Common security issues
Cross-site scripting XSS attacks
Cross-site request forgery attack CSRF
Cookies front-end security
Clickjacking attacks
Transit security issues
User password security
SQL injection attacks
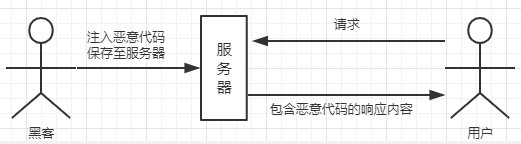
XSS (Cross Site Scripting) Cross-Site Scripting Attacks
What is XSS
Another web attacks, successfully executed by injecting executable code page (html code or JS code) browser
Conditions embodiment XSS attacks have
- Web pages need to be able to inject malicious code (input box, url)
- Malicious code can be executed successfully browser
XSS Attacks
User incoming data is treated as a program, it will execute the program
Why can XSS
- Get the page data: you can get the value specified by the document elements, such as access to the user name, phone number, address, website, etc. [steal any data including user data]
- Get cookies: you can get all the current cookies by document.cookies website, to steal the currently logged on user's login state, thereby posing stolen user login website background management system [even steal user passwords and login state]
- Hijacking front-end logic: can modify the content of a feedback operation, such as clicking a button which should only submit a request, but may be tampered with by the script XSS request address, and then transmits the information submitted by the user interface to the attacker package; or change the user's page jump [deceive users, traffic hijacking]
- Send Request: An attacker can send a request to allow the user to collect user information without the knowledge of
XSS attacks
- Reflective XSS: when a user accesses a link has been tampered with after the attacker, implanted script will be executed the user's browser, also known as non-persistent type because it is a one-time, only have an impact when the page access times
- Reflective XSS scenario: turn into short chain link with XSS script; [in] url followed xss script, a URL jump
- The script will automatically execute when the contents contain XSS attack scripts will be stored on the server side, also known as persistent type, the user reads the content: storage type XSS
- Storage type XSS scenario: a message other users to view other people's posts, comments, administrators announcement, the hacker posted a blog post; feedback, complaints function, chat function
XSS attacks injection point
- HTML node content: dynamically generated, comprising a user input, such a script containing XSS
- HTML attributes: where the user needs as the img src, input boxes manually entered value, etc.
- JS code: a JS code that requires the user to enter the pass value
- Rich Text: save the rich text edit box contents itself contains html tags, the user can input XSS script
Potential injection points
Determining whether the input point can be injected successfully into the page content data for the content but does not submit the data output to the input point of the page is not necessary Fuzzing because even submit attack code is not generated XSS;
Fuzzing: Analog XSS attack, blur a means test most commonly used to dig holes, the process of trial and error
Payload: the equivalent of test cases
Tag attributes: As < A the href = "injection position" > Test </ A > , Payload : "> </ A > < Script > Alert ( 0 ) </ Script > < A the href ="
Event tag: < IMG the href = "a.jpg" the onload = "injection position" > , Payload: Alert (0)
Defense XSS attacks
- Browser comes with defense, X-XSS-Protection, major defense reflective XSS attacks, such as the parameters appear in the HTML content and properties
- I.e. escaped escaped when stored in the database, or display; html content to escape, such as the [<>] escaped as & lt; & gt
- Html properties of double and single quotation marks [ '' ''] escaped as & quto; & apos;
- CSP1 (Content SecurityPolicy) content security policy, which is used to specify the executable content
CSRF (Cross Site Request Forgy) cross-site request forgery
User-friendly understanding CSRF
- Web site users visit malicious websites sent a number of requests, and these requests are done without the user's knowledge
- An attacker identity theft by trusted users to send malicious request on his behalf to a third party site for the server, when this request is legitimate
CSRF Attacks
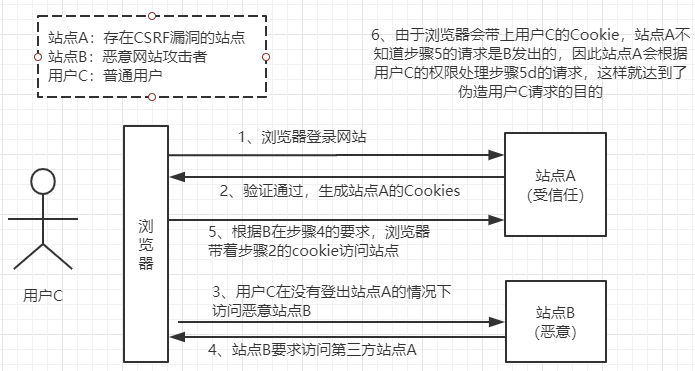
How CSRF is an attack? How defense
- Site A Site B sends a request to
- Request with the site Acookies
- A front-end does not visit the site
- referer to Site B
CSRF attacks harm
- With user login state
- The user's knowledge
- Complete a service request (to steal the user money, posing as a user to post back pot)
- Causing worm attack