1.HTTP agreement
1.1 concept
HTTP protocol is the Hyper Text Transfer abbreviation Protocol (Hypertext Transfer Protocol) is used from the World Wide Web (WWW: World Wide Web) server to transfer hypertext transfer protocol local browser.
HTTP is used to transfer a data (HTML files, image files, query results, etc.) based on TCP / IP communication protocol.
1.2 Work
HTTP protocol works on the client - server architecture on. HTTP browser as a client through the URL that is all WEB server sends a request to the HTTP server.
HTTP Three things to note:
- HTTP is a connectionless: Meaning No connection is restricted only one request per connection . After the server processes client requests and receives the customer's response, i.e., disconnected . In this way it can save transmission time.
- HTTP is an independent media: This means that, as long as the client and the server knows how to handle the data content, any type of data can be sent via HTTP . The client and server specify the appropriate MIME-type content type.
- HTTP is a stateless: HTTP protocol is stateless protocol. Stateless means the agreement for the transaction has no memory capability . If the lack of state means that the subsequent processing required in front of the information, it must be retransmitted, which may result in the amount of data transmitted for each connection is increased. On the other hand, when it does not require previous information in response to a faster server.
1.3 URL
HTTP uses uniform resource identifier (Uniform Resource Identifiers, URI) to transmit data and establish a connection. URL is a special type of URI, contains enough information for finding a resource.
URL, stands for UniformResourceLocator, Chinese called a Uniform Resource Locator, is the address used to identify a resource on the Internet at. At the following URL as an example, each part of the composition of the next ordinary URL:
http://www.aspxfans.com:8080/news/index.asp?boardID=5&ID=24618&page=1#name
As it can be seen from the above URL, a full URL, including the following sections:
1, part of the agreement: the protocol part of the URL is "http:", which represents the web page using the HTTP protocol. More may be used in the Internet protocols, such as HTTP, FTP and the like used in this example is the HTTP protocol. In the "HTTP" behind "//" is a delimiter2, domain name parts: the part of the URL domain name is "www.aspxfans.com". A URL, or you can use the IP address as the domain name
3, port sections: following the domain name is to use between the ports, the domain name and port ":" as the delimiter. Port is not a necessary part of the URL, if the port portion is omitted, the default port 80
4, the virtual directory section: from the first domain name after "/" beginning to the last "/" so far, is the virtual directory section. Virtual directory is not a necessary part of the URL. In this example the virtual directory is "/ news /"
5, the file name part: from the last after the domain name "/" beginning to date, is the filename part, if not, it is from the last after the domain name "/" beginning to "#" so far "?" "?" , is part of the file, if there is no "?" and "#", then the domain name from the last "/" start to finish, it is part of the file name. In this case the file name is "index.asp". Part of the file name is not a necessary part of the URL, if you omit this part, the default file name
6, anchor parts: from the "#" beginning to end, are part of the anchor. Anchor of this embodiment is "name". Anchor part of the URL is not a necessary part
7, part parameters: From the beginning to the "#" part of the argument between the far part, also known as part of the search query part "?." Parameters of this embodiment is "boardID = 5 & ID = 24618 & page = 1". Parameter to allow a plurality of parameters, with the parameters between the parameter and the "&" as the delimiter.
(Original link: https://blog.csdn.net/ergouge/article/details/8185219 )
1.4 Message Structure
1.4.1 Request Request
The client sends a request to the HTTP server request message comprises the following format: The general format of the request line (request line), the request header (header), a blank line, and a data portion composed of four requests, the figure shows the request packet .

Header: often called the request headers, request header is stored in some of the major explanation for the request (self-introduction). Accordingly server to obtain client information.
Common request headers:
accept: browser tells the server through the head, it supports data types
Accept-Charset: browser tells the server through the head, what kind of character set that supports
Accept-Encoding: browser tells the server through this, support the compression format
Accept-Language: browser tells the server through the head, it's locale
host: browser tells the server through the head, wanted to visit which host
If-Modified-Since: browser tells the server through the head, time cached data
Referer: browser tells the server through the head, the client which page to the anti-hotlinking
Connection: browser tells the server through the head, after the request is broken links or how to maintain links
X-requested-With: XMLHttpRequest behalf accessed by way of ajaxUser-Agent: the identity of the requesting vehicle identification
Message body: request body is often called, is stored in the request body to be transmitted / data transmitted to the information server.
1.4.2 Response response
HTTP response also consists of four parts:
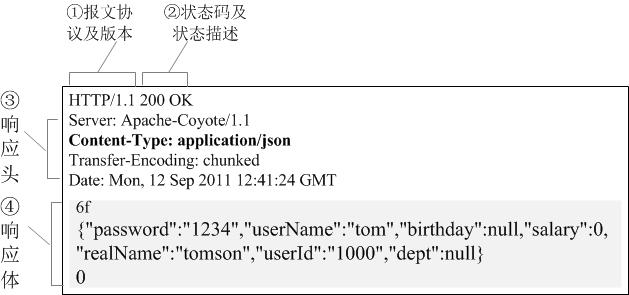
Status Code: to "clear" language tells the client processing the results of this request.
HTTP response status code is composed of five segments:
- 1xx message, usually tell the client request has been received and is being processed, do not worry ...
- 2xx successful treatment, the general said: receipt of the request, I understand what you want, the request has been accepted, and other information has been processed.
- 3xx redirect to other places. It then allows the client to initiate a request to complete the entire process.
- 4xx error handling, responsibility on the client, such as client requests a resource that does not exist, the client is not authorized to prohibit access.
- 5xx processing error occurs, the responsibility on the server, such as server throws an exception, routing error, HTTP version does not support.
Response Headers: Details Responses show
Common respective headers:
Location: server through this head, to tell the browser where to jump
Server: server through the head, telling the browser model server
Content-Encoding: server through the head, telling the browser, the compression format data
Content-Length: server through this header tells the browser loopback length data
Content-language: server through the head, telling the browser locale
Content-type: server through the head, tells the browser back to the type of transmission data
Refresh: server through the head, telling the browser regularly updated
Content-Disposition: server through the head, telling the browser to download a way to play data
Transfer-Encoding: server through the head, tells the browser to block the way data is sent back to
Expires: -1 do not control the browser cache
Cache- Control: NO-Cache
Pragma: NO-CacheIn response to the body: the information specified by the client according to the request, and transmits the specified data to the client
Common status codes 200 the OK # client request was successful 400 Bad Request # client requests a syntax error, can not be understood by the server 401 Unauthorized # request is not authorized, the status code must be used with the WWW-Authenticate header field 403 Forbidden # server receipt of the request, but refused to provide service 404 not Found # requested resource does not exist, eg: enter the wrong the URL of 500 Internal server error # server goes unexpected errors 503 server unavailable Papers with # requests that the server can not currently handle client, after a period of time may return to normal more status codes: HTTPS: //www.runoob.com/http/http-status-codes.html
1.5 Method Request
The standard HTTP, HTTP request can use several request methods.
HTTP1.0 request defines three methods: GET, POST, and HEAD method.
HTTP1.1 six new request methods: OPTIONS, PUT, PATCH, DELETE, TRACE, and CONNECT method.
The method described GET # page information specified by the request and returns the entity body. The POST # submit data processing request to the specified resource (e.g., file submission form or upload). Data contained in the request body. POST request may result in a revision to establish and / or existing resources to new resources. The HEAD # similar to the GET request, returns a response but not the specific content, the header for acquiring the PUT # substituent designated document data from the client to the server transmits the content. DELETE # requests the server to delete the specified page. The CONNECT # the HTTP / 1.1 protocol can be reserved for connection to the proxy server pipeline mode. The OPTIONS # allows the client to view server performance. The TRACE # Echo Request received from the server, mainly for testing or diagnostic PATCH # complements the PUT method, used locally known resource update.
2.HTTPS agreement
2.1 Concepts
Https (English: Hypertext Transfer Protocol Secure, abbreviation: HTTPS, often referred to as HTTP over TLS, HTTP over SSL or HTTP Secure) is a secure network transport protocol.
HTTPS for communication via the Hypertext Transfer Protocol (HTTP), but using SSL / TLS to encrypt data packets.

2.2 SSL encryption
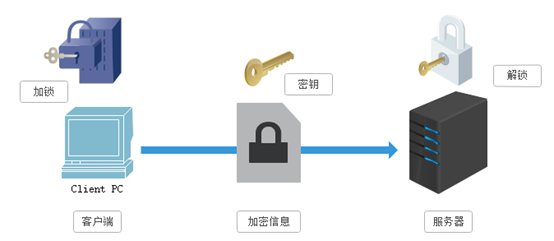
SSL encryption technology employed is called "Shared Key", also called "symmetric key encryption", this encryption method is such that, for example client sends a message to the server, the first client using known algorithms when information is encrypted, such as MD5 or Base64 encryption, the receiving end decrypts the encrypted information need to use a key, the intermediate key is passed, (encryption and decryption are the same), the transmission is a key intermediate encrypted. This approach seems safe, but there are still potentially dangerous, once tapped, or information being held hostage, it is possible to crack the key, and break the information. Therefore, "shared key encryption" security risk this way.
2.3 Asymmetric encryption secret key
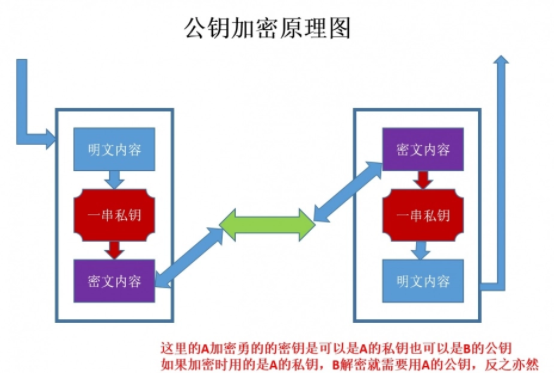
When using the "asymmetric encryption" There are two locks, one called the "private key", a "public key" encryption when using non-object of encryption, the server tells the client according to their own first given the public key encryption, in accordance with the client after the public key encryption, the server receives information and then decrypt it, using their own private key to decrypt the benefits of doing so is the key would not carry out transmission and, therefore, avoid the risk of being kidnapped. Even if the public key is to get the eavesdropper, it is difficult to decrypt, decryption process because of the discrete logarithm evaluated, this is not easily able to do. The following asymmetric encryption schematics:
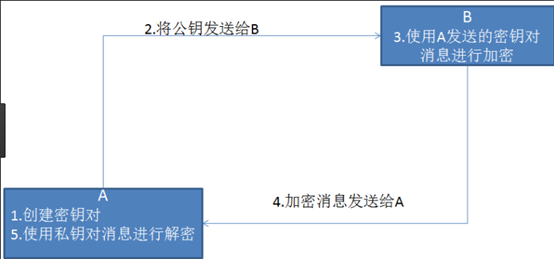
But the asymmetric secret key encryption technology has the following disadvantages:
- How to ensure that the receiving end sends the time disclosed the secret key to the transmission side, the transmission side in advance to ensure that the received transmission, without being sandwiched. As long as the key is sent, there may be at risk of being held hostage.
- Asymmetric encryption is relatively inefficient manner, it is more complicated to handle, during communication have a certain influence on the communication speed and efficiency
2.4https certificate mechanism
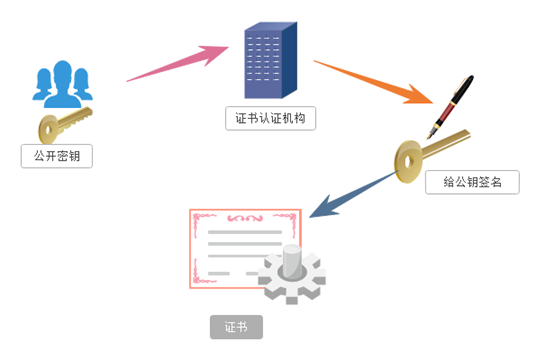
In the above, we talk about the shortcomings of asymmetric encryption, the first of which is the presence of the public key is likely to be kidnapped, the public key can not guarantee that the client receives the server's public key is released. At this time, there is caused a public key certificate mechanism. Certificate authority is a third party client and server are trusted. DETAILED communication process certificate as follows:
- Server developers to carry public key, the public key to apply to the certificate authority, certificate authority in a clear understanding of the identity of the applicant, after approval, the public key of the application developer will do a digital signature, then assign the public key has been signed certificate and key on the inside, bound together
- The server sends this digital certificate to the client, because the client also recognized certificate authority, a client can verify the authenticity of the public key digital signature by certificate number to ensure that the server pass over the public key is true. Under normal circumstances, the certificate of digital signature is difficult to forge, depending on the credibility of the certification body. Once confirmation is correct, the client will be encrypted by the public key to send the message, the server receives later with his private key to decrypt it.
Original link: https://www.cnblogs.com/sunxiuwen/p/10110762.html#_label8