Article directory
Learning resources come from: Throwing Object Line
The difference between login and authorization
Login: Identity authentication, which is the process of confirming "you are you".
Authorization: Confirmation of certain permissions (such as obtaining user information) by identity or token held. The essential purpose of the login
process is also to confirm permissions.
Therefore, in actual applications, the boundaries between "login" and "authorization" are blurred in most scenarios.
Two ways to confirm authorization (or login) in HTTP
- via cookies
- Through Authorization Header
Cookie
Origin: The demand for the "Shopping" function was created by the Netscape browser development team.
Working Mechanism:
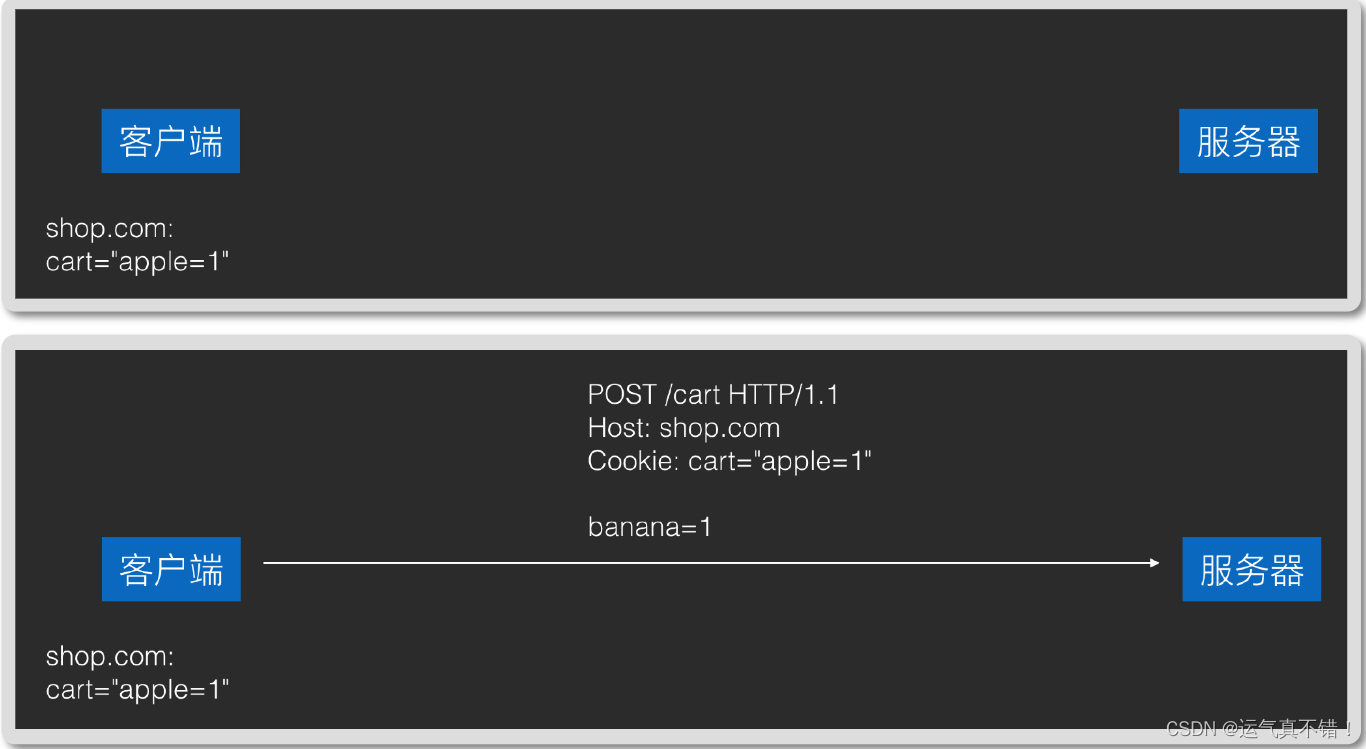
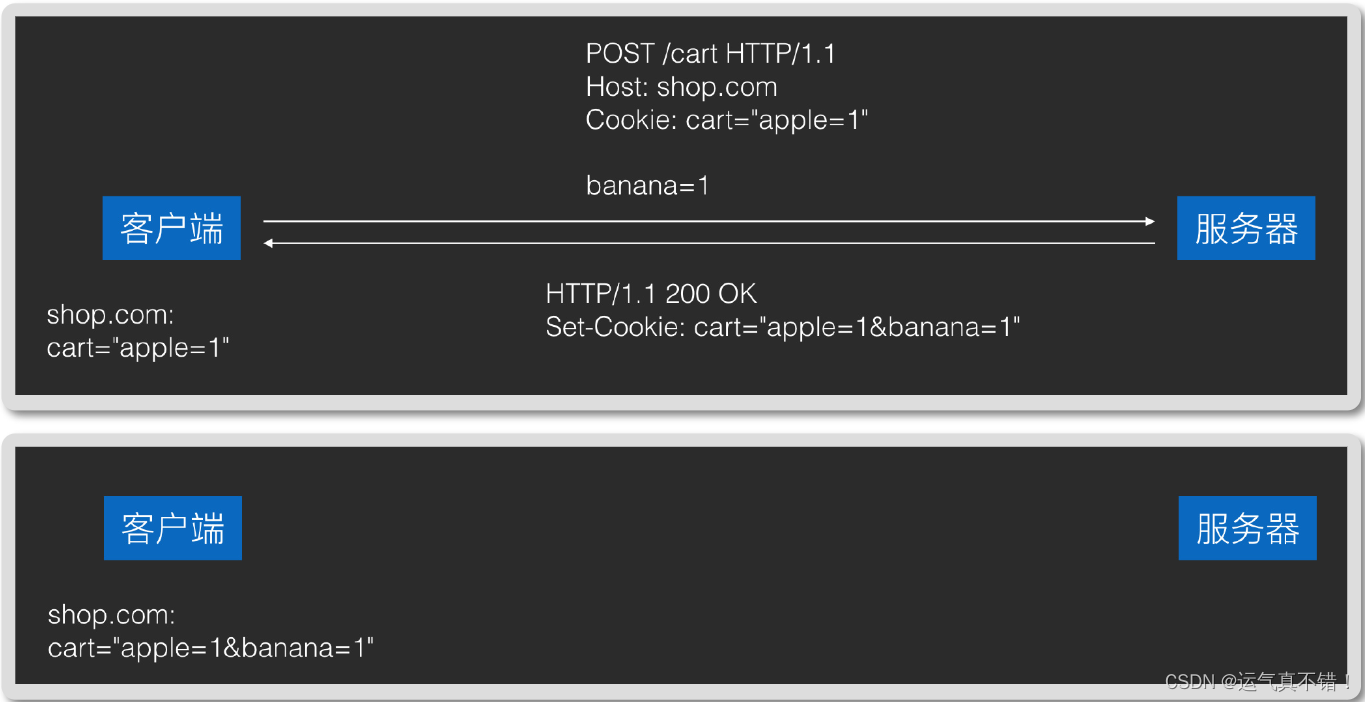
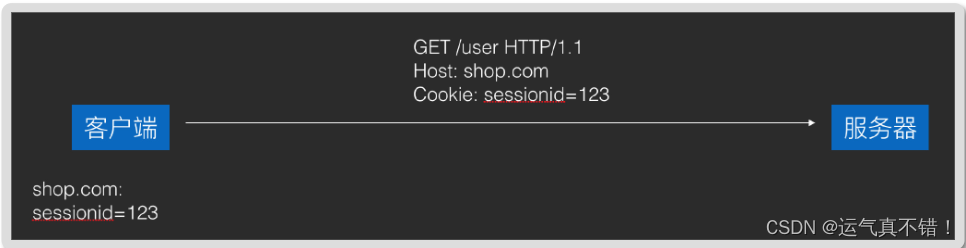
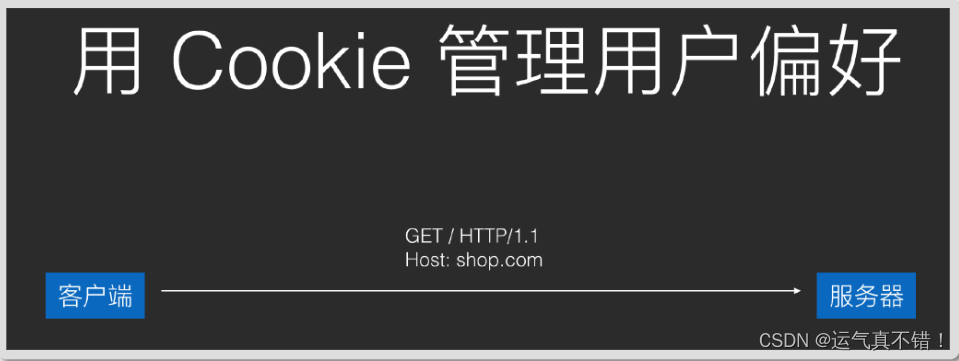
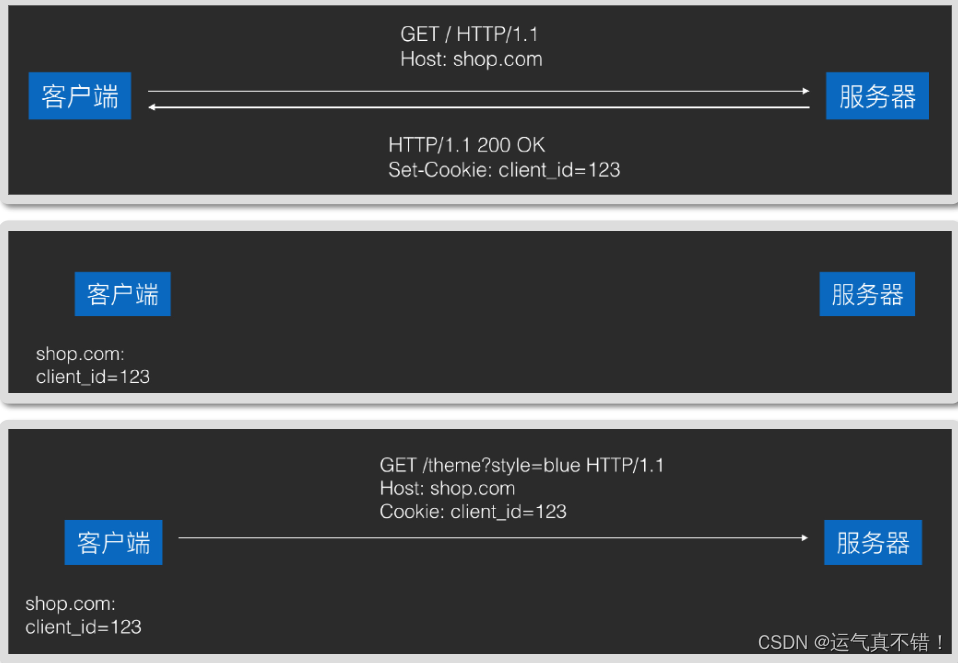
- The server needs the content saved by the client and returns it in Set-Cookie headers, and the client will save it automatically.
- Cookies saved by the client will be carried in the Cookie header and sent back to the server in all subsequent requests.

3. The cookies saved by the client are classified according to the server domain name. For example, after the cookies sent back by shop.com are saved, they will not be carried in subsequent requests to games.com.
4. Cookies saved by the client will be deleted after timeout. Cookies without set timeout (called Session Cookie) will be automatically deleted after the browser is closed. In addition, the server can also actively delete client Cookies that have not expired. .
-
What cookies do
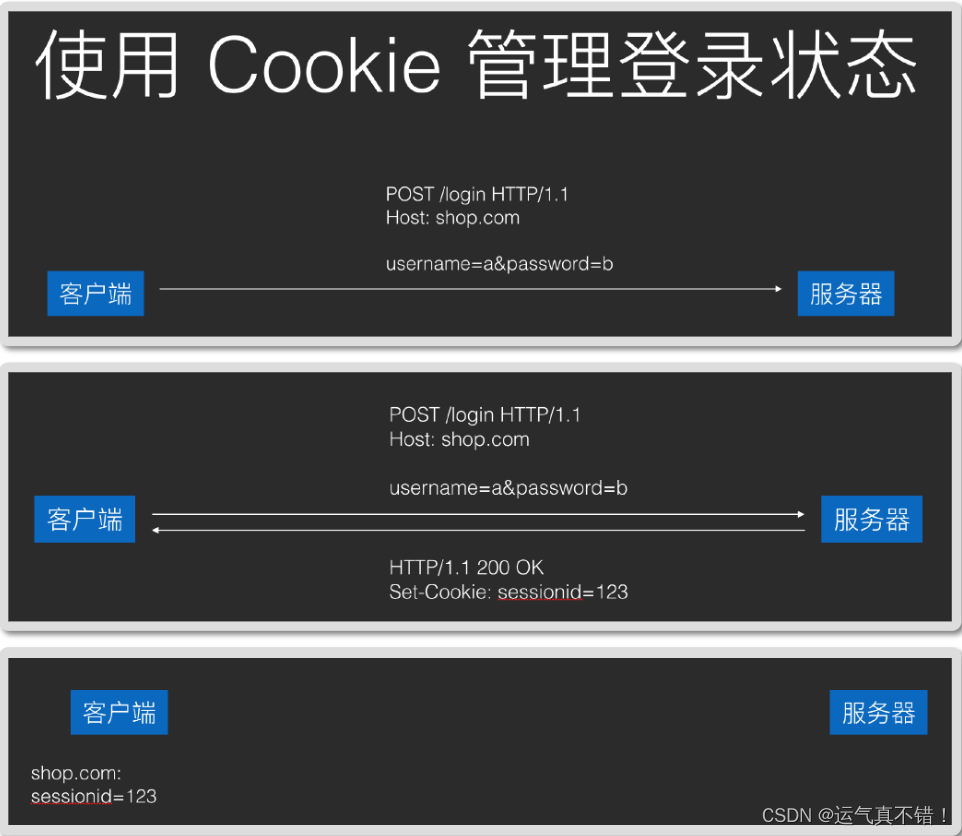
- Session management: login status, shopping cart
- Personalization: user preferences, themes
- Tracking: Analyzing user behavior

- Session management: login status, shopping cart
-
XSS (Cross-site scripting) (just understand it): Cross-site scripting attack. That is, after using JavaScript to get the browser's cookie, send it to your own website to steal the user's cookie. Response method: When the server sends cookies, add HttpOnly to sensitive cookies.
- Solution: HttpOnly - This cookie can only be used for HTTP requests and cannot be called by JavaScript. It prevents local code from abusing cookies.
-
XSRF (Cross-site request forgery) (just understand it): Cross-site request forgery. That is, accessing websites that have saved cookies without the user's knowledge, in order to operate the user's account beyond their authority (such as stealing user funds). The response method is mainly from the perspective of server security, so I won’t go into details.
- Response method: Referer verification
Authorization
Mainstream usage: Basic
Format:
Authorization: Basic <username:password(Base64ed)>
Mainstream usage: Bearer:
Format:
Authorization: Bearer <bearer token>
- How to obtain bearer token: through the OAuth2 authorization process
OAuth2 process:
-
The third-party website applies for third-party authorization cooperation from the authorized website and gets the client id and client secret.
-
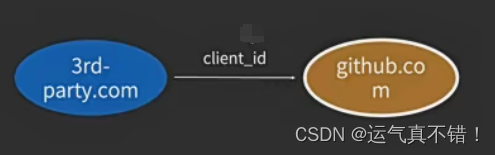
When the user clicks the "Authorize via XX (such as GitHub)" button when using a third-party website, the third-party
website will jump to the authorizing website and pass in the client id as his or her identity. -
The authorizing website displays the information of the third-party website and the user permissions required by the third-party website
to the user based on the client id, and asks the user whether he agrees to the authorization.
-
After the user clicks the "Agree Authorization" button, the authorizer's website will jump back to the third-party website and pass in the Authorization code as the user's approved certificate.
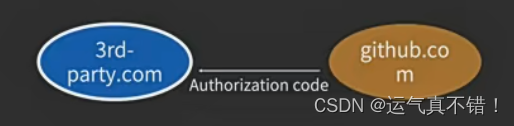
5. The third-party website sends the Authorization code back to its own server
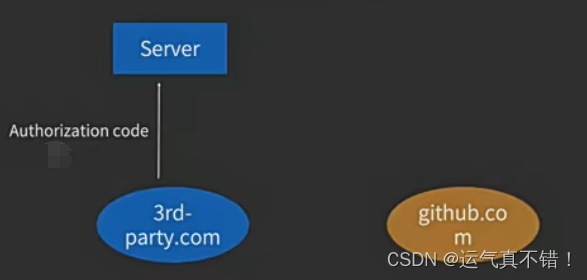
-
The server sends the Authorization code and its own client secret to the authorizer's server, and the authorizer's server returns the access token after passing the verification. The OAuth authorization process ends.

-
After the above process is completed, the server of the third-party website (or sometimes the client) can use the access token as the user authorization token and send a request to the authorizing website to obtain user information or operate the user account. But this is outside the OAuth process.

- Why does OAuth introduce an Authorization code, and requires the third party applying for authorization to send the Authorization code back to its own server, and then obtain the access token from the server, instead of returning the access token directly? What’s the point of such a complicated process? for safety. OAuth does not force the authorization process to use HTTPS, so it is necessary to ensure that security is still high enough when there are eavesdroppers in the communication path.
Third-party App login process through WeChat
The process of logging in to third-party apps through WeChat is also an OAuth2 process.
-
Third-party App applies for third-party authorization cooperation from Tencent and gets client id and client secret.
-
When the user clicks "Log in via WeChat" when using a third-party App, the third-party App will use the WeChat SDK to jump to WeChat and pass in its own client id as its identity.
-
WeChat interacts with the server to obtain the information of the third-party App and restricts it to the interface, and then asks the user whether he agrees to authorize the App to log in using WeChat.
-
After the user clicks "Log in with WeChat", WeChat interacts with the server to submit the authorization information, and then jumps back to the third-party App, and passes in the Authorization code as the user-approved credential.
-
The third-party App calls the "WeChat login" API of its own server, passes in the Authorizationcode, and then waits for the server's response.
-
After receiving the login request, the server uses the received Authorization code to send a request to WeChat's third-party authorization interface, sending the Authorization code and its own client secret as parameters. After the verification is passed, WeChat returns the access token.
-
After receiving the access token, the server immediately sends a request to WeChat's user information interface with the access token. After WeChat passes the verification, it returns the user information.
-
After receiving the user information, the server creates an account for the user in its own database, fills in its own database with the user information obtained from the WeChat server, and associates the user's ID with the user's WeChat ID.
-
After the user is created, the server sends a response to the client's request and returns the newly created user information.
-
The client receives the server response and the user logs in successfully.
- Use Bearer token in your own App.
Some Apps will design login and authorization into a process similar to OAuth2 in the design of the API, but simplify the concept of Authorization code. That is: when the login interface request is successful, the access token will be returned, and then the client can use this access token as a bearer token to perform user operations in subsequent requests.
Refresh token
{
"token_type": "Bearer",
"access_token": "xxxxx",
"refresh_token": "xxxxx",
"expires_time": "xxxxx"
}
Usage: The access token has an expiration time. After it expires, call the refresh token interface and pass in refresh_token to obtain a new access token.
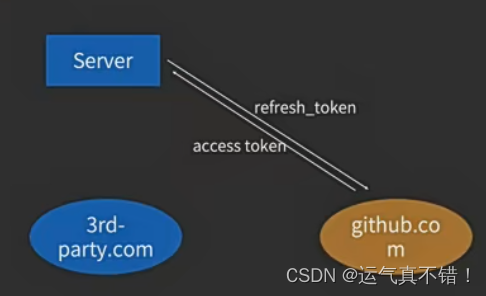
Purpose: Security. When the access token is stolen, because it has an expiration time, the bad guy only has a short time to "do bad things" ; at the same time, because (in the standard OAuth2 process) the refresh token always only exists in the server with the third-party service, so the refresh token There is almost no risk of token theft.
After-school questions
1. [Single-choice question] What are the two headers used for login authorization in HTTP?
A. Cookie and Authorization
B. Cookie and Authentication
C. Cache and Authorization
D. Cache and Authentication
Answer: A
Answer analysis: The two headers used for login authorization in HTTP are Cookie and Authorization. Among them, Cookie is used to save the user's identity information after logging in, while Authorization is used to carry the user's authorization information in each request to prove that the user has passed the authentication and has the corresponding permissions. So choose A
2. [Single-choice question] How does Cookie work?
A. The server uses Cookie header to return the information that it wants the client to save. The client uses Cookie Header to attach the content in the next request, and then deletes the cookie.
B. The server uses Set-Cookie header to return the information that it wants the client to save. The client Use Cookie Header to attach the content in the next request, and then delete the Cookie
C. The server uses the Cookie header to return the information that it wants the client to save, and the client uses the Cookie Header to attach the content in each subsequent request.
D. The server uses Set-Cookie header returns the information that the client wants to save. The client uses Cookie Header to attach the content to each subsequent request.
Answer: D
Answer analysis: Cookie is a way for the server to store data on the client. When the client sends a request to the server, the server will include the Set-Cookie header in the response header and return it to the client to instruct the client to save specific information. The client will append the saved cookie data to subsequent request headers for use by the server. The server can use the Cookie header to obtain data saved by the client to achieve a personalized user experience. So choose D
3. [Multiple choice question] What is the role of cookies?
A. Session management: login status, shopping cart
B. Personalization: user preferences, themes
C. User tracking: analyzing user behavior, targeted advertising
Answer: ABC
answer analysis:
4. [Single-choice question] When using Basic Authorization for authorization, what is the format?
A. Authorization: Basic username:password
B. Authorization: Basic username:password(Base64ed)
C. Authorization: Basic username:password(MD5ed)
Answer: BAnswer
analysis:
5. [Single-choice question] In the OAuth process, what is the role of Authorization code?
A. Ensure that users will not tamper with authorization information
B. Ensure that malicious listeners will not obtain the truly available authorization information
C. Ensure that third-party service parties that obtain authorization will not abuse their own authorization information
D. Ensure that authorization information can arrive correctly Apply for authorized third-party service provider
Answer: B
Answer analysis: In the OAuth authorization process, the Authorization code is a temporary authorization code issued by the authorization server to the client. Its function is to ensure that the authorization code will not be tampered with, thereby preventing malicious listeners from obtaining the truly available authorization information. . Therefore, the answer is B.
6. [Single-choice question] What is the function of refresh token?
A. Allow users to log in every once in a while, and use a tactful way to ensure that users are online for as long as possible.
B. Mandatory frequent replacement of access tokens will prevent access tokens that have not been used for a long time on the server and improve the stability of the system
. C. When the access token is stolen, it can be ensured that the thief can only use the token for a period of time without being discovered, and after discovering that the token has been stolen, it can be replaced with a new token immediately without the need for the user to reauthorize.
Answer: C
Answer analysis: Refresh token is a credential used to obtain a new access token before the access token expires. In the OAuth 2.0 authorization mechanism, Refresh token can be used to extend the validity period of the access token, or to regenerate a new access token if the access token is lost or stolen to protect the security of the application. So choose C