1. Foreword
ACL is also known as access control list. In fact, this thing is useful in many places. The name may be different, but the principle and function are not too different. For example, servers and firewalls have similar things. The function is actually "filtering" out Unwanted packets. Why don't you want to receive some packets? For safety.
For example, you have a server that provides web services to the outside world, so you need to open port 80, but there may be some other businesses running inside the server, using port 6666. If there are no restrictions, bad guys outside will try to connect to port 6666 and try to obtain additional information through this port that you don't want to provide to the outside world. This is what ACL does. The basic operation is to close all external ports, and then only open port 80 to the outside world.
2. ACL overview
From the name, the ACL access control list is a table, which lists the control conditions row by row. Its characteristic is to check this table when a certain access is performed. First, look at the first item. If the conditions are met Just execute this control condition and end. If this condition is not met, continue to read the next item until you have read all the control conditions in the table.
Based on this feature, there are two ways to use ACL. One is to enable all access permissions by default, and then deny unwanted access. The second is to deny all access permissions by default, and then open the access that needs to be opened. Generally speaking, the second way of thinking is adopted. In the first way, you may write tens of thousands of rules and may not be able to finish writing, but the services provided to the outside world are always limited.
The next thing to say is that due to the characteristics of ACL, you need to look at the ACL control table every time you have access, then the problem comes. If you write a lot of rules, it may directly affect the efficiency of the router, which is why The router has the function of ACL and we still need a firewall.
3. ACL rules
A simple ACL control condition is as follows:
system-view
acl 3500 #Create a rule numbered 3500
rule deny icmp source 3.3.3.2 0 destination 2.2.2.2 0 icmp-type echo #write a control command
quit
interface GigabitEthernet 0/0/0 #Enter port
traffic-filter inbound acl 3500 #binding rules
The effect is that the G0/0/0 port of the router will filter according to the acl rules, and when it finds a packet with the source address of 2.2.2.2 and the destination address of 3.3.3.2, its icmp message will be rejected.
So the specific process is:
(1) Create a rule for a certain number
(2) Write control instructions in the rules
(3) Bind the rule to the router port
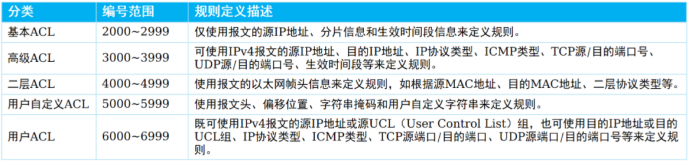
Some conventions about numbers are as follows. Numbers of different sizes will affect your writing control commands. For example, rules such as acl 2001 cannot filter destination IPs, and numbers greater than 3000 must be used.
4. ACL instance
Consider the network structure below.
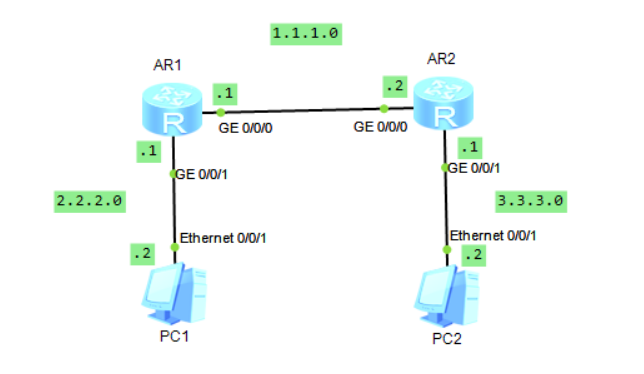
Ping-free example
In fact, it is the previous example, because we need to use the source IP and destination IP, so the acl number must be greater than 3000. At the same time, here we want to prohibit the ping of all IPs, so there is still a small modification.
system-view
acl 3500 #Create a rule numbered 3500
rule deny icmp source any destination 2.2.2.2 0 icmp-type echo #write a control command
quit
interface GigabitEthernet 0/0/0 #Enter port
traffic-filter inbound acl 3500 #binding rules
The effect is that the ping packet of any device cannot pass through the G0/0/0 port of AR1. In other words, if the packet does not pass through this specific port, it is not restricted.
5. Review
As its name suggests, the ACL access control list is a table that controls external access through the control instructions in the table. It should be noted that multiple lists can be customized in the router, and different table numbers also determine its functional characteristics. Finally, bind the table number to the port and the control policy will take effect.