Commonly used encryption algorithm types:
Encryption algorithm: symmetric encryption (reversible)
Commonly used algorithms
DES(Data Encryption Standard): Data encryption standard, fast, suitable for occasions when encrypting large amounts of data; (no longer safe,)3DES(Triple DES): Based on DES, a piece of data is encrypted three times with three different keys, which is stronger;AES(Advanced Encryption Standard): Advanced Encryption Standard is the next generation encryption algorithm standard with fast speed and high security level. It supports 128, 192, 256, 512 (preferred algorithm)
Features
- It means that the same secret key is used for encryption and decryption.
- Encryption speed is fast
- The secret key transmission process is not secure
Encryption algorithm: Asymmetric encryption (reversible)
The asymmetric encryption algorithm requires two keys for encryption and decryption. These two keys are the public key (public key for short) and the private key (private key for short).
Commonly used algorithms
RSA: It is an asymmetric key encryption technology that is currently widely used and has a long history. Because it is difficult to crack, RSA is currently the most widely used digital encryption and signature technology. For example, domestic Alipay uses the RSA algorithm for signature verification. . Its security depends on the length of the secret key. Currently, the mainstream optional key lengths are 1024 bits, 2048 bits, 4096 bits, etc. Theoretically, the longer the secret key, the more difficult it is to crack. According to Wikipedia, it is less than or equal to 256 bits. The secret key can be cracked in a few hours on a personal computer. The 512-bit secret key and the 768-bit secret key were also successfully cracked in 1999 and 2009 respectively, although there is currently no public information confirming that anyone has. A 1024-bit key can be successfully cracked, but it is obviously not far away from this node. Therefore, the industry currently recommends using a 2048-bit or above secret key, but currently it seems that a 2048-bit key is safe enough. According to Alipay’s official documentation The recommendation is also 2048 bits. Of course, longer keys are more secure, but they also mean greater performance overhead.
Features
- The public key is public and the private key is kept by yourself.
- The algorithm is complex and less efficient than symmetric encryption, but it is less likely to be cracked. It is usually used in combination with domain symmetric encryption.
- Public key encryption —> Private key decryption. Mainly used for message transmission
- Private key encryption —> Public key decryption. Mainly used for digital signatures and CA certificates. Certificate - The purpose is to prevent tampering during the delivery process of the public key.
Encryption algorithm: single hash function (Hash) (irreversible)
One-way hash function, also known as one-way Hash function and hash function, is a function that changes an input message string of any length into a fixed-length output string and makes it difficult to obtain the input string from the output string. This output string is called the hash value of the message. Generally used to generate message digests, key encryption, etc.
Commonly used algorithms
MD5The andSHA-1algorithms have been broken and should not be used for new purposes; SHA-2 and SHA-3 are still safe and can be used.SHA-2Inclusive: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256.SHA-3包括:SHA3-224、SHA3-256、SHA3-384、SHA3-512。
Mainly used
- File production summary, unique value.
- The password protection of the server does not directly store the plain text in the database, but stores the hashed value in the database.
- Prevent data from being tampered with. After generating a hash value for the transmitted data, the hash value is signed. The receiving end then verifies the signature.
- Cloud disk transfer in seconds. As long as the hash value of the uploaded file exists on the server, there is no upload step.
Features
- Fast calculation, suitable for calculating hash values of large files
- Irreversible, previous content cannot be deduced reversely through hash value
- No matter how big the encrypted object is, the resulting encryption size is consistent
digital signature
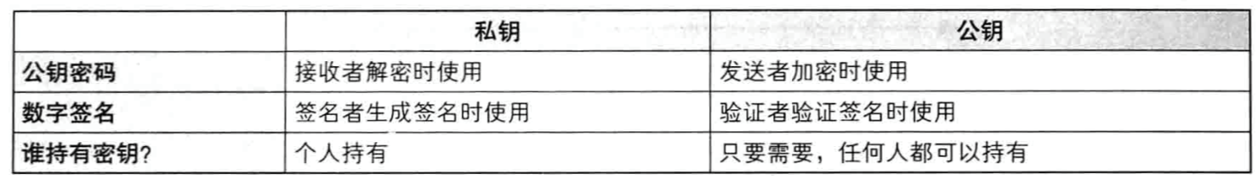
The sender of the message encrypts the message he sends to prove that he sent the message.
The main process is:
Role:
- News RecipientBob
- Message senderAlice
- Message senderAlice sends its public key to message recipientBob(unsafe, easy to be intercepted)
- The message sender Alice uses the hash function on the message to be sent--> generates a digest--> and then uses her ownprivate key Perform asymmetric encryption (signature) --> Generate an encrypted text and the original message (plain text) and send them together (signature + message)
- The message recipient Bob uses Alice's public key to decrypt the signature to obtain a hash value, and then compares it with the hash value generated by the message itself to determine whether the message is complete and whether it is the message sent by the sender himself. (decryption + comparison)
The main insecurity of is that the public key saved by the recipient cannot prove that it is the sender's own public key. If there is a man-in-the-middle attack, the public key saved by the recipient may be the middleman's public key. Therefore, the concept of certificate was introduced
which cannot prove the owner of the public key.
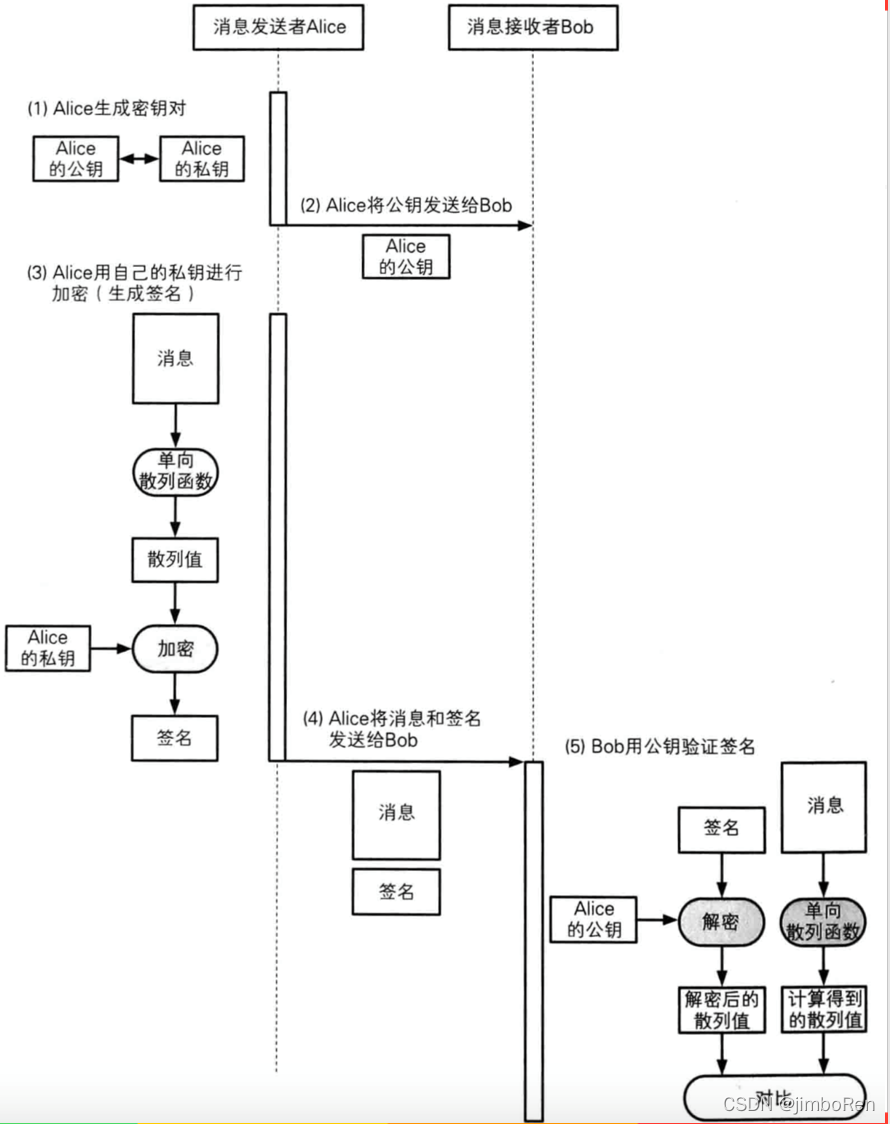
Man-in-the-middle attack examples:
The middleman is in the middle, decrypts the double-sent messages, encrypts them again and forwards them.
Both parties thought they were chatting with each other, while the others were chatting directly with the intermediary.
CA certificate
CA certificate is also known as public key certificate. An authority certifies who owns the public key. (Including email name and public key, etc.)
CA is the issuing authority of the certificate and is the core of the Public Key Infrastructure (PKI). CA is the authority responsible for issuing certificates, authenticating certificates, and managing issued certificates.
The CA holds a certificate (containing public and private keys). Public users on the Internet trust the CA by verifying the CA's signature. Anyone can obtain the CA's certificate (including the public key) to verify the certificate issued by it.
If the user wants to get a certificate of his own, he should first apply to the CA. After the CA determines the identity of the applicant, it assigns him a public key, and the CA binds the public key to the applicant's identity information and signs it, then forms a certificate and issues it to the applicant.
If a user wants to verify the authenticity of another certificate, he uses the CA's public key to verify the signature on that certificate. Once the verification is passed, the certificate is considered valid. The certificate is actually an authentication of the user's public key issued by a certificate issuing authority (CA)
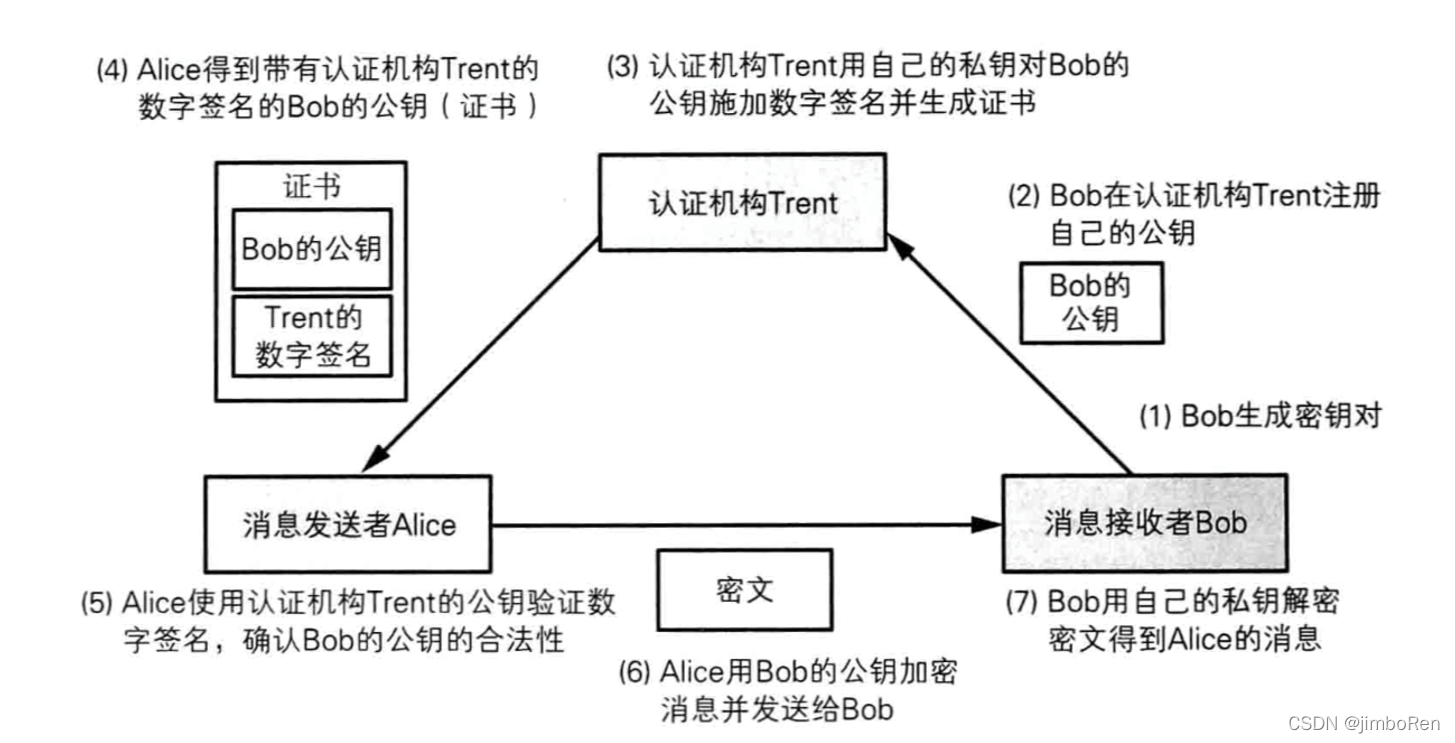
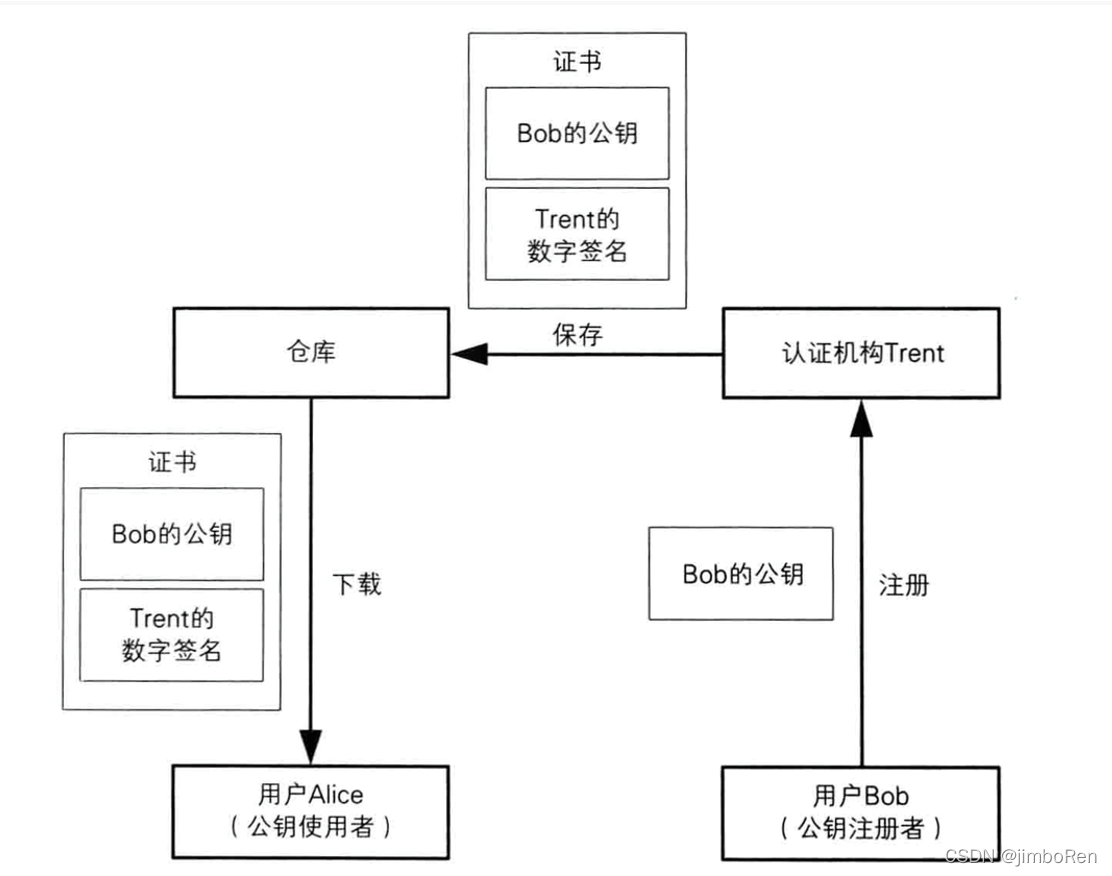
The process of sending a message with a CA certificate:
- Message recipientBob generates a secret key pair, and then sends his ownpublic keySend to CA organization
- The CA organization conducts verification through a series of means. After confirmation, use the CA's private key to digitally sign Bob's public key and his personal information (that is, the certificate), and then place it in the warehouse for users to download.
- Alice downloads Bob's certificate from the CA organization, and then uses the CA's public key to decrypt and verify it. After successful verification, Bob’s public key is obtained
- The message sender Alice uses the hash function on the message to be sent--> generates a digest--> and then uses Bob'spublic keyPerform asymmetric encryption--> Generate an encrypted text and send it together with the original message (plain text)
- The message recipient Bob uses his private key to decrypt the ciphertext to obtain the hash value, and then compares it with the hash value generated by the message itself to determine whether the message is complete and whether it is the message sent by the sender himself.
Question:
In digital signature: Step 2 is signed with your own private key.
In the CA certificate: Step 4 is encrypted with Bob's public key.
Reference:
Baidu Encyclopedia
MJ's resources