The blogger sorted out some basic network security-related questions during the summer vacation for the purpose of interviewing for insurance research, and I will share them with you here. The reference textbook "Network Security Fundamentals - Application and Standards (6th Edition)" is not a major in information security, so we have relatively little knowledge of this course. It may not be appropriate for students majoring in security to refer to this blog.
In the process of sorting out, some other materials on the Internet were also used for reference, most of which are no longer available for reference. If there is any infringement, we will notify you to delete it.
Article directory
Chapter 1 Introduction
1. Basic concepts
Computer security: a collection of tools used to protect data security and prevent hackers; network security: a general term for methods or measures to protect data transmission. The two are not clearly defined.
Definition of computer security: Protection measures for an automated information system, the purpose of which is to achieve the integrity, availability and confidentiality of information system resources.
2. CIA triad : It is the three goals included in the definition of computer security
(1) Confidentiality Confidentiality
Data confidentiality: To ensure that private or confidential information will not be disclosed to unauthorized individuals.
Privacy: Guarantee that individuals can control and influence information related to them, which may be exploited by others.
(2) Integrity Integrity
Data integrity, data has not been tampered with or damaged without authorization
System integrity, the system has not been manipulated without authorization, and operates according to established functions
(3) Availability Availability
ensures that information and information systems provide services for authorized persons at any time , instead of a situation where the unauthorized party abuses but denies the service to the authorized party.
(4) Authenticity
(5) Measurability
3. FIPS199 defines the impact of security violations on individuals or organizations into three levels :
①Low level: limited negative impact on the operation of the organization, assets or individuals
②Medium level: ...serious negative impact.
③Advanced: ...huge or catastrophic negative impact
4. OSI Security Architecture
(1) What is OSI Security Architecture? It provides a systematic approach to defining security and characterizing security measures.
(2) It mainly focuses on security attacks, mechanisms and services.
Security attack: Any behavior that may compromise the information security of the organization.
Security Mechanisms: Mechanisms to detect, prevent, and recover from security attacks
Security Services: Services used to enhance the security of an organization's data processing systems and information transfers
5. Security attack : divided into active attack and passive attack
(1) Passive attack: trying to learn or use information from the system, but does not affect the resources of the system
① message content disclosure: the data transmitted in the network contains sensitive secrets information, it is possible for the adversary to obtain this useful information.
②Traffic analysis attack: If a method is adopted to shield the content of messages or other streams, although the adversary cannot extract useful information from them, the pattern of the messages can still be observed.
(2) Active attack: attempt to change system resources or affect system operations
① Impersonation: Masquerading occurs when an entity pretends to be a different entity.
② Replay: Passively capture data units and retransmit them in the original order. (After a period of time, do it again)
③Rewrite message: change part of the legal message, or delay reordering the message.
④ Denial of service: prevent or prohibit the normal use or management of communication equipment.
6. Security service : It is a service provided by the protocol layer of the communication open system and can ensure that the system or data transmission is sufficiently secure. Its purpose is to counter security attacks.
Authentication: Authentication is to provide identification services for entities and data sources in the communication process
Access control: Access control is to protect protected resources from unauthorized use
Confidentiality: Data confidentiality is to protect data from unauthorized disclosure
Integrity: Data Integrity refers to ensuring that the data received by the receiver is the data sent by the sender.
Non-repudiation: Non-repudiation refers to preventing any entity in the communication from denying an operation or behavior it performed in the past.
Availability
7. Security mechanism
Encryption: Encryption technology can provide confidentiality for both data and communication service flow information, and it can also become a part of other security mechanisms to play a supplementary role. Digital signature mechanism: digital access control mechanism of
signature
technology : Access control is to protect protected resources from unauthorized use. Data integrity mechanism
: Data integrity means to ensure that the data received by the receiver is the data sent by the sender.
The authentication function is realized through some shared information between the authenticator and the authenticated.
Traffic filling mechanism: business flow filling is to cover up the characteristics of normal communication traffic by sending additional data, so as to achieve the purpose of protecting the confidentiality of business flow.
Routing control: Routing control is to achieve the purpose of security protection by controlling the routing process.
Fair mechanism: The fair mechanism is to use a trusted third party to realize the security function.
The relationship between security services and security mechanisms? A security service can be provided by one or more security mechanisms, and a security mechanism can be used to provide one or more security services.
8. Network security model Book P18
model requirements
Design a reasonable algorithm for security transformation
Generate secret information (key) used by the algorithm
Develop a distribution method for secret information
Specify a protocol to use this security algorithm and secret information
9. Supplement
· Intruder: refers to the person who breaks into or even destroys the integrity of the remote machine system with bad intentions
· Hacker: refers to the person who has a strong interest in the mysteries of any computer operating system.
·Computer security: protection measures for an automated information system, the purpose of which is to achieve the integrity, availability and confidentiality of information system resources ·Network security: the general term for
methods or measures to protect data transmission
·Information security: refers to information systems that are Protection against accidental or malicious reasons from being destroyed, changed, or leaked, the system operates continuously and reliably, information services are not interrupted, and business continuity is finally achieved.
Chapter 2 Symmetric Encryption and Message Confidentiality
1. A symmetric encryption scheme consists of 5 parts Book P23
2. What are the requirements for the safe use of symmetric encryption
① A strong encryption algorithm is required. (Knowing the algorithm + ciphertext, or ciphertext + plaintext, the plaintext and key cannot be obtained)
②The sender and receiver must obtain the key in a secure way and ensure the security of the key.
Supplement: The security of symmetric encryption depends on the secrecy of the key, not the secrecy of the algorithm.
3. Three classification methods of cryptographic systems
① Type of operation for converting plaintext into ciphertext: replacement, permutation and combination
② Number of keys used: symmetric encryption and public key encryption
③ Plaintext processing method: stream cipher and block cipher
Stream cipher: Continuously processes input elements during execution, producing output elements one at a time.
Block cipher: Processes one block of input elements at a time and produces one output block corresponding to that input block
4. Cryptanalysis : The process of trying to find out the plaintext or key is called cryptanalysis. Cryptanalysis type see book P24. Methods of Cryptanalysis: Exhaustion; Weaknesses of Algorithms.
5. How do you know if an encryption scheme is computationally secure?
• The cost of deciphering exceeds the value of the encrypted information
• The time to decipher exceeds the useful lifetime of the information
6. Feistel cipher structure See P25 and Figure 26 in the book for details
. Input: 2w-bit plaintext block, key k
Output: 2w-bit ciphertext block.
The plaintext block is divided into: L0, R0. After n(16) cycle processing, they are combined to generate ciphertext grouping.
Each i cycle takes Li-1 and Ri-1 generated in the previous cycle and the subkey Ki generated by K as input. In general, the subkey Ki, distinct from K and from each other, is generated from the key using a subkey generation algorithm
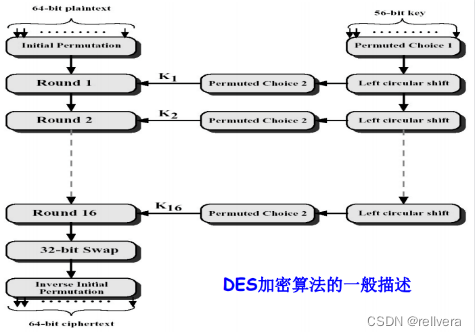
7.DES
①Block encryption algorithm: plaintext and ciphertext are 64-bit block length
②Symmetric algorithm: Encryption and decryption use the same algorithm except for the key arrangement ③Key
length: 56 bits
Each combination is replaced first and then replaced, a total of 16 rounds
8.3DES detailed algorithm see book P29
①Use 3 keys, execute DES algorithm three times
②Key length: 168 bits So how many bits are the plaintext and ciphertext length? 64-bit
③ Weaknesses of 3DES: DES and 3DES are too slow to run, initially implemented by hardware, without efficient software code. They use a 64-bit packet size, and for efficiency and security, larger packets are required
9. AES P30
① The group size is 128 bits, and the key length can be 128/192/256 bits.
② AES is not a feistel structure. ③
Encryption and decryption are similar but asymmetric.
10. Random numbers and pseudo-random numbers
(1) Requirements for random numbers generated: randomness, unpredictability
Randomness: the data should be evenly distributed, and independent
unpredictability: each number will be statistically independent of other numbers, So this number is unpredictable
(2) Pseudo-random number: a number generated by a deterministic algorithm and passed the randomness test
(3) True random generator, pseudo-random generator and pseudo-random function
True random number generator: Generate An effective random source is used as an input, this source is called an entropy source
Pseudo-random number generator: used to generate a bit stream, which can be used for stream ciphers.
Pseudo-random function PRF: Generate some fixed-length pseudo-random bit strings, which can be used for encrypted keys and random numbers.
11. Electronic codebook mode ECB of block cipher working mode
In this mode, the plaintext is processed b bits at a time, and each block of the plaintext is encrypted with the same key. For a given key, each b-bit block of plaintext corresponds to a unique ciphertext.
Features: ①Simple and effective; ②Can be implemented in parallel; ③The same plaintext generates the same ciphertext, and the same information appears repeatedly to cause leakage; ④Active attack on plaintext is possible, and information blocks can be replaced, rearranged, deleted, and replayed ; ⑤ suitable for transmitting short messages
12. Supplement
Cryptography: It is the science that studies the security and confidentiality of information systems.
Cryptography: It mainly studies the encoding of information to realize the concealment of information.
Cryptanalysis: It mainly studies the deciphering of encrypted messages or the forgery of messages.
Chapter 3 Public Key Cryptography and Message Authentication
1. Message authentication using conventional encryption requires mastering book P48
2. Message authentication using unconventional encryption Book P48-50
①Message authentication code MAC
②One-way hash function
③Secret value
discussion: The difference between MAC function and encryption function is in where?
– The encryption function must be reversible; the MAC function can be a one-way function.
• MAC can provide digital signature?
– No, because the sending and receiving parties share the secret key.
• Can authentication of message authenticity be performed without a shared secret?
– Using hash functions
Message authentication provides a process for verifying that a received message came from a trusted source and has not been tampered with.
There are methods of message authentication code and one-way hash function
Message authentication code MAC: use a key to generate a small data block of fixed size, and add it to the message, called message authentication code MAC. (At the same time authenticate the source of the message and the data)
What is the difference between the MAC function and the encryption function?
– The encryption function must be reversible; the MAC function can be a one-way function.
• MAC can provide digital signature?
– No, because the sending and receiving parties share the secret key.
• Can the authenticity of messages be authenticated without a shared secret key?
– using a hash function
One-way hash function : the input is a message M of any length, and the output is a fixed-length message digest H(M)
Advantages of using a one-way hash function without using an encryption algorithm :
• Encryption software is slow
• Encryption hardware is expensive
• Encryption hardware is advantageous for large-length data
• Encryption algorithms may be protected by patents
• Encryption algorithms may be subject to export restrictions .
Requirements for a secure hash function
hash
• H can be used for data blocks of arbitrary length
• H can produce a fixed output
• Computing H(x) for any given x is relatively easy and can be implemented in hardware and software
• For any given value h, it is computationally infeasible to find x that satisfies H(x)=h, that is, unidirectional •
For any given data block x, it is computationally infeasible to find x that satisfies H(y)=H(x) y≠x is computationally infeasible, i.e. weak-collision-resistant
• It is computationally infeasible to find any pair (x,y) satisfying H(x)=H(y), i.e. strong-collision-resistant sex
Security of Hash Functions
P52 Table
SHA-512 algorithm logic
• Input: message with a maximum length of 2128 bits;
• Output: 512-bit message digest;
• Processing: input is processed in units of 1024-bit data blocks;
Step 1: Add padding bits
Step 2: Add length.
Step 3: Initialize the hash buffer
Step 4: Process the 1024-bit data block message
Step 5: Output
Introduction to HMAC
HMAC is a message authentication code (MAC) based on a hash function considering: MAC
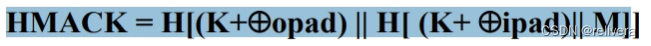

Public key cryptography
Public key encryption system components: plaintext, ciphertext; public key, private key, encryption, decryption algorithm
public key cryptography system application :
encryption and decryption digital signature: the sender uses his private key to "sign" the message key exchange :
Conditions that must be met by the public-key cryptographic algorithm to exchange session keys between the two parties
. It is computationally feasible to generate a key
pair. It is computationally feasible to encrypt plaintext
with the public key. It is computationally feasible to decrypt the ciphertext with the private key.
It is computationally infeasible to obtain the private key from the public key It is computationally infeasible
to obtain the plaintext from the public key and ciphertext There is
no restriction on the order of encryption and decryption (not required)
Implementation of RSA Algorithm

Diffie-Hellman key exchange
primitive root:

discrete logarithm


Chapter 4 Key Distribution and User Authentication
1. Key distribution based on symmetric encryption
(1) Basic method
Link layer encryption: add encryption devices at both ends of the communication link.
End-to-end encryption: takes place in the end system, with data encrypted by the source host or endpoint.
Session key: When two end systems (host or terminal, etc.) want to communicate, establish a logical connection and use a one-time session
key to encrypt all user data.
Permanent Key: A permanent key is used between two entities to distribute session keys. (Used to encrypt session keys)
(2) Four methods of key distribution: (The key distribution problem is the core problem of symmetric encryption)
The key is selected by A and handed over to B in person (physical delivery
) Third party C chooses and hands it over to A and B in person (physical delivery)
Encrypt the new key with the most recently used key and send it to the other party
A, B and C have secret channels
(3) Key Distribution Center (KDC)
KDC decides Which systems are allowed to communicate with other systems. When two systems establish a connection, the KDC
provides a one-time key for the connection. (See book P82 for the operation process)
2. Key distribution based on asymmetric encryption
A public key certificate consists of a public key, the ID of the owner of the public key, and a trusted third-party signature.
(1) Key distribution based on public key encryption is not safe. The solution: use public key infrastructure (Public Key
Infrastructure PKI), and by adding a trusted third-party CA (certificate authority, certification
center), it can be authorized by government agencies And financial institutions to take responsibility, to establish a high degree of trust among users.
(2) The use of public key certificates (the picture in book P97, I don’t quite understand it, often tested)
use public key certificates to distribute conventional encryption keys, and the communication process of Bob->Alice is as follows:
- prepare message
- Encrypt messages with a one-time session key (regular encryption)
- Encrypt the session key with Alice's public key (public key encryption)
- Add the encrypted session key to the message and send it to Alice.
3. X.509 certificate
(1) Meaning: X.509 is part of the x.500 standard series. X.509 defines a framework for providing authentication services to its users using the x.500 directory. This directory acts as a public key certificate repository. In addition, X.509 also defines an authentication protocol based on public key certificates.
Supplement: The core of the X.509 scheme is the public key certificate associated with each user. Certificates are created by a trusted certificate authority (CA) and placed in a directory by the CA or by the user. The directory server is not responsible for public key generation or certificate functions, it only provides an easily accessible location for users to obtain certificates.
(2) Certificate format: see book P97
(3) Certificate features: ① Any user who can access the CA public key can verify the signed user public key; ② Except the CA, no user can forge or tamper with the certificate content without being detected. (Cannot be forged)
(4) How to obtain certificates for users certified by different CAs: see book P99
(5) Certificate revocation
Each X.509 certificate contains a validity period, and certificates beyond the validity period will not be used.
But in some cases, it is necessary to invalidate the certificate that has not expired: ①The user applies for a new certificate before the old certificate expires ②The user's private key is leaked ③The user is no longer trusted by the CA ④The CA certificate is leaked Each CA needs to save
one Certificate Revocation List (CRL), used to store all revoked but not expired certificates.
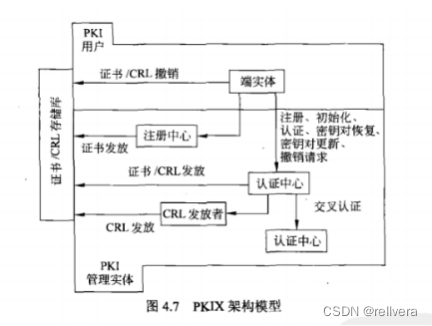
4. Public key infrastructure
(1) Definition: A set of hardware, software, personnel, policies and processes based on asymmetric cryptosystems used to generate, manage, store, distribute and revoke digital certificates. The main goal of developing a PKI is to enable safe, convenient and efficient access to public keys.
(2) Architecture model (see book for specific meaning: P102)
Chapter 6 Transport Layer Security
6.1 Web Security Requirements
Features of Web Security
n 1) Provide two-way services, weak attack defense capabilities
n 2) As a visual window and business interaction platform, it provides multiple services, which is related to reputation
n 3) The underlying software is huge, such as apache about 10M, which has always been a vulnerability 4) If compromised,
it may become a springboard to enter the enterprise
n 5) Casual and untrained users
Components of Web Security
Browser Security, Web Server Security, Browser and Web Server
Web Traffic Security Methods
§ Network layer: IPSec Transport layer: SSL/TLS Application layer: Kerberos, S/MIME
6.2 Transport layer security
SSL (Secure socket layer, Secure socket layer)/TLS (Transport layer security, Transport layer service)
TLS is developed from SSL, (the following series of explanations TLS and SSL refer to the same thing)
SSL connection and SSL session
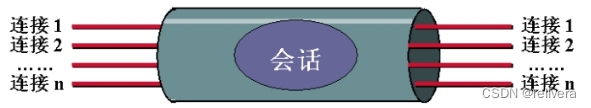
connection : A connection is a transmission carrier that can provide a certain service. For SSL, such a connection is a point-to-point relationship and is short-lived. Each connection is related to a session.
Session : An SSL session is an association between a client and a server. The characteristics are as follows:
1) The session is created by the handshake protocol
2) The session defines a set of cryptographic security parameters that can be shared by multiple connections
3) For each connection, the session can be used to avoid expensive new security parameters Negotiation
Between any pair of entities, there can be multiple secure connections
TLS Record Protocol
TLS Record Protocol provides services for TLS connections:
1) Confidentiality: The handshake protocol defines a traditional encrypted shared key that can be used for TLS payloads.
2) Message Integrity: The handshake protocol also defines a shared key for generating MAC
TLS record protocol operation process
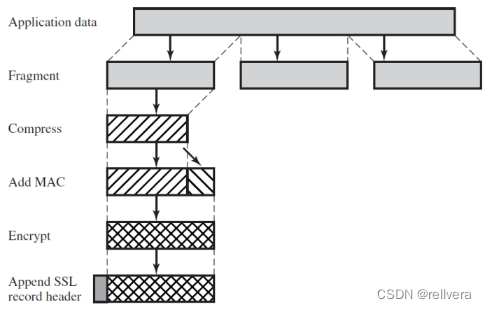
1. Segmentation, divide each upper-layer message into blocks not larger than 2^14 bytes
2. Compress or not compress. The compression must be lossless, and the length cannot exceed 1024 bytes. There is no compression in TLSv2
3. In Computes the message authentication code on the basis of the compressed data. TLS uses the HMAC algorithm, which puts the compressed message and the calculated MAC together. The fields for MAC calculation are as follows:

4. Use a symmetric encryption algorithm to encrypt the data obtained in 3. The block length increment caused by encryption will not exceed 1024 bytes, so the total block length will not exceed 2^14+2048 bytes Allowed to use: block cipher
: AES, 3DES stream cipher: RC4-128
5. Add a TLS header content type (8bit) consisting of the following fields
: a high-level protocol for processing encapsulation segments (defined as modifying cipher specifications, alarms, handshakes, and application data 4 Type)
major version number (8bit): Indicates the major version number of the applied TLS protocol. For TLSv3.0, the value is 3
minor version numbers (8 bits): indicates the minor version number of the applied TLS protocol. For TLSv3.0, the value is 0.
Compressed length (8bit): the length of the plaintext block (compressed plaintext block if compression is used) in bytes. The maximum value is 2^14+2048.
SSL modification cipher specification protocol
Consists of a single message, a single byte with a message value of 1; makes the pending state changed to the current state, updating the cipher mechanism to be used by this connection. The alarm protocol is used to
transmit
TLS related information to the other entity alarm information; during transmission, compress and encrypt according to the processing mechanism specified by the current state
Chapter 10 Malware
1. Definition of Malware : A program that secretly implants another program that attempts to destroy data, run destructive or intrusive programs, or destroy the confidentiality, integrity, and availability of victim data, applications, or operating systems.
2. Classification of malware
1: Whether it needs to reside in the host program or be independent of the host program, it can be divided into two categories: ① Program fragments that must rely on actual applications, tools or system programs to run, such as viruses, Logic bombs and backdoors; ② An independent program that can be scheduled and run by the operating system. Such as worms and zombies. Method 2: Whether it can replicate itself can be divided into two categories: ① It is a program or program fragment
that is activated by triggering .
Such as logic bombs, backdoors, and zombies; ②Including program segments (viruses) or independent programs (worms), these programs generate one or more copies of themselves when executed, and these copies will be released on this system or other systems at an appropriate time is activated within.
3. Virus
(1) Definition : A virus is a program that can infect other programs by modifying some programs.
(2) The four stages of the virus
Dormant stage, dormant until triggered
Transmission stage, replicating itself, infecting others
Trigger stage, activated by specific events
Execution stage, when the conditions are ripe, outbreak and destruction
(3) The structure of the virus
The virus can be Placed at the beginning, end, or otherwise embedded in the executable file. The key to virus execution is that when the infected program is called, it will first execute the virus code, and then execute the source code of the program.
(4) The logic and compression process of viruses : see book P257.
(5) Classification of viruses : (see book P258 for details)
① Viruses classified by target: boot sector virus, file infection virus, macro virus, hybrid virus
② Viruses classified by hiding strategy: encryption virus, stealth aircraft Type virus, polymorphic virus, metamorphic virus
(6) Macro virus and script virus
What is a macro? A macro is an executable program (script) embedded in a Word document or other types of files. The typical application is that users use macros to automatically complete some repetitive tasks without having to repeat keyboard input.
Reasons why macro viruses are highly dangerous: ① macro viruses are platform-independent (so many hardware platforms and operating systems are easily infected); ② the target of macro virus infection is documents; ③ macro viruses are easy to spread; ④ traditional files Access control systems can only do so much in stopping the spread of viruses.
4. Worm
(1) Definition : A network worm is a program that can replicate itself and send copies of the worm from one computer to other computers through a network connection. (Once entering the computer, the worm will be activated and start a new propagation, and perform some harmful functions.)
(2) Which network media does the worm use to replicate itself?
E-mail tool, file sharing, remote execution function, remote file access or transfer capability, remote login capability
(3) The worm propagation stage performs the following functions
: 1. Find new infected objects by checking the host list or similar remote system address list;
2. It copies itself to the remote system and begins executing the copy.
(4) Worm propagation mode : slow start stage, fast propagation stage, and slow end stage. (See book P262 for details)
5. Other malicious software
(1) Malicious mobile code : Malicious mobile code refers to software (scripts, macros or other mobile instructions) that can be embedded in various platforms unchanged and have the same semantics when executed.
(2) Client vulnerability and Trojan attack : When a user browses a webpage controlled by an attacker, the code contained in the webpage will attack the vulnerability of the browser, thereby downloading malicious software to the website without the user's knowledge and permission. system and install it.
(3) Trojan Horse (Trojan Horse) : It is a useful or apparently useful program or command process. It contains hidden code segments, and once invoked, it will perform some unwanted or harmful functions. The main purpose is to achieve some functions that unauthorized users cannot directly complete; another motive is to destroy data.
(4) Logic bomb : It is a code segment embedded in some legal programs, which will "explode" when certain conditions are met.
(5) Backdoor : Also called trapdoor (Trapdoor), it is the secret entry point of the program, and the insider can bypass the normal security access mechanism and directly access the program.
6. Protective measures (see book P272 for details)
Anti-virus methods: detection, identification, and removal
Development of anti-virus software: ①First generation: simple scanner ②Second generation: heuristic scanner
③Third generation: active trap④ The fourth generation: full-featured protection
Behavior blocking software, distributed worm detection: see book P273
Worm protection measures: ①Signature-based worm scanning and filtering
②Filter-based worm prevention
③Payload classification-based worm prevention
④Threshold random walk Scan detection
⑤ rate limit
⑥ rate interrupt
7. Distributed denial of service attack
(1) Denial of service (DoS) attack : Attempts to prevent legitimate users of a certain service from using the service.
DDoS attack: Attempts to consume the resources of the target device, making it unable to provide services.
DDoS attacks flood servers, networks, and even end-user systems in a network of unwanted traffic, making it impossible for legitimate users to gain access to those resources.
(2) Classify according to consumed network resources
①Internal resource attack: see P277 for an example
②Attack by consuming data transmission resources: see P277 for an example
(3) Classify according to attack means
①Direct DDoS
②Reflective DDoS
(4) DDoS attack role
① hacker and the host (attacker) operated by the hacker himself, its role is to send various commands to the master zombie, including attack instructions.
② A small number of master zombies (Master Zombie) will listen to instructions from hackers, and
issue attack commands to each daemon process terminal distributed on the network, so that they can actually start the attack.
③There are a large number of slave zombies (Slave Zombie), which will receive and respond to commands from the master control terminal, and are the real strikers.
④ Victim (Victim) The target host being attacked
(5) DDoS attack method and preventive measures
Attack method: the attacker uses zombie software to infect a large number of machines, requirements: software that can execute DDoS attacks; there are a large number of system vulnerabilities; there are loopholes in the location Machine policy, a method called scanning
DDoS prevention; attack prevention and preemption; attack detection and filtering; attack source backtracking and identification
Chapter 12 Firewalls
1. Definition : A firewall is an effective method to protect a local system or system network from network-based security threats, while
supporting access to the outside world through a wide area network and the Internet.
2. The design goal of the firewall (satisfying the conditions)
(1) All inbound and outbound network traffic must pass through the firewall.
(2) Only authorized network traffic is allowed to pass through the firewall.
(3) The firewall itself cannot be breached and must be built on a secure operating system.
3. The function of the firewall
(1) Define a necessary point to block unauthorized users from the protected network.
(2) Provide a place to monitor security-related events. (Audit, alarm)
(3) It can be used as a convenient platform for Internet functions not related to security, such as: address translation function, network management function.
(4) It can be used as an IPSec platform.
4. Limitations of the firewall
(1) Some attacks will bypass the firewall, and the firewall cannot do anything about it. For example: Dial-up Internet access by telephone can bypass the firewall
(2) The firewall cannot completely prevent internal threats.
(3) The firewall cannot prevent programs infected by viruses, such as files and emails.
5. Types of firewalls
Packet filtering firewalls, stateful inspection firewalls, application layer gateways, link layer gateways
6. Packet filtering firewall
(1) Basic idea : apply some rules to each received and sent IP packet, and then decide to forward or discard the packet.
(2) How to filter : The filtering rules are based on the fields (fields) in the IP and transport layer headers, including source and destination IP addresses, source and destination port numbers, IP protocol fields and interfaces.
(3) Default policy :
Default drop: traffic that is not explicitly allowed will be blocked (more conservative, gradually open as needed)
Default forwarding: traffic that is not explicitly blocked will be allowed (administrators must target each new attack, formulate new rules)
(4) Monitor on the network layer, usually implemented on the router .
Advantages: Simple implementation, transparent to users, and high efficiency;
Disadvantages: ①It is not easy to formulate rules correctly; ②The packet filtering firewall does not check the upper layer data, and cannot prevent attacks that exploit specific application vulnerabilities; ③The available information is limited, and the log function provided is also very Limited; ④ does not support advanced user authentication schemes; ⑤ vulnerable to TCP/IP protocol stack vulnerabilities, such as IP address spoofing; ⑥ limited protection against security threats caused by improper settings.
(5) Attacks and countermeasures against packet filtering firewalls
IP address spoofing, for example, spoofing internal IP addresses (countermeasures: ban internal addresses on external interfaces)
Source routing attacks, that is, routing by source (countermeasures: discard all used Packets with this option)
Small frame attack, using the IP fragmentation function to split the TCP header into different fragments (countermeasure: discard fragments that are too small)
7. Stateful inspection firewall
Information checked on the Internet: Stateful inspection is a more effective security control method than packet filtering. For a newly created application connection, state detection checks the preset security rules, allows the connection that meets the rules to pass, and records the relevant information of the connection in the memory to generate a state table. Subsequent data packets for this connection can pass as long as they conform to the state table. The advantage of this method is that it is not necessary to check the rules for each data packet, but the subsequent data packets of a connection (usually a large number of data packets) are directly checked by the hash algorithm, so that the performance is improved. It is greatly improved; moreover, since the state table is dynamic, ports above No. 1024 can be opened selectively and dynamically, so that the security is further improved. (????)
8. Application layer gateway
(1) Advantages and disadvantages
Advantages: The proxy server works at the application layer, which is more secure than packet filtering technology. It has more understanding of application layer data and can use specific data for each specific network application service Security policy; easy to log.
Disadvantages: It brings additional processing overhead, resulting in the sacrifice of some system performance. The processing resources (processor, memory, etc.) of the proxy server are relatively high.
(2) Implementation examples of two proxy servers
· MSP – Microsoft Proxy Server/ISA (wingate)
· Squid
's network information about proxy servers: mainly implemented at the application layer. When the proxy server receives a connection request from a client, it first verifies the request, then forwards the processed request to the real server, and after receiving the response from the real server and doing further processing, it sends the reply to the requesting client. The proxy server plays the role of intermediate transfer between the external network and the internal network. Therefore, a proxy server is sometimes called an application layer gateway.
A proxy server can inspect and authenticate packets at any layer on the network, allowing packets that meet security rules to pass and discarding the rest. It allows passing packets to be copied and passed on by the gateway, preventing direct connections between trusted servers and clients and untrusted hosts.
A proxy server firewall uses a proxy server host to separate the external network from the internal network. After the data packets sent from the inside are processed by such a firewall, it seems to come from the network card outside the firewall, so that the effect of hiding the internal network structure can be achieved. The host on the internal network does not need to set the firewall as a gateway, and only needs to directly point the IP address of the service to the proxy server host to obtain Internet resources.
Network information on the difference between proxy servers and gateways: Both proxy servers and gateways send data inside the network to the Internet. If the gateway is compared to a door leading to the Internet, the proxy server is a wall, which can avoid exposing some important information inside the network. Proxy servers filter some Internet connections and only allow those that are accessible. The gateway does not do any filtering.
9. Link layer gateway
is essentially a proxy server. Point-to-point TCP connections are not allowed, but two TCP connections are established by the gateway.
Example: socks.
10. The carrier of the firewall
The firewall can be installed on an independent machine running popular operating systems (linux, unix), or it can be implemented as an independent module in a router or LAN switch. The following introduces some other firewall implementation carriers.
(1) Bastion Host : It is exposed to the external network and is also the main connection
point for internal network users. It can act as a platform for application layer gateways and link layer gateways.
(2) Host firewall : a software module used to protect personal hosts, which can filter and limit data packets, and is generally located in the server. (Why is it used to protect personal hosts, but the location is in the server?)
(3) Personal firewall : used to control communication between a personal computer or workstation on one side and the Internet or corporate network on the other. The basic function is to prevent unauthorized remote access to the computer; it can also prevent worms and viruses.
11. Location and configuration of the firewall
(1) Network segment of the ceasefire zone: There are one or more network devices between the internal firewall and the external firewall, and this area is called the network segment of the ceasefire zone.
(2) The role of the internal firewall: ①Compared with the external firewall, the internal firewall has stricter filtering capabilities to protect the internal network from attacks; ②The internal firewall provides two-way protection related to the DMZ; ③Multiple internal firewalls can be used to Protection between various parts of the internal network.
(3) Virtual Private Network VPN: Virtual Private Network VPN can be realized through IPSec. One logical way to enforce IPSec is in a firewall. (It is recommended to read it again and expand it)
(4) Distributed firewall: Distributed firewall is an independent firewall and a host firewall that work together under the control of the central management.
12. Development of firewall
· Distributed firewall
· Further development of application layer gateway (authentication mechanism, intelligent agent)
· Integration with other technologies
(such as NAT, VPN (IPSec), IDS, and some authentication and access control technologies, firewall itself security and stability)