background:
Micro-channel fast login, obtain the user's phone number.
Micro-channel public platform to explain:
For security reasons, open micro-channel data transmitted to the encryption server via a server developer, the developer then needs to open the data obtained by the decryption.
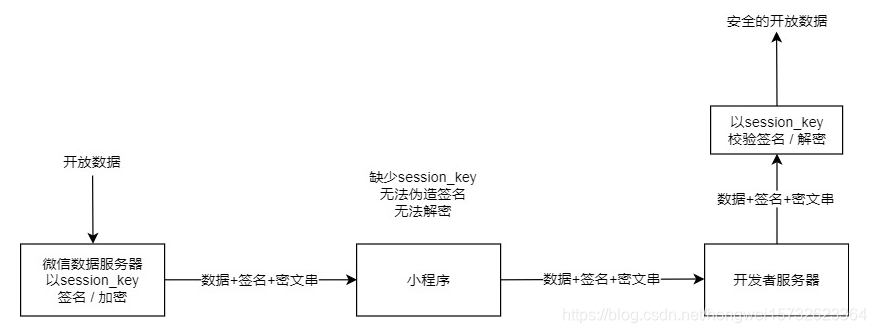
The micro-channel public internet applet explained, as follows:
1, the distal end need to call wx.login () , Get code;
2, using the micro-code calling channel interface to obtain session_key of: https://developers.weixin.qq.com/miniprogram/dev /api/open-api/login/code2Session.html
. 3, the encrypted data provided by the front end and iv encryptedData
reference: Gets phone number
4, obtained by the above encryptedData, session_key of, iv decrypting
/**
* 解密获取信息
*/
public static JSONObject getUserInfo(String encryptedData,String sessionkey,String iv) {
// 被加密的数据
byte[] dataByte = Base64.decode(encryptedData);
// 加密秘钥
byte[] keyByte = Base64.decode(sessionkey);
// 偏移量
byte[] ivByte = Base64.decode(iv);
try {
// 如果密钥不足16位,那么就补足. 这个if 中的内容很重要
int base = 16;
if (keyByte.length % base != 0) {
int groups = keyByte.length / base + (keyByte.length % base != 0 ? 1 : 0);
byte[] temp = new byte[groups * base];
Arrays.fill(temp, (byte) 0);
System.arraycopy(keyByte, 0, temp, 0, keyByte.length);
keyByte = temp;
}
// 初始化
Security.addProvider(new BouncyCastleProvider());
Cipher cipher = Cipher.getInstance("AES/CBC/PKCS7Padding", "BC");
SecretKeySpec spec = new SecretKeySpec(keyByte, "AES");
AlgorithmParameters parameters = AlgorithmParameters.getInstance("AES");
parameters.init(new IvParameterSpec(ivByte));
cipher.init(Cipher.DECRYPT_MODE, spec, parameters);// 初始化
byte[] resultByte = cipher.doFinal(dataByte);
if (null != resultByte && resultByte.length > 0) {
String result = new String(resultByte, "UTF-8");
return JSONObject.parseObject(result);
}
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
} catch (NoSuchPaddingException e) {
e.printStackTrace();
} catch (InvalidParameterSpecException e) {
e.printStackTrace();
} catch (IllegalBlockSizeException e) {
e.printStackTrace();
} catch (BadPaddingException e) {
e.printStackTrace();
} catch (UnsupportedEncodingException e) {
e.printStackTrace();
} catch (InvalidKeyException e) {
e.printStackTrace();
} catch (InvalidAlgorithmParameterException e) {
e.printStackTrace();
} catch (NoSuchProviderException e) {
e.printStackTrace();
}
return null;
}
problem
1, need to be buffered acquired sessionkey tip call wx.login () code acquired acquiring sessionkey holding the rear end code; if acquired with the repetition code, error code been used.
2, decryption method common mistakes:
①ValueError: IV the MUST BE 16 bytes Long
resolve: to fight binary
②pad block corrupted
Solution: The reason is sessionkey date and needs to reacquire
Reference:
get the phone number
