Let’s talk about the ACID properties of transactions
Atomicity: Atomicity means that a transaction is an indivisible unit of work, and all operations in the transaction either succeed or fail.
Consistency: Transactions take effect as expected, and the state of the data is the expected state
Isolation: The isolation of transactions means that when multiple users access the database concurrently, the transactions opened by the database for each user cannot be interfered with by the operation data of other transactions, and multiple concurrent transactions must be isolated from each other.
Durability: Once a transaction is committed, its changes to the data in the database are permanent
Let’s talk about the difference between the two strings char and varchar in mysql
Introduction to two types
CHAR(M) is a fixed-length character string. M represents the length of the column, ranging from 0 to 255 characters. Trailing spaces in inserted data will be automatically removed. The MyISAM storage engine is recommended.
For example: CHAR(4) defines a fixed-length string column containing a maximum of 4 characters. When a CHAR value is retrieved, trailing spaces are removed.
VARCHAR(M) is a variable-length string, M represents the length of the maximum column, and the range of M is 0~65535. Trailing spaces are not removed. The maximum actual length of a VARCHAR is determined by the size of the longest line and the character set used, while the actual space occupied is the actual length of the string plus one. InnoDB storage engine is recommended.
For example: VARCHAR(50) defines a string with a maximum length of 50. If the inserted string has only 10 characters, the actual stored string will be 10 characters and a string end character. VARCHAR trailing spaces are preserved when values are saved and retrieved.
The impact of storage engines on the choice of CHAR and VARCHAR:
For the MyISAM storage engine, it is best to use fixed-length data columns instead of variable-length data columns. This makes the entire table static, making data retrieval faster, trading space for time.
For the InnoDB storage engine, it is best to use variable-length data columns, because the storage format of the InnoDB data table is not divided into fixed length and variable length, so using CHAR is not necessarily better than using VARCHAR, but because VARCHAR is based on the actual length Storage is more space-saving, so it is better for disk I/O and total data storage.
TEXT type
The TEXT column stores non-binary strings, such as article content, comments, etc. When saving or querying TEXT column values, trailing spaces are not removed.
There are 4 types of TEXT types: TINYTEXT, TEXT, MEDIUMTEXT and LONGTEXT. Different TEXT types have different storage spaces and data lengths.
TINYTEXT represents a TEXT column with a length of 255 (28-1) characters.
TEXT represents a TEXT column with a length of 65535 (216-1) characters.
MEDIUMTEXT represents a TEXT column with a length of 16777215 (224-1) characters.
LONGTEXT represents a TEXT column with a length of 4294967295 or 4GB (232-1) characters.
Let’s talk about java’s IO model
The IO model is divided into three types: BIO [synchronous blocking IO], NIO [synchronous non-blocking IO], and AIO [asynchronous non-blocking IO].
First, you can briefly experience the scenarios of the three IO models: Suppose you need to wait for the boiling water to boil: 1. Synchronous blocking: You squat next to the boiling kettle, doing nothing, waiting for the boiling water to boil. 2. Synchronous non-blocking: You go to read a book and study, and check after a while to see if the boiling water is boiling. 3. Asynchronous and non-blocking: You run to read a book and study. When the water boils, it will make a sound. You will come back after hearing the sound.
BIO:
In BIO mode, both writing and reading of data must be blocked in a thread. The thread blocks before the writing is completed or the reading is completed.
NIO:
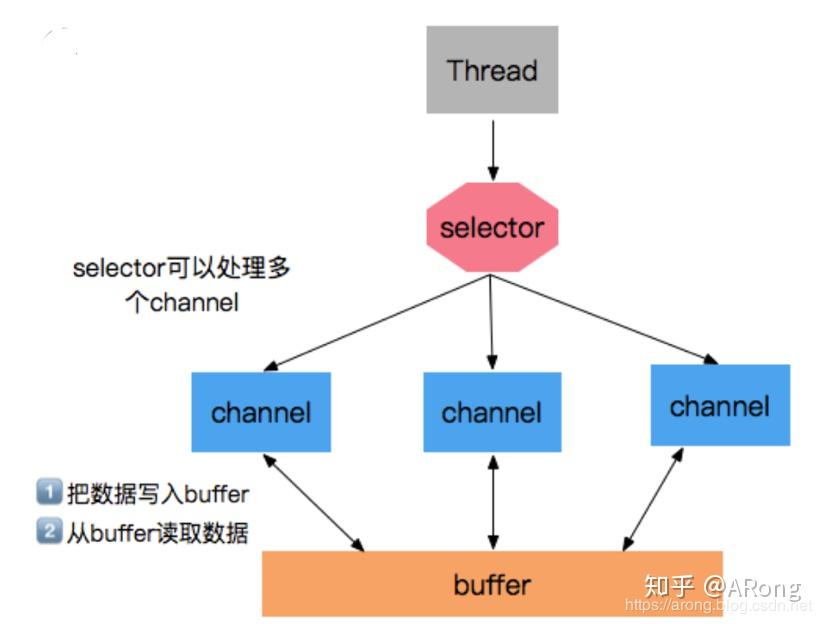
Compared with BIO, NIO has several core components, namely Selector, Channel and Buffer.
1.Buffer
The emergence of buffers leads to the difference between NIO and BIO: when reading data, you can first read part of it into the buffer, and then process other things; when writing data, you can first write part of it into the buffer, and then process other things. Read and write operations can no longer continue, so they will not block. Only when the buffer is full will it be put into actual reading/writing.
2.Channel
All IO operations of NIO start from Channel: - Reading data from channel: Create a buffer and then request the channel to read data. - Write data from the channel: Create a buffer, fill it with data, and ask the channel to write the data.
3.Selector
Selectors allow a single thread to process multiple channels for reuse.
AIO:
Asynchronous processing is mainly implemented based on events and callback mechanisms. After the IO operation has been completed, a notification is sent to the thread. Therefore, AIO will not block. At this time, our business logic will become a callback function, which will be automatically triggered by the system after the IO operation is completed.
Let’s talk about the basic data types of Java
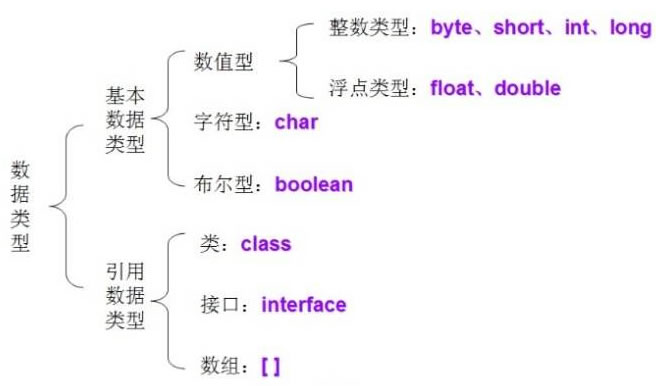
Basic data types include boolean (Boolean type), float (single precision floating point type), char (character type), byte (byte type), short (short integer type), int (integer type), long (long integer type) ) and double (double precision floating point type)
Reference data types are based on basic data types, including arrays, classes, and interfaces
Tell me what distributed components you know about
Eureka: the registration center of the service architecture, which is responsible for the registration and discovery of services;
Dubbo: manages service addresses, service registration and discovery, service monitoring, etc.
Nacos: Quickly implement dynamic service discovery, service configuration, service metadata and traffic management.
Nigix: High-Performance Web Container
MQ: distributed messaging middleware
Zookeeper: service registration center, load balancing, distributed coordination, master election
Let’s talk about list related classes and how to use them
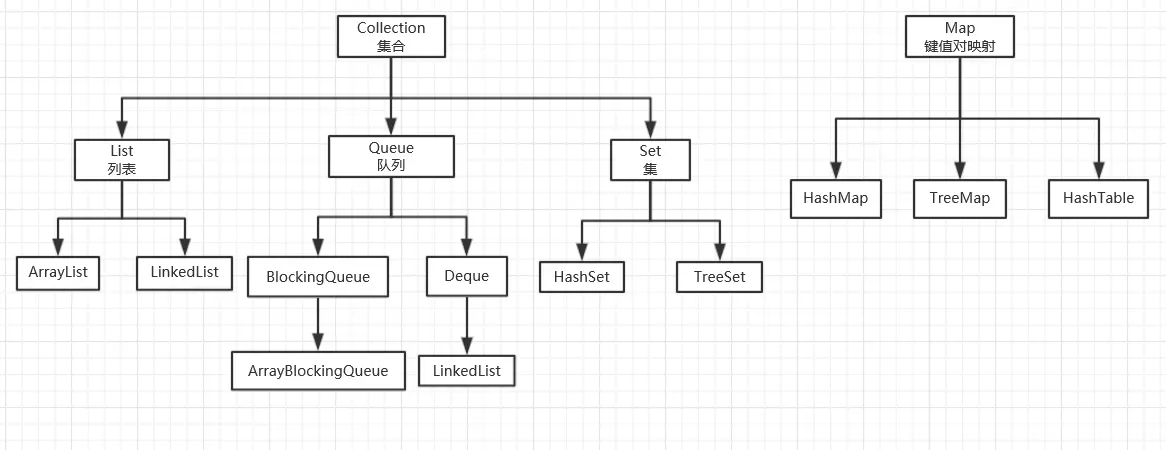
In Collection, the List collection is ordered, and developers can precisely control the insertion position of each element. They can access elements through indexes and traverse elements.
In the List collection, we commonly use the two classes ArrayList and LinkedList.
1.ArrayList
Among them, the bottom layer of ArrayList is implemented through an array, and its capacity is dynamically expanded as elements are added. The bottom layer of LinkedList is implemented through a linked list. As the elements increase, nodes are continuously added to the back end of the linked list.
ArrayList is the most commonly used class in the Java collection framework. It is an array queue and a thread-unsafe collection.
It inherits from AbstractList and implements the List, RandomAccess, Cloneable, and Serializable interfaces.
(1) ArrayList implements List and obtains the basic functions of the List collection framework;
(2) ArrayList implements RandomAccess and obtains the function of fast random access to storage elements. RandomAccess is a markup interface without any methods;
(3) ArrayList implements Cloneable and gets the clone() method, which can realize the cloning function;
(4) ArrayList implements Serializable, which means it can be serialized and transmitted through serialization. A typical application is the hessian protocol.
ArrayList thread unsafe reasons:
There will be two steps in the add process: 1. Determine whether the elementData array capacity meets the requirements. 2. Set the value at the corresponding position of elementData
Then there may be a situation where when the number of elements in the Arraylist is -1, both threads want to add an element. When judging whether to expand the capacity, they both determine that expansion is not needed, and then one of the threads writes the data. Number of elements++, when another element was written, it was found that the array was out of bounds
2. LinkedList
LinkedList is a doubly linked list, each node has a reference to the previous and next nodes. Compared with ArrayList, LinkedList's random access efficiency is lower.
It inherits AbstractSequentialList and implements the List, Deque, Cloneable, and Serializable interfaces.
(1) LinkedList implements List and obtains the basic functions of the List collection framework;
(2) LinkedList implements Deque. Deque is a two-way queue, that is, it can be either first-in-first-out or first-in-last-out. To put it simply, elements can be added to the head or to the tail;
(3) LinkedList implements Cloneable and gets the clone() method, which can realize the cloning function;
(4) LinkedList implements Serializable, which means it can be serialized and transmitted through serialization. A typical application is the hessian protocol.
Is hashmap thread-safe? How to make him safe?
He said it was thread-unsafe for the following reasons:
First, introduce his expansion process: HashMap expansion is mainly divided into two steps:
1.Expansion
Create a new empty Entry array whose length is twice the original array.
2.ReHash
Traverse the original Entry array and re-Hash all Entries into the new array. Why re-Hash? Because after the length is expanded, the rules of Hash also change.
Let’s review the Hash formula:
index = HashCode(Key) & (Length - 1)
When the original array length is 8, the Hash operation is an AND operation with 111B; when the new array length is 16, the Hash operation is an AND operation with 1111B. The Hash results are obviously different.
Circular dependencies may occur during expansion in a multi-threaded environment.
Ways to make it safe:
1. Replace with Hashtable. Hashtable achieves thread safety by locking the entire table, so the efficiency is relatively low.
2. Use the synchronizedMap method of the Collections class to wrap it. Methods as below:
public static <K,V> Map<K,V> synchronizedMap(Map<K,V> m) Returns a synchronized (thread-safe) map backed by the specified map
3. Use ConcurrentHashMap, which uses segmentation locks to ensure thread safety
Author: Xiao Yi
Link: Zhongan Java Side_Niuke.com
Source: Niuke.com