Squid server
1. ACL access control of Squid server
Set up a squid server click the link below to
set up a squid server
- Function: Squid provides a powerful proxy control mechanism, which can be restricted by setting ACL, and can
(url表示浏览器访问服务器的网络路径 )filter various conditions for source address, destination address, range and URL path , access time, etc. - ACL access control is achieved through two steps:
(1) Use ACL configuration items to define the conditions that need to be controlled
(2) Use http_access configuration items to perform "运行" or "拒绝" access control on the defined list
ACL的所有配置项都是写在squid的主配置文件中的
Define access control list
- grammar structure:
acl 列表名称 列表类型 列表内容 - Note:
(1) List name: you can customize it, and you can choose any name
(2) List type:
src (源地址、源网段、源地址范围)
dst (目标地址、网段、主机名)
port (目标端口)
destomain (目标域名)
time (时间段)
maxconn (每个客户机的并发连接数)
url_regex (目标资源的url地址)
urlpath_regex (网址中主机名的部分)
******例如:
acl abc src 192.168.100.10 (acl名字是abc,内容是源地址是192.168.100.10的ACL)
Set access permissions
- grammar structure:
http_access allow 列表名 (允许列表使用代理)
http_access deny 列表名 (拒绝列表使用代理)
- Note:
(1) If you do not set any rules, squid server rejects client requests
(2) if there are rules, but can not find matching items, squid will use the last rule opposite action
is recommended:先拒绝后允许or先允许后拒绝the way
the general rule is the lasthttp_access allow allorhttp_access deny all
Example (1):
******禁止本网段客户机使用此代理服务
[root@Squid ~]# cp /etc/squid.conf /etc/squid.conf.bak (现实环境中最好先做一个备份,以免写错)
[root@Squid ~]# vim /etc/squid.conf (打开主配置文件)
定义一条名为aaa的列表,匹配来自192.168.100.0源网段的代理访问,然后拒绝此列表
如果是按我上一次的squid传统代理或者透明代理继续做的话,记得把下面的 reply_body_max_size 10 MB 和 http_access allow all 删除再写
。。。。。。
24 acl Safe_ports port 591 # filemaker
25 acl Safe_ports port 777 # multiling http
26 acl CONNECT method CONNECT
27 acl aaa src 192.168.100.0/24 (定义一条名为aaa的acl列表,源网段是192.168.100.0)
28 http_access deny aaa (拒绝名为aaa的列表,也就拒绝了100网段使用代理服务)
29 #
。。。。。。
保存退出
[root@Squid ~]# systemctl restart squid (重启服务)
Verification: Whether to use win7 to access the browser is rejected (the squid server has been set up)
- First, point the win7 proxy server to the specified server address
(我这里是192.168.100.11,不会指的话看我最上面的链接即可)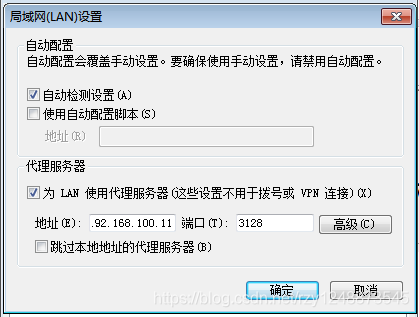
- Visit website services
(提前搭建一个httpd就行了,我这里的httpd地址是192.168.100.12)
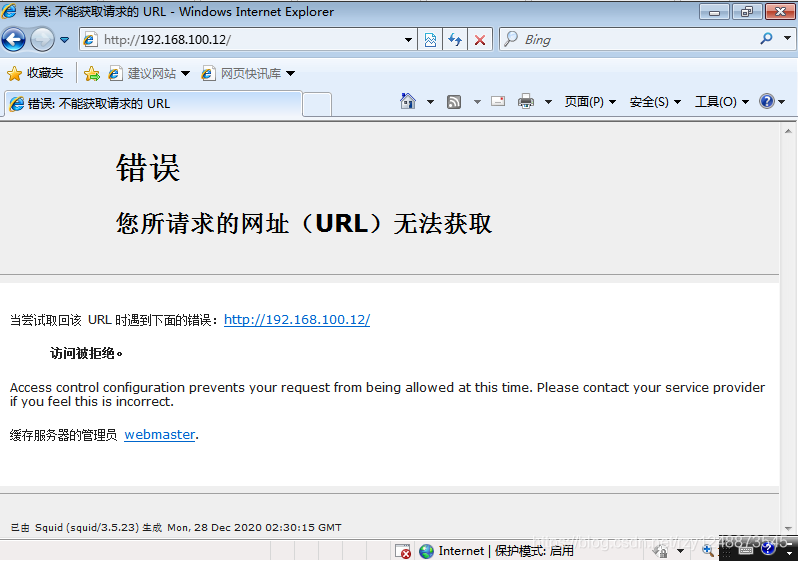
- Use the squid server to access and find that it can be accessed normally, indicating that the acl configuration is successful
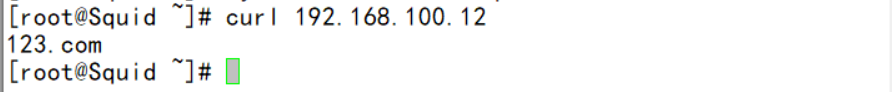
Example (2):
******允许本网段客户机在工作时间上网
[root@Squid ~]# vim /etc/squid.conf (进入主配置文件)
。。。。。。
26 acl CONNECT method CONNECT
27 acl aaa src 192.168.100.0/24 (写一个名为aaa的列表,源网段是100网段)
28 acl bbb time MTWHF 08:30-17:30 (写一个名为bbb的列表,限制时间为8:30到17:30)
29 http_access allow aaa bbb (允许100网段只能在8:30带17:30这个时间段里使用squid代理服务)
30 http_access deny aaa (除了8:30到17:30这个时间段之外都不能使用squid代理服务)
31 #
。。。。。。
保存退出
[root@Squid ~]# systemctl restart squid (重启squid服务)
[root@Squid ~]# date 122512302020 (利用date修改时间)
2020年 12月 25日 星期五 12:30:00 CST
验证的话得最好使用另外一台linux,win7时间不一样会出错,这里就不验证了,配置项都是没有错的真实环境是会生效的
Example (3):
******通过黑名单来限制目标网站
ip黑名单
[root@Squid ~]# vim /tmp/ipblock.list (往里面写入ip即可,文件名随便写)
192.168.100.12
保存退出
网址黑名单
[root@Squid ~]# vim /tmp/dmblock.list (往里面写入域名即可,文件名随便写)
.qq.com
.baidu.com
保存退出
[root@Squid ~]# vim /etc/squid.conf
。。。。。。
26 acl CONNECT method CONNECT
27 acl aaa src 192.168.100.0/24
28 acl bbb time MTWHF 08:30-17:30
29 acl ccc dst "/tmp/ipblock.list" (指定ip黑名单,文件名要相同)
30 acl ddd dstdomain "/tmp/dmblock.list" (指定网址黑名单,文件名要相同)
31 http_access deny ccc (禁用ip黑名单里的ip地址)
32 http_access deny ddd (禁用网址黑名单里的域名)
33 http_access allow aaa bbb
34 http_access deny aaa
35
。。。。。。
保存退出
[root@Squid ~]# systemctl restart squid (重启服务)
验证ip的话直接验证即可,验证域名的话要在web服务器上搭建dns,然后配置自己想要禁用的域名即可,
三个示例其实都大同小异,都是指定列表名,后面加指定选项,通过http_access allow 或者http_access deny 来禁用或者允许
Two, Squid log analysis
SARG: A Squid log analysis tool that uses html format to list in detail the site information, time occupancy information, ranking, number of connections, visits, etc. that each user visits to the internet.
The full name of SARG is: Squid Analysis Report Generator
访问sarg必须有web页面所以需要安装httpd
Install SARG
******安装GD库
[root@Squid ~]# mount /dev/cdrom /media/cdrom/ (挂载镜像)
[root@Squid ~]# yum -y install gd gd-devel (使用yum进行安装)
。。。。。。
完毕!
******安装SARG
[root@Squid ~]# mkdir /usr/local/sarg (创建sarg的根目录)
[root@Squid ~]# ll (上传源码包sarg-2.3.7.tar.gz)
总用量 5988
-rw-------. 1 root root 1263 10月 8 17:22 anaconda-ks.cfg
-rw-r--r-- 1 root root 1282619 12月 28 16:05 sarg-2.3.7.tar.gz
drwxr-xr-x 17 squid squid 4096 12月 24 17:38 squid-3.5.23
-rw-r--r-- 1 root root 4835525 12月 24 17:36 squid-3.5.23.tar.gz
解压————配置————编译————安装
[root@Squid ~]# tar zxvf sarg-2.3.7.tar.gz
[root@Squid sarg-2.3.7]# ./configure --prefix=/usr/local/sarg --sysconfdir=/etc/sarg --enable-extraprotection && make && make install (配置编译安装)
******配置
[root@Squid sarg-2.3.7]# cd /etc/sarg/ (到sarg的主配置文件目录)
[root@Squid sarg]# vim sarg.conf (文件里都是注释行)
添加:
access_log /usr/local/squid/var/logs/access.log *指定squid的访问日志文件
title "Squid User Access Reports" *网页标题
output_dir /var/www/html/sarg *sargent报告的输出目录
user_ip no *使用用户名显示
topuser_sort_field BYTES reverse *指定不计入排序的站点列表文件
user_sort_field BYTES reverse *在top排序中,指定连接次数、访问字节数、采用降序排列。(降序reverse;升序 normal)
exclude_hosts /usr/local/sarg/noreport *用户访问记录,连接次数按降序排列
overwrite_report no *当日期报告已存在,不覆盖
mail_utility mailq.postfix *发送邮件报告的命令
charset UTF-8 *使用字符集为UTF-8
weekdays 0-6 *指定排序的星期周期(0为周日)
hours 0-23 *排序的时间周期
www_document_root /var/www/html *网页根目录
保存退出
******后续操作
[root@Squid sarg]# touch /usr/local/sarg/noreport
[root@Squid sarg]# ln -s /usr/local/sarg/bin/sarg /usr/local/bin/ (优化执行路径)
[root@Squid sarg]# sarg (启动)
SARG: 纪录在文件: 99, reading: 100.00%
SARG: 成功的生成报告在 /var/www/html/sarg/2020Dec24-2020Dec28
[root@Squid sarg]# yum -y install httpd (安装httpd服务)
[root@Squid sarg]# systemctl start httpd (启动httpd服务)
******计划任务+脚本
[root@Squid sarg]# vim /usr/local/sarg/daily.sh (编写脚本)
写入
#!/bin/bash
TD=$(date +%d/%M/%Y)
YETD=$(date -d '1 day ago' +%d/%M/%Y)
/usr/local/sarg/bin/sarg –l /usr/local/squid/var/logs/access.log –o /var/www/html/sarg –z –d $YETD-$TD &>/dev/null
exit 0
保存退出
[root@Squid sarg]# chmod +x /usr/local/sarg/daily.sh (添加可执行权限)
[root@Squid sarg]# crontab -e (编写任务计划)
00 00 * * * /usr/local/sarg/daily.sh (每天的0点执行这个脚本)
******验证
[root@Squid sarg]# tail -3 /usr/local/squid/var/logs/access.log (可以查看日志)
1609143548.785 0 192.168.100.13 TCP_MISS/404 491 GET http://192.168.100.11/noindex/css/fonts/BoldItalic/OpenSans-BoldItalic.eot? - ORIGINAL_DST/192.168.100.11 text/html
1609143548.785 0 192.168.100.13 TCP_MISS/404 489 GET http://192.168.100.11/noindex/css/fonts/ExtraBold/OpenSans-ExtraBold.eot? - ORIGINAL_DST/192.168.100.11 text/html
1609143548.786 0 192.168.100.13 TCP_MISS/404 501 GET http://192.168.100.11/noindex/css/fonts/ExtraBoldItalic/OpenSans-ExtraBoldItalic.eot? - ORIGINAL_DST/192.168.100.11 text/html
可以看到那个ip访问了httpd网站
win7上使用浏览器访问http://192.168.100.11/sarg可以查看