Today, the mobile Internet has been fully integrated into our lives, all kinds of APP is endless, therefore, is particularly important for the study of Andrews APP security. Through a crack examples of the Android APP, APP to elicit explore for safety. (I pure white, initial contact Andrews reverse week a little experience here to share)
The crack Andrews APP is a section shooter, we find in the game to buy recharge function, then we crack for this function, aimed at achieving free purchase.
First, restore the game, that decompilation. Decompile can view the configuration file, the APP algorithm logic, etc., to help us analyze it. Here, we use the tool AndroidKiller to decompile.
By the figure, you can see part of APP. We just need to focus smali file because Smali Andrews system of the Java virtual machine (Dalvik) assembler dex one kind of file format used. We can see through the pseudo-code APP smali file to understand the algorithm logic.
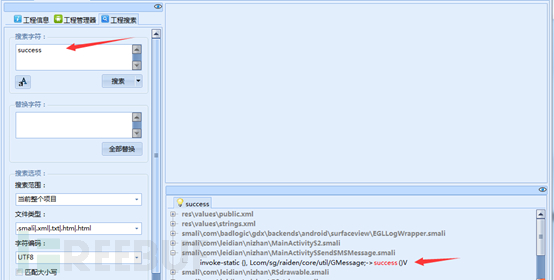
The next step is to find the entrance APP payment, you can find relevant documents by searching for success, pay, paid and other key string.
Click through to view this file, we can see some string related pay, may guess here is the entrance to the payment function, as in the end is not, then we see below.
These smali looking statements may obscure, it does not matter, we can AndroidKiller be converted to the familiar java code.
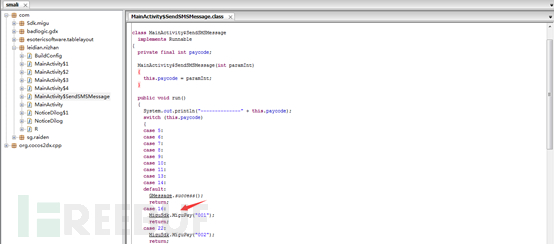
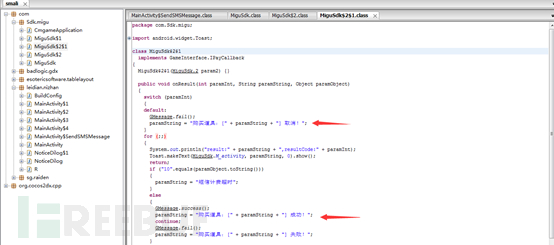
Here is a switch statement, payment functions may be right to do some judgment. We can see here there is a MiguPay function, which in the end is doing it? Click MiguSdk class, you can jump to MiguSdk class.
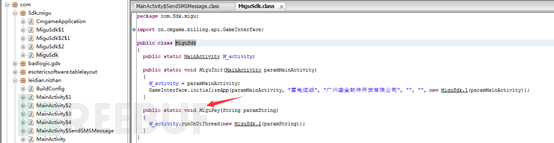
We can see that the method was called runOnUiThread method parameters involving another class MiguSdk.2, follow this method continues to jump down.
Amazing scene appeared, we can see the "buy props", "success" and other strings, here almost on here is related to the method of payment to be sure! Well, before we jump to the function switch judgment.
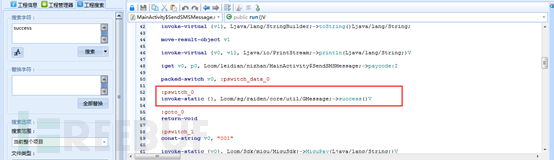
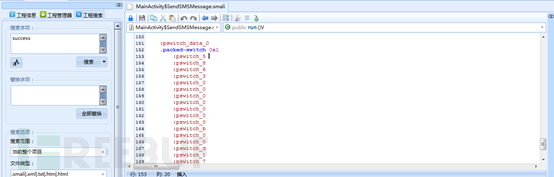
Until we see, when you call GMessage.success (), it is to explain to buy success. And here: GMessage.success pswitch_0 statement is sent (). This means that if all the statements and judgments in execution pswitch_0 like, it is not all conditions can buy success? We try all: pswitch_x all changed pswitch_0.
Packaged with the signing of the APP AndroidKiller, installation and testing!
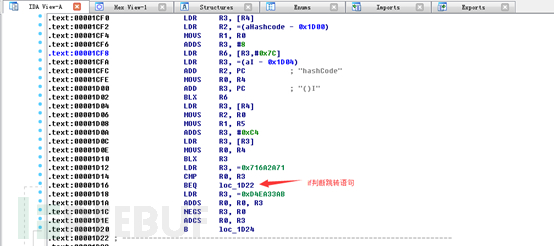
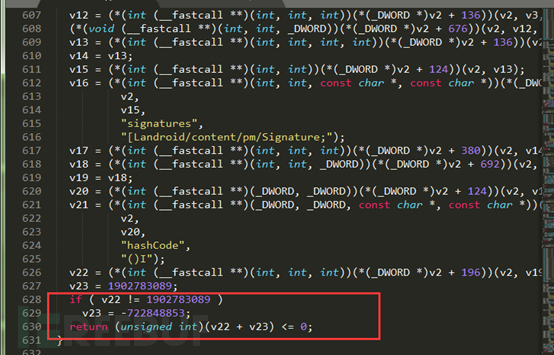
installation failed! Tip signature verification does not pass! It appears that the APP was the signature verification, the so-called signature verification is to prevent repackaging their application after being decompiled. Is there a method to bypass it? Of course there is! In fact, the signature verification layer so generally written in the native file or java layer. By searching SignKey, Signature and other key string, you can generally find the entrance signature verification. The following document is to determine the signature of documents in the so-correlation function, use IDA tools convert C language pseudo-code.
As can be seen from the figure, finally we made a statement if the judge, then we directly use a hex editor will return statement directly instead return true. Finally compiler package the APP again, ok! Successful break!
Thinking: Developing a commercial value of APP, is undoubtedly requires a lot of effort, if APP can be easily cracked, and that the loss caused is certainly unacceptable. So it is essential for the security of APP. About security APP reverse, generally have the following:
1, code obfuscation: the program advertised the re-organization and processes, making the code with the code before treatment after treatment is completed the same function, and the code is obfuscated difficult to decompile, decompile success even if it is difficult to draw program the real semantics.
2, signature verification: Compares the hash of the signing certificate app and whether we write them died in the same hash.
3, shelling: implanted in the binary program a piece of code at run time priority access control program, do some extra work.