Overview of Cyber Security
basic concept
- Basic properties of network security communication:
- Confidentiality; only the sender and intended recipient can understand the contents of the message
- Message integrity; the sender and receiver want to be sure that the message has not been tampered with, or that tampering must be detected
- Accessibility and usability; accessibility and usability are characteristics of network information that can be accessed by authorized entities and used on demand
- Authentication; sender and receiver want to confirm each other's real identity
- Network security: the hardware and software of the network system and the data in the system are protected from being damaged, changed or leaked due to accidental or malicious reasons, the system runs continuously and reliably, and the network service is not interrupted
cyber security threat
- Eavesdropping: eavesdropping on information during message transmission, or occasionally deleting message information
- Insertion: The attacker actively inserts information into the connection to confuse the information and let the receiver receive false information
- Forgery: the source address in the packet can be forged
- hijacking: "taking over" the connection by removing/replacing the sender or receiver
- Denial of service Dos and distributed DDos, etc.; Denial: prevent the server from providing services to other users; DDos: use multiple source hosts to flood each other
- Mapping: "Exploring the path" before launching an attack, find out the description service running on the network, use the ping command to determine the address of the host on the network, and finally use the port scanning method to try to establish a TCP connection with each port at a time
- Sniffing: Through the promiscuous mode network interface card, all packets/frames on the broadcast medium can be received or recorded, and all unencrypted data can be read
- IP spoofing: The "raw" IP packet is directly generated by the application, and the source IP address field of the packet is set to an arbitrary value. The receiver cannot determine whether the source address is spoofed, which may lead to incorrectly stated reception, or hide the identity of the network security attack
data encryption
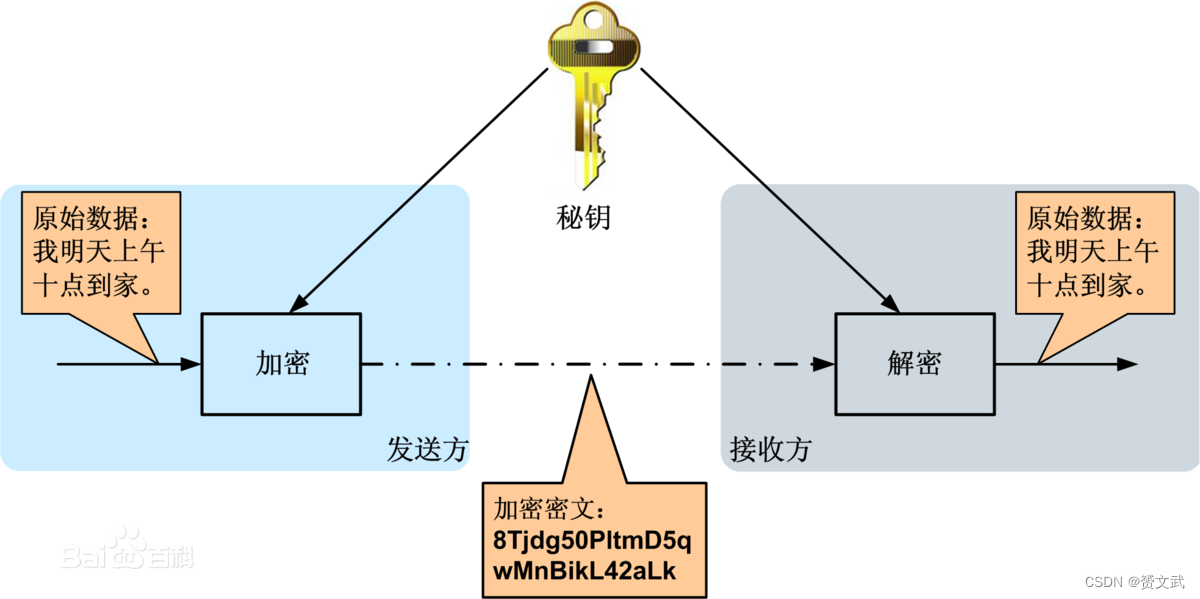
- M is a finite set of possible plaintexts called the plaintext space
- C is a finite set of possible ciphertexts called the ciphertext space
- K is the finite set of all possible keys called the key space
- E is an encryption algorithm, which can be effectively calculated for any key
- D is the decryption algorithm, for any key, it can effectively calculate
traditional encryption
- Encryption methods are divided into substitution ciphers and transposition ciphers:
- Alternative cipher; typical: Caesar cipher - push the letters back by 3 digits in sequence (not counting the three backwards themselves)
- Transposition cipher; also known as permutation cipher, the basic process is as follows: group the plaintext according to the length of the key and arrange it in rows, supplement it with x, and output the groups in order according to the order specified by the key; the example in the book is as follows:

Symmetric key encryption
- Symmetric key encryption systems can be divided into block ciphers and stream ciphers
- Common block ciphers:
- DES: Using a 56-bit key, the plaintext is a 64-bit block sequence, and a total of 16 rounds of encryption are performed. Each round of encryption will perform complex replacement and permutation operations, and each round of encryption will use a 48-bit key derived from a 56-bit key. key, and finally output a 64-bit key with the same length as the plaintext
- Triple DES: encrypt-decrypt-encrypt when encrypting
- AES: involves operations - byte replacement, row shifting, column confusion, round key addition; features - variable block length and key length, the number of cycles allows corrections within a certain range according to security requirements, and brings together security , Efficiency, ease of use, flexibility, etc., the ability to resist linear attacks and differential attacks is greatly enhanced. If 1s brute force cracks DES, it will take 149 trillion years to crack AES
- IDEA encryption algorithm: a block cipher algorithm with a block length of 64 bits and a key length of 128 bits. The same algorithm can be used for encryption and decryption
Asymmetric/public key encryption
- RSA: Currently widely used public key algorithm, the algorithm has high security and a large amount of calculation. In addition to RSA, there is Diffie-Hellman algorithm
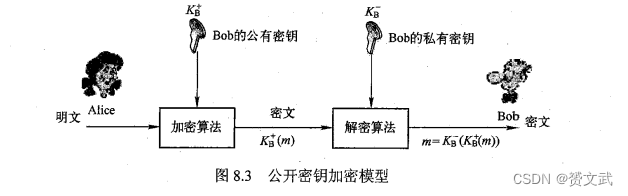
- Alice uses BOb's public key and encryption algorithm to encrypt the ciphertext and transmit it to Bob
- Bob decrypts Alice's encrypted ciphertext with Bob's private key and decryption algorithm
- Bob's private key encryption can be decrypted with Bob's public key
Message Integrity and Digital Signatures
Message/message integrity has also become the main goal of message/message authentication: prove that the message is indeed from the claimed sender; verify that the message has not been tampered with during transmission; prevent the time and order of the message from being tampered with, prevent The message holding period has been tampered with; preventing repudiation
Message Integrity Detection Method
- The main characteristics of cryptographic hash functions: general hash functions have open algorithms, can be quickly calculated, can generate fixed-length output for many-to-one mapping of messages of any length, and cannot predict the hash value of any message. Messages cannot generate the same hash value
- Typical hash functions:
- MD5 - get 128-bit hash value
- SHA-1 - produces a 160-bit hash value, a typical one-way hash algorithm used to create digital signatures
message authentication
- Message authentication: an authentication method that enables the recipient of a message to verify that the received message is authentic
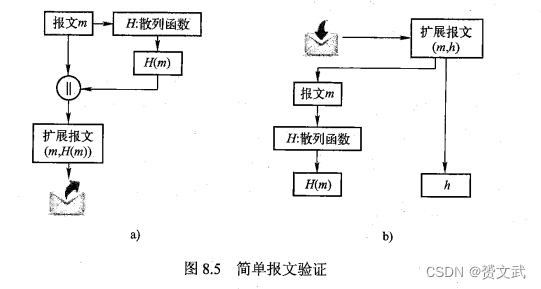
- Simple message verification works as follows:
- The working principle of message authentication code MAC is shown in the following figure:
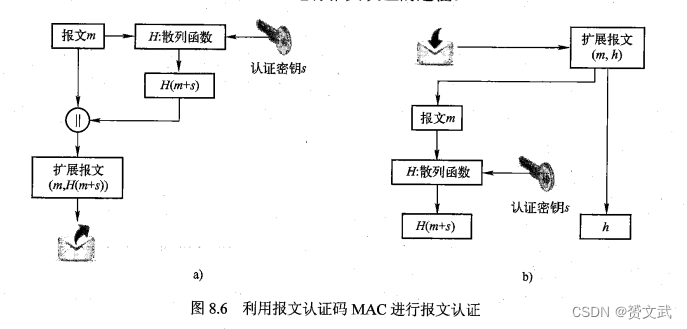
Note: MAC sender and receiver share an authentication key
digital signature
- Message authentication enables the receiver to verify the sender and whether the content of the message has been tampered with
- Digital signatures are mostly used for identification
- Requirements for digital signatures:
- The receiver can confirm or verify the sender's signature, but cannot forge it
- After the sender sends a signed message to the receiver, it can no longer deny the message it signed
- The receiving party cannot deny that the signed message has been received, and the receipt authentication
- A third party can confirm the message transmission between the sender and the sender and cannot forge the process
- Simple digital signature: the digital signature is encrypted with a private key, and the authentication is decrypted with a public key
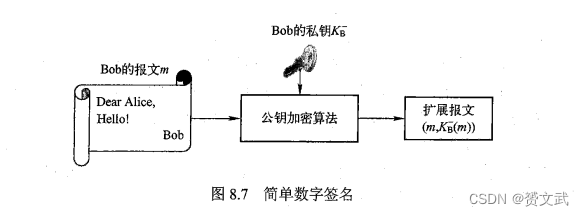
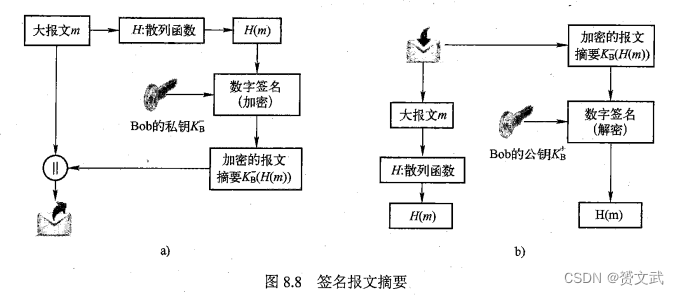
- The workflow of signed message digest is as follows:
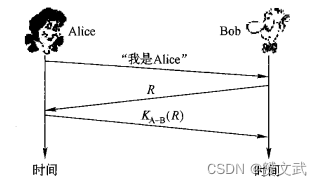
Authentication
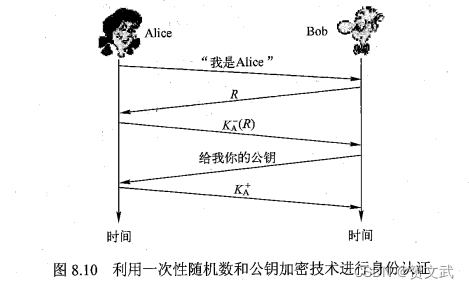
- In order to prevent replay attacks, a more effective way is to introduce a one-time random number
- Using public-key cryptography on one-time random numbers
The schematic diagram of the existing security loopholes ("Messenger Crisis") is as follows:
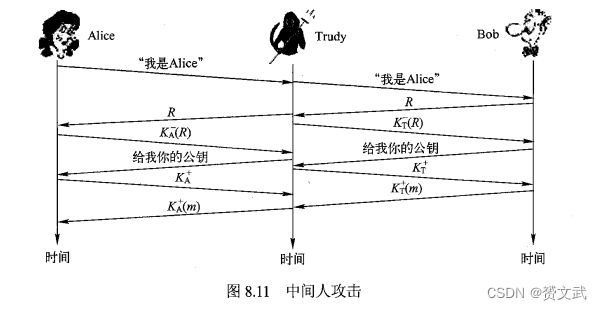
Key Distribution Center and Certificate Authority
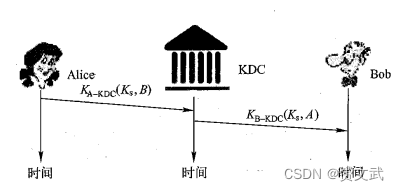
key distribution center
- Communication initiator generates session key
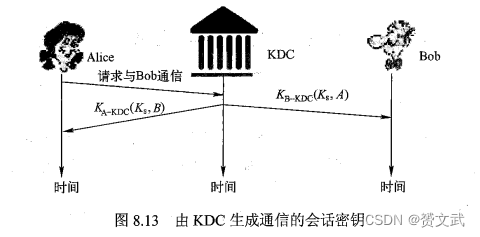
- The session key for communication is generated by the KDC for both parties
Certificate Authority
- The role of the certification authority (CA):
- Verify the true identity of an entity
- Once an entity's identity has been verified, the CA generates a certificate that binds its identity to the entity's public key
Firewall and Intrusion Detection System
Basic Concepts of Firewall
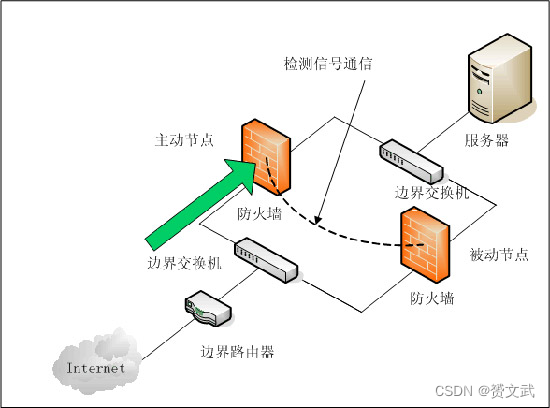
- The basic premise for the firewall to function: ensure that all traffic from the outside to the inside and from the inside to the outside passes through the firewall, and only authorized traffic is allowed to pass through, and the firewall can restrict access to authorized traffic
Firewall Classification
- Stateless packet filter; firewall deployed on internal and network edge routers; filtering is based on the following parameters: source IP address and destination IP address of IP datagram, source port number and destination of TCP/UDP segment Port number, ICMP message type, SYN and ACK flag bits of TCP message segments, etc.
- stateful packet filter
- Application Gateway; a combination of both
Intrusion Detection System IDS
- Intrusion detection system: A device or system that can generate warnings when potentially malicious traffic is observed. IDS not only operates on the TCP/IP header, but also performs deep packet inspection and detects the correlation between multiple data
Network Security Protocol
secure email
- The requirements of e-mail for network security mainly include the following aspects:
- Confidentiality; only the real recipient can read the message
- Integrity; message has not been tampered with in transit
- Identity authentication; the sender cannot be impersonated, and the receiver can confirm the identity of the sender
- Non-repudiation; the sender cannot repudiate
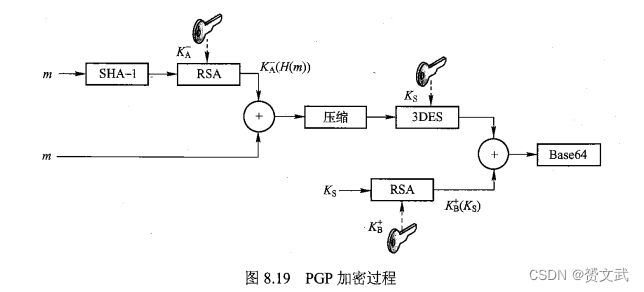
- Secure Email Standard - 1991, PGP Standard
- PGP encryption process:
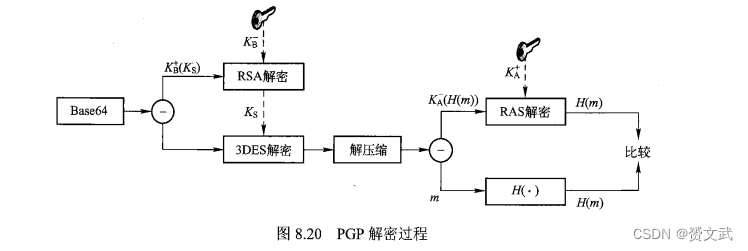
- PGP decryption process:
Secure Sockets Layer SSL
- When the HTTP protocol uses SSL for secure communication it is called HTTPS
- Simplified SSL mainly includes:
- The sender and receiver use their respective certificates, private keys to authenticate and authenticate each other, and exchange shared keys
- Key derivation or key derivation, where the sender and receiver use a shared key to derive a set of keys
- Data transmission, divide the transmission data into a series of records, encrypt and transmit
- The connection is closed. By sending a special message, the connection is safely closed, and no loopholes can be left to be exploited by the attacker.
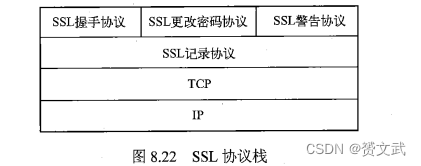
- SSL protocol stack:
- SSL handshake process:
- The client sends the algorithm list it supports, as well as the client's one-time random number nonce, and the server selects an algorithm from the algorithm list, and sends the client's own choice, public key certificate and server-side one-time random number nonce
- The client verifies the certificate, extracts the server public key, generates a pre-master key, encrypts the pre-master key with the public key in the server, and sends it to the server to realize key distribution
- The client and server independently calculate the encryption key and MAC key based on the pre-master key and a random number
- The client sends a MAC for all handshake messages and sends this MAC to the server
- The server sends a MAC for all handshake messages and sends this MAC to the client
Virtual Private Network VPNN and IP Security Protocol IPec
- PN - a network of dedicated services and specific organizations based on dedicated network equipment, links or protocols
- VPN key technology - tunneling technology, data encryption, identity authentication, key management, access control and network management, etc.
- Tunneling protocols include protocols:
- Passenger Protocol: Determines which protocol the encapsulated object belongs to
- Encapsulation protocol: Determine which protocol to follow for encapsulation and what fields need to be added
- Bearer Protocol: Determines what kind of public network the final object will be placed on
- The realization technology of VPN technology IPSec is the safest and most widely used technology
- Two typical transmission modes of IPSec: transport mode and tunnel mode
- Security association SA establishes parameters that need to be maintained:
- Security Parameter Index (SPI); 32-bit unique identifier
- Serial number; used to resist replay attacks
- Anti-replay windows; receivers use sliding windows to detect malicious hosts replaying datagrams
- life cycle; life cycle
- Operation mode; divided into transmission mode and tunnel mode
- IPSec tunnel source and destination addresses; these two parameters are only available in tunnel mode
- AH protocol and ESP are the core of IPSec
- Transmission mode AH
- Tunnel Mode AH
- Transport Mode ESP
- Tunnel Mode ESP
- IPSec key exchange IKE mainly includes the following contents:
- Internet Security Association and Key Management Protocol (ISAKMP)
- Key exchange protocol OAKELY
- Sharing and Key Update Technology SKEME