Router mismatch failure analysis
Symptom
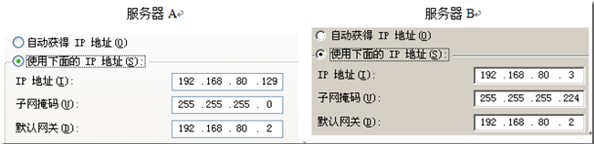
server A, B co-located in the same subnet, will be A and B communicate, but A and B can not communicate and sometimes, when checked that the subnet mask, the two servers is shown below:
basic communication between the host network may be divided into two types:
- Communication between hosts on the same network: data can be sent directly to each other without the aid of the gateway.
- Host communication between different network: data must be sent to the gateway, and then forwarded to each other through a gateway.
Fault Analysis
communication from A to B: the subnet mask 255.255.255.0 A, whereby it knows where their network network address 192.168.80.0. now it wants to transmit to B, the IP address 192.168.80.3 and a B with its own mask operation, a network address B that is located 192.168.80.0, and thus it is determined that B with their same network, may transmit data directly to B.
traffic from B to a: subnet mask of 255.255.255.224 B, whereby it knows its own network address of the network that it is now to 192.168.80.0 a send data to, the IP address of 192.168.80.129 a and B with the mask calculation, that is where a network address 192.168.80.128, and B is not in the same network, which must be by means of a gateway forwards the data to A.
Conclusion: A may be directly transmitted to the data B, which can only be forwarded to the gateway through the data A. If there is no communication between the gateway will not, A and B.
Verification failure WireShark
erection good experimental environment, collection router A, B, and MAC address of gateway
server A: 00-0c-29-bb- bb-7f
server B: 00- 0C-29-8C-BF-6D
default gateway: 00-50-56-fe-c8-98
promoter in Wireshark on server B, in communication with the ping command to A, while the communication process will Wireshark capture .ping after the command to stop the packet capture

packet analysis
The top window lists all packets caught, comprising main information are: protocol packet number, relative time captured packets, packet source address, destination address of the packet, data packets, data profile information packet size, packet.
select package 1, in the upper window will see that this is an ARP broadcast packet, the packet is sent to the server B, the purpose is to ask the MAC address of gateway 192.168.80.2 in the lower window, the first row of this package displays basic information
on server B of ping the server a, B will first go to resolve the address of the gateway
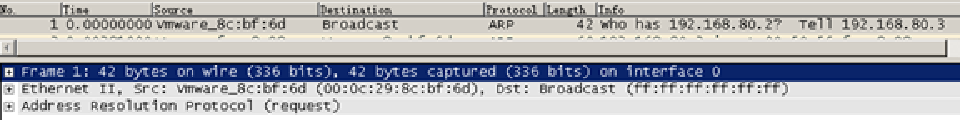
2, the packet gateway is the default response information returned tells the server its own MAC address B . Note that at the beginning of the MAC addresses have been replaced Vmware, due to the first three bytes of the MAC address represents the vendor.
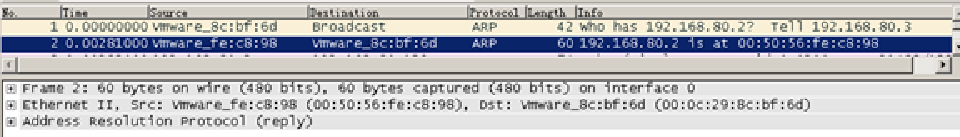
3 is a ping packet sent by the package server B, to the specified destination IP A (192.168.80.129), but the purpose is the default gateway's MAC 00-50-56-fe-c8-98, indicating that B wishes the gateway forwards the packet to A.
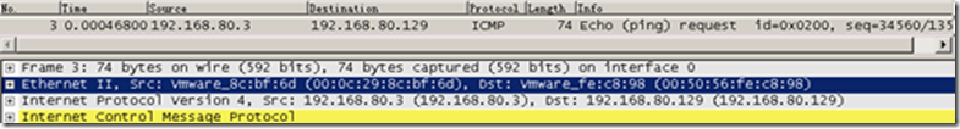
5 a broadcast ARP packet is issued, queries B's MAC address. this is because a view in, B belong to the same network, so without the help of a gateway
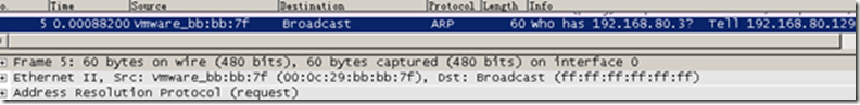
6 package B is a direct reply to the ARP request a, and tell their own MAC address a, B indicating that in the implementation of ARP replies are not considered the same network problems Although the ARP request from the other network, but still respond to protocol features -ARP
Crack passwords for sites
Whenever you hit the Enter key after you enter your user name and password on the site, in fact, your password will be sent.
If the website using HTTP (plain text format) to verify the identity of the captured traffic, after a local area network (even via the Internet) from any machine to analyze this traffic is actually very simple.
need only be located on the gateway or switch (if you gain access, traffic through their forwards, BGP router can).
you can also use pseudo Wi_Fi base station (easiest) get a website login information .
analysis of
the data packets, only the HTTP protocol POST request packet will be there user information.
To filter all traffic to identify POST data section, type in the following section filter
http.request.method == "POST"
screen shot below. It shows a POST event

analysis POST data, look for user name and password
are now mouse Right-click the line and select Follow TCP Steam

this will open a new window, the window which contains something like this:
HTTP / 1.1 302 Found
a Date: Mon, 10 Nov 2014 23:52:21 GMT
Server: the Apache / 2.2.15 (the CentOS)
X-Powered-By-: the PHP / 5.3.3
the P3P: the CP = "the COM PSAI the NOI the ADM the DEV the NAV on DEM the OUR Otro the STP IND"
the Set-cookies: = non non; Expires = Thu, 07-Nov-2024 of-23 is: 52:21 GMT; path = /
Cookies-SET: password = e4b7c855be6e3d4307b8d6ba4cd4ab91; Expires = Thu, 07-Nov-2024 of-23:52:21 GMT; path = /
SET-cookies: = sampleuser. Scifuser; Expires = Thu, 07-Nov-2024 of 23:52:21 GMT- ; path = /
the Location: loggedin.php
Content-the Length: 0
Connection: use Close
Content-Type: text / HTML; charset = UTF-8
username: sampleuser
password: e4b7c855be6e3d4307b8d6ba4cd4ab91
can guess the password value above, e4b7c855be6e3d4307b8d6ba4cd4ab91 certainly not true password value, but rather a hash value.
It should be noted that some of the passwords do not pay attention to the security of the site was not sent by the user find the value of a hash value, but directly to the password sent in the clear to the server. for this site, at this point it is possible to obtain a user name and password information. in the example of my analysis, we also need to go further, that the value of the identification code corresponding hash value.
to determine the value of the secret key hash
in this step, we will use hash-identifier tool to determine the above password hashes in the end is what type of hash. Open a terminal and enter paste "hash-identifier" and the hash value to the upper terminal, hash-identifier may match value will be given after a carriage return.

The MD5 hash value is most likely.
You can use hashcat or cudahashcat crack the MD5 hash value
can also go online to decrypt MD5: http: //www.cn.freemd5.com/index.php

Conclusion:
Currently, it is impossible to ensure that each site uses SSL to keep passwords safety, because for each URL, the service will cost money to use SSL Configuring an SSL Web site, you need to spend more than 1500USD. However, the site's developers should at least be more secure login link in the strategy to prevent the attacker from breaking site password (such as Salt algorithm)
Data flow tracking
A test case of co Skynet Security:
Hackers A through ARP spoofing, use Wireshark to obtain network traffic information across the LAN. Inadvertently, he found someone to upload a file on a Web site, but he did not know how to restore the document by Wireshark, no way, he will listen to the packet storage listen to a recording of Wireshark to help him find the file share upload it?
Case analysis process
to prepare a picture test.jpg, and allowed just looking for a site to upload, and then capture with Wireshark process will be uploaded here I have to save your file to capture the results catchme.pcapng
after opening the packet capture file , you will find the data record a total of 344. If just from the beginning to the end to a one of the audit is a very laborious thing.
using a display filter to filter, because the upload files using the HTTP protocol, so using filtering rules " http ", after filtering discovery packets from the original 344 became 137, so it is easy. after analysis, see upload the word info in Article 209 of the packet, the suspect this is related to upload packets.

relating to the collection of uploaded data packets

because the files are uploaded using the POST method, so we can use the filtering rules "http.request.method == POST" for more accurate filtering, then only 47 data package.
While there is upload the POST method to see the keywords, there is, but it does not determine that the request is not really upload files. No. 209 Double-specialized packet analysis, the data in the application layer can be seen indeed upload files, and file name is test.jpg.

Can be seen in the transport layer portion, since the file is large, TCP protocol divided into 16 data segments segment, each segment is a separate packet, click on each Frame, you can see the contents of the data packet.

The problem is that each packet contains only a portion of the upload file, in order to restore a file upload, these must be fragmented packets are reassembled into a whole. In Wireshark provides a "data flow tracking" function, since you can accomplish this task. Back to Wireshark's main interface, right click and select "Track stream / TCP flow" on the No. 209 packet,

then the whole TCP stream will be displayed in a separate window, we note that the file in this window displayed in two colors, red is used to indicate the flow from the source address access to the destination address, and blue to distinguish the opposite direction i.e. the flow rate from the destination address to the source address. here the color indicia to which side to start communication subject, under normal circumstances are initiate connection to the server by the client, it will mostly communications client shown in red.

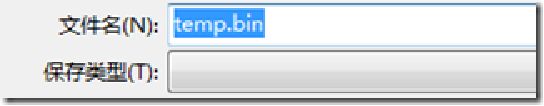
save the data stream into the original file, for further processing. It should be noted that, be sure to set the display format of the data before saving "raw data."
 Here the extension of the file specified as a .bin, in a preserved as a binary file.
Here the extension of the file specified as a .bin, in a preserved as a binary file.
Use WinHex tool to restore the original picture data
will be saved before temp.bin with WinHex open, you can see the file contains HTTP request information and our image info , as well as the tail end of the file information. we need to do is to determine the original image file header and tail, and get rid of excess parts.

back to Wireshark, you will see we have just the data stream on the head portion of the picture

in the Content-Type: there are two line breaks image / pjpeg later, in the original file with a newline character hexadecimal representation is "0D 0A", because there are two, so we look for "0D near the picture name test.jpg 0A 0D 0A ", it means the back part of the beginning of the picture.

return to wireshark, we take a look at the tail portion of the picture after the transfer is completed. You can see, this is a line break, some back end of the file "-------------."

Original file delete them

This time our files on only the contents of the original image, and save the file as test.jpg.

An electricity supplier website traffic hijacking case study
Symptom
day visit at the home of a regular electricity supplier J shopping site, the browser suddenly found suddenly jumped to third-party sites back to J, and my heart first reaction is Trojans.
Analyzed
first in reproduction Ethereal case, J network does return some JavaScript to make the browser to jump to the yiqifa.com. the figure is the packet capture application layer.

Code returned by the server causes a jump, you can exclude the local Trojans, presumably network or server The problem. According to experience, this situation is very likely that the traffic on the link hijacking attacks. Of course we can not rule J web server was hacked situation.
Continue troubleshooting. The application layer has to die, to use Wireshark packet grasp the network layer.

From the Wireshark the results can be seen, there have been two J HTTP response on the web site: # 97 and # 101 No messages.
the first 97 # first, the browser execute JavaScript code inside to the yiqifa.com;
second 101 # HTTP because a late response, are ignored by the system (identified as the Wireshark-of-Order OUT).
HTTP response packet two site J, a necessarily a true or false. look at the two IP header of the HTTP response. the first TTL value is 252 packets, the second packet TTL value is 56, and the TTL value before the TCP three-way handshake server when J is 56, so the packet is based on first-forged, true late packet is ignored by the system .

So far, confirmed hijacking on the link.
attack analysis
Forged packet TTL value is 252, which means it's original TTL value should be 255 (252 is greater than the system default TTL value is only 255, and generally does not modify), it indicates that the attacker's device away from me across the route 3; and J normal HTTP Web site 56 in response to a TTL value, every eight routes. Physically fake device closer to me, so fake HTTP response will first come - more interesting is that, when the actual monitoring also found fake packets arrive late lead to failure of the hijacking
guess is that all the data a bypass device listens package, please find J Home HTTP requests immediately return a good custom HTTP response. Approximately attacks diagram below.

Speculated that the attacker on the link to go to war should not be only for a website, so he visited several other well-known electronic business website and found several of which electricity supplier is also subject to the same attack. the flow looks hijacking purpose is to guide traffic to the site electricity supplier rebates Union, to obtain the current user rebate rebate turnover by the league.
basic operators have confirmed the problem, but was unable to confirm the operator's official deliberate or hacker attack or insiders secretly engage
attack source location
to look at the time of route results:

if the initial TTL value to count by 255, HTTP packet arrived to the unit 252, calculate elapsed 3 (255-252) a routing problem areas in the vicinity of the four routes, that is 119.145.220.86 here,
although the basic can confirm that the fourth question in the vicinity of the route (several days I get caught, forged HTTP response packet TTL value has been 252), but does not rule out a device deliberately constructed initial TTL value (for example, set to 254) to increase the difficulty of tracing, in order to avoid rigorous scholarship and Enchanted attacker, so the evidence should take real.
Positioning hijackers Location:
Since the attack packets listening device is bypassed, it can be speculated that the package is based on the state rather than attacks, we construct the intercepted data packets (ie issuing direct access to the electricity supplier J Home HTTP request TCP packet, do not need three times handshake) repeatedly transmitted, TTL value is incremented from 1 accurately transmitted data packets to each path, until the response to the occurrence forgery - no problem is not responsive to the position, the position of the first occurrence of a response is counterfeit the location of the problem
this time need a packet construction tool, and then all the way to the past, TTL value is equal to 4 times the response packet forgery emerged - confirm that the fourth-hop routing problems, and at the same time 119.145.55.14 reply the Time-to-live Exceeded ICMP packets.

offensive and defensive road
link hijacking of businesses and users are very troublesome, affect the user experience, but also the leakage of sensitive information, but also the sub-region, but also relatively difficult to detect and defense together. Link hijacking has been using some of the people reached a pinnacle. Such as the recent discovery Baidu Union advertising industry script section area is malicious JavaScript to DDoS attacks GitHub.
There are operators of the region and link hijacking DNS hijacking, DNS Server area operators were cache poisoning attacks (exploit CVE-2007- 2926, very classic), developer of implantable hijack code routing software, CDN has been the source of communication with the ARP attack, the Trojans local PC user. of course, these have been resolved at present, also continued monitoring.
in order to combat link hijacking, using HTTPS or proprietary protocols.
Link hijacking
TCP link hijacking attacks
TCP link hijacking in fact, refers to listen on a network link, forged TCP packets, to control the behavior of the target network link. The most common is the realization of certain devices to access the site of illegal interception, as well as operators of some parts of the page placement behavior.
Because the WAN link hijacking the impact was large, generally affects a region or even a country, so this article focuses on TCP link WAN hijacking, hijacking, such as LAN ARP attack outside the scope.
Currently found in TCP link hijacking attacks generally come in two forms:
disrupting access type (divided into one-way and two-way contract contract)
page replacement-type
interrupt access type:
disrupting access type common to block access to certain sites, such as certain equipment prevent users from accessing certain sites, the operators of a multi-terminal prohibit ADSL Internet access. The principle is the server to the user forged RST packet sent prevent the establishment of the TCP connection (unidirectional contract). Some devices done relatively hard, posing as a server to the user at the RST packet sent from users, while also posing RST packet to the server (two-way contract).
replace page type
common in the operator product placement, there are tampered with normal web page SEO, cheat traffic. Worst than fishing, such as 2011, there have been a number of Gmail fishing events and fishing events can not be advertised. Principle is simple, that is, after a forged HTTP request server HTTP response to the client.
Shown in the figure is a typical TCP hijacking Alternatively link page can be seen that the TCP three-way handshake is completed, the HTTP request packet transmission, two HTTP client receives the response packet, the first packet as forged (No. 10) first, the second normal HTTP response packet (13) is a client ignored. obviously, there are on the web a device that listens for the entire session, when matching a feature on the first to contract hijack the session.

using the link hijacking pop ads, misuse resulting "technical problems" block, accidentally implanted the code page mess, even fishing and will damage the interests of users.
To solve the hijacking must first find out whether the link is a link hijacking, and if so, where is the problem approximate location? Link hijacking is regional, in general, a regional user focus of complaints, you can contact a user survey.
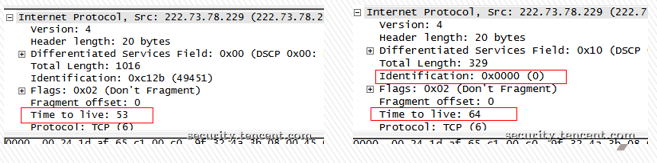
After the catch suspicious package focused on two key points: TTL value and IP id (Identification) based on actual observations, forged. id TCP packet and the TTL value is not logical.
TTL below the real packet is 53, id is sequentially incremented, and the TTL of the packet is forged 64, id is always 0. also seen somewhere multi-carrier ADSL terminal prohibit Internet access feature forge id value constant at 8888 RST packet.
can be substantially listening position location device by forging TTL value. TTL value using a forged packet plus the time a user can locate routes: route each packet through a TTL value will be decremented by one, to find fake packets, TTL (TTL are generally given an initial 128 or 64 or 256) reduce the number of anti push back to find the location of the problem.
screenshot of forged TCP TTL is 64, it may be presumed link hijacking took place in the LAN, this is a case of hijacking link router software
if Some clever attacker, a customized TTL value, this makes it difficult to pinpoint. For example, some devices will be issued three times a RST packet, the TTL is different each time. Note here that the "difficult position" not "can not be located," there are ways, you need to use your head.
Bidirectional RST, deployment in IDS room can also be found clues.
If it is replaced by a page-type attacks, or the number of hash page HTML elements have abnormalities, which also can be used as a detection point
guard link hijacking is more difficult, after all, the attacker controls the network link but not impossible.
First, the whole site using Secure Sockets layer (SSL).
another is the client or (and) server dropped forged TCP packets, such as one-way in front when it comes to disrupting access type attack, it can discard contain characterized forged TCP packets (e.g., Id is 0 or 8888).
Finally, a wide area network that is not safe, so be sure to encrypt the transmission of sensitive information, but also high-strength encryption; automatic upgrade program is also necessary to verify the signature file.
