With OSSIM easily analyze network device logs
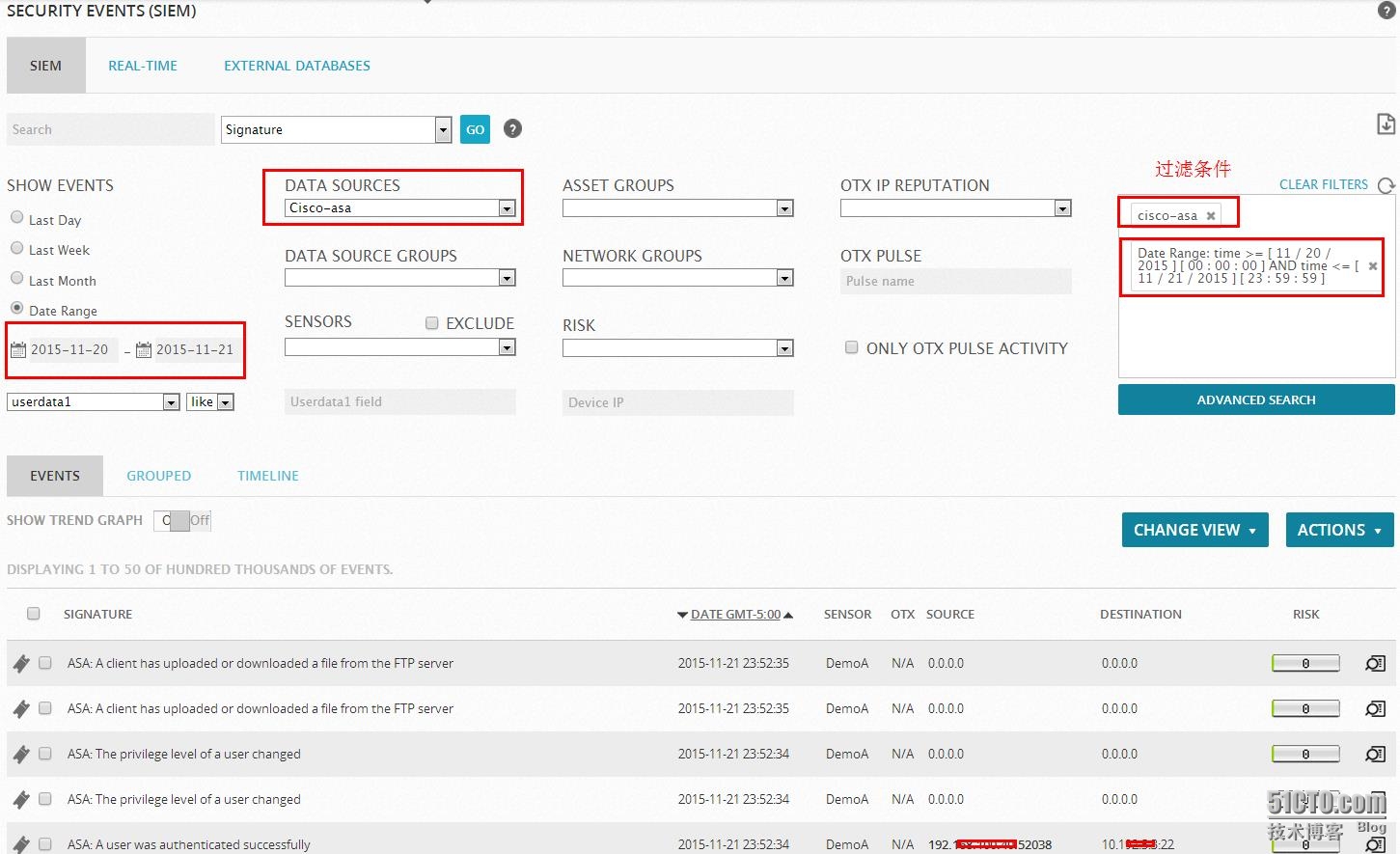
Based on the log collection and processing mode plug-in, so users can easily take advantage of OSSIM to analyze a variety of network device logs in heterogeneous network environments, the following examples show some of the hardware device logs, we RAW LOG interface, the search field, enter Cisco Key words, and instantly call up the data source have Cisco routers, firewalls, switches, and other criteria, as long as you know the basic hardware models can be found in the corresponding data source. Firstly Cisco ASA firewall, for example to illustrate for everyone.
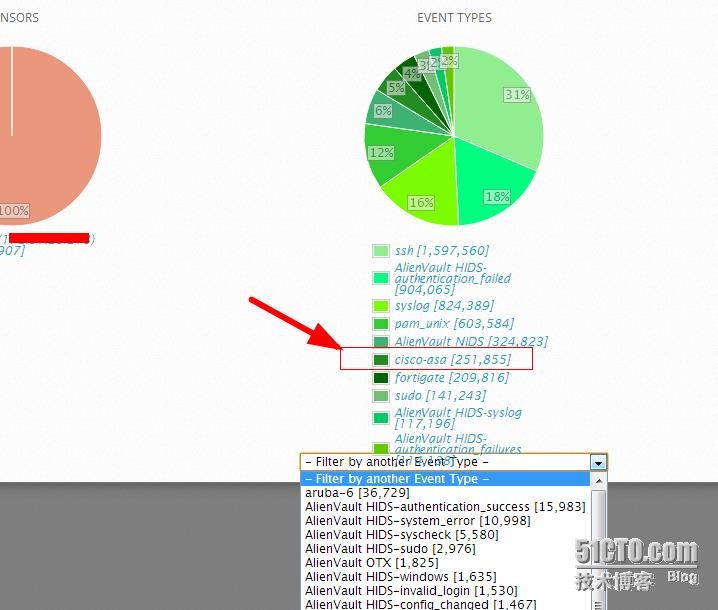
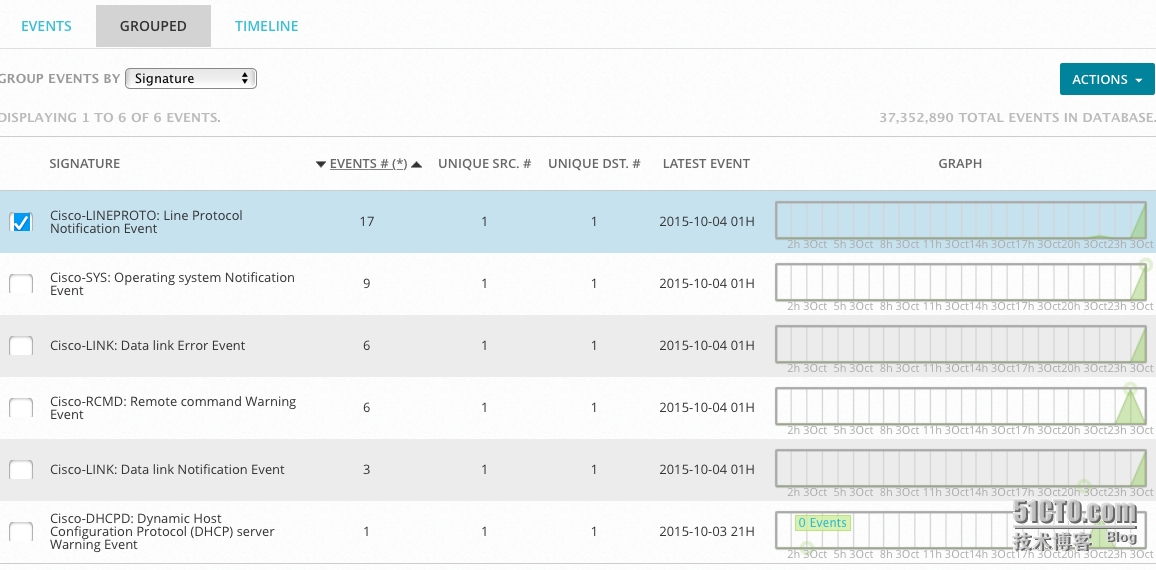
Pie in the system by the various types of logs presented to the user intuitive, easy to access.
From the network device logs collected logs, after the plug-normalized, converted into a standardized event,
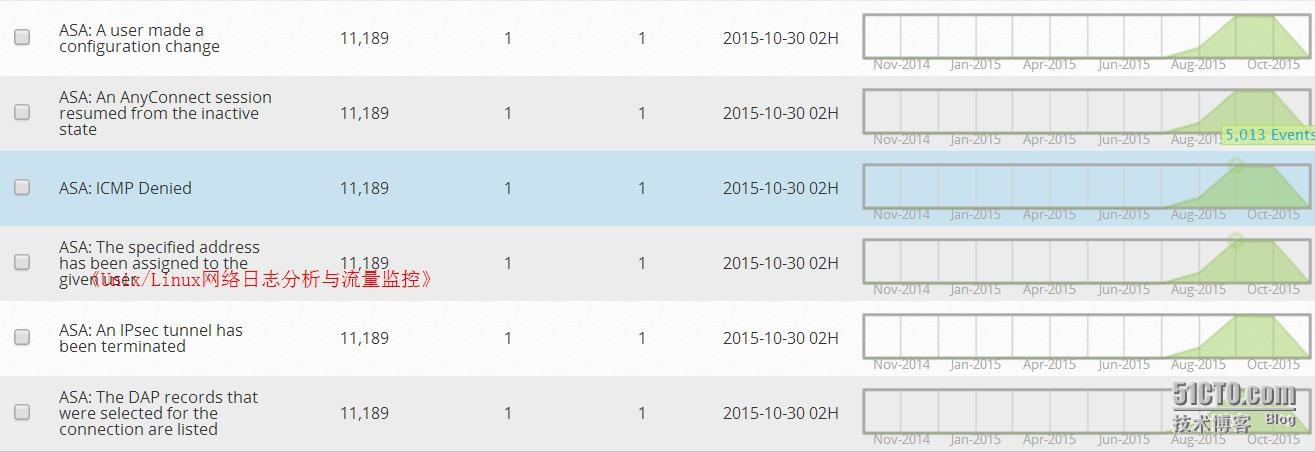
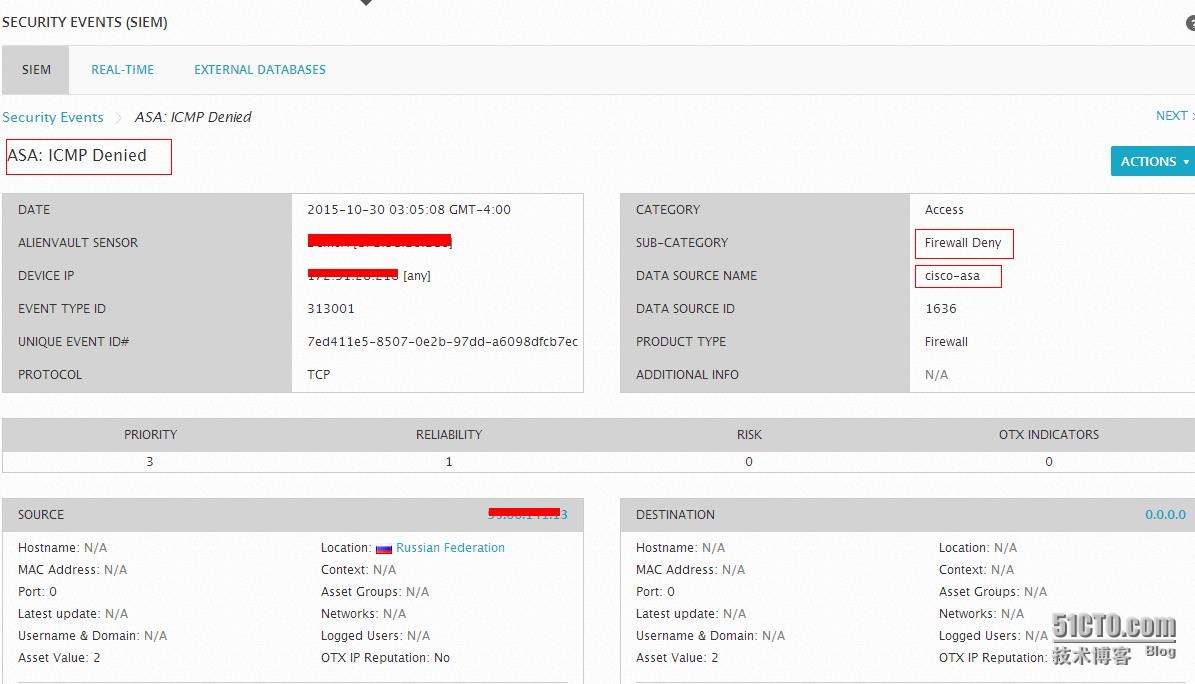
This is more than a dozen categories shown above, only the name of the event will be able to guess it. Below, we take ASA: ICMP Denied incident, for example, find out what to see in-depth clues. This ICMP first incident occurred 11,189 times, and each event details as shown below.
In fact, the original log is:
Aug 24 22:26:59 Sensor %ASA-3-313001: Denied ICMP type=8, code=0 from x5.y6.z41.13 on interface outsideIf you make a long-term look at these raw log monotonous, certainly I would go crazy. Or Cisco ASA plug-in help to the log processing so agile. Plug in the end is what? Let's look at an example (to OSSIM Cisco ASA plug-in for example)
Plug Location:
/etc/ossim/agent/plugins/cisco-asa.cfg
The plug-Scope:
the Cisco ASA _5500 7.0 7.1 7.2
the Cisco ASA_5510 - all versions
Plug-in ID Number: 1636
Plug-in type: detector
Raw log storage location: /var/log/cisco-asa.log
Here is the deal with this log regular expression:
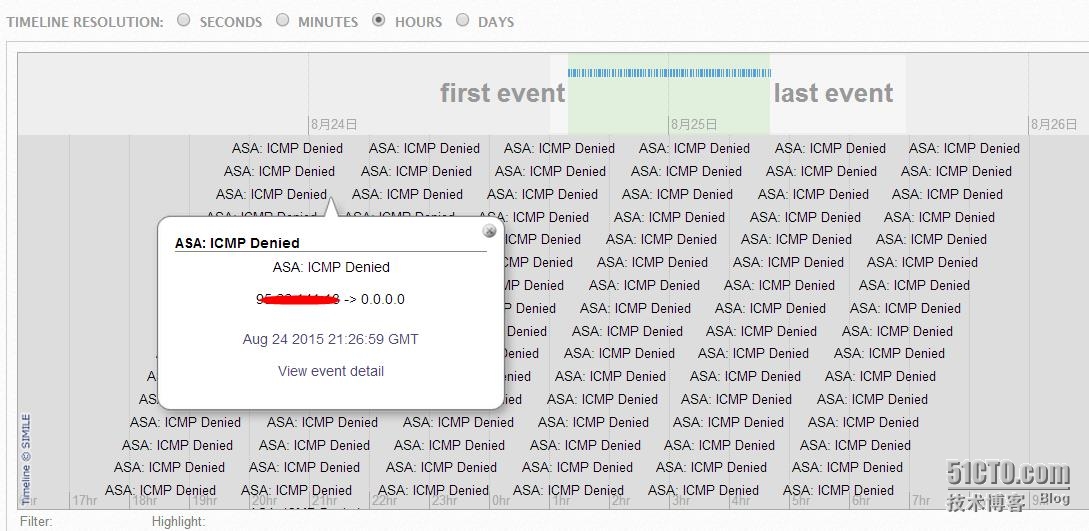
For in-depth analysis, the next step is to know the frequency and trends of these logs are generated, to achieve it on to Timeline.
Join Filter: filter out all the circumstances of a Cisco ASA event days, with sed, grep command to write a script yet? No, to achieve very Easy! As shown in FIG.
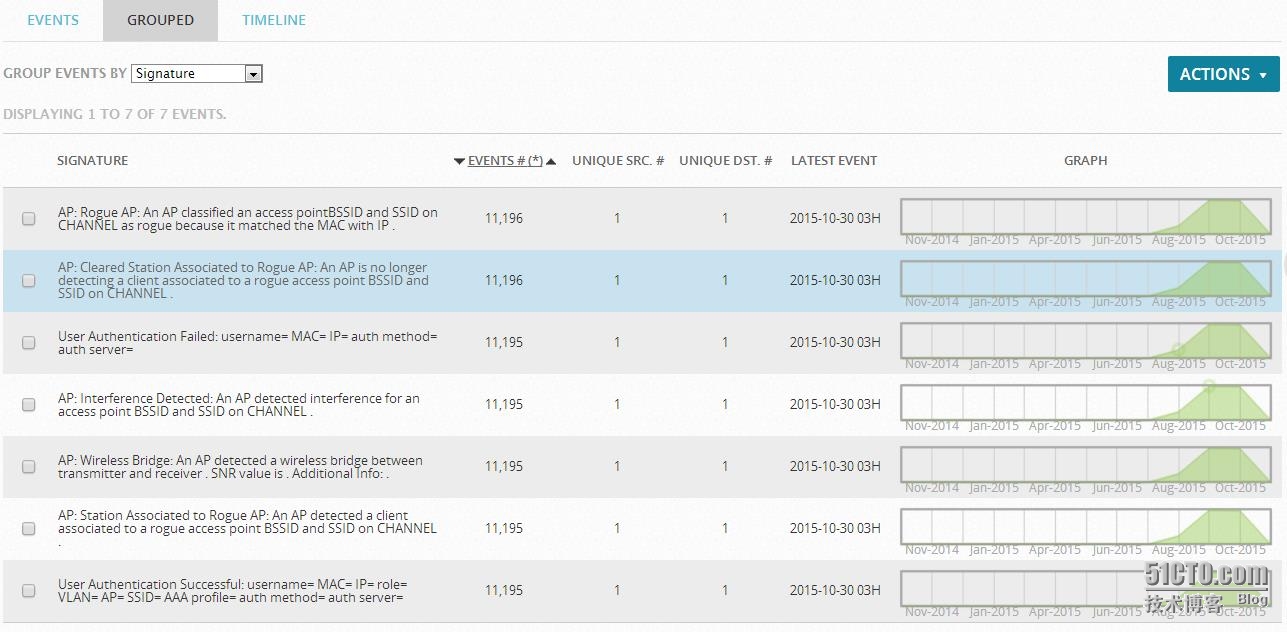
Cisco switches log collection
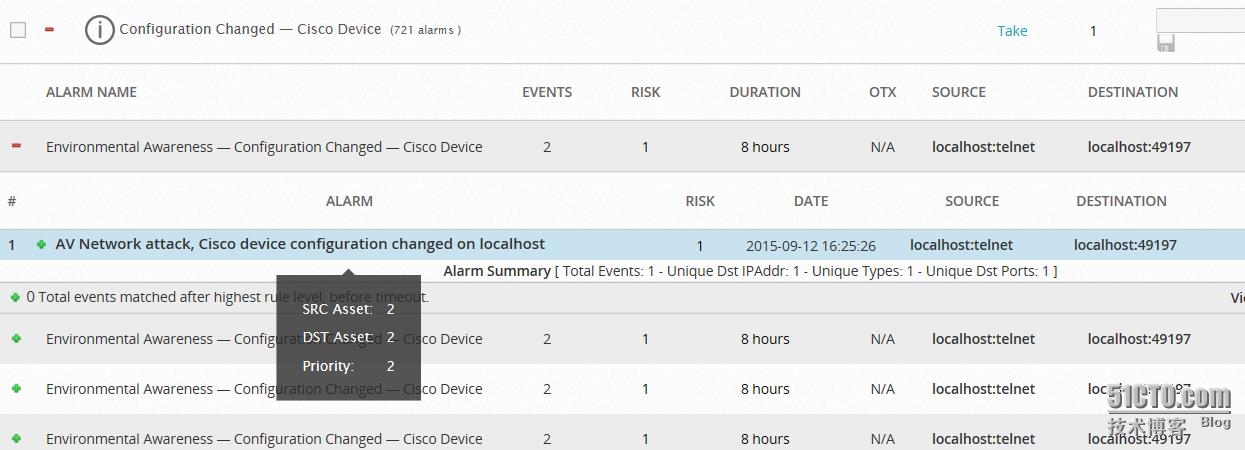
Once the configuration of Cisco equipment is modified, will immediately alarm
Here is OSSIM collected Fortinet ( Fortinet) firewall logs Category:
Warehousing wireless AP events
Note: Does not support Chinese log.
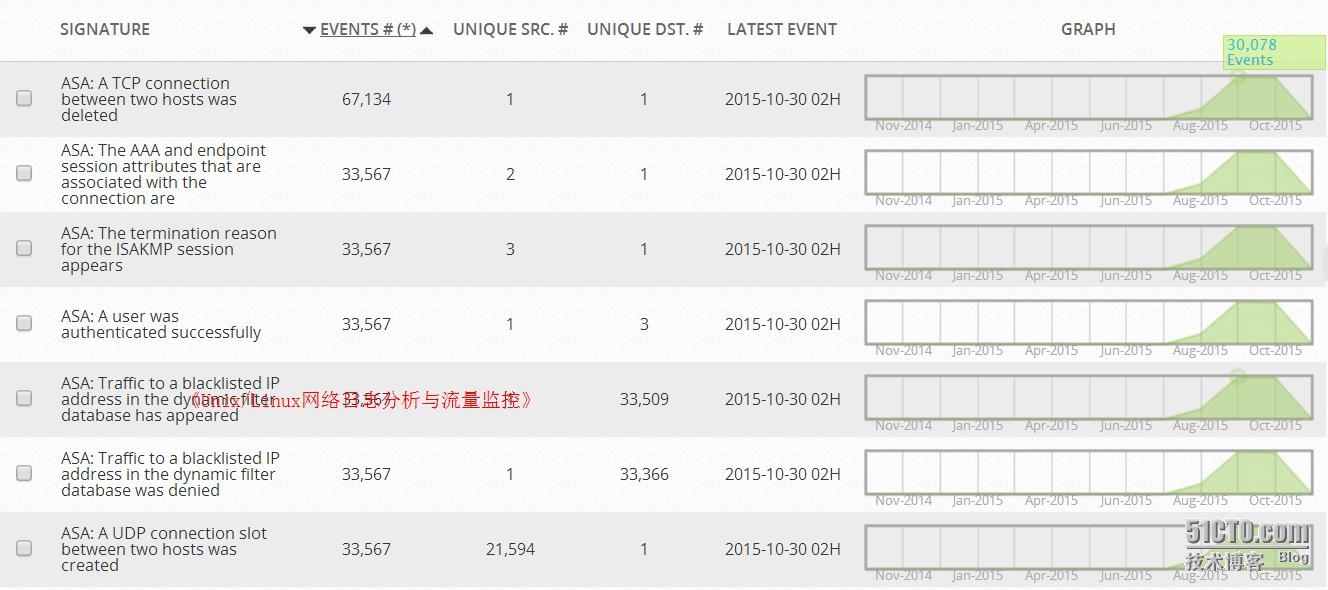
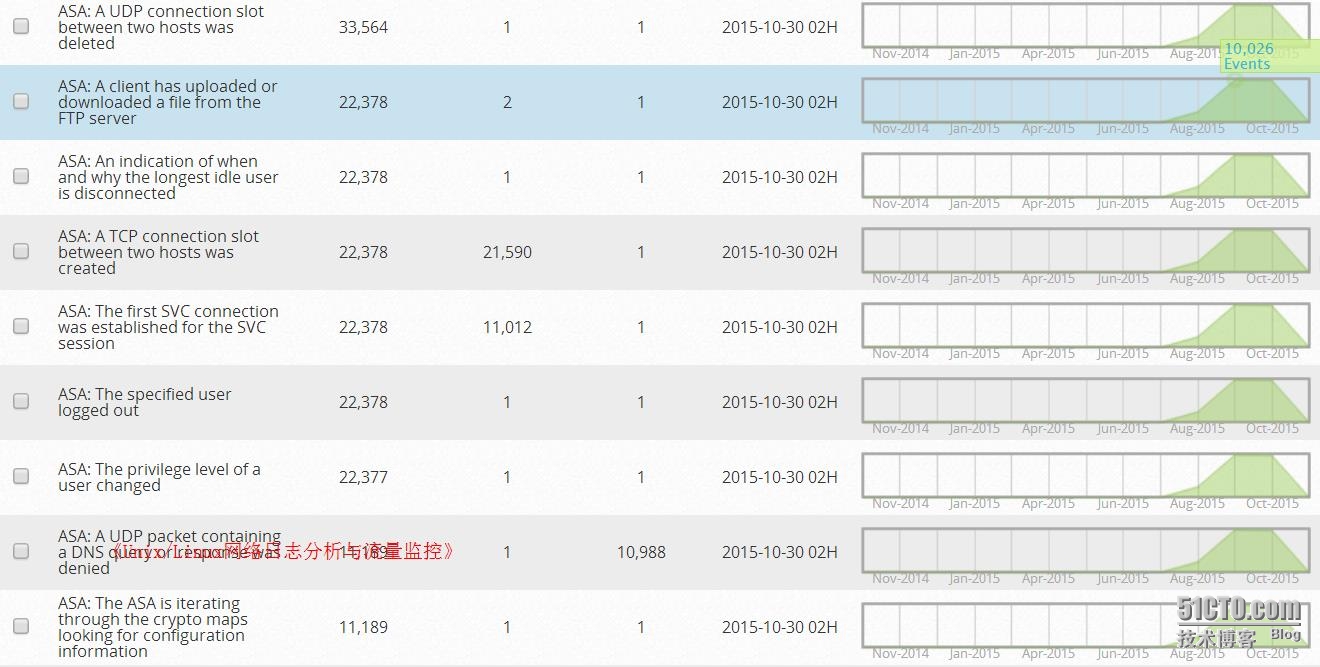
Well, the plugin system like this in the end how much Cisco ASA inside it? We look at the following illustration.
OSSIM more interesting content, please refer to the best-selling book "Unix / Linux Network log analysis and traffic monitoring."
This article comes from " Li Chenguang original technology blog " blog, declined reproduced!
Reproduced in: https: //my.oschina.net/chenguang/blog/613902