of a circuit。将 permuataion argument 与 单变量evaluations on a multiplicative subgroup 结合,而不是 [MBKM19]中的 coefficients of 双变量多项式。【具体可见本文博客 Efficient Zero-Knowledge Arguments for Arithmetic Circuits in the Discrete Log Setting学习笔记】
简而言之,合理的multiplicative subgroups在很多协议中都很实用,包括Sonic——使用了[BG12]中的permutation argument。
最终,在“grand product argument”中,可reduce为check relations between coefficients of polynomials at “neighbouring monomials”。
若将 x , g ⋅ x x,g\cdot x x,g⋅x看成是neighbour points对,其中 g g g为generator of a multiplicative subgroup of a field F \mathbb{F} F,则将很容易检查不同曲线在这些points对的关系。
还有一个便捷之处是,multiplicative subgroups可与Lagrange bases进行良好交互。如,若 H ⊂ F H\subset \mathbb{F} H⊂F 为a multiplicative subgroup of order n + 1 n+1 n+1,且 x ∈ H x\in H x∈H,则多项式 L x L_x Lx of degree at most n n n that vanishes on H ∖ { x } H\setminus\{x\} H∖{
x} and has f ( x ) = 1 f(x)=1 f(x)=1可以非常稀疏的方式表示为:【因为 X ∈ H X\in H X∈H,而 H H H的order为 n + 1 n+1 n+1,因此有 X n + 1 = 1 X^{n+1}=1 Xn+1=1。】
L x ( X ) = c x ( X n + 1 − 1 ) X − x L_x(X)=\frac{c_x(X^{n+1}-1)}{X-x} Lx(X)=X−xcx(Xn+1−1)
其中 c x c_x cx为常数。
当构建efficiently verifiable [BG12]-形式 的permutation argument时,以这种多项式identities方式表示将是有益的。
1.3 效率分析
将本文的研究成果与现有的non-universal SNARKs和universal SNARKs进行了性能对比。
-
在本文发表时,仅有[MBKM19]的Sonic protocol是fully succinct universal SNARK,Sonic protocol需要做 273 n 273n 273n 次 G 1 \mathbb{G}_1 G1 group exponentiations运算,其中 n n n为乘法门的数量。
在fully-succinct Sonic中,每根线仅可表示三种线性关系,需要额外的“dummy”乘法门来容纳多余三个加法门的线。这将导致乘法门数量的增加,进而会影响Prover的computation estimate。具体可参看[MBKM19]中的详细描述。 -
而本文的universal SNARK需要Prover计算6个polynomial commitments 以及2个opening proofs to evaluate the polynomial commitments at a random challenge point。
Plonk提供了两种模式供用户使用:proof size中增加2个group elements的化,则Prover的总计算量可降低约10%。
The combined degree of the polynomials要么是 9 ( n + a ) 9(n+a) 9(n+a)(对应larger proofs),要么是 11 ( n + a ) 11(n+a) 11(n+a)(对应smaller proofs, reduced verifier work)。其中 n n n为乘法门的数量, a a a为加法门的数量。 -
[Gro16] Groth 2016年论文《 On the size of pairing-based non-interactive arguments》 是当前效率最高fully-succinct SNARK,尽管其需要unique, non-updatable CRS per circuit。[Gro16] 中构建proof的计算量主要有 3 n + m 3n+m 3n+m次 G 1 \mathbb{G}_1 G1 group expoentiations 和 n n n次 G 2 \mathbb{G}_2 G2 group exponentiations组成,其中 m m m为R1CS的变量数, m m m的上限值为 n n n,为简化表述,可假设 m = n m=n m=n。
若假设1次 G 2 \mathbb{G}_2 G2 exponentiation计算量相当于 3 3 3次 G 1 \mathbb{G}_1 G1 exponentiation计算量,则[Gro16]总的计算量相当于 6 n + m 6n+m 6n+m次 G 1 \mathbb{G}_1 G1 group exponetiations计算量。
不过在对这些SNARK方案进行对比之前,需对一些主观假设达成共识。当evaluate common circuits时,其加法门的数量为乘法门数量的两倍,但是,若在某些假设场景下对circuit进行优化,使其不存在加法门时(常见于[Gro16]之类构建的R1CS),其评估表现将更差:【注意,以下对比都是基于所需group exponentiations计算数量。】
- 如极端情况下,对于无加法门,且仅有fan-in-2 乘法门的circuit,本文的universal SNARK proof将需要比[Gro16]多约1.1倍的prover work,而比Sonic少约30倍的prover work。
- 若 a = 2 n a=2n a=2n,即加法门数量为乘法门数量的2倍时,本文的universal SNARK proof需要比[Gro16]多约2.25倍的prover work,需要比Sonic少约10倍的prover work。
- 若 a = 5 n a=5n a=5n,即加法门数量为乘法门数量的5倍时,本文的universal SNARK proof需要比[Gro16]多约3倍的prover work,需要比Sonic少约5倍的prover work。
同时,在fast模式下,Plonk中structured reference string的degree与circuit中门数量相等,其SRS size实现了有效reduction。
当对比proof construction时,由于构建proof中所需的FFT数量是non-trivial的,因此还考虑Plonk中的field multiplications数量。
其它的succint universal SNARK也需要较高的FFT计算开销,考虑到这些开销不易对比,因此在下图中,未包含关于FFT的计算开销对比:

有定性分析指出,FFT的开销略低于 G 1 \mathbb{G}_1 G1 group exponentiations开销。
而Verifier对每个proof的验证开销对比如下图所示:【基于the simple strucuture of the committed prover polynomials,实际Verifier仅需要2次bilinear pairing 运算。此外,每次pairing计算中的 G 2 \mathbb{G}_2 G2元素是固定的,因此可通过[CS10] Costello等人2010年论文《Fixed argument pairings》 的方案进行优化,实现reduce pairing computation time by 约30%。】

实际基于BN254曲线的性能bench为:

甚至对于百万级门数量的circuit,Plonk可在消费者级别的硬件设备上在23秒内生成相应的proof。这大幅改进了universal SNARKs的效率,使其可广泛用于实际各种用户场景下。
circuit preprcessing为一次性计算,实现将每个program 编码成 一个Plonk circuit。在该步骤中,将生成polynomial commitments to the “selector” polynomials required to verify proofs。
当构建proofs时,计算FFT所需的时间 与 进行elliptic curve scalar multiplications的时间 是相当的。上表1中的field multiplication数量是从8次 FFT of size 4 n 4n 4n、5次 FFT of size 2 n 2n 2n 以及 12 12 12次 FFT of size n n n 中提取的。
当cicuit的preprocessed polynomials are provided as evaluations over the 4 n 4n 4n'th root of unity (而不是Lagrange-base form)时, F F T FFT FFT运算数量可进一步reduce,但是这将大幅增加构建proof所需的信息量,因此在本文的benchmark中未考虑该优化。
1.4 同期研究成果对比——randomized sumcheck方案、Fractal/Marlin
粗略地说,所有的succinct proving system都是通过使用randomness来将多个constraint check压缩为1个。常见的压缩做法是:take a random linear combination of the constraints。
在R1CS和其它类似系统中,待压缩的相对较困难的contraints为:
linear relations between the system variables,即形如 < a ⃗ i , x ⃗ > = 0 <\vec{a}_i, \vec{x}>=0 <ai,x>=0的contraints,其中 x ⃗ ∈ F m \vec{x}\in\mathbb{F}^m x∈Fm为系统变量, a ⃗ i ∈ F m \vec{a}_i\in\mathbb{F}^m ai∈Fm表示其中的一个constraint。
这类似于circuit satisifiability statement中形如 x i = x j x_i=x_j xi=xj的“wiring constraints”,如 x i x_i xi表示gate G G G的输出线, x j x_j xj表示由gate G G G到另一个gate G ′ G' G′的输入线。
A random linear combination of linear constraint的形式为:
∑ i ∈ [ n ] r i < a ⃗ i , x ⃗ > = 0 \sum_{i\in[n]}r^i<\vec{a}_i,\vec{x}>=0 ∑i∈[n]ri<ai,x>=0
其中 r ∈ F r\in\mathbb{F} r∈F。
忽略一些技术细节,在[MBKM19]和后续的[Gab19] Gabizon 2019年论文《Auroralight:improved prover efficiency and SRS size in a soniclike system》【基于[BCR+19] Ben-Sasson等人2018年论文《 Aurora: Transparent succinct arguments for R1CS》】将上述check reduce为 evaluate a degree n n n bivariate S S S at a random point,使得 S S S的非零单项式数量与contraint vectors { a ⃗ i } i ∈ [ n ] \{\vec{a}_i\}_{i\in[n]} { ai}i∈[n] 中的非零元素数相等。在这方面,[MBKM19]采用了更聪明的策略来amortize the cost of many evaluations of S S S across many proofs。[MBKM19]中的方式Prover效率更高,但是无法实现fully succinct,因为需要Verifier自身来计算至少1个evaluation of S S S。
阻碍Sonic(以及[Gab19])具有more prover efficiency + fully succinct 属性的技术难点在于:
需要一种方法来实现efficiently verify an evaluation S ( z , y ) S(z,y) S(z,y) in the case S S S 仅包含 O ( n ) O(n) O(n)个 non-zero 单项式。
在最近同期的研究成果中,采用的解决方案为借助“Lagrange Basis”:
- Fractal:[COS19] Chiesa等人2019年论文《Fractal: Post-quantum and transparent recursive proofs from holography》。Fractal 针对的是transparent recursive SNARKs,使用的是sparse bi-variate evaluation技术。
- Marlin:[CHM+19] Chiesa等人2019年论文《Marlin: Preprocessing zksnarks with universal and updatable SRS》。Marlin 关注的是实现fully succinct (universal) SNARK,与本论文的目标一致。
特别地,假设 H , K H,K H,K为multiplicative subgroups of size O ( n ) O(n) O(n) of F \mathbb{F} F,使得 S S S仅有 M M M个非零值 on H × K H\times K H×K;然后[CHM+19]和[COS19]中制定了一种协议来 convince a succinct verifier that S ( z , y ) = t S(z,y)=t S(z,y)=t where the prover’s work is linear in M M M。解决该问题的一个直观做法是将[KZG10] Kate等人2010年论文《Constant-size commitments to polynomials and their applications》 generalize为 a bi-variate polynomial commitment scheme,这将需要 O ( n 2 ) O(n^2) O(n2) proving time。
回到Plonk,不需要 “bi-variate evaluation breakthrough” 的主要原因是,Plonk关注的是constant fan-in circuits,而不是R1CS/unlimited addition fan-in。因此Plonk中的linear constraints仅仅是wiring contraints,这些wiring constraints可reduce为a permutation check(具体见本论文第5.2和6章)。
可将[BG12]中的技术理解为:
“linear constraints that correspond to a permutation can be more simply combined than general linear constraints”。
比如,在上述方程式中,每个constraint乘以不同的random coefficient;而在[BG12]的randomization中,在某种意义上,为每个变量值添加相同的random shift就足够了。(详细的permutation protocol见本论文第5章。)
本文的目标和[CHM+19] Marlin的研究目标都是:
fully succinct (universal) SNARK
但是,目前并没有完全直接的方式来对比Plonk和Marlin,原因在于Plonk在具体常熟领域,且两者所使用的basic measure 是不同的。
Plonk中的参数 n n n表示的是fan-in two circuit中的加法和乘法门数量;
Marlin中的主要参数为:the maximal number of non-zeros in one of the three matrices describing an R1CS。
对于相同的 n n n,Plonk的表现优于Marlin,如Prover 的group运算和proof size都将改进2倍。极端情况下,对于只有乘法门的circuit,这将代表Plonk和Marlin的性能表现差异。
但是,对于具有 “frequent large addtion fan-in” constraint system,Marlin的表现将优于 the currently specified variant of Plonk。比如,对于极端情况下的 “fully dense” R1CS constraint:
( ∑ j ∈ [ m ] a j x j ) ⋅ ( ∑ j ∈ [ m ] b j x j ) = ∑ j ∈ [ m ] c j x j (\sum_{j\in[m]}a_jx_j)\cdot(\sum_{j\in[m]}b_jx_j)=\sum_{j\in[m]}c_jx_j (∑j∈[m]ajxj)⋅(∑j∈[m]bjxj)=∑j∈[m]cjxj
其中 a ⃗ , b ⃗ , c ⃗ ∈ F m \vec{a},\vec{b},\vec{c}\in\mathbb{F}^m a,b,c∈Fm具有all non-zero entries。(所有元素均为非零值。)
另外,似乎将Fractal中隐含的思想——上述提及的sparse bi-variate evaluation protocol 嵌入到[Gab19]中,将改进其性能表现,特别是针对可将某些Prover work委托给外部helper的场景。而在Plonk中,不大有机会存在这样的委托,因为Plonk中的wiring is checked on the witness itself,而在[Gab19][CHM+19][COS19] 中,it is in sense checked on the random coefficients of the verifier。
2. 相关术语及约定
2.1 术语
假设field F \mathbb{F} F具有prime order。假设所有的算法中都包含了一个隐含的安全参数 λ \lambda λ。
-
F < d [ X ] \mathbb{F}_{<d}[X] F<d[X] 表示的是一系列单变量多项式over F \mathbb{F} F of degree smaller than d d d。
-
efficient:是指算法的run time为 p o l y ( λ ) poly(\lambda) poly(λ)。
-
object generator O \mathcal{O} O:输入为 λ \lambda λ,且在所有协议运行前执行。输出为all fields and groups used。
本文 O ( λ ) = ( F , G 1 , G 2 , G t , e , g 1 , g 2 , g t ) \mathcal{O}(\lambda)=(\mathbb{F},\mathbb{G}_1,\mathbb{G}_2,\mathbb{G}_t,e,g_1,g_2,g_t) O(λ)=(F,G1,G2,Gt,e,g1,g2,gt),其中:
1) F \mathbb{F} F为prime filed,具有super-polynomial size r = λ w ( 1 ) r=\lambda^{w(1)} r=λw(1)。
2) G 1 , G 2 , G t \mathbb{G}_1,\mathbb{G}_2,\mathbb{G}_t G1,G2,Gt均为groups of size r r r, e e e为an efficiently computable non-degenerate pairing e : G 1 × G 2 → G t e:\mathbb{G}_1\times \mathbb{G}_2\rightarrow \mathbb{G}_t e:G1×G2→Gt。
3) g 1 , g 2 g_1,g_2 g1,g2为uniformly chosen generators 使得 e ( g 1 , g 2 ) = g t e(g_1,g_2)=g_t e(g1,g2)=gt。
通常 λ \lambda λ参数为隐性的,即用 F \mathbb{F} F来代替 F ( λ ) \mathbb{F}(\lambda) F(λ)。
G 1 \mathbb{G}_1 G1和 G 2 \mathbb{G}_2 G2为加法group,具有:
[ x ] 1 : = x ⋅ g 1 [x]_1:=x\cdot g_1 [x]1:=x⋅g1
[ x ] 2 : = x ⋅ g 2 [x]_2:=x\cdot g_2 [x]2:=x⋅g2 -
[ n ] [n] [n]表示整数 { 1 , ⋯ , n } \{1,\cdots,n\} { 1,⋯,n}
-
e.w.p:全称为“except with probability”,即 e.w.p λ \lambda λ 表示 probability at least 1 − λ 1-\lambda 1−λ。
-
universal SRS-based public-coin protocols:是指可借助Fiat-Shamir transform或a random oracle 来实现non-interactive protocols。
proof length是指the total communication of the prover。
本文的SRS可源于:
deterministic p o l y ( λ ) poly(\lambda) poly(λ)-time from an “SRS of monomials” of the form { [ x i ] 1 } a ≤ i ≤ b , { [ x i ] 2 } c ≤ i ≤ d \{[x^i]_1\}_{a\leq i\leq b}, \{[x^i]_2\}_{c\leq i\leq d} { [xi]1}a≤i≤b,{ [xi]2}c≤i≤d for uniform x ∈ F x\in\mathbb{F} x∈F, and some integers a , b , c , d a,b,c,d a,b,c,d with absolute value bounded by p o l y ( λ ) poly(\lambda) poly(λ)。
然后遵循[BGM17] Bowe等人2017年论文《Scalable multi-party computation for zksnark parameters in the random beacon model》中要求SRS can be derived in a universal and updatable setup 仅需one honest participant —— 即若adversary控制了all but one of the participants in the setup does not gain more than a n e g l ( λ ) negl(\lambda) negl(λ) advantage in its probability of producing a proof of any statement。
为了简化,本文将SRS s r s srs srs 作为protocol中的隐性参数而不明确写出。
2.2 Algebraic Group Model (AGM)下的安全分析
本文采用[FKL18] Fuchsbauer等人2018年论文《The algebraic group model and its applications》中的安全分析模式。
在本文协议中,algebraic adversary A \mathcal{A} A in an SRS-based protocol, p o l y ( λ ) poly(\lambda) poly(λ)-time 算法满足如下要求:
- For i ∈ { 1 , 2 } i\in\{1,2\} i∈{ 1,2},任何时候 A \mathcal{A} A输出element A ∈ G i A\in\mathbb{G}_i A∈Gi的同时,还可以输出a vector v ⃗ \vec{v} v over F \mathbb{F} F 使得 A = < v ⃗ , s r s i > A=<\vec{v}, srs_i> A=<v,srsi>成立。
在介绍AGM模式下的安全分析的优点之前,先了解以下术语:
- s r s srs srs 具有degree Q Q Q:若 s r s i srs_i srsi的所有元素都形如 [ f ( x ) ] i [f(x)]_i [f(x)]i for f ∈ F < Q [ X ] f\in\mathbb{F}_{<Q}[X] f∈F<Q[X] and uniform x ∈ F x\in\mathbb{F} x∈F。
后续的协议都对应的是a degree Q Q Q SRS,并以多项式 f i , j f_{i,j} fi,j来表示 s r s i srs_i srsi的第 j j j个元素。 - a ⃗ , b ⃗ \vec{a},\vec{b} a,b 表示vectors of F \mathbb{F} F-elements,algebraic adversary A \mathcal{A} A 输出的相应的encodings in G 1 , G 2 \mathbb{G}_1,\mathbb{G}_2 G1,G2形如: [ a j ] 1 [a_j]_1 [aj]1 表示第 j j j个 G 1 \mathbb{G}_1 G1 element。
- real pairing check是指 a check of the form:
( a ⃗ ⋅ T 1 ) ⋅ ( T 2 ⋅ b ⃗ ) = 0 (\vec{a}\cdot \mathbf{T}_1)\cdot (\mathbf{T}_2\cdot \vec{b})=0 (a⋅T1)⋅(T2⋅b)=0
其中 T 1 , T 2 \mathbf{T}_1,\mathbf{T}_2 T1,T2为矩阵over F \mathbb{F} F。
注意,在已知encoded elements和pairing function e : G 1 × G 2 → G t e:\mathbb{G}_1\times\mathbb{G}_2\rightarrow \mathbb{G}_t e:G1×G2→Gt的情况下,以上check可高效完成。 - ideal check 是指:
A \mathcal{A} A为algebraic的,当他输出 [ a j ] i [a_j]_i [aj]i的同时,还可输出vector v ⃗ \vec{v} v,使得如下线性关系成立:
a j = ∑ v l f i , l ( x ) = R i , j ( x ) a_j=\sum v_lf_{i,l}(x)=R_{i,j}(x) aj=∑vlfi,l(x)=Ri,j(x)
其中 R i , j ( X ) : = ∑ v l f i , l ( X ) R_{i,j}(X):=\sum v_lf_{i,l}(X) Ri,j(X):=∑vlfi,l(X)。
for i ∈ { 1 , 2 } i\in\{1,2\} i∈{ 1,2},the vector of polynomials表示为:
R ⃗ i = ( R ⃗ i , j ) j \vec{R}_i=(\vec{R}_{i,j})_j Ri=(Ri,j)j
从而有相应的ideal check为 checks as a polynomial whether:
( R ⃗ 1 ⋅ T 1 ) ⋅ ( T 2 ⋅ R ⃗ 2 ) ≡ 0 (\vec{R}_1\cdot\mathbf{T}_1)\cdot (\mathbf{T}_2\cdot \vec{R}_2)\equiv 0 (R1⋅T1)⋅(T2⋅R2)≡0
是否成立。
受[FKL18]中对[Gro16]分析的启发,本文发现关注ideal checks就足以完成soundness analysis against algebraic adversaries。
-
首先定义了类似[FKL18]中的Q-DLOG assumption:【即已知 [ 1 ] 1 , [ x ] 1 , ⋯ , [ x Q ] 1 , [ 1 ] 2 , [ x ] 2 , ⋯ , [ x Q ] 2 [1]_1,[x]_1,\cdots,[x^Q]_1,[1]_2,[x]_2,\cdots,[x^Q]_2 [1]1,[x]1,⋯,[xQ]1,[1]2,[x]2,⋯,[xQ]2,找到 x x x的概率可忽略。】
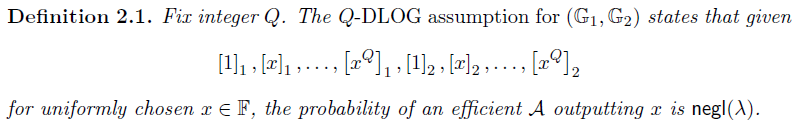
-
由Q-DLOG assumption,推出的lemma:【即real pairing check成立的概率与ideal check成立的概率相当。】
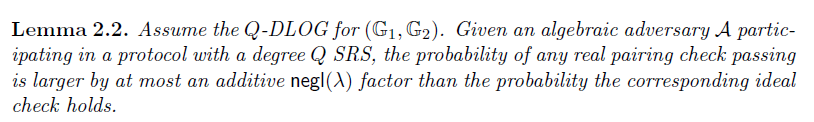
-
Knowledge soundness in AGM 是指:
Prover P P P 和Verifier V V V之间的protocol P \mathscr{P} P for relation R \mathcal{R} R 具有Knowledge Soundness in the Algebraic Group Model的前提条件为——存在efficient E E E使得任意的algebraic adversary A \mathcal{A} A赢得如下游戏的概率可忽略:【又称 KS game】
1) A \mathcal{A} A选择输入值 x x x,并以Prover的角色运行 P \mathscr{P} P with input x x x;
2) E E E可获取 A A A在协议中的所有消息(包括linear combinations的系数),输出 w w w;
3)若同时满足以下情况,则 A A A赢了:
3.a) V V V在协议结束输出 a c c acc acc,即验证通过。且
3.b) ( x , w ) ∉ R (x,w)\notin \mathcal{R} (x,w)∈/R
3. [KZG10]的batch版本
本文协议的关键是实现了:
a batched version of the [KZG10] polynomial commitment scheme【与[MBKM19]中的附录C类似】,以满足 query multiple committed polynomials at multiple points。
接下来以有利于本文协议的方式来定义polynomial commitment schemes,特别地,其中的open流程对应的是a batched setting having multiple polynomials and evaluation points。
d d d-polynomial commitment scheme中包含如下算法:
- g e n ( d ) gen(d) gen(d)——为随机算法,输出为SRS s r s srs srs。
- c o m ( f , s r s ) com(f,srs) com(f,srs)——输入为多项式 f ∈ F < d [ X ] f\in\mathbb{F}_{<d}[X] f∈F<d[X],输出为commitment c m cm cm to f f f。
- P P C P_{PC} PPC和 V P C V_{PC} VPC 之间的public coin protocol o p e n open open,针对的场景为:【具有completness和knowledge soundness in the algebraic group model属性。】
– public info:SRS s r s srs srs, t = p o l y ( λ ) t=poly(\lambda) t=poly(λ),分别对应 f 1 , ⋯ , f t f_1,\cdots,f_t f1,⋯,ft的commitments c m 1 , ⋯ , c m t cm_1,\cdots,cm_t cm1,⋯,cmt,evaluate points z 1 , ⋯ , z t ∈ F z_1,\cdots,z_t\in\mathbb{F} z1,⋯,zt∈F 以及 evaluation values s 1 , ⋯ , s t ∈ F s_1,\cdots,s_t\in\mathbb{F} s1,⋯,st∈F。
– witness:多项式 f 1 , ⋯ , f t ∈ F < d [ X ] f_1,\cdots,f_t\in\mathbb{F}_{<d}[X] f1,⋯,ft∈F<d[X]。
– relations: s 1 = f 1 ( z 1 ) , ⋯ , s t = f t ( z t ) s_1=f_1(z_1),\cdots,s_t=f_t(z_t) s1=f1(z1),⋯,st=ft(zt) 且 c m 1 = c o m ( f 1 , s r s ) , ⋯ , c m t = c o m ( f t , s r s ) cm_1=com(f_1,srs),\cdots, cm_t=com(f_t,srs) cm1=com(f1,srs),⋯,cmt=com(ft,srs)。
3.1 batch open different polynomials at same points
根据[KZG10]和[MBKM19],对以上 d d d-polynomial commitment scheme实例化为:
- g e n ( d ) gen(d) gen(d)——选择随机值 x ∈ F x\in\mathbb{F} x∈F,输出SRS s r s = ( [ 1 ] 1 , [ x ] 1 , ⋯ , [ x d − 1 ] 1 , [ 1 ] 2 , [ x ] 2 ) srs=([1]_1,[x]_1,\cdots,[x^{d-1}]_1,[1]_2,[x]_2) srs=([1]1,[x]1,⋯,[xd−1]1,[1]2,[x]2)。
- c o m ( f , s r s ) : = [ f ( x ) ] 1 com(f,srs):=[f(x)]_1 com(f,srs):=[f(x)]1。
- P P C P_{PC} PPC和 V P C V_{PC} VPC 之间的public coin protocol o p e n open open,首先值考虑 z 1 = ⋯ = z t = z z_1=\cdots=z_t=z z1=⋯=zt=z的情况, o p e n ( { c m i } , { z i } , { s i } ) open(\{cm_i\},\{z_i\},\{s_i\}) open({
cmi},{
zi},{
si})的具体实现为:【即此处考虑的是:open diffierent polynomials at same points。】
a) V P C V_{PC} VPC 发送随机值 γ ∈ F \gamma\in\mathbb{F} γ∈F。
b) P P C P_{PC} PPC 计算:
h ( X ) : = ∑ i = 1 t γ i − 1 ⋅ f i ( X ) − f i ( z ) X − z h(X):=\sum_{i=1}^{t}\gamma^{i-1}\cdot\frac{f_i(X)-f_i(z)}{X-z} h(X):=∑i=1tγi−1⋅X−zfi(X)−fi(z)
并使用 s r s srs srs计算和发送 W : = [ h ( x ) ] 1 W:=[h(x)]_1 W:=[h(x)]1
c) V P C V_{PC} VPC 计算:
F : = ∑ i ∈ [ t ] γ i ⋅ c m i , v = [ ∑ i ∈ [ t ] γ i ⋅ s i ] 1 F:=\sum_{i\in[t]}\gamma^i\cdot cm_i, v=[\sum_{i\in[t]}\gamma^i\cdot s_i]_1 F:=∑i∈[t]γi⋅cmi,v=[∑i∈[t]γi⋅si]1
d)当且仅当如下条件成立时, V P C V_{PC} VPC输出 a c c acc acc:
e ( F − v , [ 1 ] 2 ) ⋅ e ( − W , [ x − z ] 2 ) = 1 e(F-v,[1]_2)\cdot e(-W,[x-z]_2)=1 e(F−v,[1]2)⋅e(−W,[x−z]2)=1
需对以上实现进行knowledge soundness论证,即判断是否存在efficient E E E使得algebraic adversary A \mathcal{A} A取任意的 z = z 1 = ⋯ = z t z=z_1=\cdots=z_t z=z1=⋯=zt赢得 KS game的概率可忽略。详细的分析思路为:【核心思想为Schwartz-Zippel Lemma】

3.2 batch open different polynomials at different points
当考虑:open diffierent polynomials at different points 时:
- 可将其看成是对
open协议的并行执行,即每个open协议对应一个evaluation point和相应的polynomial evaluated at at that point; - 然后引入generic method for batched randomized evaluation of pairing equations。
为了简化,本文将open协议中 z 1 , ⋯ , z t z_1,\cdots,z_t z1,⋯,zt分为两个不同的evaluation points(与本文主协议的实际情况对应)。将相应evaluation points表示为 z , z ′ z,z' z,z′,对应的polynomials数量分别为 t 1 , t 2 t_1,t_2 t1,t2,分别evaluate { f i } i ∈ [ t 1 ] \{f_i\}_{i\in [t_1]} {
fi}i∈[t1] at z z z 以及 evaluate { f i ′ } i ∈ [ t 2 ] \{f_i'\}_{i\in[t_2]} {
fi′}i∈[t2] at z ′ z' z′。
相应的open协议为—— o p e n ( { c m i } i ∈ [ t 1 ] , { c m i ′ } i ∈ [ t 2 ] , { z , z ′ } , { s i , s i ′ } ) open(\{cm_i\}_{i\in[t_1]},\{cm_i'\}_{i\in[t_2]},\{z,z'\},\{s_i,s_i'\}) open({
cmi}i∈[t1],{
cmi′}i∈[t2],{
z,z′},{
si,si′}):
a) V P C V_{PC} VPC 发送随机值 γ , γ ′ ∈ F \gamma,\gamma'\in\mathbb{F} γ,γ′∈F。
b) P P C P_{PC} PPC 计算:
h ( X ) : = ∑ i = 1 t 1 γ i − 1 ⋅ f i ( X ) − f i ( z ) X − z h(X):=\sum_{i=1}^{t_1}\gamma^{i-1}\cdot\frac{f_i(X)-f_i(z)}{X-z} h(X):=∑i=1t1γi−1⋅X−zfi(X)−fi(z)
h ′ ( X ) : = ∑ i = 1 t 2 γ ′ i − 1 ⋅ f i ′ ( X ) − f i ′ ( z ′ ) X − z ′ h'(X):=\sum_{i=1}^{t_2}\gamma'^{i-1}\cdot\frac{f_i'(X)-f_i'(z')}{X-z'} h′(X):=∑i=1t2γ′i−1⋅X−z′fi′(X)−fi′(z′)
并使用 s r s srs srs计算和发送 W : = [ h ( x ) ] 1 , W ′ : = [ h ′ ( x ) ] 1 W:=[h(x)]_1,W':=[h'(x)]_1 W:=[h(x)]1,W′:=[h′(x)]1。
c) V P C V_{PC} VPC 选择随机值 r ′ ∈ F r'\in\mathbb{F} r′∈F。
d) V P C V_{PC} VPC 计算:
F : = ( ∑ i ∈ [ t 1 ] γ i − 1 ⋅ c m i − [ ∑ i ∈ [ t 1 ] γ i − 1 ⋅ s i ] 1 ) + r ′ ⋅ ( ∑ i ∈ [ t 2 ] γ ′ i − 1 ⋅ c m i ′ − [ ∑ i ∈ [ t 2 ] γ ′ i − 1 ⋅ s i ′ ] 1 ) F:=(\sum_{i\in[t_1]}\gamma^{i-1}\cdot cm_i-[\sum_{i\in[t_1]}\gamma^{i-1}\cdot s_i]_1)+r'\cdot (\sum_{i\in[t_2]}\gamma'^{i-1}\cdot cm_i'-[\sum_{i\in[t_2]}\gamma'^{i-1}\cdot s_i']_1) F:=(∑i∈[t1]γi−1⋅cmi−[∑i∈[t1]γi−1⋅si]1)+r′⋅(∑i∈[t2]γ′i−1⋅cmi′−[∑i∈[t2]γ′i−1⋅si′]1)
当且仅当如下条件成立时, V P C V_{PC} VPC输出 a c c acc acc:
e ( F + z ⋅ W + r ′ z ′ ⋅ W ′ , [ 1 ] 2 ) ⋅ e ( − W − r ′ ⋅ W ′ , [ x ] 2 ) = 1 e(F+z\cdot W+r'z'\cdot W',[1]_2)\cdot e(-W-r'\cdot W',[x]_2)=1 e(F+z⋅W+r′z′⋅W′,[1]2)⋅e(−W−r′⋅W′,[x]2)=1
以上[KZG10] batch版本的算法效率分析如下:
- 对于 n ≤ d n\leq d n≤d且 f ∈ F < n [ X ] f\in\mathbb{F}_{<n}[X] f∈F<n[X]时,计算 c o m ( f ) com(f) com(f)需要 n n n次 G 1 \mathbb{G}_1 G1-exponentiations运算。
- 已知 z ⃗ : = ( z 1 , ⋯ , z t ) ∈ F t , f 1 , ⋯ , f t ∈ F < d [ X ] \vec{z}:=(z_1,\cdots,z_t)\in\mathbb{F}^t, f_1,\cdots,f_t\in\mathbb{F}_{<d}[X] z:=(z1,⋯,zt)∈Ft,f1,⋯,ft∈F<d[X],将 t ∗ t^* t∗表示为 z ⃗ \vec{z} z中的distinct values数量;对于 i ∈ [ t ∗ ] i\in[t^*] i∈[t∗], d i : = m a x { d e g ( f i ) } i ∈ S i d_i:=max\{deg(f_i)\}_{i\in S_i} di:=max{
deg(fi)}i∈Si,其中 S i S_i Si表示的是the set of indices j j j such that z j z_j zj equals the i i i'th distinct point in z ⃗ \vec{z} z。令 c m i = c o m ( f i ) cm_i=com(f_i) cmi=com(fi),则 o p e n ( { c m i , f i , z i , s i } ) open(\{cm_i,f_i,z_i,s_i\}) open({
cmi,fi,zi,si}) 需要的计算量为:
a)Prover需要 ∑ i ∈ [ t ∗ ] d i \sum_{i\in[t^*]}d_i ∑i∈[t∗]di次 G 1 \mathbb{G}_1 G1-exponentiation运算。
b)Verifier需要 t + 2 t ∗ − 2 t+2t^*-2 t+2t∗−2次 G 1 \mathbb{G}_1 G1-exponentiation运算 和 2次pairing运算。
4. 理想化的low-degree protocols
对[KZG10]中的polynomial commitment scheme进行了抽象,形成的协议内容为:
- Prover将low-degree polynomials发送给可信第三方 I \mathcal{I} I。
- Verifier可询问 I \mathcal{I} I来确认Prover的这些多项式之间的关系,以及与Verifier提前知悉的预定义的多项式之间的关系。
形成的协议表示为 ( d , D , t , l ) (d,D,t,l) (d,D,t,l)-polynomial protocol,其中 d , D , t , l d,D,t,l d,D,t,l均为正整数。该协议在 Prover P p o l y P_{poly} Ppoly、Verifier V p o l y V_{poly} Vpoly 以及 可信第三方 I \mathcal{I} I 之间进行多轮执行,详细描述为:【具有completeness和Knowledge soundness属性。但实际实现时,不具有zero-knowledge 属性。具体见本论文中的Remark 4.4。】
- 1)协议定义中包含了一组预处理了的多项式 g 1 , ⋯ , g l ∈ F < d [ X ] g_1,\cdots,g_l\in\mathbb{F}_{<d}[X] g1,⋯,gl∈F<d[X]。
- 2) P p o l y P_{poly} Ppoly发送给 I \mathcal{I} I的消息形式为: f f f for f ∈ F < d [ X ] f\in\mathbb{F}_{<d}[X] f∈F<d[X]。若 P p o l y P_{poly} Ppoly的消息不是这种形式,则协议终止。【注意此处不是 ( f , n ) , n ≤ d (f,n),n\leq d (f,n),n≤d,具体原因见本论文中Remark 4.2。】
- 3) P p o l y P_{poly} Ppoly与 V p o l y V_{poly} Vpoly之间的消息为任意形式的(但是本文将关注public coin protocols where the messages are simply random coins)。
- 4)在协议结束时,假设 f 1 , ⋯ , f t f_1,\cdots,f_t f1,⋯,ft为 P p o l y P_{poly} Ppoly发送给 I \mathcal{I} I的多项式。 V p o l y V_{poly} Vpoly可询问 I \mathcal{I} I 是否 certain polynomial identities holds between { f 1 , ⋯ , f t , g 1 , ⋯ , g l } \{f_1,\cdots,f_t,g_1,\cdots,g_l\} {
f1,⋯,ft,g1,⋯,gl},其中identity的形式为:
F ( X ) : = G ( X , h 1 ( v 1 ( X ) ) , ⋯ , h M ( v M ( X ) ) ) ≡ 0 F(X):=G(X,h_1(v_1(X)), \cdots,h_M(v_M(X)))\equiv 0 F(X):=G(X,h1(v1(X)),⋯,hM(vM(X)))≡0
其中 h i ∈ { f 1 , ⋯ , f t , g 1 , ⋯ , g l } , G ∈ F [ X , X 1 , ⋯ , X M ] , v 1 , ⋯ , v M ∈ F < d [ X ] h_i\in\{f_1,\cdots,f_t,g_1,\cdots,g_l\}, G\in\mathbb{F}[X,X_1,\cdots,X_M], v_1,\cdots,v_M\in\mathbb{F}_{<d}[X] hi∈{ f1,⋯,ft,g1,⋯,gl},G∈F[X,X1,⋯,XM],v1,⋯,vM∈F<d[X],使得 F ∈ F < D [ X ] F\in\mathbb{F}_{<D}[X] F∈F<D[X] for every choice of f 1 , ⋯ , f t f_1,\cdots,f_t f1,⋯,ft made by P p o l y P_{poly} Ppoly when following the protocol correctly。 - 5)当收到 I \mathcal{I} I发送的关于identities的回复时,若所有identities均成立,则 V p o l y V_{poly} Vpoly输出 a c c acc acc,否则输出 r e j rej rej。
4.1 polynomial protocols on range
实际要求 V p o l y V_{poly} Vpoly check if certain polynomial equations hold on a certain range of input values,而不仅是as a polynomial identity。
即,for subset S ⊂ F S\subset\mathbb{F} S⊂F,定义an S S S-ranged ( d , D , t , l ) (d,D,t,l) (d,D,t,l)-polynomial protocol identically to a ( d , D , t , l ) (d,D,t,l) (d,D,t,l)-polynomial protocol, except that the verifier asks if his identities hold on all points of S S S,rather than identically。(即该子集内的所有元素均符合相应特性)
只需额外再引入一个prover polynomial,就可将ranged protocol转换为polynomial protocol。相应有Lemma 4.5:
若 P \mathscr{P} P为 S S S-ranged ( d , D , t , l ) (d,D,t,l) (d,D,t,l)-polynomial protocol for R \mathcal{R} R,则可构建相应的 ( m a x { d , ∣ S ∣ , D − ∣ S ∣ } , D , t + 1 , l + 1 ) (max\{d,|S|,D-|S|\},D,t+1,l+1) (max{
d,∣S∣,D−∣S∣},D,t+1,l+1)-polynomial protocol P ∗ \mathcal{P}^* P∗ for R \mathcal{R} R。
在证明该Lemma之前,先了解Claim 4.6内容:


Lemma 4.5相应的证明为:

4.2 由polynomial protocols 到 protocols against algebraic adversaries
目的是:
可用第3节的polynomial commitment scheme来compile a polynomial protocol into one with knowledge soundness in the algebraic group model。
为了对以上转换的效率进行衡量,需定义相关技术来衡量 ( d , D , t , l ) (d,D,t,l) (d,D,t,l)-polynomial protocol P \mathscr{P} P。
- 当 i ∈ [ t ] i\in[t] i∈[t],设置 d i d_i di为 P \mathscr{P} P中由honest prover发送的 f i f_i fi的最大degree,假设仅有一个identity G ( X , h 1 ( v 1 ( X ) ) , ⋯ , h M ( v M ( X ) ) ) ≡ 0 G(X,h_1(v_1(X)),\cdots,h_M(v_M(X)))\equiv 0 G(X,h1(v1(X)),⋯,hM(vM(X)))≡0 is checked by V p o l y V_{poly} Vpoly in P \mathscr{P} P。
- 当 i ∈ [ M ] i\in[M] i∈[M]时,设置 d i ′ d_i' di′为the “matching” d j d_j dj。即若 h i = f j h_i=f_j hi=fj有 d i ′ = d j d_i'=d_j di′=dj;若 h i = g j h_i=g_j hi=gj有 d i ′ = d e g ( g j ) d_i'=deg(g_j) di′=deg(gj)。
- 设 t ∗ = t ∗ ( P ) t^*=t^*(\mathscr{P}) t∗=t∗(P) 为 v 1 , ⋯ , v M v_1,\cdots,v_M v1,⋯,vM 中的不同多项式的数量。设 S 1 ∪ ⋯ ∪ S t ∗ = [ M ] S_1\cup\cdots\cup S_{t^*}=[M] S1∪⋯∪St∗=[M]为相应的 partition of [ M ] [M] [M] 。当 j ∈ [ t ∗ ] j\in[t^*] j∈[t∗],令 e j : = m a x { d i ′ } i ∈ S j e_j:=max\{d_i'\}_{i\in S_j} ej:=max{ di′}i∈Sj。
- 最后,定义 e ( P ) : = ∑ i ∈ [ t ] ( d i + 1 ) + ∑ j ∈ [ t ∗ ] e j e(\mathscr{P}):=\sum_{i\in[t]}(d_i+1)+\sum_{j\in[t^*]}e_j e(P):=∑i∈[t](di+1)+∑j∈[t∗]ej
Lemma 4.7 内容为:【详细的证明可参见论文P17~P18。】
若 P \mathscr{P} P为 ( d , D , t , l ) (d,D,t,l) (d,D,t,l)-polynomial protocol for R \mathcal{R} R,其中仅有一个identity is checked by V p o l y V_{poly} Vpoly,则可构建相应的protocol P ∗ \mathcal{P}^* P∗ for R \mathcal{R} R with knowledge soundness in the Algebraic Group Model under 2 d 2d 2d-DLOG 具有如下属性:
- 1) P ∗ \mathscr{P}^* P∗中的Prover需要 e ( P ) e(\mathscr{P}) e(P)次 G 1 \mathbb{G}_1 G1-exponentiation 运算。
- 2)总的communication cost为 t + t ∗ ( P ) t+t^*(\mathscr{P}) t+t∗(P)个 G 1 \mathbb{G}_1 G1 elements 和 M M M 个 F \mathbb{F} F-elements。【可借助Mary Maller优化,进一步reduce F \mathbb{F} F-elements 的数量。】
- 3)Verifier需要 t + t ∗ ( P ) t+t^*(\mathscr{P}) t+t∗(P) 次 G 1 \mathbb{G}_1 G1-exponentiations运算,2次pairing运算和1次evaluation of G G G。
4.2.1 优化 F \mathbb{F} F-elements 数量
借助Mary Maller优化,进一步reduce F \mathbb{F} F-elements 的数量:
假设 V V V想要check identity h 1 ( X ) h 2 ( X ) − h 3 ( X ) ≡ 0 h_1(X)h_2(X)-h_3(X)\equiv 0 h1(X)h2(X)−h3(X)≡0,之前的方法是 P P P 发送values of h 1 , h 2 , h 3 h_1,h_2,h_3 h1,h2,h3 at random x ∈ F x\in\mathbb{F} x∈F,然后 V V V验证 h 1 ( x ) h 2 ( x ) − h 3 ( x ) = 0 h_1(x)h_2(x)-h_3(x)=0 h1(x)h2(x)−h3(x)=0是否成立。整个过程中 P P P发送了3个field elements。
现在,可让 P P P仅发送 c : = h 1 ( x ) c:=h_1(x) c:=h1(x),然后运行open protocol来验证多项式 L ( X ) : = x ⋅ h 2 ( X ) − h 3 ( X ) L(X):=x\cdot h_2(X)-h_3(X) L(X):=x⋅h2(X)−h3(X)是否为zero at x x x。【同时注意,可计算 c o m ( L ) = c ⋅ c o m ( h 2 ) − c o m ( h 3 ) com(L)=c\cdot com(h_2)-com(h_3) com(L)=c⋅com(h2)−com(h3)。】
因此,需定义另一种技术手段来衡量a polynomial protocol。
为了简化,再次假设 V p o l y V_{poly} Vpoly仅需验证one identity F F F。现定义 r ( P ) r(\mathscr{P}) r(P)为the minimal size of a subset S ⊂ [ M ] S\subset [M] S⊂[M],满足:
- ( [ M ] ∖ S ) ⊂ S i ([M]\setminus S)\subset S_i ([M]∖S)⊂Si for one of the subsets S i S_i Si of the partition descrbed before Lemma 4.7。
- polynomial G G G:
F ( X ) : = G ( X , h 1 ( v 1 ( X ) ) , ⋯ , h M ( v M ( X ) ) ) F(X):=G(X,h_1(v_1(X)),\cdots,h_M(v_M(X))) F(X):=G(X,h1(v1(X)),⋯,hM(vM(X)))
具有degree zero or one as a polynomial in the variables { X j } j ∈ [ M ] ∖ S \{X_j\}_{j\in[M]\setminus S} { Xj}j∈[M]∖S whose coefficients are polynomials in X X X and { X j } j ∈ S \{X_j\}_{j\in S} { Xj}j∈S。
假设有 r : = r ( P ) < M r:=r(\mathscr{P})< M r:=r(P)<M,可对Lemma 4.7做如下reduction,使得Prover发送的 F \mathbb{F} F-elements数量由 M M M降为 r r r个:

5. Polynomial protocols for identifying permutations
本文universal SNARK的核心为 ”permutation check“,受[BG12]中的permutation argument 和 [BCC+16][MBKM19]的变种 启发。
相比于[MBKM19],本文算法的由于采用的是单变量多项式和multiplicative subgroups,实现的协议更简单。
要求 n ≤ d n\leq d n≤d,其中 n n n为the degree of the honest prover’s polynomials, d d d为the bound we actually enforce on malicous provers。
相应地,在分析prover efficiency和描述”official“ protocol input时,可将degree bound 看成为 n n n,而分析soundness时,可假设degree bound 为 d d d。
当 i ∈ [ n ] i\in[n] i∈[n]时, L i ( X ) L_i(X) Li(X) 表示 the element of F < n [ X ] \mathbb{F}_{<n}[X] F<n[X] with L i ( g i ) = 1 L_i(\mathbf{g}^i)=1 Li(gi)=1 and L i ( a ) = 0 L_i(a)=0 Li(a)=0 for a ∈ H a\in H a∈H different from g i \mathbf{g}^i gi,即 { L i } i ∈ [ n ] \{L_i\}_{i\in [n]} {
Li}i∈[n]为a Lagrange basis for H。
同时注意, L i L_i Li可”reduce point checks to range checks“。
Claim 5.1内容为:
若 i ∈ [ n ] , Z , Z ∗ ∈ F [ X ] i\in[n],Z,Z^*\in \mathbb{F}[X] i∈[n],Z,Z∗∈F[X],则当且仅当 Z ( g i ) = Z ∗ ( g i ) Z(\mathbf{g}^i)=Z^*(\mathbf{g}^i) Z(gi)=Z∗(gi)时,有 L i ( a ) ( Z ( a ) − Z ∗ ( a ) ) = 0 L_i(a)(Z(a)-Z^*(a))=0 Li(a)(Z(a)−Z∗(a))=0 for each a ∈ H a\in H a∈H。
当 f , g ∈ F < d [ X ] f,g\in\mathbb{F}_{<d}[X] f,g∈F<d[X]和permutation σ : [ n ] → [ n ] \sigma:[n]\rightarrow [n] σ:[n]→[n]时,若对于每一个 a ∈ H a\in H a∈H,都有 g ( g i ) = f ( g σ ( i ) ) g(\mathbf{g}^i)=f(\mathbf{g}^{\sigma(i)}) g(gi)=f(gσ(i)),则可表示为: g = σ ( f ) g=\sigma(f) g=σ(f)。
5.1 证明 g = σ ( f ) g=\sigma(f) g=σ(f)的ranged polynomial protocol
接下来将构建a ranged polynomial protocol来证明 g = σ ( f ) g=\sigma(f) g=σ(f)。
针对的场景为:
-
preprocessed polynomials:有polynomial S I D ∈ F < n [ X ] S_{ID}\in\mathbb{F}_{<n}[X] SID∈F<n[X] defined by S I D ( g i ) = i S_{ID}(\mathbf{g}^i)=i SID(gi)=i for each i ∈ [ n ] i\in [n] i∈[n],以及polynomial S σ ∈ F < n [ X ] S_{\sigma}\in\mathbb{F}_{<n}[X] Sσ∈F<n[X] defined by S σ ( g i ) = σ ( i ) S_{\sigma}(\mathbf{g}^i)=\sigma(i) Sσ(gi)=σ(i) for each i ∈ [ n ] i\in [n] i∈[n]。【注意,有 g n + 1 = g \mathbf{g}^{n+1}=\mathbf{g} gn+1=g。】
-
inputs 输入为: f , g ∈ F < n [ X ] f,g\in\mathbb{F}_{<n}[X] f,g∈F<n[X]。
-
Protocol 具体协议实现为:
1) V p o l y V_{poly} Vpoly 发送随机值 β , γ ∈ F \beta,\gamma\in\mathbb{F} β,γ∈F 给 P p o l y P_{poly} Ppoly。
2)令 f ′ : = f + β ⋅ S I D + γ , g ′ = g + b e t a ⋅ S σ + γ f':=f+\beta\cdot S_{ID}+\gamma, g'=g+beta\cdot S_{\sigma} + \gamma f′:=f+β⋅SID+γ,g′=g+beta⋅Sσ+γ,则对 i ∈ [ n ] i\in[n] i∈[n]有:
f ′ ( g i ) = f ( g i ) + β ⋅ i + γ , g ′ ( g i ) = g ( g i ) + β ⋅ σ ( i ) + γ f'(\mathbf{g}^i)=f(\mathbf{g}^i)+\beta\cdot i+\gamma,g'(\mathbf{g}^i)=g(\mathbf{g}^i)+\beta\cdot \sigma(i)+\gamma f′(gi)=f(gi)+β⋅i+γ,g′(gi)=g(gi)+β⋅σ(i)+γ
3) P p o l y P_{poly} Ppoly 计算 Z ∈ F < n [ X ] Z\in\mathbb{F}_{<n}[X] Z∈F<n[X],使得 Z ( g ) = 1 Z(\mathbf{g})=1 Z(g)=1;且对于 i ∈ { 2 , ⋯ , n } i\in\{2,\cdots,n\} i∈{ 2,⋯,n},有:
Z ( g i ) = ∏ 1 ≤ j < i f ′ ( g j ) / g ′ ( g j ) Z(\mathbf{g}^i)=\prod_{1\leq j < i}f'(\mathbf{g}^j)/g'(\mathbf{g}^j) Z(gi)=∏1≤j<if′(gj)/g′(gj)
(one of the product elements为undefined的概率可忽略。)
4) P p o l y P_{poly} Ppoly将 Z Z Z发送给 I \mathcal{I} I。
5) V p o l y V_{poly} Vpoly对所有的 a ∈ H a\in H a∈H,当且仅当如下两个条件都成立时输出 a c c acc acc:
5.a) L 1 ( a ) ( Z ( a ) − 1 ) = 0 L_1(a)(Z(a)-1)=0 L1(a)(Z(a)−1)=0【即满足 Z ( g ) = 1 Z(\mathbf{g})=1 Z(g)=1】
5.b) Z ( a ) f ′ ( a ) = g ′ ( a ) Z ( a ⋅ g ) Z(a)f'(a)=g'(a)Z(a\cdot \mathbf{g}) Z(a)f′(a)=g′(a)Z(a⋅g) 【即满足 Z ( g i ) = ∏ 1 ≤ j < i f ′ ( g j ) / g ′ ( g j ) Z(\mathbf{g}^i)=\prod_{1\leq j < i}f'(\mathbf{g}^j)/g'(\mathbf{g}^j) Z(gi)=∏1≤j<if′(gj)/g′(gj)】
5.2 checking “extended” permutations
本文的目的是:
check a permutation “across” the values of several polynomials。
假设有多个多项式 f 1 , ⋯ , f k ∈ F < d [ X ] f_1,\cdots,f_k\in\mathbb{F}_{<d}[X] f1,⋯,fk∈F<d[X] 和 permutation σ : [ k n ] → [ k n ] \sigma: [kn]\rightarrow [kn] σ:[kn]→[kn]。
对于 ( g 1 , ⋯ , g k ) ∈ ( F < d [ X ] ) k (g_1,\cdots,g_k)\in(\mathbb{F}_{<d}[X])^k (g1,⋯,gk)∈(F<d[X])k,当以下条件成立时,可称 ( g 1 , ⋯ , g k ) = σ ( f 1 , ⋯ , f k ) (g_1,\cdots,g_k)=\sigma(f_1,\cdots,f_k) (g1,⋯,gk)=σ(f1,⋯,fk):
定义序列 ( f ( 1 ) , ⋯ , f ( k n ) ) , ( g ( 1 ) , ⋯ , g ( k n ) ) ∈ F k n (f_{(1)},\cdots,f_{(kn)}),(g_{(1)},\cdots,g_{(kn)})\in\mathbb{F}^{kn} (f(1),⋯,f(kn)),(g(1),⋯,g(kn))∈Fkn 为:
f ( ( j − 1 ) ⋅ n + i ) : = f j ( g i ) , g ( ( j − 1 ) ⋅ n + i ) : = g j ( g i ) f_{((j-1)\cdot n +i)}:= f_j(\mathbf{g}^i),g_{((j-1)\cdot n +i)}:= g_j(\mathbf{g}^i) f((j−1)⋅n+i):=fj(gi),g((j−1)⋅n+i):=gj(gi)
for each j ∈ [ k ] , i ∈ [ n ] j\in[k], i\in [n] j∈[k],i∈[n]。则有 g l = f σ ( l ) g_{l}=f_{\sigma(l)} gl=fσ(l) for each l ∈ [ k n ] l\in[kn] l∈[kn]。
针对的场景为:
-
Preprocessed polynomials有:
S I D 1 , ⋯ , S I D k ∈ F < n [ X ] S_{ID_1},\cdots,S_{ID_k}\in\mathbb{F}_{<n}[X] SID1,⋯,SIDk∈F<n[X] defined by S I D j ( g i ) = ( j − 1 ) ⋅ n + i S_{ID_j}(\mathbf{g}^i)=(j-1)\cdot n + i SIDj(gi)=(j−1)⋅n+i for each i ∈ [ n ] i\in [n] i∈[n] 【实际上仅需要 S I D = S I D 1 S_{ID}=S_{ID_1} SID=SID1就足够了,其它的 S I D j ( x ) S_{ID_j}(x) SIDj(x)均可计算出来—— S I D j ( x ) = S I D ( x ) + ( j − 1 ) ⋅ n S_{ID_j}(x)=S_{ID}(x)+(j-1)\cdot n SIDj(x)=SID(x)+(j−1)⋅n】
对于每一个的 j ∈ [ k ] j\in[k] j∈[k],有 S σ j ∈ F < n [ X ] S_{\sigma_j}\in\mathbb{F}_{<n}[X] Sσj∈F<n[X] defined by S σ j ( g i ) = σ ( ( j − 1 ) ⋅ n + i ) S_{\sigma_j}(\mathbf{g}^i)=\sigma((j-1)\cdot n + i) Sσj(gi)=σ((j−1)⋅n+i) for each i ∈ [ n ] i\in [n] i∈[n]。 -
inputs 输入为: f 1 , ⋯ , f k , g 1 , ⋯ , g k ∈ F < n [ X ] f_1,\cdots,f_k, g_1,\cdots,g_k\in\mathbb{F}_{<n}[X] f1,⋯,fk,g1,⋯,gk∈F<n[X]。
-
Protocol 相应的协议实现为:
1) V p o l y V_{poly} Vpoly 发送随机值 β , γ ∈ F \beta,\gamma\in\mathbb{F} β,γ∈F 给 P p o l y P_{poly} Ppoly。
2)令 f j ′ : = f j + β ⋅ S I D j + γ , g j ′ = g j + b e t a ⋅ S σ j + γ f_j':=f_j+\beta\cdot S_{ID_j}+\gamma, g_j'=g_j+beta\cdot S_{\sigma_j} + \gamma fj′:=fj+β⋅SIDj+γ,gj′=gj+beta⋅Sσj+γ,则对 j ∈ [ k ] , i ∈ [ n ] j\in[k],i\in[n] j∈[k],i∈[n]有:
f j ′ ( g i ) = f j ( g i ) + β ⋅ ( ( j − 1 ) ⋅ n + i ) + γ , g j ′ ( g i ) = g j ( g i ) + β ⋅ σ ( ( j − 1 ) ⋅ n + i ) + γ f_j'(\mathbf{g}^i)=f_j(\mathbf{g}^i)+\beta\cdot ((j-1)\cdot n +i)+\gamma,g_j'(\mathbf{g}^i)=g_j(\mathbf{g}^i)+\beta\cdot \sigma((j-1)\cdot n + i)+\gamma fj′(gi)=fj(gi)+β⋅((j−1)⋅n+i)+γ,gj′(gi)=gj(gi)+β⋅σ((j−1)⋅n+i)+γ
3)定义 f ′ , g ′ ∈ F < k n [ X ] f',g'\in\mathbb{F}_{<kn}[X] f′,g′∈F<kn[X]为:
f ′ ( X ) : = ∏ j ∈ [ k ] f j ′ ( X ) , g ′ ( X ) : = ∏ j ∈ [ k ] g j ′ ( X ) f'(X):=\prod_{j\in[k]}f_j'(X), g'(X):=\prod_{j\in[k]}g_j'(X) f′(X):=∏j∈[k]fj′(X),g′(X):=∏j∈[k]gj′(X)
4) P p o l y P_{poly} Ppoly 计算 Z ∈ F < n [ X ] Z\in\mathbb{F}_{<n}[X] Z∈F<n[X],使得 Z ( g ) = 1 Z(\mathbf{g})=1 Z(g)=1;且对于 i ∈ { 2 , ⋯ , n } i\in\{2,\cdots,n\} i∈{ 2,⋯,n},有:
Z ( g i ) = ∏ 1 ≤ j < i f ′ ( g j ) / g ′ ( g j ) Z(\mathbf{g}^i)=\prod_{1\leq j < i}f'(\mathbf{g}^j)/g'(\mathbf{g}^j) Z(gi)=∏1≤j<if′(gj)/g′(gj)
(one of the product elements为undefined的概率可忽略。)
5) P p o l y P_{poly} Ppoly将 Z Z Z发送给 I \mathcal{I} I。
6) V p o l y V_{poly} Vpoly对所有的 a ∈ H a\in H a∈H,当且仅当如下两个条件都成立时输出 a c c acc acc:
6.a) L 1 ( a ) ( Z ( a ) − 1 ) = 0 L_1(a)(Z(a)-1)=0 L1(a)(Z(a)−1)=0【即满足 Z ( g ) = 1 Z(\mathbf{g})=1 Z(g)=1】
6.b) Z ( a ) f ′ ( a ) = g ′ ( a ) Z ( a ⋅ g ) Z(a)f'(a)=g'(a)Z(a\cdot \mathbf{g}) Z(a)f′(a)=g′(a)Z(a⋅g) 【即满足 Z ( g i ) = ∏ 1 ≤ j < i f ′ ( g j ) / g ′ ( g j ) Z(\mathbf{g}^i)=\prod_{1\leq j < i}f'(\mathbf{g}^j)/g'(\mathbf{g}^j) Z(gi)=∏1≤j<if′(gj)/g′(gj)】
5.3 checking “extended copy constraints” using a permutation
最终本文主协议中实际的primitive为:
令 T = { T 1 , ⋯ , T s } \mathcal{T}=\{T_1,\cdots,T_s\} T={
T1,⋯,Ts} 为 a partition of [ k n ] [kn] [kn] into disjoint blocks。
对于特定的 f 1 , ⋯ , f k ∈ F < n [ X ] f_1,\cdots, f_k\in\mathbb{F}_{<n}[X] f1,⋯,fk∈F<n[X],定义 ( f ( 1 ) , ⋯ , f ( k n ) ) ∈ F k n (f_{(1)},\cdots,f_{(kn)})\in\mathbb{F}^{kn} (f(1),⋯,f(kn))∈Fkn,若有 f ( l ) = f ( l ′ ) f_{(l)}=f_{(l')} f(l)=f(l′) whenever l , l ′ l,l' l,l′ belong to the same block of T \mathcal{T} T,则可称 f 1 , ⋯ , f k f_1,\cdots,f_k f1,⋯,fk copy-satisfy T \mathcal{T} T。
5.2节的protocol for extended permutations可直接拿来check whether f 1 , ⋯ , f k f_1,\cdots,f_k f1,⋯,fk satisfy T \mathcal{T} T,具体为:
定义a permutation σ ( T ) \sigma(\mathcal{T}) σ(T) on [ k n ] [kn] [kn],使得对于 T \mathcal{T} T中的每一个block T i T_i Ti, σ ( T ) \sigma(\mathcal{T}) σ(T) 包含了a cycle going over all elements of T i T_i Ti。
则 当且仅当 ( f 1 , ⋯ , f k ) = σ ( f 1 , ⋯ , f k ) (f_1,\cdots,f_k)=\sigma(f_1,\cdots,f_k) (f1,⋯,fk)=σ(f1,⋯,fk),有 ( f 1 , ⋯ , f k ) (f_1,\cdots,f_k) (f1,⋯,fk) copy-satisfy T \mathcal{T} T。
6. Constraint systems
有 n ≤ m ≤ 2 n n\leq m\leq 2n n≤m≤2n。
将fan-in two arithmetic circuits of unlimited fan-out with n n n gates and m m m wires 以constraint system的形式来表达。
constraint system L = ( V , Q ) \mathscr{L}=(\mathcal{V},\mathcal{Q}) L=(V,Q)定义如下:
- V \mathcal{V} V 的形式为: V = ( a ⃗ , b ⃗ , c ⃗ ) \mathcal{V}=(\vec{a},\vec{b},\vec{c}) V=(a,b,c),其中 a ⃗ , b ⃗ , c ⃗ ∈ [ m ] n \vec{a},\vec{b},\vec{c}\in[m]^n a,b,c∈[m]n,可将 a ⃗ , b ⃗ , c ⃗ \vec{a},\vec{b},\vec{c} a,b,c 看成是 L \mathscr{L} L的左侧、右侧和输出序列。
- Q \mathcal{Q} Q 的形式为: Q = ( q ⃗ L , q ⃗ R , q ⃗ O , q ⃗ M , q ⃗ C ) ∈ ( F n ) 5 \mathcal{Q}=(\vec{q}_L,\vec{q}_R,\vec{q}_O,\vec{q}_M,\vec{q}_C)\in(\mathbb{F}^n)^5 Q=(qL,qR,qO,qM,qC)∈(Fn)5,其中 q ⃗ L , q ⃗ R , q ⃗ O , q ⃗ M , q ⃗ C ∈ F n \vec{q}_L,\vec{q}_R,\vec{q}_O,\vec{q}_M,\vec{q}_C\in\mathbb{F}^n qL,qR,qO,qM,qC∈Fn 可看成是”selector vectors“。
称 x ⃗ ∈ F m \vec{x}\in\mathbb{F}^m x∈Fm satisfies L \mathscr{L} L 当且仅当 对于每一个 i ∈ [ n ] i\in[n] i∈[n] 均有:
( q ⃗ L ) i ⋅ x ⃗ a ⃗ i + ( q ⃗ R ) i ⋅ x ⃗ b ⃗ i + ( q ⃗ O ) i ⋅ x ⃗ c ⃗ i + ( q ⃗ M ) i ⋅ ( x ⃗ a ⃗ i ⋅ x ⃗ b ⃗ i ) + ( q ⃗ C ) i = 0 (\vec{q}_L)_i\cdot \vec{x}_{\vec{a}_i} +(\vec{q}_R)_i\cdot \vec{x}_{\vec{b}_i}+(\vec{q}_O)_i\cdot \vec{x}_{\vec{c}_i}+(\vec{q}_M)_i\cdot (\vec{x}_{\vec{a}_i}\cdot \vec{x}_{\vec{b}_i})+(\vec{q}_C)_i=0 (qL)i⋅xai+(qR)i⋅xbi+(qO)i⋅xci+(qM)i⋅(xai⋅xbi)+(qC)i=0
定义正整数 l ≤ m l\leq m l≤m,子集 I ⊂ [ m ] \mathcal{I}\subset [m] I⊂[m] of “public inputs”。
进一步不失一般性地假设 I = { 1 , ⋯ , l } \mathcal{I}=\{1,\cdots,l\} I={
1,⋯,l}。
定义relation R L \mathcal{R}_{\mathscr{L}} RL为:
the set of pairs ( x ⃗ , w ⃗ ) (\vec{x},\vec{w}) (x,w) with x ⃗ ∈ F l , w ∈ F m − l \vec{x}\in\mathbb{F}^l,w\in\mathbb{F}^{m-l} x∈Fl,w∈Fm−l,使得 x : = ( x ⃗ , w ⃗ ) \mathbf{x}:=(\vec{x},\vec{w}) x:=(x,w) satisfies L \mathscr{L} L。
则相应的constraint system实例化分类有:
- Arithmetic circuits
- Booleanity constraints
- public inputs constraints
6.1 arithmetic circuits 对应的constraint systems
针对的是:fan-in 2 circuit of n n n gates,gate类型仅支持加法或乘法,其constraint可表示为:
- 1) m m m用于表示线的数量,每根线对应一个index i ∈ [ m ] i\in[m] i∈[m]。
对于每一个门, i ∈ [ n ] i\in[n] i∈[n],有:
- 2)依次设置 a i , b i , c i a_i,b_i,c_i ai,bi,ci为第 i i i个门的left/right/output wire index。
- 3)当第 i i i个门为乘法门时,依次设置 ( q ⃗ L ) i = 0 , ( q ⃗ R ) i = 0 , ( q ⃗ M ) i = 1 , ( q ⃗ O ) i = − 1 (\vec{q}_L)_i=0,(\vec{q}_R)_i=0,(\vec{q}_M)_i=1,(\vec{q}_O)_i=-1 (qL)i=0,(qR)i=0,(qM)i=1,(qO)i=−1。
- 4)当第 i i i个门为加法门时,依次设置 ( q ⃗ L ) i = 1 , ( q ⃗ R ) i = 1 , ( q ⃗ M ) i = 0 , ( q ⃗ O ) i = − 1 (\vec{q}_L)_i=1,(\vec{q}_R)_i=1,(\vec{q}_M)_i=0,(\vec{q}_O)_i=-1 (qL)i=1,(qR)i=1,(qM)i=0,(qO)i=−1。【注意,可设置 ( q ⃗ L ) i , ( q ⃗ R ) i (\vec{q}_L)_i,(\vec{q}_R)_i (qL)i,(qR)i为非零值来表达“linear combination gates”。】
- 5)总是设置 ( q ⃗ C ) i = 0 (\vec{q}_C)_i=0 (qC)i=0。
6.2 booleanity constraints
针对要求 x j ∈ { 0 , 1 } \mathbf{x}_j\in\{0,1\} xj∈{
0,1} for some j ∈ [ m ] j\in[m] j∈[m]的场景。
对于每一个门, i ∈ [ n ] i\in[n] i∈[n],有:
a i = b i = j , ( q ⃗ L ) i = − 1 , ( q ⃗ M ) i = 1 , ( q ⃗ R ) i = ( q ⃗ O ) i = ( q ⃗ C ) i = 0 a_i=b_i=j,(\vec{q}_L)_i=-1,(\vec{q}_M)_i=1,(\vec{q}_R)_i=(\vec{q}_O)_i=(\vec{q}_C)_i=0 ai=bi=j,(qL)i=−1,(qM)i=1,(qR)i=(qO)i=(qC)i=0
6.4 public inputs constraints
针对public inputs x 1 , ⋯ , x l \mathbf{x}_1,\cdots,\mathbf{x}_l x1,⋯,xl 的约束,即要求对于某个门 i ∈ [ n ] i\in[n] i∈[n],满足 x j = x j \mathbf{x}_j=x_j xj=xj,有:
a i = j , ( q ⃗ L ) i = 1 , ( q ⃗ M ) i = ( q ⃗ R ) i = ( q ⃗ O ) i = 0 , ( q ⃗ C ) i = − x j a_i=j,(\vec{q}_L)_i=1,(\vec{q}_M)_i=(\vec{q}_R)_i=(\vec{q}_O)_i=0,(\vec{q}_C)_i=-x_j ai=j,(qL)i=1,(qM)i=(qR)i=(qO)i=0,(qC)i=−xj
7. 主协议
令 L = ( V , Q ) \mathscr{L}=(\mathcal{V},\mathcal{Q}) L=(V,Q) 为第6节对应的constraint system,对应的relation为 R L \mathcal{R}_{\mathscr{L}} RL。
partition of L \mathscr{L} L 表示为 T L \mathcal{T}_{\mathscr{L}} TL。
假设: V = ( a ⃗ , b ⃗ , c ⃗ ) \mathcal{V}=(\vec{a},\vec{b},\vec{c}) V=(a,b,c),可将其看成是a vector V ⃗ \vec{V} V in [ m ] 3 n [m]^{3n} [m]3n。
对于 i ∈ [ m ] i\in[m] i∈[m],令 T i ⊂ [ 3 n ] T_i\subset[3n] Ti⊂[3n]为the set of indices j ∈ [ 3 n ] j\in[3n] j∈[3n],使得 V ⃗ = i \vec{V}=i V=i,则可定义:
T L : = { T i } i ∈ [ m ] \mathcal{T}_{\mathscr{L}}:=\{T_i\}_{i\in[m]} TL:={
Ti}i∈[m]
for i ∈ [ l ] i\in[l] i∈[l],当满足如下条件时,可称 L \mathscr{L} L is prepared for l l l public inputs:
a i = i , ( q ⃗ L ) i = 1 , ( q ⃗ M ) i = ( q ⃗ R ) i = ( q ⃗ O ) i = 0 , ( q ⃗ C ) i = 0 a_i=i,(\vec{q}_L)_i=1,(\vec{q}_M)_i=(\vec{q}_R)_i=(\vec{q}_O)_i=0,(\vec{q}_C)_i=0 ai=i,(qL)i=1,(qM)i=(qR)i=(qO)i=0,(qC)i=0
记住 H = { g , ⋯ , g n } H=\{\mathbf{g},\cdots,\mathbf{g}^n\} H={ g,⋯,gn},为 R L \mathcal{R}_{\mathscr{L}} RL构建的 H H H-ranged polynomial protocol为:
-
Preprocessing:
令 σ = σ ( T L ) \sigma=\sigma(\mathcal{T}_{\mathscr{L}}) σ=σ(TL)。
具体 S I D 1 , S I D 2 , S I D 3 , S σ 1 , S σ 2 , S σ 3 ∈ F < n [ X ] S_{ID_1},S_{ID_2},S_{ID_3},S_{\sigma_1},S_{\sigma_2},S_{\sigma_3}\in\mathbb{F}_{<n}[X] SID1,SID2,SID3,Sσ1,Sσ2,Sσ3∈F<n[X]多项式的定义可参见 5.1节“checking “extended” permutations”。
对于每个门 i ∈ [ n ] i\in[n] i∈[n],相应的多项式 q L , q R , q O , q M , q C ∈ F < n [ X ] q_L,q_R,q_O,q_M,q_C\in\mathbb{F}_{<n}[X] qL,qR,qO,qM,qC∈F<n[X]的定义为:
q L ( g i ) : = ( q ⃗ L ) i , q R ( g i ) : = ( q ⃗ R ) i , q O ( g i ) : = ( q ⃗ O ) i , q M ( g i ) : = ( q ⃗ M ) i , q C ( g i ) : = ( q ⃗ C ) i q_L(\mathbf{g}^i):=(\vec{q}_L)_i,q_R(\mathbf{g}^i):=(\vec{q}_R)_i,q_O(\mathbf{g}^i):=(\vec{q}_O)_i,q_M(\mathbf{g}^i):=(\vec{q}_M)_i,q_C(\mathbf{g}^i):=(\vec{q}_C)_i qL(gi):=(qL)i,qR(gi):=(qR)i,qO(gi):=(qO)i,qM(gi):=(qM)i,qC(gi):=(qC)i -
具体的协议实现为:【 H H H-ranged polynomial protocol for relation R L \mathcal{R}_{\mathscr{L}} RL。】
1)令 x ∈ F m \mathbf{x}\in\mathbb{F}^m x∈Fm为 P p o l y P_{poly} Ppoly的assignment,其与public input x ⃗ \vec{x} x保持一致性。 P p o l y P_{poly} Ppoly输出了3个多项式 f L , f R , f O ∈ F < n [ X ] f_L,f_R,f_O\in\mathbb{F}_{<n}[X] fL,fR,fO∈F<n[X],使得对每一个门 i ∈ [ n ] i\in[n] i∈[n],有:
f L ( i ) = x a i , f R ( i ) = x b i , f O ( i ) = x c i f_L(i)=\mathbf{x}_{a_i}, f_R(i)=\mathbf{x}_{b_i},f_O(i)=\mathbf{x}_{c_i} fL(i)=xai,fR(i)=xbi,fO(i)=xci
P p o l y P_{poly} Ppoly将 f L , f R , f O f_L,f_R,f_O fL,fR,fO发送给 I \mathcal{I} I。
2) P p o l y P_{poly} Ppoly和 V p o l y V_{poly} Vpoly都运行 the extended permutation check 协议,使用the permutation σ \sigma σ between ( f L , f R , f O ) (f_L,f_R,f_O) (fL,fR,fO) and itself。
如 5.3节“checking “extended copy constraints” using a permutation” 所解释的,其exactly checks whether ( f L , f R , f O ) (f_L,f_R,f_O) (fL,fR,fO) copy-satisfies T L \mathcal{T}_{\mathscr{L}} TL。
3) V p o l y V_{poly} Vpoly 计算“Public input polynomial”:
P I ( X ) : = ∑ i ∈ [ l ] − x i ⋅ L i ( X ) PI(X):=\sum_{i\in[l]}-x_i\cdot L_i(X) PI(X):=∑i∈[l]−xi⋅Li(X)
4) V p o l y V_{poly} Vpoly 基于 H H H以下identity是否成立:
q L ⋅ f L + q R ⋅ f R + q O ⋅ f O + q M ⋅ f L ⋅ f R + ( q C + P I ) = 0 q_L\cdot f_L +q_R\cdot f_R+q_O\cdot f_O+q_M\cdot f_L\cdot f_R+(q_C+PI)=0 qL⋅fL+qR⋅fR+qO⋅fO+qM⋅fL⋅fR+(qC+PI)=0
以上协议对应的计算量和communication cost为:
- Prover 需要 11 n + 2 11n+2 11n+2次 G 1 \mathbb{G}_1 G1-exponentiations运算;【 e ( P ) = 11 n + 2 e(\mathscr{P})=11n+2 e(P)=11n+2,因其中有 7 n + 1 7n+1 7n+1 cost of commitments,the maximal degree among the polynomial evaluated at x x x为 3 n 3n 3n 以及 the maximum degree among polynomials evaluated at x / g x/{\mathbf{g}} x/g 为 n + 1 n+1 n+1。】
- 总的communication cost为 7个 G 1 \mathbb{G}_1 G1-elements和8个 F \mathbb{F} F-elements。
- t ∗ P = 2 t^*{\mathscr{P}}=2 t∗P=2,因有2个distinct evaluation points。
- r ( P ) ≤ 8 r(\mathscr{P})\leq 8 r(P)≤8。
8. 最终完整的协议
为了便于读者理解,整理了 the full final protocol。
在此之前,都未考虑zero-knowledge属性,而此时,将通过增加 random multiples of Z H Z_H ZH to the witness based-polynomials 来实现zero-knowledge属性。这种方式不会影响satisfiability,但可create a situation where the values are either completely uniform or determined by verifier equations。【实际上,为实现优化的FFT性能,一般要求 H H H为a multiplicative group with few points omitted so that the degrees even after adding these random multiples are smaller than the group order n n n。这将要求a slight complication of the grand product argument with separate constraints for Z Z Z staring and ending at one,as our actual set H H H does not “wrap” anymore。】
明确定义multiplicative group H H H包含了 n n n’th roots of unity in F p \mathbb{F}_p Fp,其中 ω \omega ω 为 a primitive n n n'th root of unity and a generator of H H H,即 H = { 1 , ω , ⋯ , ω n − 1 } H=\{1,\omega,\cdots,\omega^{n-1}\} H={ 1,ω,⋯,ωn−1}。
假设circuit中的门数量不超过 n n n。
同时,本文还包含了来自Vitalik的优化建议——定义the identity permutations through degree-1 polynomials。这种identity permutations必须map 每一个wire value TO a unique element ∈ F \in\mathbb{F} ∈F。可通过定义 S I D 1 ( X ) = X , S I D 2 ( X ) = k 1 X , S I D 3 ( X ) = k 2 X S_{ID_1}(X)=X,S_{ID_2}(X)=k_1X,S_{ID_3}(X)=k_2X SID1(X)=X,SID2(X)=k1X,SID3(X)=k2X来实现,其中 k 1 , k 2 k_1,k_2 k1,k2为quadratic non-residues ∈ F \in\mathbb{F} ∈F。这可effectively map 每一个wire value TO a root of unity in H H H,其中right wires和ouput wires分别具有额外的mulitplicative factor of k 1 , k 2 k_1,k_2 k1,k2。通过所实现的identity permutation via degree-1 polynomials,其evaluations可由Verifier来直接计算。这将减少proof size中的1个 F \mathbb{F} F element的同时,还可以减少Prover运行FFT的次数 以及 减少Verifier 的1个scalar multiplication计算。
8.1 用于定义特定circuit的多项式
以下这些多项式,与integer n n n一起,唯一定义了a universal SNARK circuit:
- q M ( X ) , q L ( X ) , q R ( X ) , q O ( X ) , q C ( X ) q_M(X),q_L(X),q_R(X),q_O(X),q_C(X) qM(X),qL(X),qR(X),qO(X),qC(X) 为“selector”多项式,定义了circuit’s arithmetisation。
- S I D 1 ( X ) = X , S I D 2 ( X ) = k 1 X , S I D 3 ( X ) = k 2 X S_{ID_1}(X)=X,S_{ID_2}(X)=k_1X,S_{ID_3}(X)=k_2X SID1(X)=X,SID2(X)=k1X,SID3(X)=k2X 为 用于 a , b , c \mathbf{a},\mathbf{b},\mathbf{c} a,b,c的identity permutation。其中 k 1 , k 2 ∈ F k_1,k_2\in\mathbb{F} k1,k2∈F 满足 H , k 1 ⋅ H , k 2 ⋅ H H,k_1\cdot H,k_2\cdot H H,k1⋅H,k2⋅H为distinct cosets of H H H in F ∗ \mathbb{F}^* F∗,即包含有 3 n 3n 3n个不同的元素。(如,当 ω \omega ω为quadratic residue in F \mathbb{F} F时,取 k 1 k_1 k1为任意quadratic non-residue,取 k 2 k_2 k2为a quadratic non-residue not contained in k 1 ⋅ H k_1\cdot H k1⋅H。)
- S σ 1 ( X ) , S σ 2 ( X ) , S σ 3 ( X ) S_{\sigma_1}(X),S_{\sigma_2}(X),S_{\sigma_3}(X) Sσ1(X),Sσ2(X),Sσ3(X) 为 用于 a , b , c \mathbf{a},\mathbf{b},\mathbf{c} a,b,c的copy permutation。
- n n n为特定circuit中总的门数量。由 V V V用于计算vanishing polynomial:
Z H ( X ) = X n − 1 Z_H(X)=X^n-1 ZH(X)=Xn−1
8.2 对wire values 的commitments
proof的witness实际为the wire value witnesses ( w i ) i = 1 3 n (w_i)_{i=1}^{3n} (wi)i=13n。
Kate polynomial commitments具有computationally binding属性,对wire value witnesses的commItment可表示为 [ a ] 1 , [ b ] 1 , [ c ] 1 [a]_1,[b]_1,[c]_1 [a]1,[b]1,[c]1,其会用到包含 group elements ( x ⋅ [ 1 ] 1 , ⋯ , x n ⋅ [ 1 ] 1 ) (x\cdot [1]_1,\cdots,x^n\cdot [1]_1) (x⋅[1]1,⋯,xn⋅[1]1) 的structured reference string。
8.3 un-rolled universal SNARK proof relation表示
完整的un-rolled universal SNARK proof relation表示为:
R s n a r k ( λ ) = { ( x , w , c r s ) = ( ( w i ) i ∈ [ l ] ) , ( ( w i ) i = 1 , i ∉ [ l ] 3 n ) , ( ( q M i , q L i , q R i , q O i , q C i ) i = 1 n , n , σ ( x ) ) For all i ∈ { 1 , ⋯ , 3 n } : w i ∈ F p , and for all i ∈ { 1 , ⋯ , n } : w i w n + i q M i + w i q L i + w n + i q R i + w 2 n + i q O i + q C i = 0 and for all i ∈ { 1 , ⋯ , 3 n } : w i = w σ ( i ) } \mathcal{R}_{snark}(\lambda)=\begin{Bmatrix} (x,w,crs)=((w_i)_{i\in[l]}),((w_i)_{i=1,i\notin[l]}^{3n}),\\ ((q_{M_i},q_{L_i},q_{R_i},q_{O_i},q_{C_i})_{i=1}^n,n,\sigma(x))\\ \text{For all } i\in\{1,\cdots,3n\}: w_i\in\mathbb{F}_p, \text{ and for all } i\in\{1,\cdots,n\}:\\ w_iw_{n+i}q_{M_i}+w_iq_{L_i}+w_{n+i}q_{R_i}+w_{2n+i}q_{O_i}+q_{C_i}=0\\ \text{ and for all } i\in\{1,\cdots,3n\}: w_i=w_{\sigma(i)} \end{Bmatrix} Rsnark(λ)=⎩⎪⎪⎪⎪⎨⎪⎪⎪⎪⎧(x,w,crs)=((wi)i∈[l]),((wi)i=1,i∈/[l]3n),((qMi,qLi,qRi,qOi,qCi)i=1n,n,σ(x))For all i∈{
1,⋯,3n}:wi∈Fp, and for all i∈{
1,⋯,n}:wiwn+iqMi+wiqLi+wn+iqRi+w2n+iqOi+qCi=0 and for all i∈{
1,⋯,3n}:wi=wσ(i)⎭⎪⎪⎪⎪⎬⎪⎪⎪⎪⎫
8.4 具体协议实现
本文使用Fiat-Shamir heuristic来实现non-interactive protocol。
使用transcript来表示:
the concatenation of the common preprocessed input, and public input, and the proof elements written by the prover up to a certain point in time。
本文使用transcript来获取random challenges via Fiat-Shamir。
可将以下写“compute challenges”的部分替换为:Verifier 发送random field elements来改为interactive protocol。
使用 R \mathcal{R} R 来表示hash函数, R : { 0 , 1 } ∗ → F p \mathcal{R}:\{0,1\}^*\rightarrow\mathbb{F}_p R:{ 0,1}∗→Fp 来模拟the random oracle。
-
Common preprocessed input有:
n , ( x ⋅ [ 1 ] 1 , ⋯ , x n + 5 ⋅ [ 1 ] 1 ) , ( q M i , q L i , q R i , q O i , q C i ) i = 1 n , σ ( X ) n,(x\cdot [1]_1,\cdots,x^{n+5}\cdot [1]_1),(q_{M_i},q_{L_i},q_{R_i},q_{O_i},q_{C_i})_{i=1}^n,\sigma(X) n,(x⋅[1]1,⋯,xn+5⋅[1]1),(qMi,qLi,qRi,qOi,qCi)i=1n,σ(X)
q M ( X ) = ∑ i = 1 n q M i L i ( X ) , q_M(X)=\sum_{i=1}^{n}q_{M_i}L_i(X), qM(X)=∑i=1nqMiLi(X),
q L ( X ) = ∑ i = 1 n q L i L i ( X ) , q_L(X)=\sum_{i=1}^{n}q_{L_i}L_i(X), qL(X)=∑i=1nqLiLi(X),
q R ( X ) = ∑ i = 1 n q R i L i ( X ) , q_R(X)=\sum_{i=1}^{n}q_{R_i}L_i(X), qR(X)=∑i=1nqRiLi(X),
q O ( X ) = ∑ i = 1 n q O i L i ( X ) , q_O(X)=\sum_{i=1}^{n}q_{O_i}L_i(X), qO(X)=∑i=1nqOiLi(X),
q C ( X ) = ∑ i = 1 n q C i L i ( X ) , q_C(X)=\sum_{i=1}^{n}q_{C_i}L_i(X), qC(X)=∑i=1nqCiLi(X),
S σ 1 ( X ) = ∑ i = 1 n σ ( i ) L i ( X ) , S_{\sigma_1}(X)=\sum_{i=1}^{n}\sigma(i)L_i(X), Sσ1(X)=∑i=1nσ(i)Li(X),
S σ 2 ( X ) = ∑ i = 1 n σ ( n + i ) L i ( X ) , S_{\sigma_2}(X)=\sum_{i=1}^{n}\sigma(n+i)L_i(X), Sσ2(X)=∑i=1nσ(n+i)Li(X),
S σ 3 ( X ) = ∑ i = 1 n σ ( 2 n + i ) L i ( X ) S_{\sigma_3}(X)=\sum_{i=1}^{n}\sigma(2n+i)L_i(X) Sσ3(X)=∑i=1nσ(2n+i)Li(X) -
Public input有:
l , ( w i ) i ∈ [ l ] l,(w_i)_{i\in[l]} l,(wi)i∈[l]
8.4.1 Prover P P P 端算法
Prover input 有: ( w i ) i ∈ [ 3 n ] (w_i)_{i\in[3n]} (wi)i∈[3n]
-
Round 1 第一轮:
1)生成随机blinding scalars ( b 1 , ⋯ , b 9 ) ∈ F p (b_1,\cdots,b_9)\in\mathbb{F}_p (b1,⋯,b9)∈Fp
2)计算wire 多项式 a ( X ) , b ( X ) , c ( X ) a(X),b(X),c(X) a(X),b(X),c(X):
a ( X ) = ( b 1 X + b 2 ) Z H ( X ) + ∑ i = 1 n w i L i ( X ) a(X)=(b_1X+b_2)Z_H(X)+\sum_{i=1}^{n}w_iL_i(X) a(X)=(b1X+b2)ZH(X)+∑i=1nwiLi(X)
b ( X ) = ( b 3 X + b 4 ) Z H ( X ) + ∑ i = 1 n w n + i L i ( X ) b(X)=(b_3X+b_4)Z_H(X)+\sum_{i=1}^{n}w_{n+i}L_i(X) b(X)=(b3X+b4)ZH(X)+∑i=1nwn+iLi(X)
c ( X ) = ( b 5 X + b 6 ) Z H ( X ) + ∑ i = 1 n w 2 n + i L i ( X ) c(X)=(b_5X+b_6)Z_H(X)+\sum_{i=1}^{n}w_{2n+i}L_i(X) c(X)=(b5X+b6)ZH(X)+∑i=1nw2n+iLi(X)
3)计算: [ a ] 1 : = [ a ( x ) ] 1 , [ b ] 1 : = [ b ( x ) ] 1 , [ c ] 1 : = [ c ( x ) ] 1 [a]_1:=[a(x)]_1,[b]_1:=[b(x)]_1,[c]_1:=[c(x)]_1 [a]1:=[a(x)]1,[b]1:=[b(x)]1,[c]1:=[c(x)]1
第一轮 P P P的输出为 ( [ a ] 1 , [ b ] 1 , [ c ] 1 ) ([a]_1,[b]_1,[c]_1) ([a]1,[b]1,[c]1)。 -
Round 2 第二轮:
1)计算permutation challeges ( β , γ ) ∈ F p (\beta,\gamma)\in\mathbb{F}_p (β,γ)∈Fp:
β = R ( t r a n s c r i p t , 0 ) , γ = R ( t r a n s c r i p t , 1 ) \beta=\mathcal{R}(transcript,0), \gamma=\mathcal{R}(transcript,1) β=R(transcript,0),γ=R(transcript,1)
2)计算permutation polynomial z ( X ) z(X) z(X):
z ( X ) = ( b 7 X 2 + b 8 X + b 9 ) Z H ( X ) + L 1 ( X ) + ∑ i = 1 n − 1 ( L i + 1 ( X ) ∏ j = 1 i ( w j + β ω j − 1 + γ ) ( w n + j + β k 1 ω j − 1 + γ ) ( w 2 n + j + β k 2 ω j − 1 + γ ) ( w j + σ ( j ) β + γ ) ( w n + j + σ ( n + j ) β + γ ) ( w 2 n + j + σ ( 2 n + j ) β + γ ) ) z(X)=(b_7X^2+b_8X+b_9)Z_H(X)+L_1(X)+\sum_{i=1}^{n-1}(L_{i+1}(X)\prod_{j=1}^{i}\frac{(w_j+\beta \omega^{j-1}+\gamma)(w_{n+j}+\beta k_1\omega^{j-1}+\gamma)(w_{2n+j}+\beta k_2\omega^{j-1}+\gamma)}{(w_j+\sigma(j)\beta+\gamma)(w_{n+j}+\sigma(n+j)\beta+\gamma)(w_{2n+j}+\sigma(2n+j)\beta+\gamma)}) z(X)=(b7X2+b8X+b9)ZH(X)+L1(X)+∑i=1n−1(Li+1(X)∏j=1i(wj+σ(j)β+γ)(wn+j+σ(n+j)β+γ)(w2n+j+σ(2n+j)β+γ)(wj+βωj−1+γ)(wn+j+βk1ωj−1+γ)(w2n+j+βk2ωj−1+γ))
3)计算: [ z ] 1 : = [ z ( x ) ] 1 [z]_1:=[z(x)]_1 [z]1:=[z(x)]1
第二轮 P P P的输出为 ( [ z ] 1 ) ([z]_1) ([z]1)。 -
Round 3 第三轮:
1)计算quotient challenege α ∈ F p \alpha\in\mathbb{F}_p α∈Fp:
α = R ( t r a n s c r i p t ) \alpha=\mathcal{R}(transcript) α=R(transcript)
2)计算quotient polynomial t ( X ) t(X) t(X):
t ( X ) = ( a ( X ) b ( X ) q M ( X ) + a ( X ) q L ( X ) + b ( X ) q R ( X ) + c ( X ) q O ( X ) + P I ( X ) + q C ( X ) ) 1 Z H ( X ) + ( ( a ( X ) + β X + γ ) ( b ( X ) + β k 1 X + γ ) ( c ( X ) + β k 2 X + γ ) z ( X ) ) α Z H ( X ) − ( ( a ( X ) + β S σ 1 ( X ) + γ ) ( b ( X ) + β S σ 2 ( X ) + γ ) ( c ( X ) + β S σ 3 ( X ) + γ ) z ( X ω ) ) α Z H ( X ) + ( z ( X ) − 1 ) L 1 ( X ) α 2 Z H ( X ) t(X)=(a(X)b(X)q_M(X)+a(X)q_L(X)+b(X)q_R(X)+c(X)q_O(X)+PI(X)+q_C(X))\frac{1}{Z_H(X)}+((a(X)+\beta X+\gamma)(b(X)+\beta k_1X+\gamma)(c(X)+\beta k_2 X+\gamma)z(X))\frac{\alpha}{Z_H(X)}-((a(X)+\beta S_{\sigma_1}(X)+\gamma)(b(X)+\beta S_{\sigma_2}(X)+\gamma)(c(X)+\beta S_{\sigma_3}(X)+\gamma)z(X\omega))\frac{\alpha}{Z_H(X)}+(z(X)-1)L_1(X)\frac{\alpha^2}{Z_H(X)} t(X)=(a(X)b(X)qM(X)+a(X)qL(X)+b(X)qR(X)+c(X)qO(X)+PI(X)+qC(X))ZH(X)1+((a(X)+βX+γ)(b(X)+βk1X+γ)(c(X)+βk2X+γ)z(X))ZH(X)α−((a(X)+βSσ1(X)+γ)(b(X)+βSσ2(X)+γ)(c(X)+βSσ3(X)+γ)z(Xω))ZH(X)α+(z(X)−1)L1(X)ZH(X)α2
将 t ( X ) t(X) t(X)拆分为degree < n <n <n 多项式 t l o ( X ) , t m i d ( X ) t_{lo}(X),t_{mid}(X) tlo(X),tmid(X) 和 degree ≤ n + 5 \leq n+5 ≤n+5 多项式 t h i ( X ) t_{hi}(X) thi(X)表示为:
t ( X ) = t l o ( X ) + X n t m i d ( X ) + X 2 n t h i ( X ) t(X)=t_{lo}(X)+X^n t_{mid}(X) + X^{2n}t_{hi}(X) t(X)=tlo(X)+Xntmid(X)+X2nthi(X)
3)计算: [ t l o ] 1 : = [ t l o ( x ) ] 1 , [ t m i d ] 1 : = [ t m i d ( x ) ] 1 , [ t h i ] 1 : = [ t h i ( x ) ] 1 [t_{lo}]_1:=[t_{lo}(x)]_1,[t_{mid}]_1:=[t_{mid}(x)]_1,[t_{hi}]_1:=[t_{hi}(x)]_1 [tlo]1:=[tlo(x)]1,[tmid]1:=[tmid(x)]1,[thi]1:=[thi(x)]1
第三轮 P P P的输出为 ( [ t l o ] 1 , [ t m i d ] 1 , [ t h i ] 1 ) ([t_{lo}]_1,[t_{mid}]_1,[t_{hi}]_1) ([tlo]1,[tmid]1,[thi]1)。 -
Round 4 第四轮:
1)计算evaluation challenge ϑ ∈ F p \vartheta \in\mathbb{F}_p ϑ∈Fp:
ϑ = R ( t r a n s c r i p t ) \vartheta =\mathcal{R}(transcript) ϑ=R(transcript)
2)计算opening evaluations:
a ˉ = a ( ϑ ) , b ˉ = b ( ϑ ) , c ˉ = c ( ϑ ) , s ˉ σ 1 = S σ 1 ( ϑ ) , s ˉ σ 2 = S σ 2 ( ϑ ) , t ˉ = t ( ϑ ) , z ˉ ω = t ( ϑ ω ) \bar{a}=a(\vartheta),\bar{b}=b(\vartheta),\bar{c}=c(\vartheta),\bar{s}_{\sigma_1}=S_{\sigma_1}(\vartheta),\bar{s}_{\sigma_2}=S_{\sigma_2}(\vartheta),\bar{t}=t(\vartheta),\bar{z}_{\omega}=t(\vartheta\omega) aˉ=a(ϑ),bˉ=b(ϑ),cˉ=c(ϑ),sˉσ1=Sσ1(ϑ),sˉσ2=Sσ2(ϑ),tˉ=t(ϑ),zˉω=t(ϑω)
3)计算linearisation polynomial r ( X ) r(X) r(X):
r ( X ) = ( a ˉ b ˉ ⋅ q M ( X ) + a ˉ ⋅ q L ( X ) + b ˉ ⋅ q R ( X ) + c ˉ ⋅ q O ( X ) + q C ( X ) ) + ( ( a ˉ + β ϑ + γ ) ( b ˉ + β k 1 ϑ + γ ) ( c ˉ + β k 2 ϑ + γ ) ⋅ z ( X ) ) α − ( ( a ˉ + β s ˉ σ 1 + γ ) ( b ˉ + β s ˉ σ 2 + γ ) β z ˉ ω ⋅ S σ 3 ( X ) ) α + ( z ( X ) ) L 1 ( ϑ ) α 2 r(X)=(\bar{a}\bar{b}\cdot q_M(X)+\bar{a}\cdot q_L(X)+\bar{b}\cdot q_R(X)+\bar{c}\cdot q_O(X)+q_C(X))+((\bar{a}+\beta\vartheta+\gamma)(\bar{b}+\beta k_1\vartheta+\gamma)(\bar{c}+\beta k_2\vartheta+\gamma)\cdot z(X))\alpha - ((\bar{a}+\beta\bar{s}_{\sigma_1}+\gamma)(\bar{b}+\beta\bar{s}_{\sigma_2}+\gamma)\beta\bar{z}_{\omega}\cdot S_{\sigma_3}(X))\alpha + (z(X))L_1(\vartheta)\alpha^2 r(X)=(aˉbˉ⋅qM(X)+aˉ⋅qL(X)+bˉ⋅qR(X)+cˉ⋅qO(X)+qC(X))+((aˉ+βϑ+γ)(bˉ+βk1ϑ+γ)(cˉ+βk2ϑ+γ)⋅z(X))α−((aˉ+βsˉσ1+γ)(bˉ+βsˉσ2+γ)βzˉω⋅Sσ3(X))α+(z(X))L1(ϑ)α2
4)计算 linearsation evaluation r ˉ = r ( ϑ ) \bar{r}=r(\vartheta) rˉ=r(ϑ)
第四轮 P P P的输出为 ( a ˉ , b ˉ , c ˉ , s ˉ σ 1 , s ˉ σ 2 , z ˉ ω , t ˉ , r ˉ ) (\bar{a},\bar{b},\bar{c},\bar{s}_{\sigma_1},\bar{s}_{\sigma_2},\bar{z}_{\omega},\bar{t},\bar{r}) (aˉ,bˉ,cˉ,sˉσ1,sˉσ2,zˉω,tˉ,rˉ)。 -
Round 5 第五轮:
1)计算opening challenge v ∈ F p v\in\mathbb{F}_p v∈Fp:
v = R ( t r a n s c r i p t ) v=\mathcal{R}(transcript) v=R(transcript)
2)计算opening proof polynomial W ϑ ( X ) W_{\vartheta}(X) Wϑ(X):
W ϑ ( X ) = 1 X − ϑ ( ( t l o ( X ) + ϑ n t m i d ( X ) + ϑ 2 n t h i ( X ) − t ˉ ) + v ( r ( X ) − r ˉ ) + v 2 ( a ( X ) − a ˉ ) + v 3 ( b ( X ) − b ˉ ) + v 4 ( c ( X ) − c ˉ ) + v 5 ( S σ 1 ( X ) − s ˉ σ 1 ) + v 6 ( S σ 2 ( X ) − s ˉ σ 2 ) ) W_{\vartheta}(X)=\frac{1}{X-\vartheta}((t_{lo}(X)+\vartheta^nt_{mid}(X)+\vartheta^{2n}t_{hi}(X)-\bar{t})+ v(r(X)-\bar{r})+v^2(a(X)-\bar{a})+v^3(b(X)-\bar{b})+v^4(c(X)-\bar{c})+v^5(S_{\sigma_1}(X)-\bar{s}_{\sigma_1})+v^6(S_{\sigma_2}(X)-\bar{s}_{\sigma_2})) Wϑ(X)=X−ϑ1((tlo(X)+ϑntmid(X)+ϑ2nthi(X)−tˉ)+v(r(X)−rˉ)+v2(a(X)−aˉ)+v3(b(X)−bˉ)+v4(c(X)−cˉ)+v5(Sσ1(X)−sˉσ1)+v6(Sσ2(X)−sˉσ2))
3)计算opening proof plynomial W ϑ ω ( X ) W_{\vartheta\omega}(X) Wϑω(X):
W ϑ ω ( X ) = ( z ( X ) − z ˉ ω ) X − ϑ ω W_{\vartheta\omega}(X)=\frac{(z(X)-\bar{z}_{\omega})}{X-\vartheta\omega} Wϑω(X)=X−ϑω(z(X)−zˉω)
4)计算 [ W ϑ ] 1 : = [ W ϑ ( x ) ] 1 , [ W ϑ ω ] 1 : = [ W ϑ ω ( x ) ] 1 [W_{\vartheta}]_1:=[W_{\vartheta}(x)]_1,[W_{\vartheta\omega}]_1:=[W_{\vartheta\omega}(x)]_1 [Wϑ]1:=[Wϑ(x)]1,[Wϑω]1:=[Wϑω(x)]1
第五轮 P P P的输出为 ( [ W ϑ ] 1 , [ W ϑ ω ] 1 ) ([W_{\vartheta}]_1,[W_{\vartheta\omega}]_1) ([Wϑ]1,[Wϑω]1)
总的proof内容为:
π S N A R K = ( [ a ] 1 , [ b ] 1 , [ c ] 1 , [ z ] 1 , [ t l o ] 1 , [ t m i d ] 1 , [ t h i ] 1 , [ W ϑ ] 1 , [ W ϑ ω ] 1 , a ˉ , b ˉ , c ˉ , s ˉ σ 1 , s ˉ σ 2 , z ˉ ω , r ˉ ) \pi_{SNARK}=([a]_1,[b]_1,[c]_1,[z]_1,[t_{lo}]_1,[t_{mid}]_1,[t_{hi}]_1,[W_{\vartheta}]_1,[W_{\vartheta\omega}]_1,\bar{a},\bar{b},\bar{c},\bar{s}_{\sigma_1},\bar{s}_{\sigma_2},\bar{z}_{\omega},\bar{r}) πSNARK=([a]1,[b]1,[c]1,[z]1,[tlo]1,[tmid]1,[thi]1,[Wϑ]1,[Wϑω]1,aˉ,bˉ,cˉ,sˉσ1,sˉσ2,zˉω,rˉ)
- 计算multipoint evaluation challenge u ∈ F p u\in\mathbb{F}_p u∈Fp:
u = R ( t r a n s c r i p t ) u=\mathcal{R}(transcript) u=R(transcript)
8.4.2 Verifier V V V 端算法
Verifier preprocessed input 有:
[ q M ] 1 : = q M ( x ) ⋅ [ 1 ] 1 , [ q L ] 1 : = q L ( x ) ⋅ [ 1 ] 1 , [ q R ] 1 : = q R ( x ) ⋅ [ 1 ] 1 , [ q O ] 1 : = q O ( x ) ⋅ [ 1 ] 1 , [ s σ 1 ] 1 : = S σ 1 ( x ) ⋅ [ 1 ] 1 , [ s σ 2 ] 1 : = S σ 2 ( x ) ⋅ [ 1 ] 1 , [ s σ 3 ] 1 : = S σ 3 ( x ) ⋅ [ 1 ] 1 [q_M]_1:=q_M(x)\cdot [1]_1,[q_L]_1:=q_L(x)\cdot [1]_1,[q_R]_1:=q_R(x)\cdot [1]_1,[q_O]_1:=q_O(x)\cdot [1]_1,[s_{\sigma_1}]_1:=S_{\sigma_1}(x)\cdot [1]_1,[s_{\sigma_2}]_1:=S_{\sigma_2}(x)\cdot [1]_1,[s_{\sigma_3}]_1:=S_{\sigma_3}(x)\cdot [1]_1 [qM]1:=qM(x)⋅[1]1,[qL]1:=qL(x)⋅[1]1,[qR]1:=qR(x)⋅[1]1,[qO]1:=qO(x)⋅[1]1,[sσ1]1:=Sσ1(x)⋅[1]1,[sσ2]1:=Sσ2(x)⋅[1]1,[sσ3]1:=Sσ3(x)⋅[1]1 以及 x ⋅ [ 1 ] 2 x\cdot [1]_2 x⋅[1]2
详细的 V ( ( w i ) i ∈ [ l ] , π S N A R K ) V((w_i)_{i\in[l]}, \pi_{SNARK}) V((wi)i∈[l],πSNARK)算法内容为:
- 1)验证 ( [ a ] 1 , [ b ] 1 , [ c ] 1 , [ z ] 1 , [ t l o ] 1 , [ t m i d ] 1 , [ t h i ] 1 , [ W ϑ ] 1 , [ W ϑ ω ] 1 ) ∈ G 1 ([a]_1,[b]_1,[c]_1,[z]_1,[t_{lo}]_1,[t_{mid}]_1,[t_{hi}]_1,[W_{\vartheta}]_1,[W_{\vartheta\omega}]_1)\in\mathbb{G}_1 ([a]1,[b]1,[c]1,[z]1,[tlo]1,[tmid]1,[thi]1,[Wϑ]1,[Wϑω]1)∈G1。
- 2)验证 ( a ˉ , b ˉ , c ˉ , s ˉ σ 1 , s ˉ σ 2 , z ˉ ω , r ˉ ) ∈ F p 7 (\bar{a},\bar{b},\bar{c},\bar{s}_{\sigma_1},\bar{s}_{\sigma_2},\bar{z}_{\omega},\bar{r})\in\mathbb{F}_p^7 (aˉ,bˉ,cˉ,sˉσ1,sˉσ2,zˉω,rˉ)∈Fp7。
- 3)验证 ( w i ) i ∈ [ l ] ∈ F p l (w_i)_{i\in[l]}\in\mathbb{F}_p^l (wi)i∈[l]∈Fpl。
- 4)按照Prover端的流程,根据common inputs, public input和 π S N A R K \pi_{SNARK} πSNARK中的elements,计算challenges β , γ , α , ϑ , v , u ∈ F p \beta,\gamma,\alpha,\vartheta,v,u\in\mathbb{F}_p β,γ,α,ϑ,v,u∈Fp。
- 5)计算zero polynomial evaluation Z H ( ϑ ) = ϑ n − 1 Z_H(\vartheta)=\vartheta^n-1 ZH(ϑ)=ϑn−1。
- 6)计算Lagrange polynomial evaluation L 1 ( ϑ ) = ϑ n − 1 n ( ϑ − 1 ) L_1(\vartheta)=\frac{\vartheta^n-1}{n(\vartheta-1)} L1(ϑ)=n(ϑ−1)ϑn−1。
- 7)计算 public input polynomial evaluation P I ( ϑ ) = ∑ i ∈ l w i L i ( ϑ ) PI(\vartheta)=\sum_{i\in l}w_iL_i(\vartheta) PI(ϑ)=∑i∈lwiLi(ϑ)。
- 8)计算quotient polynomial evaluation t ˉ = r ˉ + P I ( ϑ ) − ( ( a ˉ + β s ˉ σ 1 + γ ) ( b ˉ + β s ˉ σ 2 + γ ) ( c ˉ + γ ) z ˉ ω ) α − L 1 ( ϑ ) α 2 Z H ( ϑ ) \bar{t}=\frac{\bar{r}+PI(\vartheta)-((\bar{a}+\beta\bar{s}_{\sigma_1}+\gamma)(\bar{b}+\beta\bar{s}_{\sigma_2}+\gamma)(\bar{c}+\gamma)\bar{z}_{\omega})\alpha-L_1(\vartheta)\alpha^2}{Z_H(\vartheta)} tˉ=ZH(ϑ)rˉ+PI(ϑ)−((aˉ+βsˉσ1+γ)(bˉ+βsˉσ2+γ)(cˉ+γ)zˉω)α−L1(ϑ)α2。
- 9)计算 batched polynomial commitment 的第一部分 [ D ] 1 : = v ⋅ [ r ] 1 + u ⋅ [ z ] 1 [D]_1:=v\cdot [r]_1+u\cdot [z]_1 [D]1:=v⋅[r]1+u⋅[z]1:
[ D ] 1 : = a ˉ b ˉ ⋅ [ q M ] 1 + a ˉ v ⋅ [ q L ] 1 + b ˉ v ⋅ [ q R ] 1 + c ˉ v ⋅ [ q O ] 1 + v ⋅ [ q C ] 1 + ( ( a ˉ + β ϑ + γ ) ( b ˉ + β k 1 ϑ + γ ) ( c ˉ + β k 2 ϑ + γ ) + L 1 ( ϑ ) α 2 v + u ) ⋅ [ z ] 1 − ( a ˉ + β s ˉ σ 1 + γ ) ( b ˉ + β s ˉ σ 2 + γ ) a v β z ˉ ω [ s σ 3 ] 1 [D]_1:=\bar{a}\bar{b}\cdot [q_M]_1+\bar{a}v\cdot [q_L]_1+\bar{b}v\cdot [q_R]_1+\bar{c}v\cdot [q_O]_1+v\cdot [q_C]_1 + ((\bar{a}+\beta\vartheta+\gamma)(\bar{b}+\beta k_1\vartheta+\gamma)(\bar{c}+\beta k_2 \vartheta+\gamma)+L_1(\vartheta)\alpha^2v+u)\cdot [z]_1-(\bar{a}+\beta\bar{s}_{\sigma_1}+\gamma)(\bar{b}+\beta\bar{s}_{\sigma_2}+\gamma)av\beta\bar{z}_{\omega}[s_{\sigma_3}]_1 [D]1:=aˉbˉ⋅[qM]1+aˉv⋅[qL]1+bˉv⋅[qR]1+cˉv⋅[qO]1+v⋅[qC]1+((aˉ+βϑ+γ)(bˉ+βk1ϑ+γ)(cˉ+βk2ϑ+γ)+L1(ϑ)α2v+u)⋅[z]1−(aˉ+βsˉσ1+γ)(bˉ+βsˉσ2+γ)avβzˉω[sσ3]1。 - 10)计算 full batched polynomial commitment [ F ] 1 [F]_1 [F]1:
[ F ] 1 : = [ t l o ] 1 + ϑ n ⋅ [ t m i d ] 1 + ϑ 2 n ⋅ [ t h i ] 1 + [ D ] 1 + v 2 ⋅ [ a ] 1 + v 3 ⋅ [ b ] 1 + v 4 ⋅ [ c ] 1 + v 5 ⋅ [ s σ 1 ] 1 + v 6 ⋅ [ s σ 2 ] 1 [F]_1:=[t_{lo}]_1+\vartheta^n\cdot [t_{mid}]_1+\vartheta^{2n}\cdot [t_{hi}]_1+[D]_1+v^2\cdot [a]_1+v^3\cdot [b]_1+v^4\cdot [c]_1+v^5\cdot [s_{\sigma_1}]_1+v^6\cdot [s_{\sigma_2}]_1 [F]1:=[tlo]1+ϑn⋅[tmid]1+ϑ2n⋅[thi]1+[D]1+v2⋅[a]1+v3⋅[b]1+v4⋅[c]1+v5⋅[sσ1]1+v6⋅[sσ2]1。 - 11) 计算group-encoded batch evaluation [ E ] 1 [E]_1 [E]1:
[ E ] 1 : = ( t ˉ + v r ˉ + v 2 a ˉ + v 3 b ˉ + v 4 c ˉ + v 5 s ˉ σ 1 + v 6 s ˉ σ 2 + u z ˉ ω ) ⋅ [ 1 ] 1 [E]_1:=(\bar{t}+v\bar{r}+v^2\bar{a}+v^3\bar{b}+v^4\bar{c}+v^5\bar{s}_{\sigma_1}+v^6\bar{s}_{\sigma_2}+u\bar{z}_{\omega})\cdot [1]_1 [E]1:=(tˉ+vrˉ+v2aˉ+v3bˉ+v4cˉ+v5sˉσ1+v6sˉσ2+uzˉω)⋅[1]1。 - 12)批量验证所有evaluations,判断如下等式是否成立即可:
e ( [ W ϑ ] 1 + u ⋅ [ W ϑ ω ] 1 , [ x ] 2 ) = e ( ϑ ⋅ [ W ϑ ] 1 + u ϑ ω ⋅ [ W ϑ ω ] 1 + [ F ] 1 − [ E ] 1 , [ 1 ] 2 ) e([W_{\vartheta}]_1+u\cdot [W_{\vartheta\omega}]_1,[x]_2)=e(\vartheta\cdot [W_{\vartheta}]_1+u\vartheta\omega\cdot [W_{\vartheta\omega}]_1+[F]_1-[E]_1,[1]_2) e([Wϑ]1+u⋅[Wϑω]1,[x]2)=e(ϑ⋅[Wϑ]1+uϑω⋅[Wϑω]1+[F]1−[E]1,[1]2)。
参考资料
[1] mirprotocol 2020n年6月22日博客 Fast recursive arguments based on Plonk and Halo
[2] Fluidex整理的plonk相关资料库