Configure remote access on a Cisco ASA firewall virtual private network (Easy Virtual Private Network) router and the same principle, the principle of Easy VPN unclear friends can refer Bowen Cisco router for remote access virtual private network --Easy virtual private network ( solve the problem of employee travel within the access network) configurations and configuration differences, after all, still on the firewall on the router. Here begin the configuration directly, no longer describes in detail!
Implement IPSec Virtual Private Network firewall can refer Bowen Cisco ASA firewalls IPSec virtual private network, can now do! ! !
First, the case of the environment
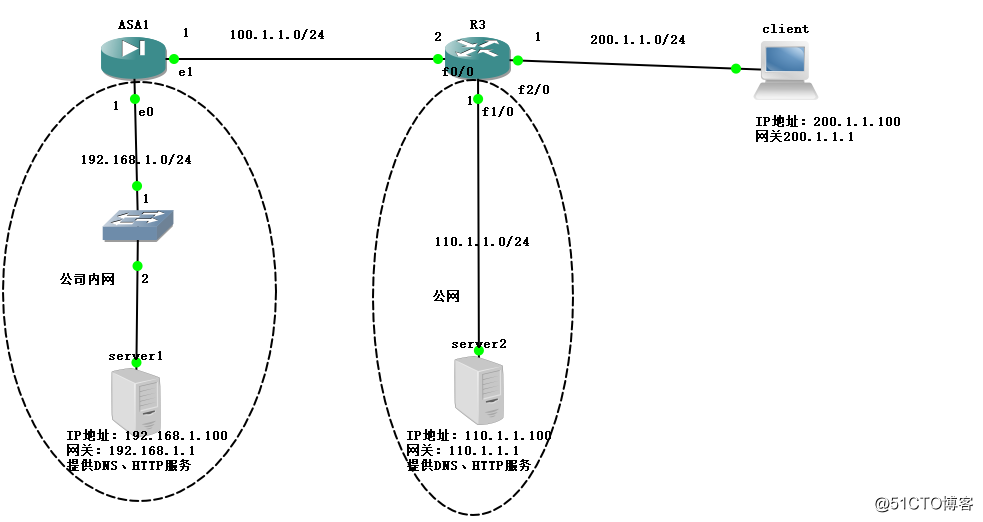
Due to the simulator, and it can lead to the firewall device connected to the terminal, so the middle put a switch!
Second, the case needs
(1) Easy user through a virtual private network through the domain name (www.yinuo.com) access to the internal Web site;
(2) the user through the domain name (www.xiaojiang.com) normal access to public Internet sites;
(3) the user according topology FIG requirements, and self-configure the IP address of the corresponding service;
Third, the implementation of case
(1) gateway ASA firewall configuration:
ASA(config)# int e0/0
ASA(config-if)# nameif inside
ASA(config-if)# ip add 192.168.1.1 255.255.255.0
ASA(config-if)# no sh
ASA(config-if)# int e0/1
ASA(config-if)# nameif outside
ASA(config-if)# ip add 100.1.1.1 255.255.255.0
ASA(config-if)# no sh
ASA(config-if)# exit
ASA(config)# route outside 0 0 100.1.1.2 //配置IP地址,并设置默认网关
ASA(config)# username lvzhenjiang password jianjian
//防护墙默认已经启用AAA,而且是通过本地验证,所以直接设置用户名和密码即可
ASA(config)# crypto isakmp enable outside //启用ISAKMP/IKE协议
ASA(config)# crypto isakmp policy 10
ASA(config-isakmp-policy)# encryption 3des
ASA(config-isakmp-policy)# hash sha
ASA(config-isakmp-policy)# authentication pre-share
ASA(config-isakmp-policy)# group 2
ASA(config-isakmp-policy)# exit
阶段1配置完成!
ASA(config)# ip local pool lv-pool 192.168.2.10-192.168.2.50
//配置地址池,向虚拟专用网客户端分发IP地址(不可和内网的IP地址为同一网段)
ASA(config)# access-list lv-acl permit ip 192.168.1.0 255.255.255.0 any
//定义一个命名的ACL用于允许192.168.1.0去往任何地址,当推送到客户端时,就会反过来
//变成了允许任何IP地址访问192.168.1.0。因为这里的源地址是站在路由器的角度的
ASA(config)# group-policy lv-group internal
//定义策略并放置在本地(external表示定义在别的AAA服务器上)
ASA(config)# group-policy lv-group attributes //定义用户组的属性
ASA(config-group-policy)# dns-server value 192.168.1.100
//定义发布给客户端的DNS服务器地址
ASA(config-group-policy)# address-pool value lv-pool
//调用刚才定义的地址池
ASA(config-group-policy)# split-tunnel-policy tunnelspecified
//关于上面的“split-tunnel-policy”后面可以接三种类型的规则,如下:
* tunnelspecified表示所有匹配的流量走隧道,我这里选择的就是这个;
* tunnelall:所有流量必须走隧道,即不做分离隧道,这是默认设置,一般不使用该选项;
* excludespecified:所有不匹配ACL的流量走隧道,不推荐使用此选项;
ASA(config-group-policy)# split-tunnel-network-list value lv-acl
//调用刚才定义的ACL
ASA(config-group-policy)# exit
ASA(config)# tunnel-group lv-group type ipsec-ra //指定隧道组的类型是远程访问
ASA(config)# tunnel-group lv-group general-attributes //配置隧道组的属性
ASA(config-tunnel-general)# address-pool lv-pool //调用刚才定义的地址池
ASA(config-tunnel-general)# default-group-policy lv-group //调用用户组策略
ASA(config-tunnel-general)# exit
ASA(config)# tunnel-group lv-group ipsec-attributes //定义隧道组名称
ASA(config-tunnel-ipsec)# pre-shared-key lv-key //定义隧道组密码
ASA(config-tunnel-ipsec)# exit
阶段1.5配置完成
ASA(config)# crypto ipsec transform-set lv-set esp-3des esp-sha-hmac
//定义传输集名称,及加密验证的方式
ASA(config)# crypto dynamic-map lv-dymap 1 set transform-set lv-set
//定义动态map名称为lv-dymap,优先级为1,并调用刚才定义的传输集
ASA(config)# crypto map lv-stamap 1000 ipsec-isakmp dynamic lv-dymap
//定义静态map,优先级为1000 ,调用动态map
ASA(config)# crypto map lv-stamap int outside
//将静态map应用到网关连接外网的接口上
阶段2配置完成(2) for testing the client
Windows 7 system used here to test! If you are using windows 10 system of friends, when you install client tools will be relatively trouble, we could refer Bowen Windows 10 system installed VPN client tools
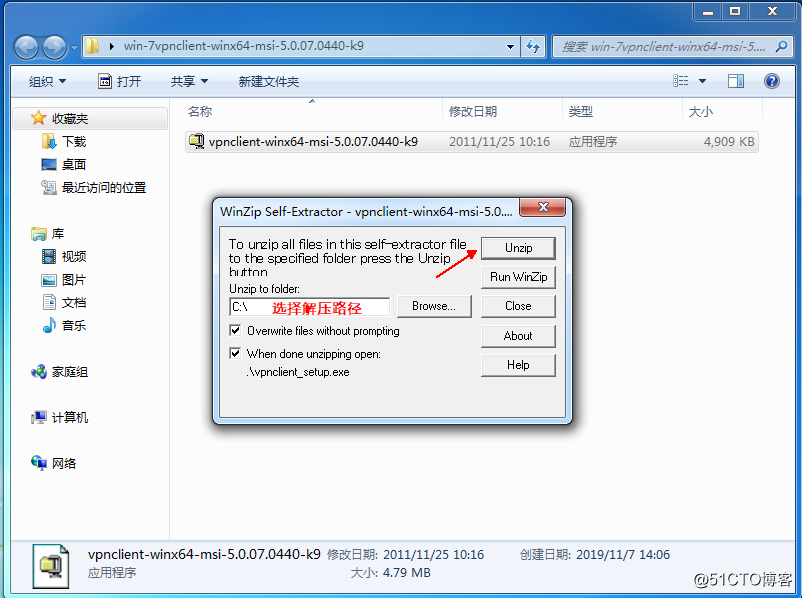
Then the next step can be no brain! After the installation is complete, 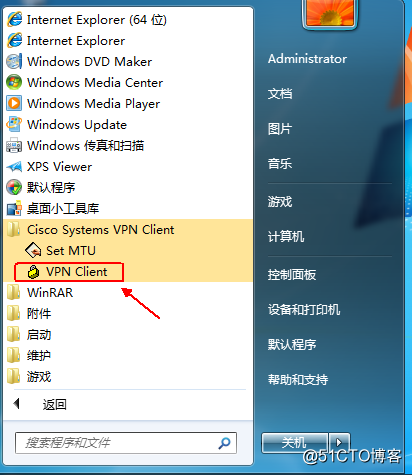
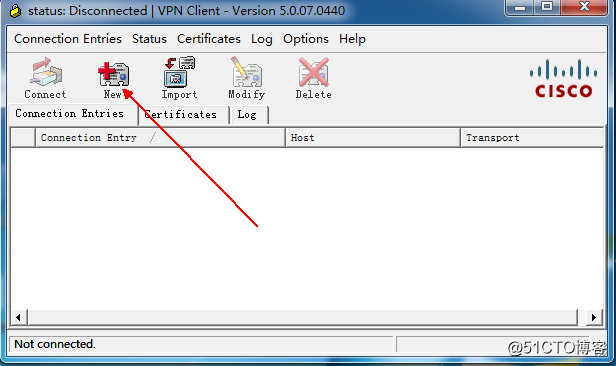
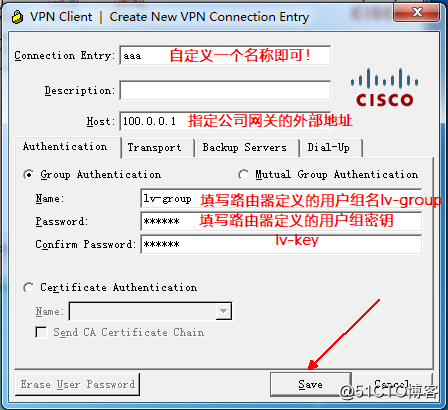
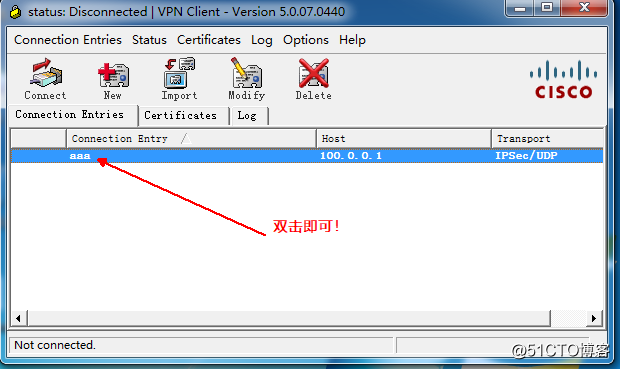
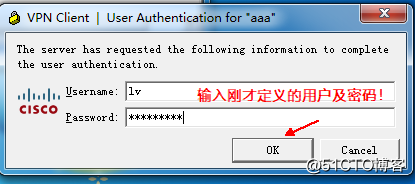
the connection is successful, IP address, view the generated virtual private network 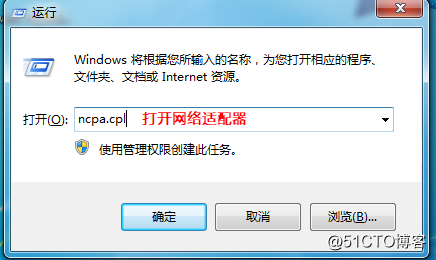
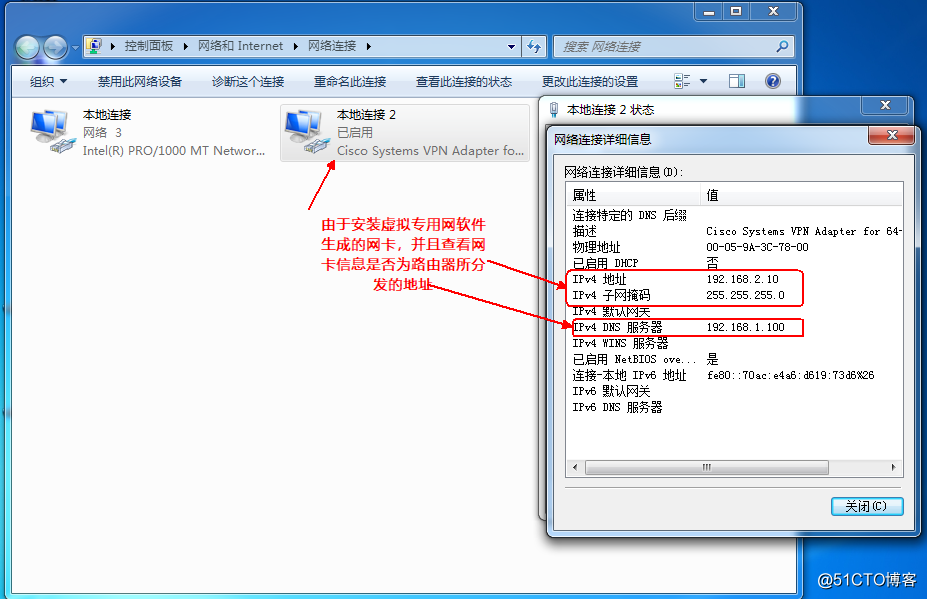
access to internal company server test access public network! 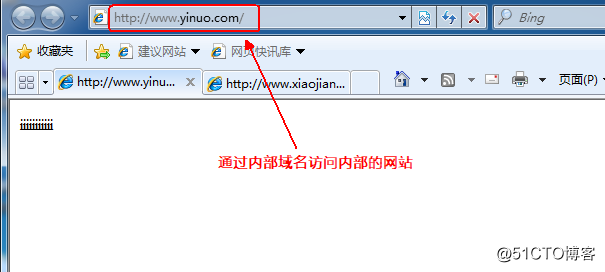
Successful visit!
-------- end of this article so far, thanks for reading --------