Access Control List Description
ACL (Access Control Lists, referred to as ACL) is applied to the router interface commands list. These instructions are used to tell the router list which can receive data packets, which packets are rejected. As the data packet is accepted or rejected, may be determined by the specific conditions indicated similar to the source address, destination address, port number and the like. ACL read the third layer, the fourth layer header information, and to filter packets based on pre-defined rules.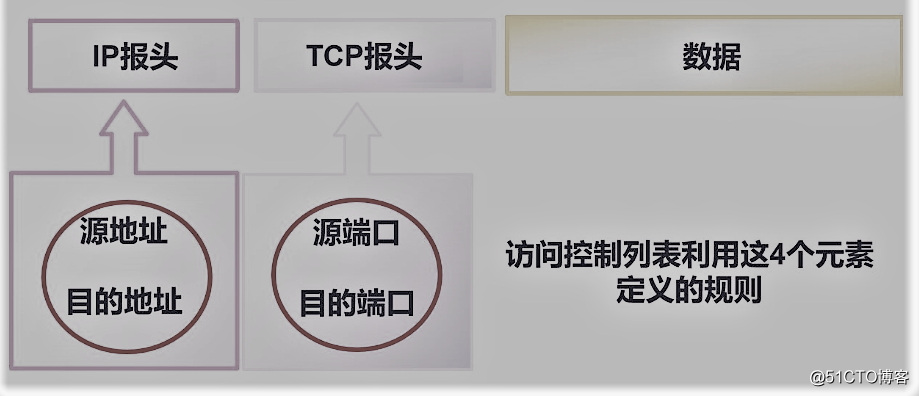
ACL functions
1. limit network traffic and improve network performance
2 provides communication traffic controls
basic security measures provide network access to 3.
4. at the network interface device, decide which type of traffic to be forwarded, which type of communication traffic is blocked
ACL works
1. Access Control Lists direction in interface applications:
Outbound: router has been processed, is leaving the router interface packets
inbound: the packet has reached the interface of the router, the router will be processed
the application list to the interface with the orientation direction related data
2. Access control list processing:
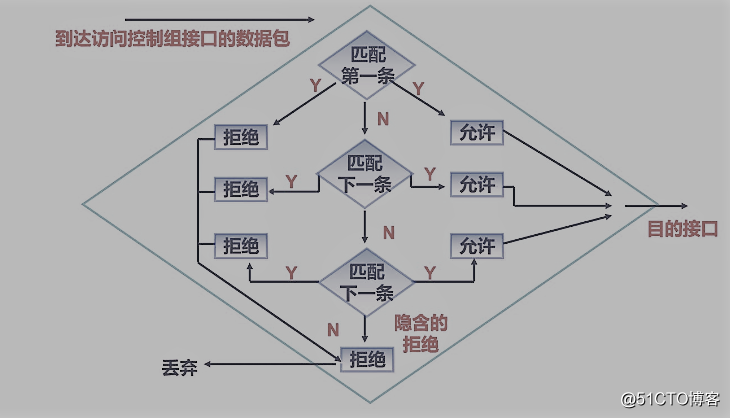
ACL规则:匹配为自上而下逐条匹配,默认隐含的拒绝是拒绝所有(any)
白名单
允许 1.2
允许 1.3
拒绝所有(可不写,隐含的拒绝会拒绝所有)
**黑名单**
拒绝 1.2
拒绝 1.3
允许所有(必须写,否则隐含的拒绝会拒绝所有)ACL type
Standard Access Control Lists
Filtering packets based on the IP address of the
control list ACL standard access number from 1 to 99
Extended Access Control Lists
Based on the source IP, destination IP address, specify the protocol, and port flags to filter packets
extended access control list ACL number from 100 to 199
Named Access Control Lists
Named access control lists allow the use of names in the standard and extended access control list to be enemy No.
adjusted relatively flexible security policy
ACL-related commands
1. Create ACL
access-list access-list-number { permit | deny} source [source-wildcard ]
//permit表示允许数据包通过 ,deny表示拒绝数据包通过 ,source [ source-wildcard ]只对源IP进行控制+(反子网掩码)Example demonstrates
Router(config)# access-list 1 permit 192.168.1.0 0.0.0.255
Router(config)# access-list 1 permit 192.168.2.2 0.0.0.0
//允许192.168.1.0/24和主机192.168.2.2的流量通过2. Delete ACL
no access-list access-list-number //直接删除ACL列表号3. implicit denial statement
access-list 1 deny 0.0.0.0 255.255.255.255 //拒绝所有ip 4. Keyword
host //host后面可跟ip地址,免去子网掩码的输入
any //等同于拒绝所有ip5.ACL applied to an interface
ip access-group access-list-number {in | out} //in定义于离控制方最近的端口6. apply an ACL on the interface
no ip access-group access-list-number {in | out}Standard ACL configuration demo
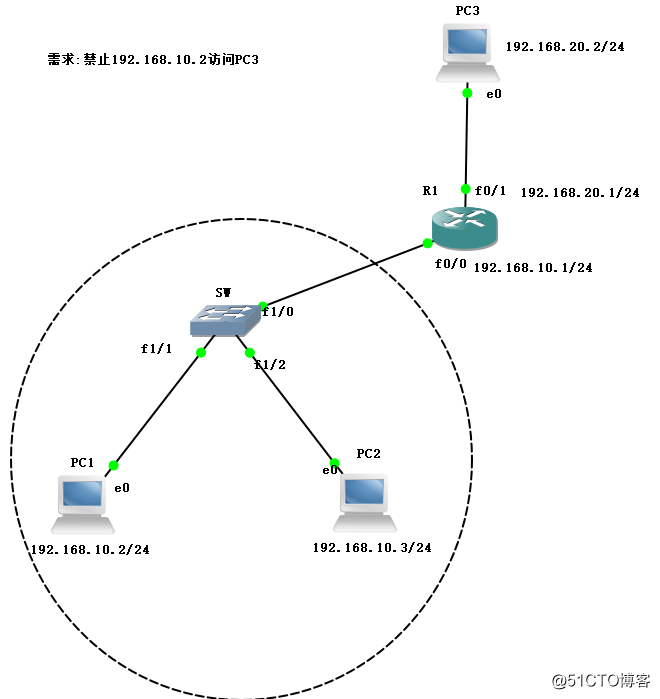
1. Assign switch
conf t //进入全局模式
no ip routing //关闭路由功能
int f1/0 //进入端口f1/0
speed 100 //配置速率
dup full //配置全双工模式2. configure the router R2
conf t
int f0/0
ip add 192.168.10.1 255.255.255.0 //配置端口f0/0的IP地址
no shut
nt f0/1
p add 192.168.20.1 255.255.255.0 //配置端口f0/1的IP地址
no shut
do show ip route //查看路由表Configuration 3.PC IP address
(1) the IP address of PC1 and gateway
ip 192.168.10.2 192.168.10.1And gateway IP address (2) arranged in PC2
ip 192.168.10.3 192.168.10.1 IP address and gateway (3) Configuration of PC3
ip 192.168.20.2 192.168.20.14. Test between the PC communication
PC1> ping 192.168.20.2
192.168.20.2 icmp_seq=1 timeout
84 bytes from 192.168.20.2 icmp_seq=2 ttl=63 time=31.242 ms
84 bytes from 192.168.20.2 icmp_seq=3 ttl=63 time=31.241 ms
84 bytes from 192.168.20.2 icmp_seq=4 ttl=63 time=31.243 ms
84 bytes from 192.168.20.2 icmp_seq=5 ttl=63 time=31.222 ms
PC3> ping 192.168.10.3
192.168.10.3 icmp_seq=1 timeout
84 bytes from 192.168.10.3 icmp_seq=2 ttl=63 time=31.518 ms
84 bytes from 192.168.10.3 icmp_seq=3 ttl=63 time=31.266 ms
84 bytes from 192.168.10.3 icmp_seq=4 ttl=63 time=31.263 ms
84 bytes from 192.168.10.3 icmp_seq=5 ttl=63 time=31.244 ms5. Create ACL on router R1 and used in f0 / 0 port
access-list 1 deny host 192.168.10.2 //拒绝ip为192.168.10.2 的主机访问
access-list 1 permit any //允许其他所有ip访问
int f0/0
ip access-group 1 in //将ACL应用与f0/0端口的入方向
do show access-list //查看ACL列表6. Verify ACL configuration
(1) Test PC1 and PC3 communication
PC1> ping 192.168.20.2
*192.168.10.1 icmp_seq=1 ttl=255 time=31.223 ms (ICMP type:3, code:13, Communication administratively prohibited)
*192.168.10.1 icmp_seq=2 ttl=255 time=15.618 ms (ICMP type:3, code:13, Communication administratively prohibited)
*192.168.10.1 icmp_seq=3 ttl=255 time=15.621 ms (ICMP type:3, code:13, Communication administratively prohibited)
*192.168.10.1 icmp_seq=4 ttl=255 time=15.622 ms (ICMP type:3, code:13, Communication administratively prohibited)
*192.168.10.1 icmp_seq=5 ttl=255 time=15.620 ms (ICMP type:3, code:13, Communication administratively prohibited)Conclusion: Discovery Communications and prompt communication can not be banned management side, ACL take effect
(2) Test PC1 and PC2 communication
PC1> ping 192.168.10.3
84 bytes from 192.168.10.3 icmp_seq=1 ttl=64 time=0.000 ms
84 bytes from 192.168.10.3 icmp_seq=2 ttl=64 time=0.000 ms
84 bytes from 192.168.10.3 icmp_seq=3 ttl=64 time=0.000 ms
84 bytes from 192.168.10.3 icmp_seq=4 ttl=64 time=0.000 ms
84 bytes from 192.168.10.3 icmp_seq=5 ttl=64 time=0.000 msConclusion: The internal LAN without an ACL, can communicate normally