"Built on Snort + Guardian + Iptables of the IPS"
2020 On the third day, as usual, still writing articles, sharing following the "A recent project for small and medium enterprise-class firewall deployment after" the other part " built on Snort + Guardian + Iptables of IPS ", later will complete the entire open-source project Share out, welcome everyone to share exchange
IPS
About IPS
IPS is in English "Intrusion Prevention System" abbreviation, Chinese meaning "intrusion prevention systems", is a network security device or software application, in addition to monitoring detection of IDS, but also has depth perception test data traffic, malicious packets discarded, real-time alerting and blocking intrusion prevention system.
IPS functional components
数据采集:采集和捕获流量数据
入侵检测:分析流量和日志数据,发现安全异常行为并发出警报,常见的有Snort、Suricata、Bro
结果展示:用于分析IDS警报并进行友好展示,常见的IDS警报分析工具有Snorby、Sguil、Base
安全防御:主动响应安全事件,阻断攻击者入侵行为,常用iptablesIDS
IDS is in English "Intrusion Detection Systems" abbreviation, Chinese meaning "intrusion detection system", is a network security device or software application, you can, for the health of the network, system monitors in accordance with certain security policy, found as much as possible a variety of attack attempts, aggressive behavior or attack the results and issue security alerts.
IDS general system model
(1) Data Collector (also known as detectors): mainly responsible for data collection. The input data stream includes a detector system data may include any intrusion clues, such as a variety of network protocol packets, system calls and file system log records. The probe data is collected, and then sent to the detector for processing.
(2) detector (also known as the analyzer or detection engine): Responsible for analysis and intrusion detection tasks, and to signal an alarm controller.
(3) Knowledge: providing the necessary support for the data detector and a controller. This information includes: user activity history files or detection rule sets and so on.
(4) Controller: The detector is sent from the alarm signal manually or automatically respond to the intrusion.
IDS Category
IDS are classified according to two methods: According to the data sources, in accordance with the intrusion detection strategy.
According to sources of data classification
基于网络的入侵检测系统(NIDS)
基于主机的入侵监测系统(HIDS)
分布式入侵检测系统(DIDS)According to classify intrusion detection strategy
滥用检测
异常检测
完整性分析Environment to build
Enterprise Topology

Preparing the Environment
DMZ区:CentOS7 --- IP:192.168.9.100 Gateway:192.168.9.254
防火墙:kali --- ip1:211.67.93.254;ip2:192.168.9.254;ip3:192.168.33.254;
外网主机:win2003 --- IP:211.67.93.100 Gateway:211.67.93.254
内网主机:win2003 --- IP:192.168.33.100 Gateway:192.168.33.254IDS Snort
Snort Profile
In 1998, Martin Roesch developed using C language open source (Open Source) intrusion detection system Snort. Even today, Snort has developed into a multi-platform (Multi-Platform), real time (Real-Time) traffic analysis, a powerful network intrusion detection characteristics (Pocket) records the IP packet network / prevention systems (Network Intrusion Detection / Prevention System), i.e. NIDS / NIPS. Snort in line with the General Public License (GPL - GNU General Pubic License) , Snort can be obtained online by downloading free, and only takes a few minutes to install and start using.
Snort has three operating modes: sniffer, packet logging, a network intrusion detection system. Sniffer mode only read packets from the network as a continuous stream and displayed on the terminal. A packet recording mode to record the data packets to the hard disk. Network intrusion detection mode is the most complex, and is configurable. We can make snort analyze network data stream to match the number of user-defined rules, and to take certain actions based on test results.
Snort installation
Mounting system Kali
the Snort installation generally divided source compiler installation and package manager installed in two ways. Download the source code would be more complicated to use, but the document is complete, debug convenient; and Package Manager is easy to install, a command to solve all problems
apt-get install snortSnort configuration
Set Rule Path
Modify the configuration file
/etc/snort/snort.conf
View Rules

PS: After the default Linux install Snort log path, etc. will default configuration is good, no trouble Configuration
Snort start
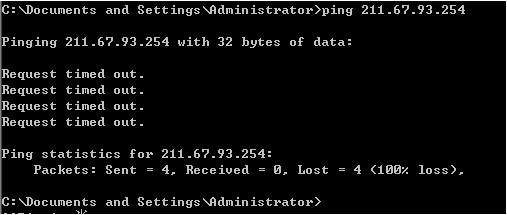
snort -i eth1 -c /etc/snort/snort.conf -A fast -l /var/log/snort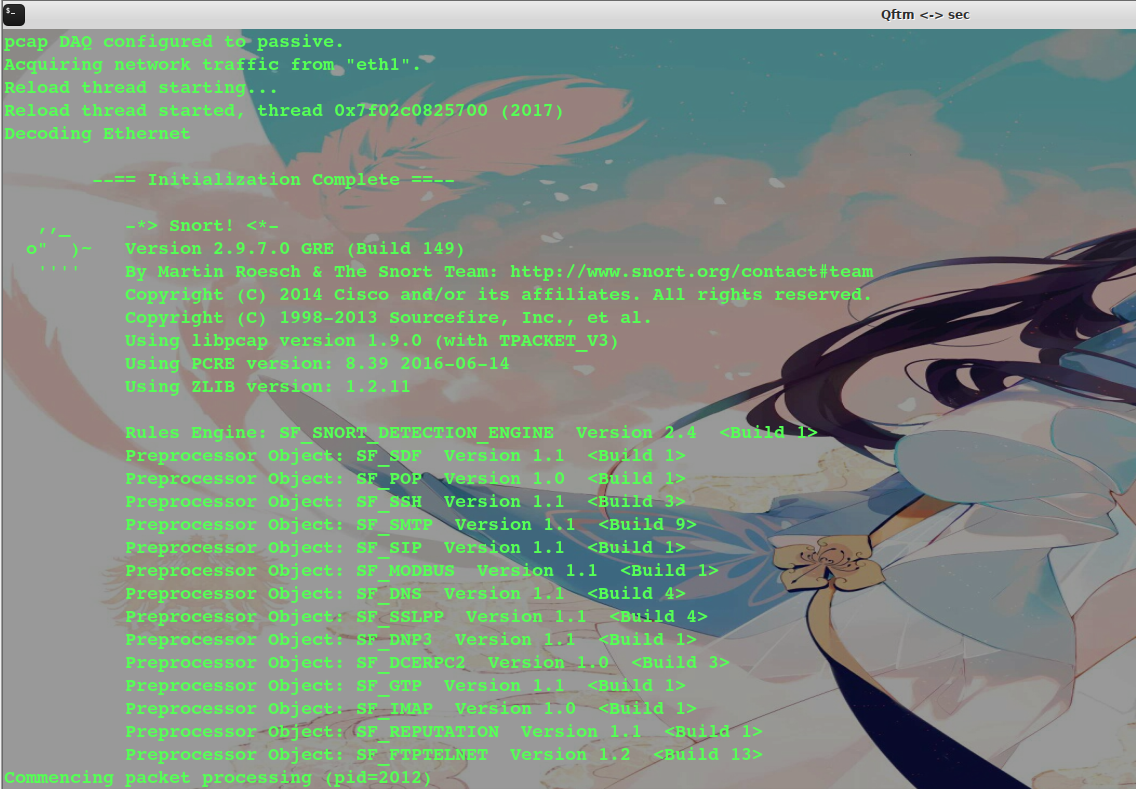
Snort test
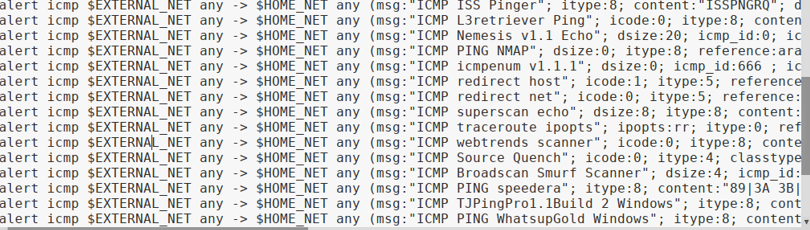
Review the default Snort ICMP rules
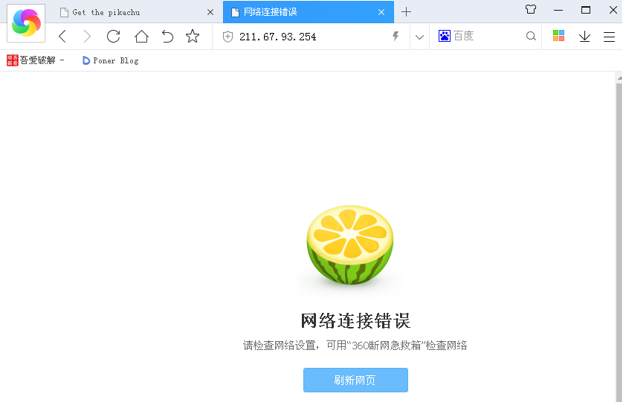
Test the external network ping DMZ area of the Web server
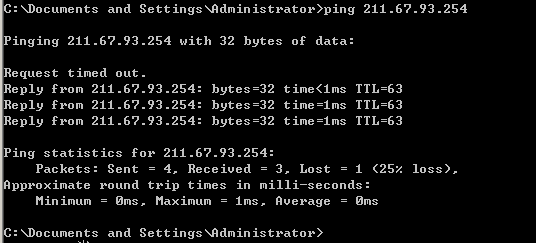
View IDS logging
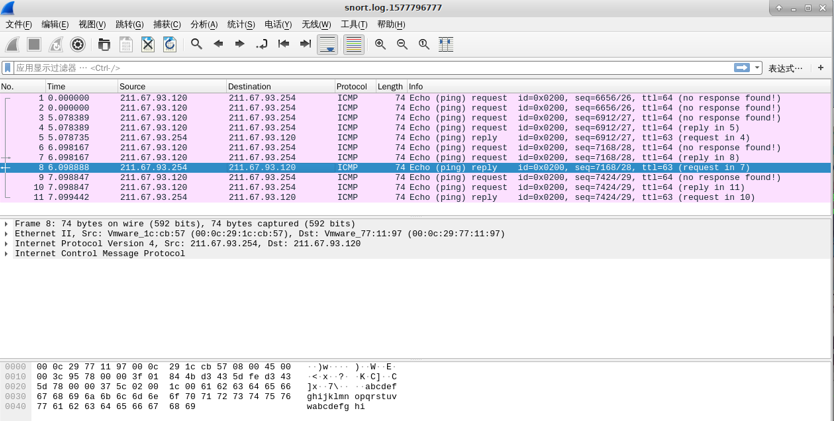
Analysis found the log, allowing the Snort by ICMP, and recorded data of ICMP.
Guardian
Guardian linkage effects achieved Snort + Iptables
Guardian Download
Guardian need Quguan network download
http://www.chaotic.org/guardian/Guardian installation
Download after decompression
tar -zxvf guardian-1.7.tar.gz
Move to the next guardian snort && && create a list of the log
→ Qftm ← :~/桌面# mv guardian-1.7 /etc/snort/
→ Qftm ← :~/桌面# touch /etc/snort/guardian-1.7/guardian.ignore 创建白名单
→ Qftm ← :~/桌面# touch /etc/snort/guardian-1.7/guardian.target 创建黑名单
→ Qftm ← :~/桌面# touch /var/log/snort/guardian.log guardian的日志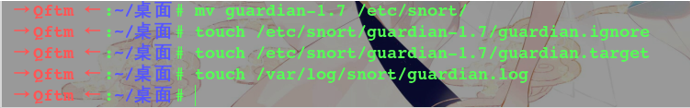
Copy the script block
→ Qftm ← :/etc/snort/guardian-1.7# cp scripts/iptables_block.sh /usr/local/bin/guardian_block.sh
→ Qftm ← :/etc/snort/guardian-1.7# cp scripts/iptables_unblock.sh /usr/local/bin/guardian_unblock.sh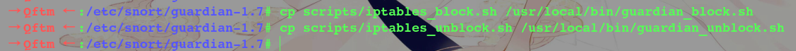
This operation is provided in order to meet the guardian.pl \ (blockpath and \) unblockpath path
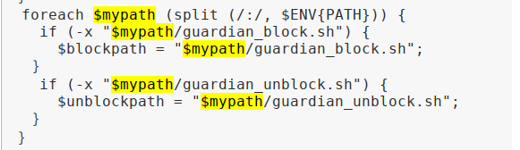
PS:
(1)Guardian的执行文件 guardian.pl
(2)Guardian封锁IP所要调用的外部程序 scripts/iptalbes_block.sh
(3)Guardian解除对某一IP封锁时,所需要调用的外部程序scripts/iptalbes_unblock.shGuardian Configuration
Configuration guardian.conf
Interface eth1
HostGatewayByte 1
LogFile /var/log/snort/guardian.log
AlertFile /var/log/snort/alert
IgnoreFile /etc/snort/guardian-1.7/guardian.ignore
TargetFile /etc/snort/guardian-1.7/guardian.target
TimeLimit 86400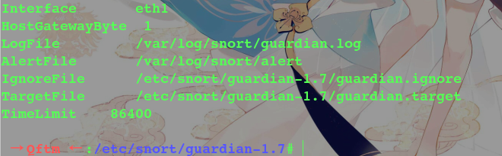
PS:
TimeLimit:在多少秒后解除对IP的封锁,86400秒也就是24小时之后解除对IP的封锁。
AlertFile:警报信息,前提是snort以alert_fast输出报警信息Configuring guardian_block.sh rules and guardian_unblock.sh
Preparation of policy files, configuration intercept foreign invaders and release strategy
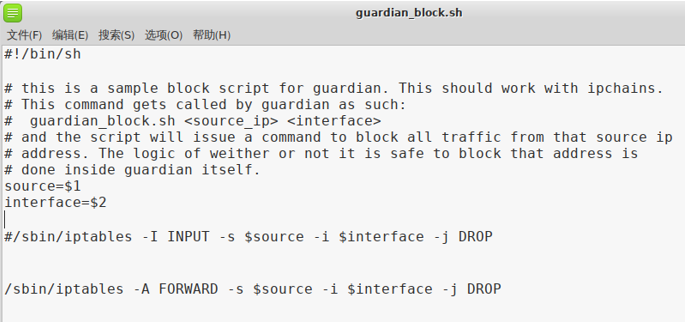
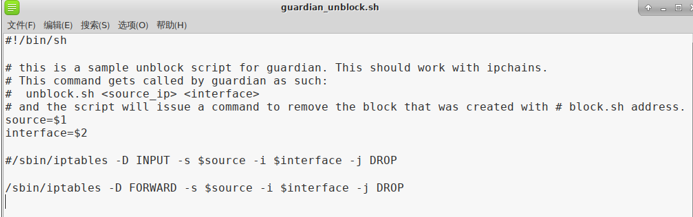
Guardian start
→ Qftm ← :/etc/snort/guardian-1.7# perl guardian.pl -c guardian.conf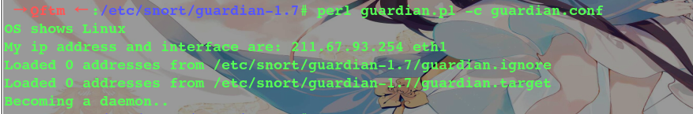
IPS Test
External network attacker to attack Web servers

IPS detection & interceptor
IPS detection
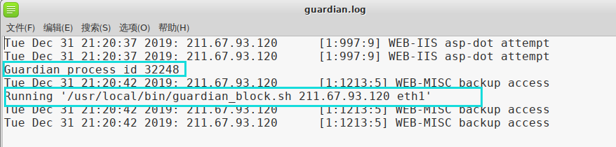
IPS interception
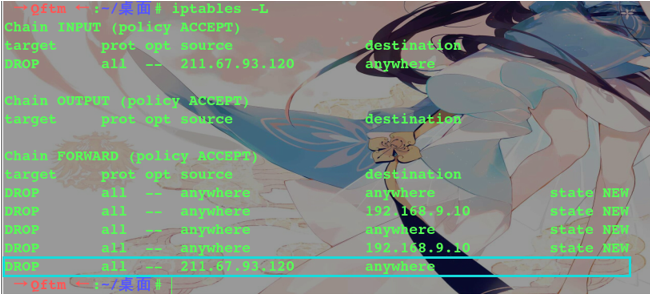
From the above, the external attacker intercepted IPS restrict access to records