Level protection system involved
Level protection system involved
December 1, 2019 2.1 grade protection system was introduced, then the system-level protection system, which included it in the end? Today a small article to let everyone know the next!
System-level protection system involves systems involved are: operation and maintenance of safety management systems OSM, log audit system LAS, baseline verification system BVT, one-way security isolation and information into the system (shutter) FGAP and so on.
Operation and maintenance of the safety management system OSM
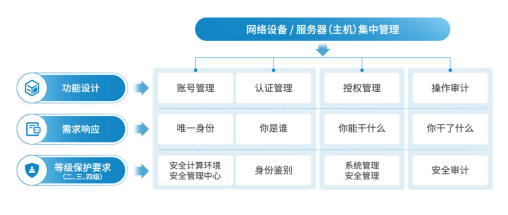
Network information security level protection operation maintenance and safety management system OSM focus on operation and maintenance and safety management, is a set of account management, authentication, single sign-on, resource authorization, access control and audit operations as one of the new generation of operation and maintenance of security audit products . It enables efficient operation and maintenance operations audit of government and enterprise IT assets (such as servers, network devices, security devices, databases, etc.) during operation, the operation and maintenance audit by the event auditing enhance audit operation content, through internal management platform advance the prevention and control and post-audit and comprehensive solution to government and enterprise operation and maintenance of security issues, and to improve IT operations management level government and business.
Network information security level protection operation and maintenance of the safety management system OSM User Manual
Log audit system LAS
Level of protection in 2.0, starting from the second stage explicit requirements "to deal with the health network equipment network systems, network traffic, user behavior such as logging, audit records should include the date and time of the event, user, type of event, whether the event was successful and other information related to the audit. "
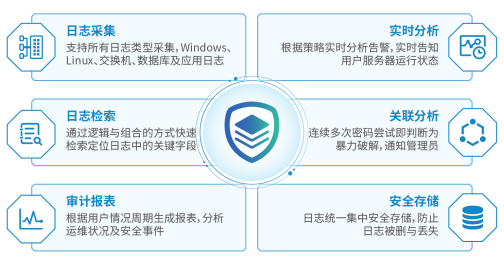
Log audit system is deeply convinced the introduction of professional information security audit products, system by system security event monitoring and collection information system, user access, and logs, system status and other information, through standardization, filter, merge and alarm post-processing analysis, centralized storage and management in order to form a unified log format, combined with extensive log statistical summary and comprehensive analysis capabilities, achieve a comprehensive audit of the overall information security system. Log lifecycle management model provides intelligent system audit logs, set log data acquisition, real-time dynamic analysis, secure storage management, retrieval of historical events, a comprehensive audit reporting functions, to help users quickly and efficiently complete the information system security audit.
Network information security protection log audit system LAS User Manual
Baseline verification system BVT
Network information security baseline verification system to solve major companies are increasingly onerous security vulnerabilities and security configuration management, configuration to achieve a variety of intelligent vulnerability (vulnerability, configuration compliance, change) the discovery, centralized and orderly operation and maintenance. Comprehensive centralized security vulnerability exists scan and analyze various types of user information systems or equipment, with automated collection, analysis, and reporting capabilities. Business as a user, automatically complete security experts ever need to complete risk analysis, to provide comprehensive, detailed, clear inspection reports, and can compare different test results.
Network Information Security Protection baseline verification BVT user manual

Security isolation and information exchange systems (gatekeepers) the GAP
Network Information Security Protection Gatekeeper uses "2 + 1" system architecture, from the inside, the external host unit and a data exchange unit (isolation switch chip) consisting of three parts, based on a multi-core multi-thread private private secure operating system, similar lock works, including ferry, ferry application data between external host, network security isolation at the same time to do real-time data exchange. SANGFOR gatekeeper function product innovation, from the initial simple file exchange capabilities, and gradually increase the complexity of database synchronization, video platform cascade, multicast agent functions to meet different business systems data sharing, video networking, radio and television broadcasting complex network data exchange network isolation requirements of the exchange.
网络信息安全等级保护安全隔离与信息交换系统GAP用户手册

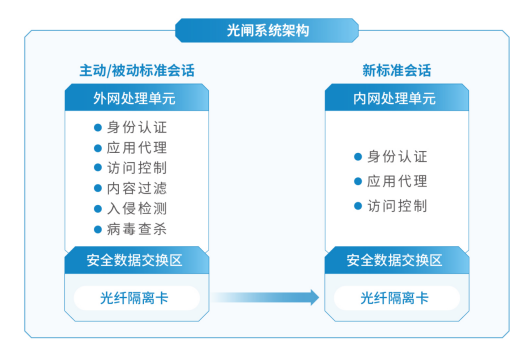
安全隔离与信息单向导入系统(光闸)FGAP
针对安全要求极高且数据单向导入的需求场景,深信服研发并推出深信服安全隔离与信息单向导入系统(简称“单向光闸”)。
基于SFP光模块中发光器和收光器分离的技术特点,深信服单向光闸的两个主机之间只是通过外网主机光模块的一个发光器与内网主机光模块的一个收光器连接,从而从物理原理上实现了数据的绝对单向传输。基于单向传输部件,结合传统安全隔离网闸的“摆渡+代理”技术,单向光闸在保证单向数据传输的同时,保证数据的实时、准确、可控传输。
网络信息安全等级保护安全隔离与信息单向导入系统FGAP用户手册