01. The origin of graded protection in my country
Regulations of the People's Republic of China on Security Protection of Computer Information Systems
1994.2.18, State Council Order No. 147 Article 9 Computer information systems implement security level protection. The classification standards for safety levels and specific measures for safety level protection shall be formulated by the Ministry of Public Security in conjunction with relevant departments.
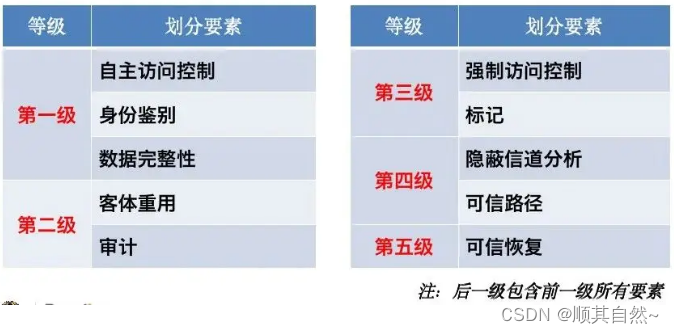
GB 17859 Criteria for Classification of Security Protection Levels of Computer Information Systems Released on 1999.9.13, implemented on 2001.1.1 into 5 levels:
The first level: user independent protection level; the second level: system audit protection level; the third level: security mark protection level; the fourth level: structured protection level; the fifth level: access verification protection level.
Elements of GB 17859 safety level classification
02. Level protection authorities
Ministry of Public Security
- Cyber Security Bureau
- Information Security Level Protection Assessment Center
Provincial Public Security Department
- Network Team – Evaluation Organization Management
Prefecture-level public security bureau
- Cyber Security Team – Filing and Inspection
03. Level protection policy
Cybersecurity Law of the People's Republic of China
2017.6.1 Implementation of Article 21 The state implements a network security level protection system. Network operators shall, in accordance with the requirements of the network security level protection system, perform the following security protection obligations to protect the network from interference, damage or unauthorized access, and to prevent network data from being leaked or stolen. Tampering: (1) Develop internal security management systems and operating procedures, determine the person in charge of network security, and implement network security protection responsibilities; (2) Take measures to prevent computer viruses, network attacks, network intrusions and other hazards Technical measures for network security behavior; (3) Take technical measures to monitor and record network operating status and network security events, and retain relevant network logs for no less than six months in accordance with regulations; (4) Take data classification and important data backup and encryption and other measures; (5) Other obligations stipulated in laws and administrative regulations.
Several terms in the Network Security Law (1) Network refers to a network consisting of computers or other information terminals and related equipment that collects information in accordance with certain rules and procedures , storage, transmission, exchange, and processing systems. (2) Network security refers to taking necessary measures to prevent attacks, intrusions, interference, destruction, illegal use and accidents on the network, keeping the network in a stable and reliable operating state, and ensuring the integrity and confidentiality of network data , usability capabilities. (3) Network operators refer to the owners, managers and network service providers of the network. (4) Network data refers to various electronic data collected, stored, transmitted, processed and generated through the Internet.
rules and regulations
- Information Security Level Protection Management Measures (Gongtongzi [2007] No. 43)
- Grading – Filing – Construction Rectification – Evaluation – Supervision and Inspection
- Measures for the Management of Network Security Level Protection Evaluation Institutions (Gongxinan [2018] No. 765)
- Recommended directory of evaluation agencies
- Evaluator management
- http://www.djbh.net
- Regulations on Cybersecurity Level Protection (Draft for Comments)
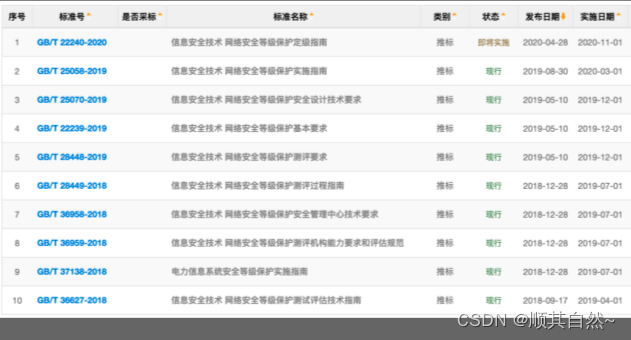
Level protection standardsThe standards for network security level protection are roughly divided into two categories: national standards and industry standards. The figure below lists 10 commonly used and important standards for network security level protection.
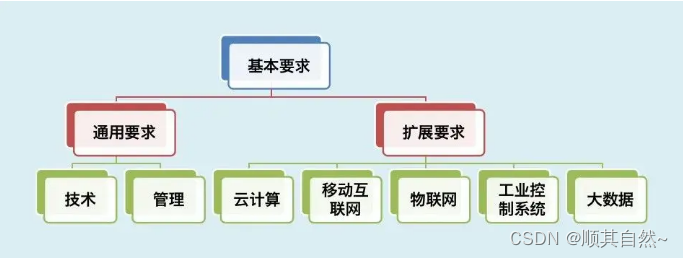
04. GB/T 22239 Basic requirements for network security level protection
1 Scope
This standard specifies the general security requirements and security extension requirements for the first to fourth level protection objects of network security level protection. This standard is applicable to guide the safety construction and supervision and management of hierarchical non-confidential objects. The safety requirements for Level 5 protection objects are not described in this standard.
Several terms of GB/T 222393.1 Cybersecurity takes necessary measures to prevent attacks, intrusions, interference, destruction, illegal use and accidents on the network. The network is in a state of stable and reliable operation, as well as the ability to ensure the integrity, confidentiality, and availability of network data. 3.2 Security protection ability security protection ability refers to the degree to which the security protection ability can resist threats, detect security incidents, and restore the previous state after being damaged. 5.1 Level Protection Objects Level protection objects refer to objects in network security level protection, usually consisting of computers or other information terminals and related equipment that collect, store, transmit, exchange, and process information in accordance with certain rules and procedures. Systems mainly include basic information networks, cloud computing platforms/systems, big data applications/platforms/resources, the Internet of Things, industrial control systems and systems using mobile Internet technology, etc. The level of protection objects is based on their importance in national security, economic construction, and social life, and the degree of harm to national security, social order, public interests, and the legitimate rights and interests of citizens, legal persons, and other organizations after being destroyed, from low to High is divided into five security protection levels.
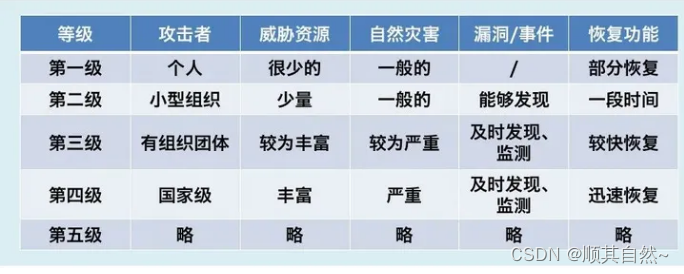
GB/T 22239 five levels of security protection capabilities
GB/T22239 general requirements and extended requirements
05. GB/T 22240 Network security level protection grading guide
1 ScopeThis standard provides the security protection level grading method and grading process for level-protected objects that do not involve state secrets. This standard is applicable to guide network operators in grading protection objects that do not involve state secrets.
Grading elements and safety protection levels of GB/T 22240

The grading process of GB/T 22240 (Level 2-Level 4)General process of grading work for graded protection objects:
Determine the grading object → Preliminarily determine the grade → Expert review → Approval by the competent department → Filing and review
Grading objects of GB/T 22240

Grading method of GB/T 22240
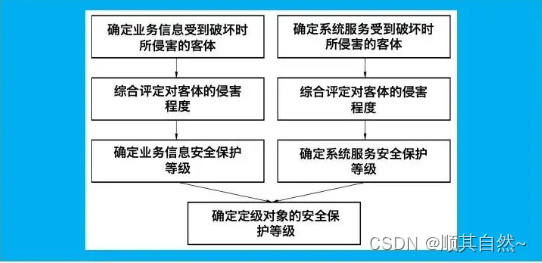
06. Summary
Working framework for hierarchical protection
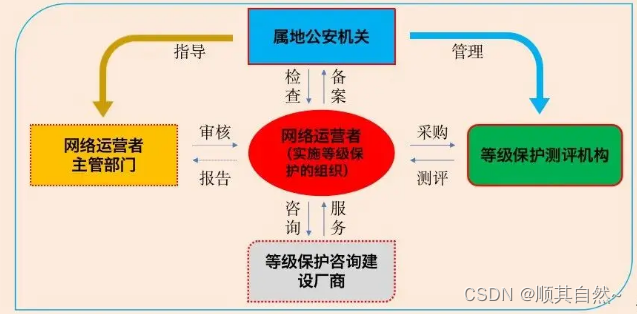
"Network security level protection" is a basic system in the field of network security established by our country in accordance with the law; the network security law applies to all types of legal entities at all levels.
The main contents of the "network security level protection" work include:
For network operators: rating, filing, construction and rectification, application for evaluation
For public security organs: filing and approval, supervision and inspection
For assessment agencies: Implement assessment
Reprinted from:Powertime Shared Classroom | Basics of Network Security Level Protection - Zhihu