Preface


Many friends who have read my articles know that I have been engaged in the network security industry for several years and have accumulated rich experience and skills. During this time, I participated in the planning and implementation of multiple actual projects, successfully prevented various network attacks and vulnerability exploitation, and improved the level of security protection.
Many friends also sent me private messages asking me how to learn? How to dig holes? How to penetrate?
A more reasonable approach should be to start with vulnerability exploitation. You might as well analyze some public CVE vulnerabilities. There is relatively good information on many vulnerabilities. The more you analyze and study them, the more you understand the vulnerabilities. Then it will be easier to start digging!
As the saying goes: "Sharpening a knife will save you from chopping wood." That's the truth.
**Then this article will teach you how to learn from scratch to digging loopholes! **Don’t forget to give a thumbs up if you learned something~

What is vulnerability mining
Vulnerability mining refers to discovering and exploiting security vulnerabilities by analyzing them in software, systems or networks. Vulnerability mining is an important task in the field of information security, which can help companies and organizations improve the security of their systems and avoid hacker attacks and data leaks.
The vulnerability mining process can generally be summarized into the following steps:

-
Determine the target: Determine the software or system to be mined. This may be an application, operating system, network device, or other system.
-
Collect information: Collect information about the target, including architecture, protocol, version, configuration, etc. This information can be obtained through Internet searches, manual scans, automated tools, and other means.
-
Analyze Vulnerabilities: Perform vulnerability analysis through manual and automated techniques to identify potential vulnerability types and attack surfaces. Vulnerability types may include buffer overflow, SQL injection, cross-site scripting, file inclusion, code injection, and more.
-
Verify vulnerabilities: Verify the identified vulnerabilities. This usually involves building exploit code and trying to run it on the target system to determine if the vulnerability exists.
-
Write a report: For verified vulnerabilities, you need to write a vulnerability report. The report should include a description of the vulnerability, impact, difficulty of exploitation, and recommended fixes.
-
Report a Vulnerability: Send a vulnerability report to the owner or operator of the target system. Typically, this information will be sent to the security team or person responsible for the system.
-
Track vulnerabilities: Track the progress of fixing vulnerabilities and monitor their status. If a vulnerability is fixed, the fix can be verified to ensure that the vulnerability has been completely resolved.
It should be noted that vulnerability mining is a job that requires long-term continuous learning and practice. To become an excellent vulnerability digger, you need to constantly learn new technologies and methods, and maintain good thinking habits and innovation capabilities.
Learn the correct sequence for vulnerability hunting
Of course, before learning vulnerability mining, you need to master the following aspects:
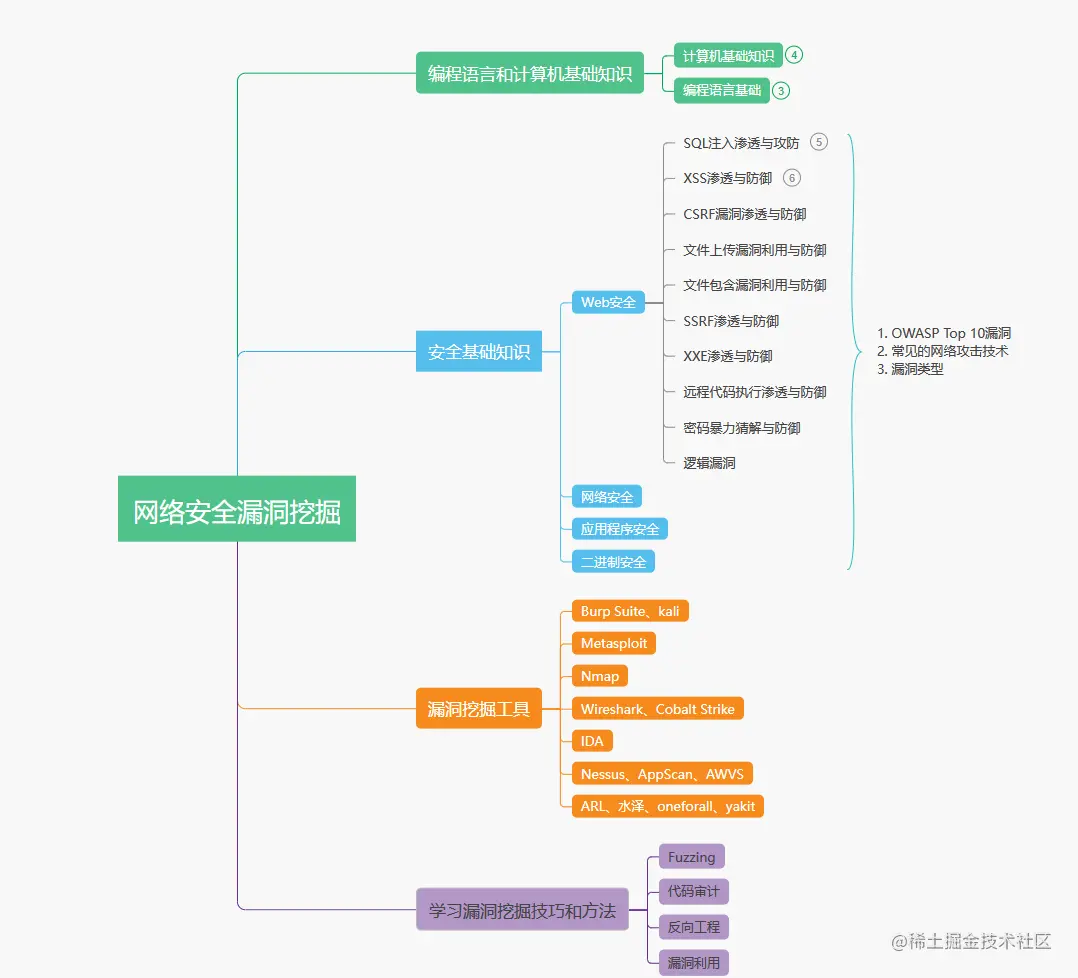
Programming languages and computer basics
During the vulnerability mining process, diggers need to write code to verify and exploit vulnerabilities, so they need to master at least one programming language, such as C, Python, Java, etc. At the same time, you also need to understand the basic knowledge of computers, such as the structure of computer systems, principles of operating systems, basic concepts of computer networks, working principles of databases, etc. Without basic knowledge in this area, it will be difficult to understand the various techniques and tools required for vulnerability mining.
Security Basics
Vulnerability mining is a security job, so you need to master some basic security knowledge, such as web security, network security, application security, binary security, etc. It is recommended that diggers first learn some basic security knowledge, such as OWASP Top 10 vulnerabilities, common network attack techniques and vulnerability types, etc. This can help diggers better understand the problems and challenges faced in vulnerability mining.
Vulnerability mining tools
Learning vulnerability mining requires mastering some commonly used vulnerability mining tools, such as Burp Suite, Metasploit, Nmap, Wireshark, IDA, etc. These tools can help diggers speed up the process of vulnerability discovery, and can also help diggers deeply understand the principles and causes of vulnerabilities. For example, Burp Suite can help miners intercept and modify HTTP requests, and Metasploit can help miners construct attack payloads, etc.

Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
In general, learning vulnerability mining requires a comprehensive mastery of various aspects of knowledge, including programming, basic computer knowledge, basic security knowledge, vulnerability mining tools, and vulnerability mining techniques and methods. It is recommended to start with basic knowledge, gradually learn in depth, continue to practice, and discover and solve problems in practice, so that you can gradually become an excellent vulnerability digger.
For beginners with some basic knowledge, how should they conduct vulnerability mining?
1. How to find vulnerabilities
From a certain perspective, we can compare vulnerability digging to playing a maze game. The difference is that this maze is slightly different from the mazes we usually see in games:
(1) You can’t immediately see its overall appearance
(2) As the vulnerability mining work deepens, the shape of this maze gradually expands.
(3) You will have multiple starting points and ending points, but you cannot determine where these points are.
(4) In the end, this maze may never be 100% complete, but it can figure out a complete path from point A to point B.
For a more specific description, we can summarize the vulnerability mining work into three steps:
(1) Enumerate program entry points (for example: interface for interacting with the program)
(2) Think about possible unsafe states (i.e. vulnerabilities)
(3) Try to use the identified entry point to reach an unsafe state
That is to say, in this process, the maze is the application we study, the map is our understanding of the program, the starting point is our entry point (interaction interface), and the end point is the unsafe state of the program.
The so-calledentry point can be either an intuitively visible interactive interface on the UI interface, or a very fuzzy and transparent interactive interface ( For example, IPC), the following are the points of interest to some security researchers:
(1) An older code segment in the application, and this part has not changed much over time.
(2) The interface part of the application program used to connect program modules developed by different development teams or developers
(3) Some of the debugging and testing code in the application. This part of the code should have been removed when forming the Release version, but for some reason it was accidentally left in the program.
(4) The difference between the client and the server calling the API in C-S mode (with client and server) applications (such as the hide attribute field in the web form)
(5) Internal requests not directly affected by end users (such as IPC)
In terms of attack surface, vulnerabilities can be divided into two categories, general vulnerabilities (General) and contextual vulnerabilities (Contextual). General vulnerabilities refer to vulnerabilities that can be found when we are not very familiar with the business logic of the application, such as some RCE (remote code execution), SQLi (sql injection), XSS (cross-site), etc. Contextual vulnerabilities refer to vulnerabilities that can only be found if you are very familiar with the application's business logic, authentication methods, etc., such as permission bypass.
In the process of vulnerability mining, first prioritize research and testing those parts that may pose a huge threat to the application based on experience. Some lightweight threat detection models (such as STRIDE) can assist us in making such decisions.
Let’s look at an example of a vulnerability in a WEB application. Desktop programs will be introduced later:

First, we assume that the target web application is a single-page-application SPA. We have obtained legal verification to access this application, but we do not have any source code or binaries for the server. In this case, when we enumerate the entry points, we can further understand its business logic and functions by exploring the different functions of the application. We can see the HTTP request content through packet capture analysis, and we can also analyze the client's web page code acquisition needs. Submit a list of forms, but the final limitation is that we cannot specifically know the difference between the APIs called by the client and the server. However, through the above method, we can find some entry points.
The next step is to manipulate these entry points in an attempt to reach our desired unsafe state. Since there are many forms of vulnerabilities, we usually need to build a test set suitable for the business function vulnerabilities of the test application in order to find vulnerabilities most efficiently. If we don't do that, we will spend a lot of time on some useless test sets and see no effect (for example, when the background database is Postgres, we use xp_cmdshell to test, and test again and again to no avail). Therefore, when constructing a test set, you need to have a deep understanding of the application logic. The following figure vividly demonstrates the effect of the inefficient test set:
For desktop applications, the idea of vulnerability mining is essentially similar to that of web programs, but there are some differences: The biggest difference is that the execution method and process of desktop applications are different from those of web programs. The following figure shows the vulnerability mining of desktop applications. Some contents of:
Compared with black box testing, when the source code is available (white box testing), the guess work done in finding vulnerability mining points such as code entry and program execution paths will be greatly reduced. In this case, the data Payload execution from the entry point to an unsafe program location is less efficient than backtracking from an unsafe program location to the entry point. However, in white-box testing, your test coverage of the code may be affected by the limitations of your own knowledge.
Knowledge required for vulnerability mining
The knowledge required to engage in vulnerability hunting is extremely broad and changes over time, depending on what you are working on (web applications, desktop applications, embedded, etc.). However, the knowledge areas that need to be mastered can always be considered certain, and can be roughly divided into the following four aspects:
(1) Program forward development technology.
This is a capability that developers need to master, including programming languages, system internal design, design patterns, protocols, frameworks, etc. People with rich programming experience and development capabilities often have a deeper understanding of the target application during the vulnerability mining process than those who only have knowledge of security-related fields, and thus have higher output.
(2) The concept of integrating offense and defense.
This knowledge ranges from basic security principles to ever-changing vulnerability patterns and vulnerability mitigation measures. The concept of combining attack and defense can effectively help researchers not only discover vulnerabilities, but also quickly provide effective vulnerability mitigation measures and avoidance methods.
(3) Use tools effectively.
Being able to use tools efficiently can quickly transform ideas into practice. This requires continuous accumulation of experience by taking the time to learn how to configure and use the tools, apply them to your own tasks, and build your own workflow. Furthermore, it is necessary to have an in-depth understanding of the principles of the tools used and how to re-develop them so that they can be more efficiently applied to current work practices. In fact, process-oriented learning methods are often more efficient and valuable than tool-oriented learning methods. When you find yourself encountering a bottleneck in using a tool, don't shrink back, try to transform it, or complete it through your own hands-on practice Tools that can be adapted to the current work often help to quickly accumulate a lot of practical experience. Help us practice vulnerability mining more efficiently in the future.
(4) Understanding of target applications.
Finally, and most importantly, as a vulnerability digger, you must have a deeper understanding of the security of the application you are researching than the developer or maintainer of this application. This way you can find as many vulnerabilities in the program as possible and fix them.
The following table describes what you need to know when digging for vulnerabilities in web applications and desktop applications. The entries in each category are for illustrative purposes only and are not exhaustive.

These areas of knowledge will help you improve your ability to find vulnerabilities. If the above section is about the knowledge needed to dig out vulnerabilities, then the following section will talk about how to do it.
write at the end
I hope this article can help you solve some of the mysteries of vulnerability mining. It’s normal to encounter difficulties and feel overwhelmed while learning and researching vulnerability mining. But this is the process of learning. Only by constantly trying can you make progress. I wish you go further and further on the road of vulnerability discovery.

Cyber Security Learning Package

Data directory
-
Growth Roadmap & Learning Plan
-
Supporting video tutorial
-
SRC&hacker literature
-
Network protection operation information
-
A must-read list for hackers
-
Collection of interview questions
282G《Network security/hacking technology introductory learning gift package》, yes Scan the QR code below to get it for free!
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
1. Growth roadmap & learning plan
To learn a new technology, as a novice, you must first learn the growth roadmap, If the direction is wrong, efforts will be in vain.
For students who have never been exposed to network security, we have prepared a detailed learning and growth roadmap & learning plan for you. It can be said to be the most scientific and systematic learning route. It will be no problem for everyone to follow this general direction.

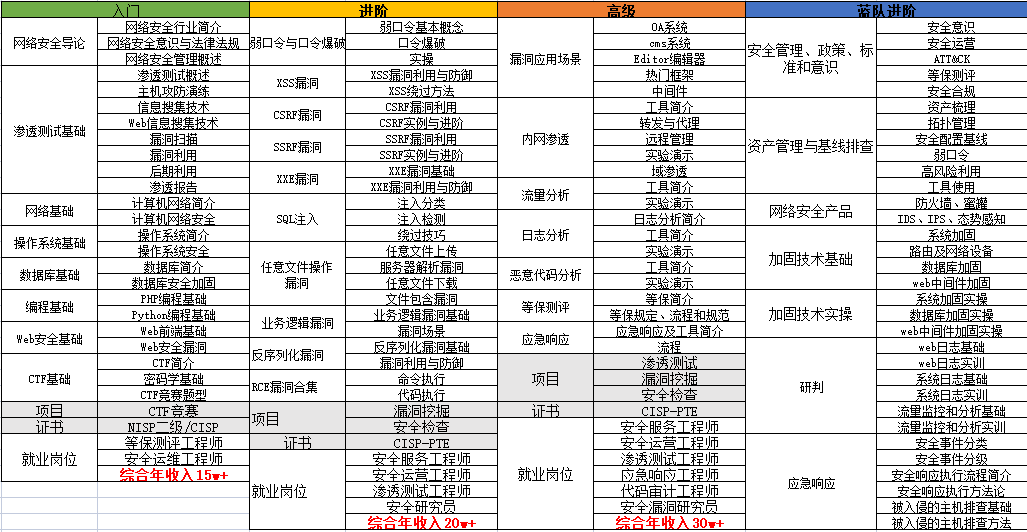
2. Video tutorial
Many friends don’t likeobscure text. I have also prepared video tutorials for everyone, including a total of21 chapters, each chapter is the essence of the current section.


3.SRC&hacker literature
Everyone’s favorite and most concerned aboutSRC technical books & hacker technology are also included
SRC technical documents:

Since hacker information is a sensitive resource, it cannot be displayed directly here!
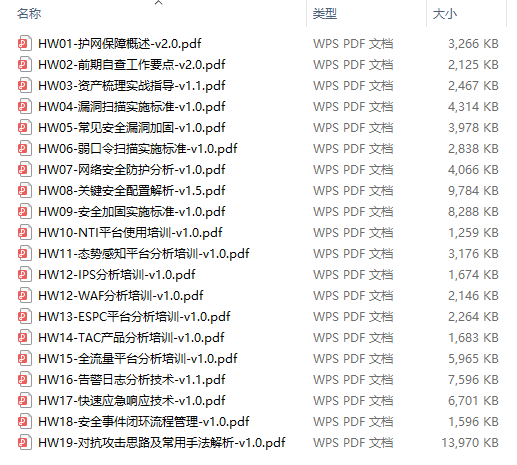
4. Network protection action information
We have also prepared corresponding information regardingHW Net Protection Operation. These contents can be equivalent to the golden fingers of the competition!
5. A must-read list for hackers
**

**
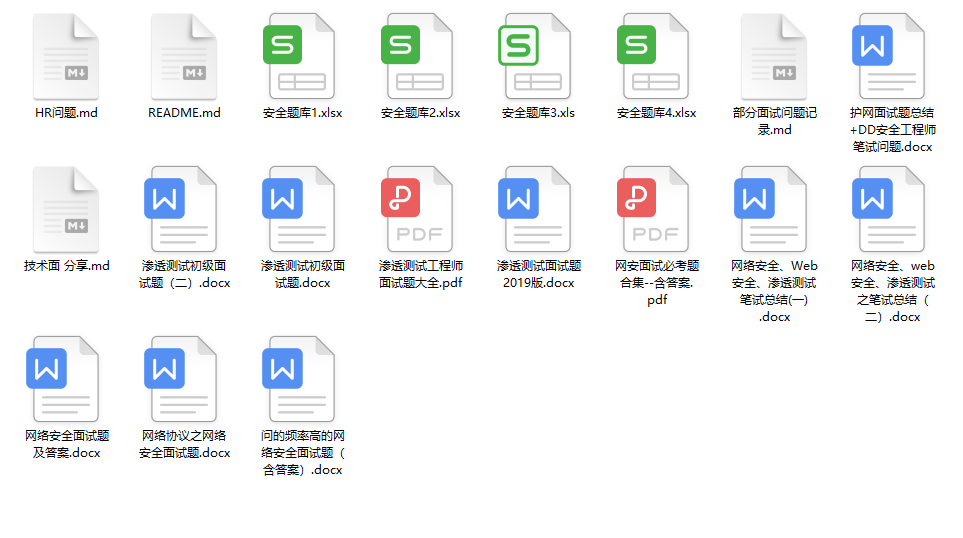
6. Collection of interview questions
When you have learned this by yourself, you will startthinking about finding a job, and work cannot be avoidedReal questions and interview questions.
To prevent harmonization, more content can be obtained by scanning ~

Friends need a complete set of the "Network Security/Hacking Technology Introduction Learning Gift Pack282G /span>! scan the QR code below to get it for free》, you can
Due to limited space, only part of the information is displayed. You need to click on the link below to obtain it.
Special statement:
This tutorial is purely technical sharing! The purpose of this book is never to provide technical support to those with bad intentions! We also do not assume any joint liability arising from the misuse of technology! The purpose of this book is to awaken everyone's attention to network security to the greatest extent, and to take corresponding security measures, thereby reducing the economic losses caused by network security! ! !