1 directory and path
1.1 relative path and absolute path
Absolute path: the path of a certain wording from the root directory / write from.
Relative path: the path was not written from the write /.
1.2 directory related operations
: This layer represents the directory
..: On behalf of parent directory
-: former representative of a working directory
~: Identity on behalf of the current user's home directory located
~ Account: account on behalf of a user's home directory
Note that: are present in all the directory / .., represent this layer and an upper layer directory. .. catalog. Directory under the root directory is the same.
Common treatment directory command:
cd: Change directory
pwd: Displays the current directory
mkdir: create a new directory
Create a directory named dirname mkdir dirname of
mkdir -p dirname1 / dirname2 / dirname3 in order to establish a multi-layer directory (-p parameter must be added)
mkdir -m 711 dirname establish rights for rwx - x - x directory (-m forcibly given directory permissions)
rmdir: delete an empty directory
Variable 1.3 executable file path: $ PATH
echo $ PATH to see the current PATH
PATH = "$ {PATH}: / root" to the / root directory to the PATH variable
2 file and directory management
2.1 view files and directories: ls
ls [-aAdfFhilnrRSt] filename/dirname
ls [--color={never,auo,always}] filename/dirname
ls [--full-time] filename/dirname
Options and parameters:
-a: All files, together with (The file begins with a) together to hide the file list (common)
-A: all the documents, along with hidden files, but does not include .. these two directories.
-d: directory lists only itself, instead of listing the data files in the directory (common)
-f: Direct lists results without sorting (ls will sort the file name)
-F: According to the file, directory information, additional data structures given, for example:
*: On behalf of the executable file /: directory = representatives: representatives socket file I: representatives FIFO file
-h: The file capacity to read human easier way to list
-i: number listed incode
-l: a long serial data comprising attribute data such as file permissions (common)
-n: list the name of the UID and GID instead of the Users and Groups
-r: reverse the sort output results
-R: lists the contents of all files along with subdirectories come together, equal to that of the directory will be displayed
-S: file size to the size of the sort, but not sorted by file name
-t: sorted by time, rather than the file name
--color = never: do not give color display based on document properties
--color = always: Display Color
--color = auto: Let the system based on their own settings to determine whether to give color
--full-time: in full time mode (year, month, day, hour, minute) output
--time = {atime, ctime}: outputting attribute change authority access time or time (ctime), rather than the content change time (modification time)
2.2 copy, delete and move: cp / rm / mv
2.2.1 cp (copy a file or directory)
cp [-adfilprsu] source file (source) target document (destination)
cp [options] source1 source2 source3 ... directory
Options and parameters:
-a: -dr --preserve = all equivalent mean (common)
-d: If the source file for the linked file attributes (link file), link files instead of file attributes are copied itself
-f: to force (force) meaning, if the target file already exists and can not be opened, remove and then try again
-i: If the target file (destination) already exists in the coverage will be asked to operate the (common)
-l: Hard-established link (hard link) the link file, not copy the file itself
-p: Copy the past along with the attributes of the file (permissions, users, time) together, instead of using the default properties (backup commonly used)
-r: recursive continuous replication for copying directories (common)
-s: Copy the file to be a symbolic link (symbolic link), that is different shortcut file
Copy only the case of destination is updated destination older than the source or destination does not exist: -u
--preserve = all: in addition to the rights associated parameter -p, further added SELinux attributes, links, xattr, also copied
2.2.2 rm (remove file or directory)
rm [-fir] filename / dirname remove files or directories
remove empty directories rmdir dirname
Options and parameters:
-f: force is meant to ignore the file does not exist, a warning message will not appear
-i: interactive mode, before deleting the user will be asked whether the action
-r: recursive delete! Delete the most commonly used in the directory
2.2.3 mv (move files and directories, or renamed)
mv [-fiu] source destination
mv [options] source1 source2 source3 ... directory more than one source file or directory, the target file must be a directory
Options and parameters:
-f: force the mandatory sense, if the target file already exists, do not ask directly covered
-i: If the target file (destination) already exists, it will ask whether to overwrite
-u: If the destination file already exists, and the source is relatively new, will be updated
3 File Content Access
cat from the first line displays the file contents
tac beginning to show from the last row, it can be seen tac is cat's write down
When nl is displayed, stopped by the output line number
more display file contents page by page
less and more similar, but better than the more that can flip forward
Look at the first few lines of head
Look at the tail end of lines
od binary way to read the file contents
3.1 direct view file contents
cat [-AbEnTv] concatenate (continuous) shorthand
Options and parameters:
-A: the equivalent of -vET integration options to list some special characters instead of a blank
-b: lists the line number, line number do only for non-blank line display, blank lines are not marked line number
-E: The end of the line break character is displayed $
-n: Print the line number, along with a blank line will have line numbers, with different -b option
-T: The [Tab] ^ I button to be displayed
-v: list some do not see the special characters
tac reverse display
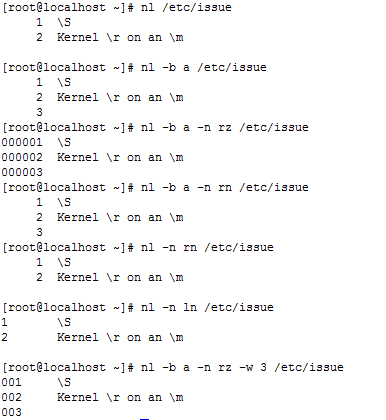
nl [-bnw] filename print line number added
Options and parameters:
-b: Specifies the line number specified by the way, there are two:
-ba: indicate whether he is a blank line, also lists the line number (similar to cat -n)
-bt: If there are empty lines, empty lines that do not list (default value) line number
-n: line numbers, represented list, there are three:
-n ln: Line number is displayed in the far left of the screen
-n rn: line number on the far right in their own field of display and does not add 0
-n rz: line number on the far right in their own field of display and add 0
The number of characters occupied by the line number field: -w
Example:
Turn Pages View 3.2
more flipping page by page
more enterprises during instruction can be used are:
Spacebar: scroll down a
Enter: scroll down one line
/ String: string [] down search function
: F: immediately shows the file name and line number currently displayed
q: immediately leave more, no longer displays the contents of the file
b or [ctrl] -b: back flip, but this action only useful for files, useless for pipeline
less flip from page to page
less operation of the process, the instruction can be used are:
Spacebar: scroll down a
[Page Down]: Scroll down one
[Page Up]: flipping up a
/ String: string [] down search function
? String: string up] [Search function
n: repetition before a search (and / or related?)
N: a reverse search (and / or related?) Before repeating
g: the first line forward this information to go
G: advance to the last line of data to go
q: leave less program
3.3 data acquisition
head [-n number] filename remove the first few lines
Options and parameters:
-n: followed by the number representing the show a few lines of meaning (ten lines before the default display)
Note: -n option if the parameter back then is negative, on behalf of all the number of rows in front, not including the number of rows behind
tail [-n number] filename taken back lines
tail [-f] filename
Options and parameters:
-n: followed by the number representing the show a few lines of meaning (ten lines before the default display)
-f: file name represents the continuous detection of the connected behind, until press [ctrl] -c will end taild detection
Note: -n parameter options back then that if + number, representing all rows back, not including front-line number
Example 1: displaying the first 11-20 rows of /etc/man_db.conf
head -n 20 /etc/man_db.conf | tail -n 10
|: Message in front of the command output, the pipeline will pass through [|] handed over to subsequent instructions continue to use
Example 2: Showing page 11-20 /etc/man_db.conf line, and the print line number
cat -n /etc/man_db.conf | head -n 20 | tail -n 10
od [-t TYPE] filename non-plain text file
Options and parameters:
-t: back can take various types (TYPE) output, for example:
a: to use the default character output
c: use ASCIIz character output
d [size]: using decimal (decimal) to output data size bytes occupied by each integer
f [size]: using a float (Floating) to output data, the number of occupied size bytes each
o [size]: using octal (Octal) to output data size bytes occupied by each integer
x [size]: using a hexadecimal (HEXADECIMAL) to output data size bytes occupied by each integer
Example 1: set / etc / issue in this document are listed in table 8 is stored into the bit value of the ASCII
od -t oCc /etc/issue
Example Two: Find the password string of ASCII control
echo password | od -t oCc
echo can display any information on the screen above, and this information help screen output, but passed od to continue processing
touch [-acdmt] filename file modification time, or build a new file
Options and parameters:
-a: Revision only access time
-c: Modify only time of the file, if the file does not exist the new file is not established
-d: you can take back the date to be amended rather than the current date, you can also use --date = "date or time."
-m: Modify only mtime
-t: the back can take time to be amended without the current time in the format [YYYYMMDDhhmm]
Example 1: The ~ / .bashrc exact copy of / tmp / bashrc, check date
cp -a ~/.bashrc /tmp/bashrc
date;ll /tmp/bashrc;ll --time=atime /tmp/bashrc;ll --time=ctime /tmp/bashrc
Linux file time major changes:
modification time (mtime): When the contents of the file data changes, it will update this time! Content data refers to the contents of the file, rather than attributes or file permissions. By default, ls show is mtime of the file.
status time (ctime): When the state files (status) change, it will update the time, such as: property rights and
access time (atime): When the contents of the file is accessible, it will update the read time (access), such as: use cat to read /etc/man_db.conf, will update the file atime.
4 default permissions and permissions hidden files and directories
4.1 Default file permissions: umask
umask default value is specified the current user permissions when creating a file or directory. There are two ways to look at:
[the root @ localhost ~] # the umask
0022 the umask scores, associated with the general authority is the next three digits, the first set of numbers is used for special permissions
[the root @ localhost ~] # the umask -S
U = rwx, G = RX, o = rx
NOTE: umask score means that the default values need to lose authority!
When creating a file: (- rw-rw-rw-) - (----- w - w-) ==> -rw-r - r-- NOTE: there is no default users to create an executable file (x) permission
When you create a directory: (drwxrwxrwx) - (d ---- w - w-) ==> drwxr-xr-x
umask 002 to modify the default permissions: U = rwx, G = rwx, rx O =
4.2 file hidden attribute
chattr [+ - =] [ASacdisu] filename / dirname hidden attributes to files
Options and parameters:
+: Increase in a certain specific parameter, other parameters is not movable originally present
-: a remove a special parameter, other parameters is not movable originally present
=: Setting specific parameters
A: When this attribute set A, if you have access to this file (or directory), his access time atime will not be modified, to avoid I / O slower machines excessive disk access. (Currently recommend the use of the file system mount options to deal with this item)
S: general asynchronous file is written to disk, plus S if this attribute when you modify any file, which is written to disk synchronization modifiers.
a: When setting a, this will only increase the data file, but can not modify the data can not be deleted, only root can set this property.
c: This attribute set the fire, it will automatically compress the file will be automatically decompressed when read, then when stored, will first be compressed before storage.
d: when the dump program is executed is set to allow the d attribute file (or directory) is not backed up dump.
i: allows a file can not be deleted, renamed, set up the link can not write or add data! For the security of the system has a great help, only root can set this property.
s: When a file set s property, if this file is deleted, he will be completely removed out of this hard disk space, accidentally deleted, completely unable to remedy!
u: s and contrary, when u profile case, if the file is deleted, the data content actually exist on disk, it can be used to rescue the file.
Note: 1, setting common attribute is set to a value of i, a lot of the set value must be set as root can
2, xfs file system only supports AadiS
lsattr [-adR] filename / dirname show hidden file attributes
Options and parameters:
-a: the hidden file attribute is displayed
-d: If you pick a directory, list only the file name in the directory rather than the property itself directory
-R: also together with a parallel data out subdirectory
4.3 Special file permissions
Set UID referred to as SUID
SUID permission only for binaries (binary program) effectively;
Practitioners need to have executable permissions x for the program;
This authority is only valid during the execution of the program (run-time);
The implementation of the program will have the rights owner (owner) of.
Set GID referred SGID
SGID useful for binary program;
Program executive for the program, the need to have x permission;
Executor of the program will receive support group in the process of implementation!
Sticky Bit referred SBIT
SBIT only valid for the directory;
When the user has the w, x permissions for this directory, i.e. having write permission;
When users create a file or directory in the directory, just delete the file and root themselves have the power
SUID / SGID / SBIT permissions:
4 for the SUID
2 for the SGID
1 SBIT
4.4 observe file types
file filename
Instructions and documents Search 4.5
Search 4.5.1 script file name
which [-a] command to find and execute files
Options and parameters:
-a: All instructions can be found by the PATH directory are listed, not just the first to be found in the instruction name
Example 1: searching for the full file name ifconfig command
[root @ localhost /] # Which ifconfig
/ sbin / ifconfig
Search 4.5.2 document file name
whereis [-bmsu] filename / dirname directory to find a certain file name
Options and parameters:
-l: You can list several major catalog whereis will go to query it
-b: only to find binary format files
-m: only to find files in the documentation manual path
-s: source only to find the source file
-u: Search Other special file is not among the above three projects
locate [-ir] keyword
Options and parameters:
-i: ignore case differences
-c: no output file name, only the calculation of the number of files found
-l: means outputs only a few lines, for example, five elements are output -l 5
-S: information output locate database files used by, the database record including a file / directory number, etc.
-r: the display mode can be followed by the regular expression
update: According to /etc/updatedb.conf set to search for the file name in the system hard drive, and update the database file in / var / lib / mlocate;
locate: based on database records in / var / lib / mlocate, find the file name keywords entered by the user.
find [PATH] [option] [action]
Options and parameters:
1, time-related options: a total of -atime, -ctime and -mtime, to -mtime Description:
-mtime n: n is a number, meaning the modifier content in a single day over the previous n days of the file;
-mtime + n: n listed days before (n days excluding itself) had been modifier content file filename;
-mtime -n: n listed in days (itself containing n days) had been modifier content file filename.
-newer file: file to an existing file that lists the file is newer than the file filename
Example 1: find / etc under the file, if the file date than the / etc / passwd on the new list
find /etc newer /etc/passwd
2, the user name or group of related parameters:
-uid n: n is a number, this number is the user's account ID, i.e. UID, the UID is recorded in a digital / etc / passwd and account name corresponding to the inside.
-gid n: n is a number, this number is the ID name of the group, i.e. GID, the GID recorded in / etc / group.
-user name: name for the user account name, for example: root.
-group name: name for the group name, for example: users.
-nouser: looking for the owner of the file / etc / passwd people do not exist
-nogroup: find files owned group does not exist in / etc / group file
Example 2: Find / home belonging to zhouweijie file under
find / home -user zhouweijie
Examples of three: Search system does not belong to anyone's file
find / -nouser
3, relating to the name of the file permissions and parameters:
-name filename: Find the file named filename
-size [+ -] SIZE: Search bigger than SIZE (+) or less (-) files. The SIZE specifications are:
c: represents the byte, k: representatives 1024bytes.
-type TYPE: TYPE type as search documents, the main types: general regular file (F), the file means (b, c), the directory (D), link file (l), socket (s), and FIFO ( p) attributes.
-perm mode: just search for [equal to] file permissions file mode, this mode is similar to chmod the property value, for example, property -rwsr-xr-x is 4755!
-perm -mode: search all file permissions [must] include permission mode of the file, for example, we want to find -rwxr - r--, ie 0744 files, use -perm -0744, when a file permissions for -rwsr-xr-x, that is 4755, it will also be listed, because the property -rwsr-xr-x's have included -rwxr - r-- properties.
-perm / mode: search for file permissions include permission [of] any one mode of the file, for example, we find -rwxr-xr-x, namely -perm, 755 time, but a file attribute -rw --- ---- it will be listed, because he has -rw .... attributes exist!
Examples of four: find the file name contains the keyword passwd file
find / -name "*passwd*"
Examples of five: find / under run directory, file type, file name is Socket
find /run -type s
Examples Six: Find files which contain attributes or SUID or SGID of SBIT
find / -perm /7000
4, additional action that can be performed
-exec command: command of other instructions, may be followed by additional -exec back instruction results to the search process.
-print: print the results to the screen, this action is the default action!
Examples VII: find / usr / bin, under / usr / sbin these two directories with SUID or SGID files, and use ls -l to list files found
find /usr/bin /usr/sbin -perm /6000 -exec ls -l {} \;
Note: [{} represents the content found by the find], find the result is placed in position {};
-exec until \; it is the key word, start (-exec) behalf find additional action to end (\;), additional action in the middle is the find command.
Because the [;] at the bash environment is of special significance, so use a backslash to escape.