1. Introduction to ADB
1. What is adb
The full name of ADB is Android Debug Bridge, which acts as a debug bridge and is a client-server program . The client is the computer used for operation, and the server is the Android device.
ADB is also a tool in the Android SDK, which can directly operate and manage Android emulators or real Android devices.
2. Why use adb
Run the shell (command line) of the device
to manage the port mapping of the emulator or the device
Upload/download files between the computer and the device Uninstall
and install the application of the device, etc.
When the App encounters bugs such as ANR/Crash, you can use ADB to catch them fetch log
In short, ADB is a bridge connecting Android phones and PCs, so ADB is also called Android debugging bridge (note: it is Android, not iOS), which allows users to fully operate the phone on the computer!
2. Preparation tools
Install adb alone without sdk
1. Download adb
Google is very kind and directly releases the zip of ADB for people to download. The path is as follows:
Windows version: https://dl.google.com/android/repository/platform-tools-latest-windows.zip
Mac version: https://dl.google.com/android/repository/platform-tools-latest-windows .zip
Linux version: https://dl.google.com/android/repository/platform-tools-latest-linux.zip
2. Configure environment variables
After decompression and installation, put the decompression path into the system variable (Path),
How to configure environment variables, for example, my configuration is as follows: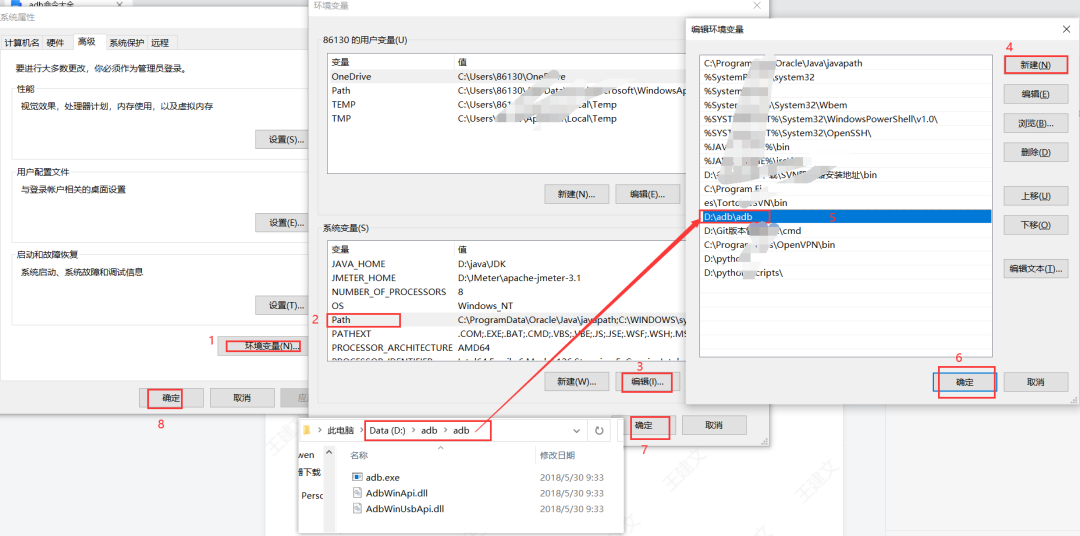
3. Connection
It can be connected through an emulator or through a data cable.
When connected via a data cable, the phone enters "Developer Options" and opens "USB Debugging".
Different brands of Android models have different ways to open "Developer Options" for the first time. Most of them double-click the phone version number 3~5 times, and a toast will remind "Developer Mode is enabled". The specific opening method can be searched on Baidu according to the phone brand.
4. Open the cmd window on the computer
Enter adb version: display the adb version, indicating that the installation is successful

3. Detailed explanation of ADB commands
1. Basic commands
adb version : display adb version

adb help: Help information, view all commands supported by adb

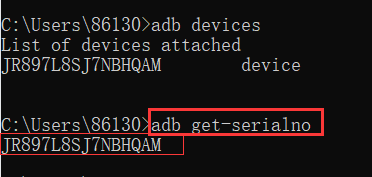
adb devices: view the currently connected devices, the connected devices will be displayed

adb get-serialno: You can also view the device number
2. Permission command
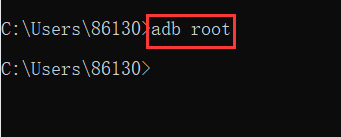
adb root: Get the permissions of the Android administrator (root user).
Note : General test machines can use root privileges.
Android version 9 or above does not support root privileges for commercial machines, but some underlying configurations can be modified
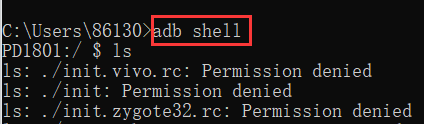
adb shell: log in to the device shell, this command will log in to the shell (kernel) of the device, after logging in to the shell, you can use cd, ls, rm and other Linux commands
adb remount: Obtain the writable permission of the System partition, which requires root to have this permission
3. Establish a connection
adb -d: If the usb is connected at the same time, and the emulator is turned on, connect the only Android device currently connected through usb
adb -e shell: Specify the only emulator currently connected to this computer
adb -s <device number> shell: when multiple mobile phones or emulators are plugged into the computer, specify a device number to connect

exit: exit

adb kill-server: kill the current adb service, if the device cannot be connected, kill and restart. (nothing don't use it)

adb start-server: restart after killing
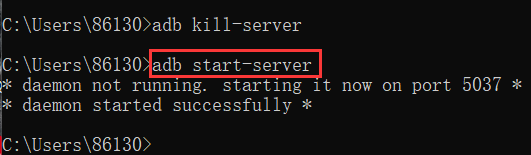
5037: adb default port, if the port is occupied, you can specify a port number, the following command ↓
adb -p 6666 start-server: Arbitrarily specify the port of an adb shell

4. Apk operation instructions
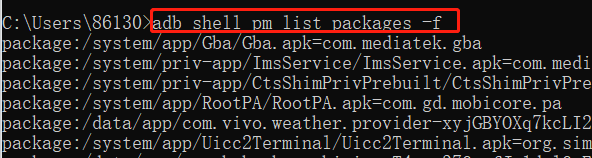
adb shell pm list packages: list the current device/mobile phone, all package names

adb shell pm list packages -f: Display packages and associated files (installation path)
adb shell pm list packages -d: display disabled package names
adb shell pm list packages -e: display currently enabled package names
adb shell pm list packages -s: display system application package names
adb shell pm list packages -3: display enabled Install the third-party package name
adb shell pm list packages xxxx: add the package name to be filtered, such as: xxx = taobao
adb install <file path\apk>: install the local apk software on the device (mobile phone). If the external installation of the mobile phone requires a password, remember to enter the password on the mobile phone.

adb install -r <file path\apk>: Overwrite installation

adb install -d <file path\apk>: allow downgrade overwrite installation
adb install -g <file path\apk>: authorize/obtain permissions, open all permissions when installing software
adb uninstall <package name>: uninstall the software/ app.
Note: The apk is installed during installation, and the package name is the package name during uninstallation. You can view the package names that need to be uninstalled through adb shell pm list packages.

adb shell pm uninstall -k <package name>: Although the application is uninstalled, but still save the data and cache of this application
adb shell am force-stop <package name>: force quit the application/app

5. File operation instructions
adb push <local path\file or folder> <mobile phone path>: copy the local (pc) file or folder to the device (mobile phone)

Note 1: The path of the PC machine and the path of the Android machine have different separators.
Note 2: If the copy fails, there is a high probability that there is no permission. You can first use the two commands introduced above: adb root; adb remount. Using the adb push command
**adb pull <mobile phone path/file or folder> <pc path>: copy the file or folder of the device (mobile phone) to the local. ** Note the same as above

6. Log operation instructions
adb shell logcat -c:清理现有日志
adb shell logcat -v time :输出日志,信息输出在控制台
adb shell logcat -v time > <存放路径\log.txt>:输出日志并保存在本地文件
Ctrl+C:终止日志抓取
adb shell logcat -v time *:E > <存放路径\log.txt>:打印级别为Error的信息
日志的等级:
-v:Verbse(明细)
-d:Debug(调试)
-i:Info(信息)
-w:Warn(警告)
-e:Error(错误)
-f:Fatal(严重错误)
抓取日志的步骤先输入命令启动日志,然后操作 App,复现 bug,再 ctrl+c 停止日志,分析本地保存的文件。
:日志是记录手机系统在运行app时有什么异常的事件
EXCEPTION
也可以把更详细得Anr日志拉取出来:adb shell pull /data/anr/traces.txt <存放路径>
7. System operation instructions
adb shell getprop ro.product.model: get device model

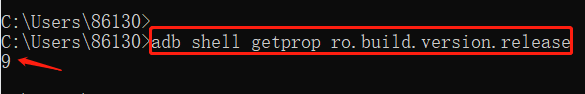
adb shell getprop ro.build.version.release: Get Android system version
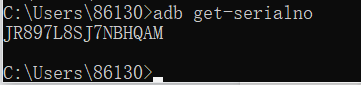
adb get-serialno: Get the serial number of the device (device number)
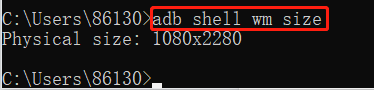
adb shell wm size: get device screen resolution
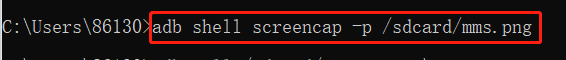
adb shell screencap -p /sdcard/mms.png: screenshot
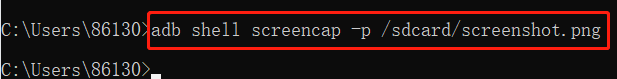
adb shell screencap -p /sdcard/screenshot.png: screenshot
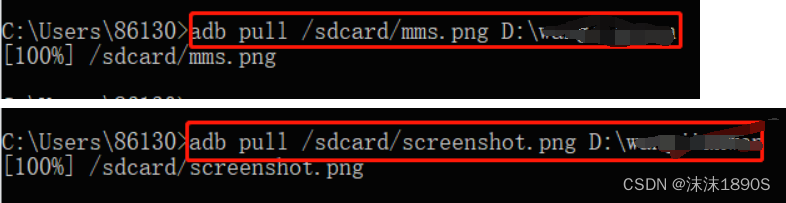
adb pull /sdcard/mms.png <storage path>: export the screenshot to the local
adb pull /sdcard/screenshot.png <storage path>: export the screenshot to the local
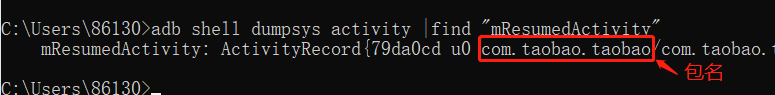
adb shell dumpsys activity |find "mResumedActivity": View the foreground application package name, you must start the app first, applicable to Android 8.0 and above
adb shell cat /proc/meminfo: get phone memory information

adb shell df: get phone storage information

adb shell screenrecord <storage path/xxx.mp4>: record screen, name ends with .mp4
adb shell screenrecord --time-limit 10 <storage path/xxx.mp4>: record screen time is 10 seconds
**题外话**
=========
Many people who are new to the computer industry or graduates of computer-related majors have encountered obstacles everywhere due to lack of practical experience. Let's look at two sets of data:
-
The 2023 national college graduates are expected to reach 11.58 million, and the employment situation is severe;
-
According to the data released by the National Network Security Publicity Week, by 2027, the shortage of network security personnel in my country will reach 3.27 million.
On the one hand, the employment situation of fresh graduates is severe every year, and on the other hand, there is a gap of one million cyber security talents.
On June 9, the 2023 edition of the Employment Blue Book of MyCOS Research (including the 2023 Employment Report for Undergraduates in China and the Employment Report for Higher Vocational Students in China in 2023) was officially released.
Top 10 Majors with Higher Monthly Salary for 2022 College Graduates
The monthly income of undergraduate computer science majors and higher vocational automation majors is relatively high. The monthly income of the 2022 class of undergraduate computer science and higher vocational automation majors is 6,863 yuan and 5,339 yuan, respectively. Among them, the starting salary of undergraduate computer majors is basically the same as that of the 2021 class, and the monthly income of higher vocational automation majors has increased significantly. The 2022 class of overtaking railway transportation majors (5295 yuan) ranks first.
Specifically, depending on the major, the major with a higher monthly income for undergraduates in 2022 is information security (7579 yuan). Compared with the class of 2018, undergraduate majors related to artificial intelligence, such as electronic science and technology, automation, performed well, and their starting salaries increased by 19% compared with five years ago. Although data science and big data technology are newly added majors in recent years, they have performed well, and have ranked among the top three majors with higher monthly income half a year after graduation for the 2022 class of undergraduates. The only humanities and social science major that entered the top 10 undergraduate high-paying list five years ago-French has dropped out of the top 10.

"There is no national security without cybersecurity". At present, network security has been elevated to the height of national strategy and has become one of the most important factors affecting national security and social stability.
Characteristics of the network security industry
1. The employment salary is very high, and the salary rises quickly. In 2021, Liepin.com released the highest employment salary in the network security industry, which is 337,700 yuan per capita!
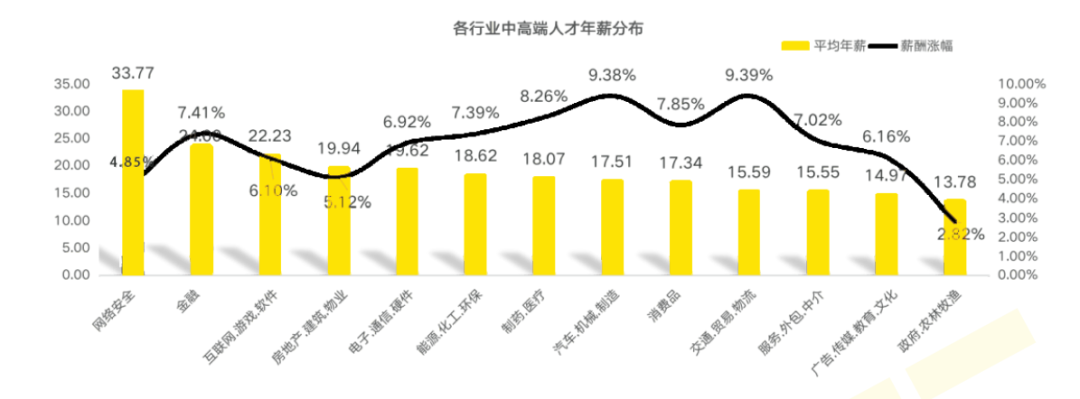
2. There is a large talent gap and many employment opportunities
On September 18, 2019, the official website of the "Central People's Government of the People's Republic of China" published: my country needs 1.4 million cyberspace security talents, but schools across the country train less than 1.5 million people each year. Liepin.com's "Cyber Security Report for the First Half of 2021" predicts that the demand for cyber security talents will be 3 million in 2027, and there are only 100,000 employees currently engaged in the cyber security industry.
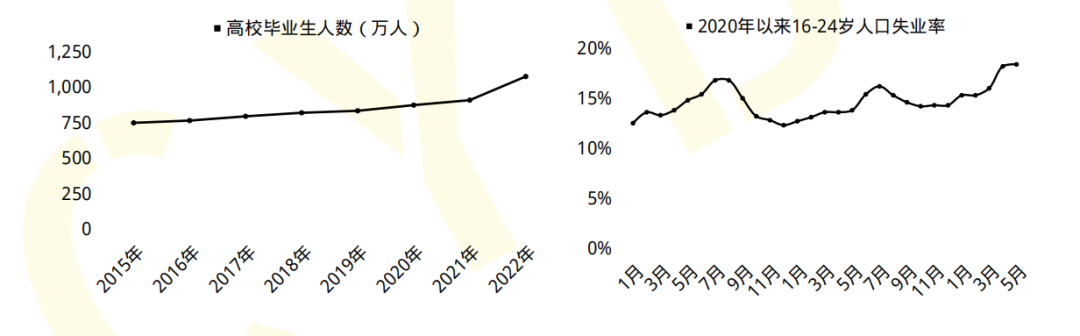
The industry has a lot of room for development and many jobs
Since the establishment of the network security industry, dozens of new network security industry positions have been added: network security experts, network security analysts, security consultants, network security engineers, security architects, security operation and maintenance engineers, penetration engineers, information security management Data Security Engineer, Network Security Operations Engineer, Network Security Emergency Response Engineer, Data Appraiser, Network Security Product Manager, Network Security Service Engineer, Network Security Trainer, Network Security Auditor, Threat Intelligence Analysis Engineer, Disaster Recovery Professional , Actual combat offensive and defensive professionals...
Great career potential
The network security major has strong technical characteristics, especially mastering the core network architecture and security technology in the work, which has an irreplaceable competitive advantage in career development.
With the continuous improvement of personal ability, the professional value of the work will also increase with the enrichment of one's own experience and the maturity of project operation, and the appreciation space is bullish all the way, which is the main reason why it is popular with everyone.
To some extent, in the field of network security, just like the doctor profession, the older you are, the more popular you become. Because the technology becomes more mature, the work will naturally be valued, and promotion and salary increase are a matter of course.
How to Learn Hacking & Cyber Security
Today, as long as you give my article a thumbs-up, I will share my private collection of online security learning materials with you for free, so let’s see what is there.
1. Learning Roadmap
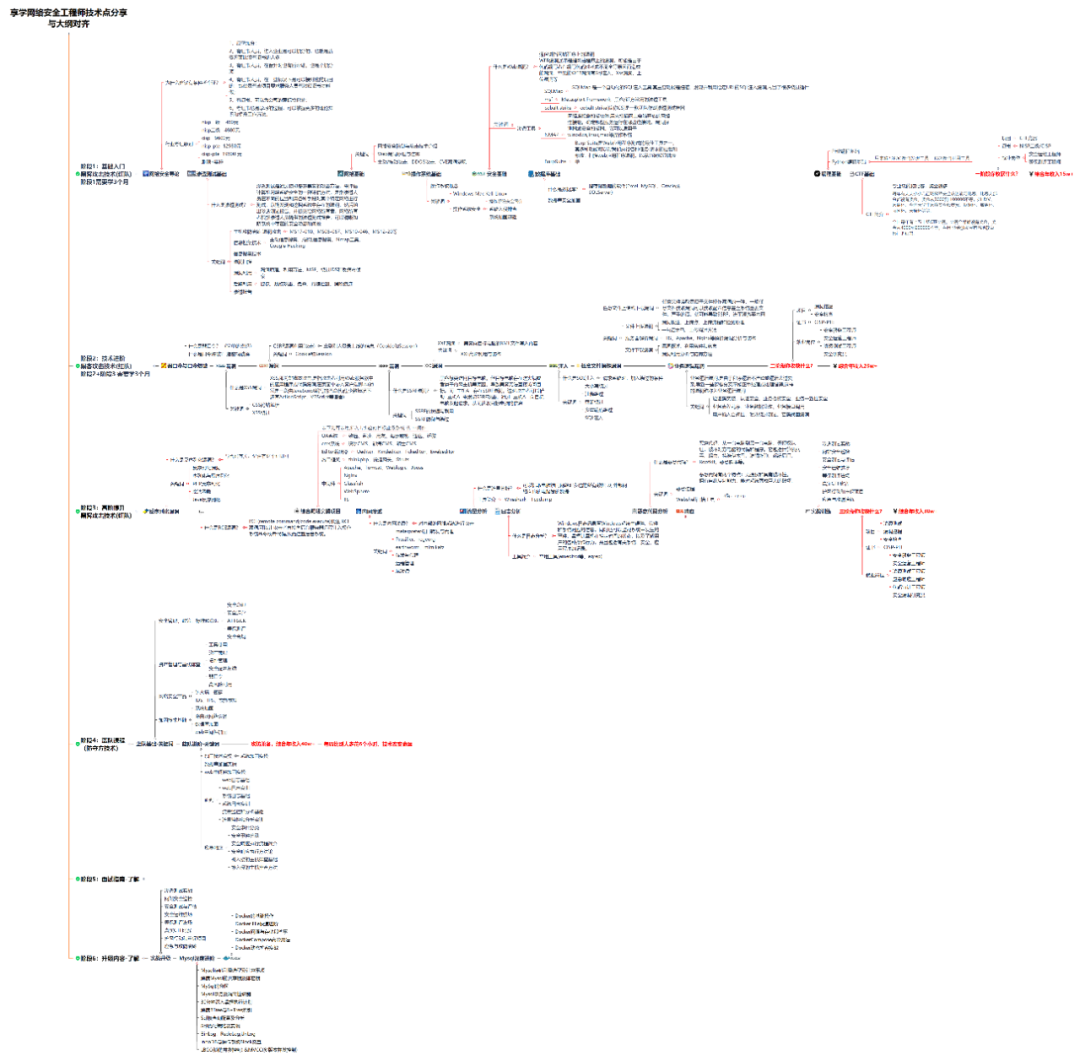
There are also many things to learn in attack and defense. I have written all the specific things to learn in the roadmap above. If you can learn them, you will have no problem getting a job or taking private jobs.
2. Video Tutorial
Although there are many learning resources on the Internet, they are basically incomplete. This is a video tutorial on cyber security recorded by myself. I have a supporting video explanation for every knowledge point in the above roadmap.
The content covers the study of network security law, network security operation and other guarantee assessment, penetration testing basics, detailed explanation of vulnerabilities, basic computer knowledge, etc., which are all learning contents that must be known when getting started with network security.
(It’s all packed into one piece and cannot be unfolded one by one. There are more than 300 episodes in total)
Due to limited space, only part of the information is shown, you need to click the link below to get it
CSDN spree: "Hacker & Network Security Introduction & Advanced Learning Resource Pack" free sharing
3. Technical documents and e-books
The technical documents are also compiled by myself, including my experience and technical points of participating in large-scale network security operations, CTF and SRC vulnerability mining. There are also more than 200 e-books. Due to the sensitivity of the content, I will not show them one by one.
Due to limited space, only part of the information is shown, you need to click the link below to get it
CSDN spree: "Hacker & Network Security Introduction & Advanced Learning Resource Pack" free sharing
4. Toolkit, interview questions and source code
"If you want to do a good job, you must first sharpen your tools." I have summarized dozens of the most popular hacking tools for everyone. The scope of coverage mainly focuses on information collection, Android hacking tools, automation tools, phishing, etc. Interested students should not miss it.
There is also the source code of the case and the corresponding toolkit mentioned in my video, which can be taken away if needed.
Due to limited space, only part of the information is shown, you need to click the link below to get it
CSDN spree: "Hacker & Network Security Introduction & Advanced Learning Resource Pack" free sharing
Finally, there are interview questions about Internet security that I have sorted out in the past few years. If you are looking for a job in Internet security, they will definitely help you a lot.
These questions are often encountered in interviews with Sangfor, Qi Anxin, Tencent or other major companies. If you have good questions or good insights, please share them.
Reference analysis: Sangfor official website, Qi Anxin official website, Freebuf, csdn, etc.
Content features: clear organization, including graphic representation, which is easier to understand.
Summary of content: Including intranet, operating system, protocol, penetration test, security service, vulnerability, injection, XSS, CSRF, SSRF, file upload, file download, file inclusion, XXE, logic vulnerability, tool, SQLmap, NMAP, BP, MSF…
Due to limited space, only part of the information is shown, you need to click the link below to get it
CSDN spree: "Hacker & Network Security Introduction & Advanced Learning Resource Pack" free sharing