The wind is rustling and the water is cold
-
- Black and white gray test
- static testing dynamic testing
- stack
- The difference between dynamic libraries and static libraries
- TCP three-way handshake
- Test login interface
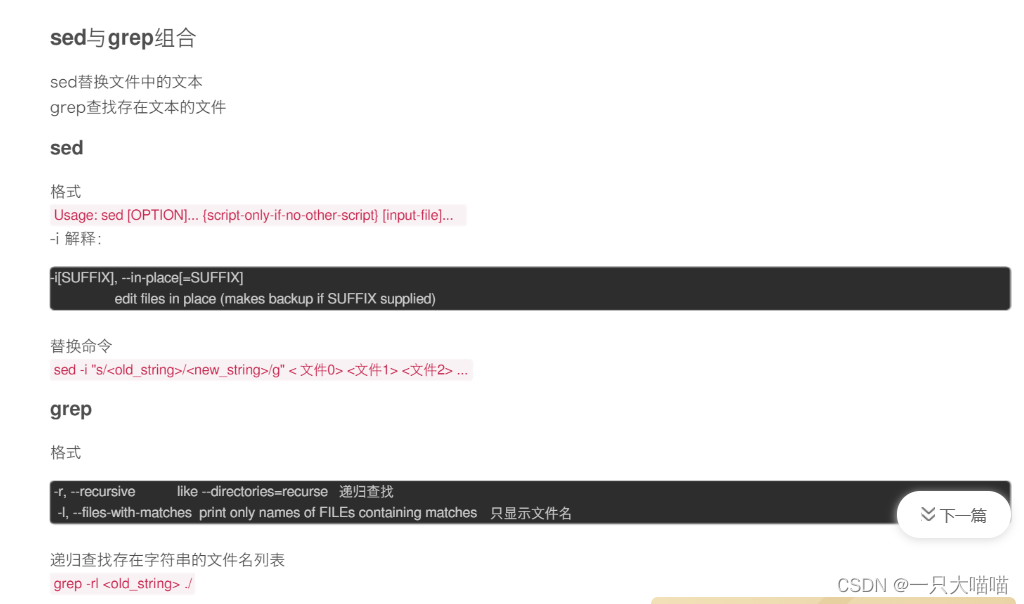
- Linux replacement command sed 's/old address/new value' grep
- POST and GET
- The difference between cookies and sessions
- object-oriented
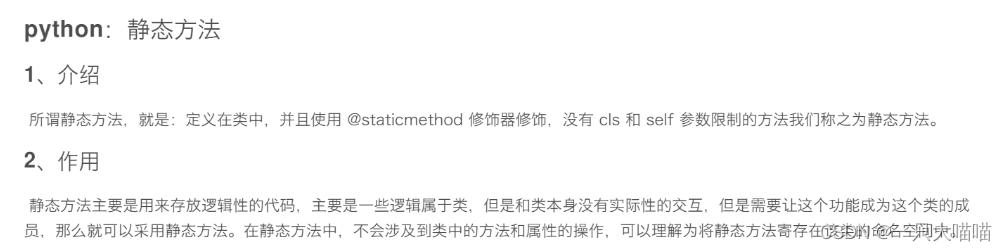
- static method
- Exception handling in Python try/except/finally/raise usage analysis
- Linux common commands
- DNS working process
Black and white gray test
1. Divided according to testing technology
Black box testing uses the external behavior of software to discover defects and errors.
The black box testing method treats the test object as a black box and does not consider the internal structure and processing of the program at all.
Testing is performed at the program interface. It only checks whether the sample sequence is implemented normally according to the requirements specification.
White-box testing looks for problems by analyzing and detecting the internal structure of the program.
White box testing can treat the program as being installed in a transparent white box, understand the program structure and processing process, check whether all structures and paths are correct, and check whether the internal actions of the software are carried out normally according to the design instructions.
White box testing is also called structural testing
Gray box testing is a test between white box testing and black box testing. Gray box testing focuses on the correctness of the output to the input; it also focuses on internal performance, but this focus is not as detailed and complete as white box testing. It only judges the internal operating status through some representative phenomena, events, and signs.
Gray box testing combines elements of white box testing and black box testing. The user side, specific system knowledge, and operating environment are also considered. It evaluates the design of application software in the context of the interoperability of system components
static testing dynamic testing
Static testing refers to a process that does not actually run the object under test, but only statically checks for possible errors in program code, interfaces or documents. Code testing: mainly tests whether the code conforms to corresponding standards and specifications. Interface testing: mainly tests the actual interface of the software and Whether the description in the requirements is consistent with the document test: mainly testing whether the user manual and requirements description truly meet the actual needs of the user
Dynamic testing refers to the process of actually running the object under test, inputting corresponding test data, and checking whether the actual output results match the expected results. So the only criterion for us to judge whether a test is a dynamic test or a static test is to see whether the program is running.
stack
The stack is a specific
storage area or register that has a fixed end and a floating end [1]. The data stored in the heap storage area is a special data structure. All data can be deposited or taken out only at one end of the float (called the top of the stack). Access is strictly in accordance with the principle of "first in, last out". The elements located in the middle must be in the upper part of the stack (those who enter the stack last). The elements can be removed only after they are removed one by one. Opening up an area in the internal memory (random access memory) as a stack is called a software stack; a stack composed of registers is called a hardware stack.
The difference between dynamic libraries and static libraries
Differences: 1. The extension of static libraries is generally ".a" or ".lib"; the extension of dynamic libraries is generally ".so" or ".dll". 2. The static library will be directly integrated into the target program during compilation, and the successfully compiled executable file can run independently; the dynamic library will not be placed in the connected target program during compilation, that is, the executable file cannot run independently.
TCP three-way handshake
In the TCP/IP protocol, the TCP protocol provides reliable connection services and uses a three-way handshake to establish a connection.
First handshake: Client sets the SYN flag to 1, randomly generates a value seq=J, and sends the data packet to the Server. The Client enters the SYN_SENT state and waits for confirmation from the Server.
SYN: Synchronize Sequence Numbers
Second handshake: After receiving the data packet, the Server knows that the Client requests to establish a connection from the flag bit SYN=1. The Server sets both the flag bits SYN and ACK to 1, ack=J+1, randomly generates a value seq=K, and This data packet is sent to the Client to confirm the connection request, and the Server enters the SYN_RCVD state.
Third handshake: After the Client receives the confirmation, it checks whether the ack is J+1 and whether the ACK is 1. If it is correct, it sets the flag ACK to 1, ack=K+1, and sends the data packet to the Server. Server checks whether ack is K+1 and ACK is 1. If correct, the connection is established successfully. Client and Server enter the ESTABLISHED state and complete the three-way handshake. Then the Client and Server can start transmitting data.
Why a three-way handshake is needed is to solve one of the following problems:
The first connection request segment sent by the client was not lost, but stayed at a certain network node for a long time, so that it was delayed until a certain time after the connection was released before reaching the server. It turns out that this is a message segment that has long since expired. However, after the server receives this invalid connection request segment, it mistakenly thinks that it is a new connection request sent by the client again. So it sends a confirmation message segment to the client and agrees to establish the connection. Assuming that the three-way handshake is not used, a new connection is established as long as the server sends a confirmation. Since the client has not issued a request to establish a connection, it will not pay attention to the server's confirmation and will not send data to the server. But the server thinks that a new transport connection has been established and has been waiting for the client to send data. In this way, many resources of the server are wasted. The three-way handshake method can prevent the above phenomenon from happening.
Four-Way Wavehand terminates the TCP connection, which means that when disconnecting a TCP connection, the client and server need to send a total of 4 packets to confirm the disconnection. In socket programming, this process is triggered by either the client or the server executing close.
Test login interface
https://blog.csdn.net/QuietSnow_wuyaya/article/details/104965626
Linux replacement command sed 's/old address/new value' grep
POST and GET
1.POST and GET are essentially the same.
2. POST and GET are both basic methods of HTTP requests.
3. The main differences are as follows:
3-1 GET requests are harmless when the browser refreshes or rolls back. If POST is used, the data will be resubmitted.
3-2 GET can be bookmarked, but POST cannot.
3-3 GET can be stored in the cache. POST will not work
3-4 GET will store the data in the browser's history, POST will not
3-5 GET encoding format can only use ASCII code, POST has no restrictions
3-6 GET data type urlencode, POST is URLENCODE, form-data
3 -7 Visibility parameters can be seen by users in the URL, and POST parameters will not be seen by users in REQUSET BODY
3-8 Security GET is relatively unsafe, POST is relatively safe
3-9 The length parameter is generally limited to 2048 (related to WEB servers) , parameters are unlimited.
4. When requesting GET and POST,
4-1 GET sends the hearer and data in the data to the server together and returns 200code.
4-2 POST first sends the hearer to the server and returns 100continue, and then sends the data to the server. Returns 200
4-3 GET sends one TCP data packet to the server, while POST sends two TCP data packets to the server.
4-4 GET and POST have already been defined, so it is best not to mix them.
5. GET and POST are essentially the same. GET can add a Request Body, and POST can also add parameters to the URL. Implementation is possible.
The difference between cookies and sessions
The difference between cookie and session:
1. The cookie data is stored on the client's browser, and the session data is stored on the server.
2. Cookies are not very safe. Others can analyze the COOKIE stored locally and conduct COOKIE deception.
Sessions should be used for security reasons.
3. The session will be saved on the server for a certain period of time. When access increases, it will take up more of your server's performance.
In order to reduce server performance, COOKIE should be used.
4. The data saved by a single cookie cannot exceed 4K. Many browsers limit a site to save up to 20 cookies.
object-oriented
1. Object-oriented is a programming idea that conforms to people’s thinking habits and turns the executor into a commander.
Simplify complex things. If you want to complete the opinion thing, find an object with such function
If it can be found, call the function of this object to complete the task. If it cannot be found, create
An object with such a function can be called to complete the task.
2. Object-oriented is a programming idea that encapsulates data into objects and uses object methods to
To operate data, the entire function is completed through mutual calls and cooperation between objects.
process.
Features of object-oriented: Encapsulation: Encapsulate code with certain functions and call it when used. Inheritance: Put public properties and methods in the parent class, and consider your own unique properties and methods. Polymorphism: During program running, the process of dynamically executing different operation codes based on different execution conditions is called runtime polymorphism.
- Short answer
- The difference between class objects and instance objects
The class object is the class itself. When a class is encountered, a new namespace is created. The namespace
Contains the names of all class variables and method definitions.
An instance object is an instance created through a class object (returned after the class object is instantiated)
It is an instance object), used to store instance attributes and store references to instance objects.
- The difference between class attributes and instance attributes
Class attributes: defined inside the class, outside the method, and belong to all class objects and all instance objects
Call: class object.property = value
Instance attributes: variables initialized by init and attributes created by instance objects
Call: instance object.properties
- The difference between class methods, instance methods and static methods
Class method: must have a parameter, which is represented by the current class object, usually cls, in
Add @classmethod to the head of the method
Instance method: must have a parameter indicating the current instance object, usually self
Static method: the format of an ordinary function, there is no mandatory requirement to pass parameters, in the head of the method
static method
Exception handling in Python try/except/finally/raise usage analysis
Exceptions occur during program execution. If Python cannot handle the program normally, an exception will occur, causing the entire program to terminate execution. Use try/except statements in Python to catch exceptions.
try/except
There are many types of exceptions. You can use Exception to catch all exceptions when you are not sure about the types of exceptions that may occur:
The try statement can also be followed by an else statement, so that when the try statement block is executed normally and no exception occurs, the content after the else statement will be executed:
If a try statement is followed by a finally statement, regardless of whether an exception occurs in the try statement block, the content after the finally statement will be executed after the try is executed:
Linux common commands
https://wenku.baidu.com/view/c8a8e10bee630b1c59eef8c75fbfc77da269973b.html
DNS working process
The working process of DNS is as follows:
1. The client makes a domain name resolution request and sends the request to the local domain name server;
2. When the local domain name server receives the request, it first queries the local cache. If there is such a record, the local domain name server directly returns the query result;
3. If there is no such record in the local cache, the local domain name server will directly send the request to the root domain name server, and then the root domain name server will return to the local domain name server the primary domain name server of the queried domain (subdomain of the root). address;
4. The local server sends a request to the domain name server returned in the previous step, and then the server that accepts the request queries its own cache. If there is no such record, the address of the relevant lower-level domain name server is returned;
5. Repeat step 4 until the correct record is found;
6. The local domain name server saves the returned results to the cache for next time use, and returns the results to the client at the same time.