As we all know, iOS system relative to the Andrew system, with fewer pirated software and security vulnerabilities. Why, because iOS system uses a mechanism for signature.
First, Apple's signature mechanism system
1, Apple needs:
- Does not require the installation package uploaded to the App Store, can be installed directly to the phone
- Apple ensure the security of the system, we must have absolute control over the installation of the APP
- After Apple can allow installation
- Can not be abused led to the development of non-APP can also be installed
To achieve these requirements, iOS signature complexity greatly increased, given Apple's solution is a double signature:
Double signature principle:
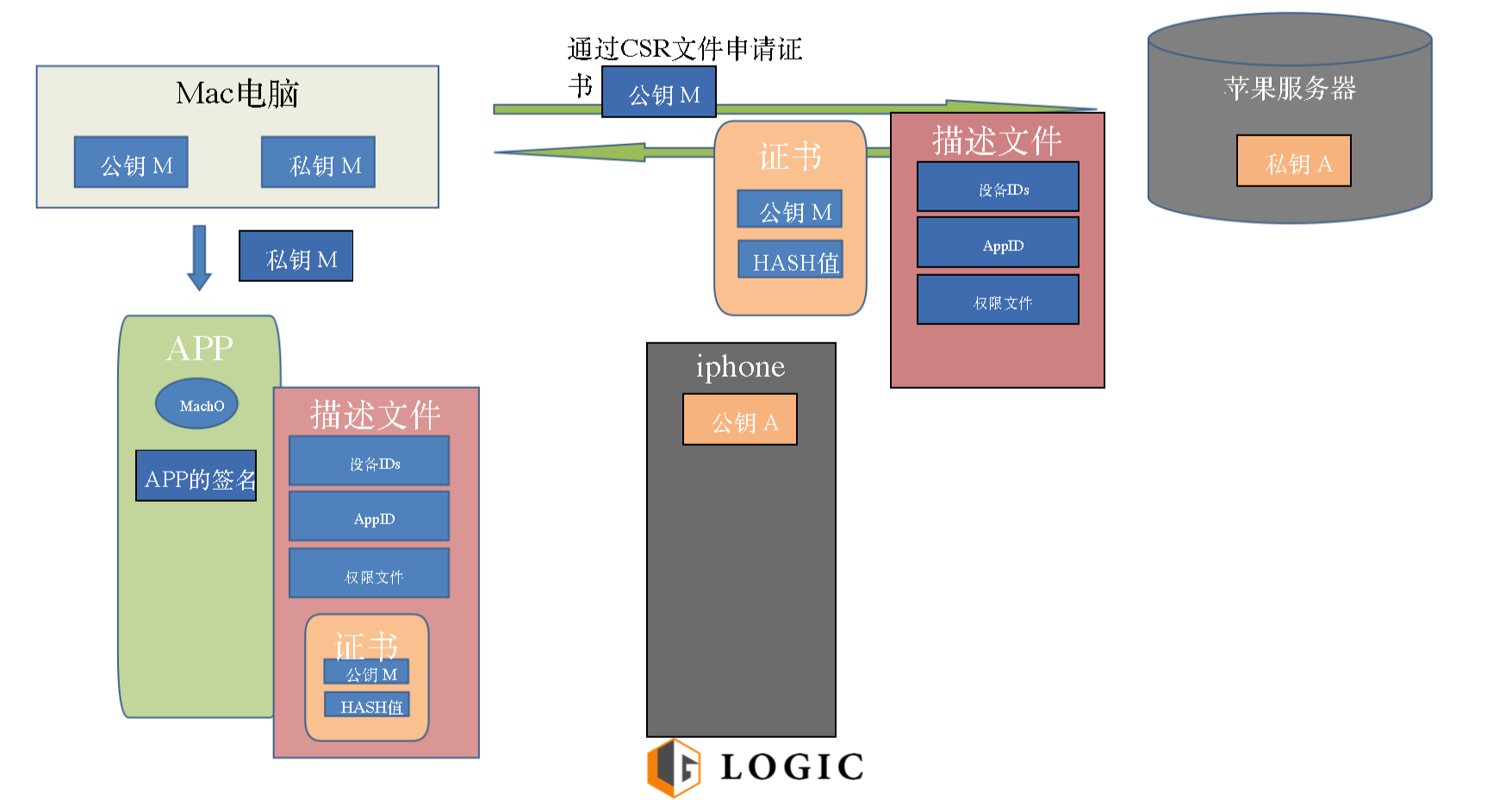
(1) Mac computers in the existing public and private M M, Apple's application for a certificate to the server through the CSR file, Apple will be encrypted for the public key M, M and return a public key certificate HASH carrying value;
(2) how the APP installed computer to the phone, to be signed with the private key M application on your computer, and will put together a certificate within APP packaged ipa (xcode in these steps are completed);
(3) Packaged IPA package to try to install on the phone, Apple will use the public key to decrypt A validation obtain the public key M, to see if the public key M package this APP is a certificate issued by Apple, if all verified, it can be installed.
2, description file is generated
Signing this can lead to the occurrence of a problem, that is, all the phones can be installed, in order to solve the problem of abuse of the application, Apple added two restrictions:
- The first restriction is registered in the background Apple devices can be installed.
- The second limitation is only for one specific signature of APP.
And also to control the Apple APP inside iCloud / push / background / debugger to attach these rights, so Apple to switch these rights collectively called Entitlements (authority), and the file in a place called Provisioning Profile (profile ) file.
View profile location: ~ / Library / MobileDevice / Provisioning Profiles
Second, the application re-signing
Download IPA-signature application package, and then decompressed.
View signature information ipa package:
$ codesign -vv -d WeChat.app
Check whether the package is downloaded IPA jailbreak package:
$ otool -l WeChat > ~/Desktop/123.txt
Search criptid, if the value is 0, for the package to escape, if 1, for the genuine package
Keychains listed in the certificate can be signed:
$ security find -identity -v -p codesigning
Forced to replace signature:
$ Codesign -fs "certificate name" File Name
Add permissions to the file:
$ Chmod + x the executable file
Re-signed the steps of:
1, enter the application .app file, delete Plugins, Watch plugin
2、重签Frameworks
$ Codesign -fs "certificate name" File Name
3, create a new project, application profiles, build applications
4, to copy the profile package APP
5, info.plist change in the bundle ID (must match the bundle ID description file)
6, the entire signature APP package
Signature method: $ security cms -DI profile
拷贝<key>Entitlements</key>
<Dict> </ dict> the contents

In the new project in a plist file, copy the code above into it, and then copy the new plist file out, and app files and description files placed in the same directory within
7. Signature
$ Codesign -fs "certificate name" --no-strict --entitlements = plist file name APP name
Finally, re-signed package installed on your phone!