Today is August 31, 2023. There are only 65 days until the advanced soft exam. Come on!
Note: The information is collected from the Internet.
Base
Information must depend on the carrier (media) for storage, transmission, processing and application. Information system security can be divided into equipment security, data security, content security and behavioral security.
Information security elements:
- Confidentiality: Also called confidentiality, it ensures that information is not exposed to unauthorized entities or processes and that useful information is not leaked to unauthorized users. It can be realized through information encryption, identity authentication, access control, secure communication protocols and other technologies. Information encryption is the most basic means to prevent illegal leakage of information. It mainly emphasizes the feature that useful information can only be used by authorized objects.
- Integrity: Only authorized people can modify the data and can tell whether the data has been tampered with. It refers to the characteristic that during the process of information transmission, exchange, storage and processing, the information is not destroyed or modified, is not lost, and the information cannot be changed without authorization, which is also the most basic security feature.
- Availability: Also known as validity, authorized entities can access data when needed, that is, attackers cannot occupy all resources and hinder the work of the authorizer. Refers to the characteristics that information resources can be accessed by authorized entities as required, used normally, or restored to use under abnormal circumstances (the security characteristics of the system's user-oriented services). Correctly access the required information while the system is running. When the system is accidentally attacked or damaged, it can be quickly restored and put into use. It is a measure of the user-oriented security performance of network information systems to ensure the provision of services to users.
- Controllability: You can control the flow of information and behavior within the scope of authorization. Refers to the degree of controllability of network systems and information within the transmission range and storage space. It is the control capability characteristic of network systems and information transmission.
- Non-repudiation: Also known as non-repudiation and non-repudiation, it means that during the information exchange process, both parties in network communication are convinced that the participants themselves and the information provided are true and identical, that is, all participants cannot deny or deny their true identity. As well as the authenticity of the information provided and the performance and commitment to complete it.
The security and confidentiality levels involved in the operation of the application system, from large to small granularity, include:
- System level security
- Resource access security
- functional safety
- Data domain security
Encryption and decryption
The process of encryption and decryption goes roughly like this:
First, the sender of the message prepares the original form of the message to be sent, called plaintext. Then the plaintext undergoes a series of transformations to form another form of information that cannot directly reflect the meaning of the plaintext, called ciphertext. The process of converting plaintext into ciphertext is called encryption. A set of rules or methods used in encryption is called an encryption algorithm. After receiving the ciphertext, the recipient restores the ciphertext to plaintext and obtains the letter and specific content, which is decrypted. Decryption also requires the use of a series of methods or rules corresponding to the encryption algorithm, that is, the decryption algorithm. In the process of encryption and decryption, the specific encryption and decryption process is controlled by the parameter information mastered by both communicating parties. This parameter is called the secret key. The secret key is divided into encryption key and decryption key, which are used in the encryption and decryption processes respectively.
In the process of encryption and decryption, if the encryption and decryption keys used are the same, or it is easy to calculate from one to the other, then this method is called a symmetric key cryptography system or a single-key cryptography system.
On the contrary, if the encryption and decryption keys are not the same, or it is difficult to calculate one from the other, it is called an asymmetric key cryptosystem, a public key cryptosystem, or a dual-key system.
Encryption and decryption algorithms can generally be divided into two categories: symmetric and asymmetric:
- Symmetry: DES, IDEA, Skipjack, Lucifer, FEALN, LOKI91, RC4, RC5 (suitable for large data encryption)
- Asymmetric: RSA, ECC, McEliece, Diffe Hellman, Rabin, Ong Fiat Shamir, EIGamal
Symmetric encryption is more efficient than asymmetric encryption.
Symmetric encryption
OF THE
Divide the plaintext to be encrypted into 64-bit data segments as input, and then generate 52 subkeys based on the changes in the 64-bit secret key. The input data segments are sequentially subjected to initial permutation, 16 rounds of iterations, and reverse initial permutation, and then the 64-bit secret key is obtained. arts.
The decryption process of DES is almost the same, except that the order of the subkeys used is exactly the opposite.
The DES encryption algorithm uses a 56-bit key with an additional 8 parity bits (the 8th bit of each group serves as the parity bit), resulting in a maximum block size of 64 bits. This is an iterative block cipher that splits an encrypted block of text in half. Apply a loop function to one half using the subkey, then XOR the output with the other half; the halves are then swapped, and the process continues, except for the final loop without swapping. DES uses a 16-round loop and uses four basic operations: XOR, permutation, substitution, and shift operations. The encryption key length used by Triple DES is 112 bits.
3DES
As a classic symmetric encryption algorithm, the 3DES encryption algorithm has been widely used in data encryption, decryption and identity authentication in various security-related industries.
Both 3DES and DES algorithms are block encryption algorithms, that is, the plaintext is sequentially grouped according to the length of 8 bytes before encryption (if the length of the last group of data is less than 8 bytes, padding is performed). For example: If the plaintext is 16 bytes, the first 8 bytes are used as plaintext data block 1, and the last 8 bytes are used as plaintext data block 2. During encryption, the key (length is 8 bytes) is used to perform independent DES encryption operations on data block 1 and data block 2, respectively, to generate ciphertext data block 1 and ciphertext data block 2, and finally the two ciphertext data blocks are Spliced together in sequence, the DES encryption operation is completed.
3DES, 3-fold DES encryption, performs 3 DES operations on plain text data blocks, and has higher security strength than DES. Here, only 8-byte plaintext data is used as an example. The 3DES algorithm groups the 24-byte key into 8-byte lengths. The first eight bytes are KEY1, the middle 8 bytes are KEY2, and the last 8 bytes are KEY3. When encrypting, use KEY1 to DES encrypt plaintext data block 1 to obtain C1, use KEY2 to DES decrypt C1 to obtain C2, and then use KEY3 to DES encrypt C2 to obtain C3. The decryption process is the opposite. First use KEY3 to DES decrypt C3 to get M3, then use KEY2 to DES encrypt M3 to get M2, and finally use KEY1 to DES decrypt M2 to get M1.
Although the key length of the 3DES algorithm is 24 bytes, during encryption and decryption operations, it is also divided into groups of 8 bytes for DES operations.
IDEA
The IDEA algorithm is an international data encryption algorithm. The IDEA block length is 64 bits and the key length is 128 bits. The operations it uses are very simple, requiring only XOR, modulo 2 16 addition and modulo (2 16+1) multiplication. In terms of software implementation, the IDEA algorithm is more efficient than the DES algorithm.
IDEA and DES are also close, but the key length used is 128 bits, which greatly increases the cracking time.
asymmetric encryption
During the operation, a pair of secret keys is first generated, one of which is a secret key, which is kept by oneself and cannot be disclosed to the outside world, referred to as a private key; the other is a public key, which can be disclosed to the outside world.
Data encrypted with the public key can only be decrypted using the private key, while data encrypted with the private key can only be decrypted with the public key. During the communication process, if the sender wants to send confidential information to the recipient, it needs to be encrypted with the recipient's public key and then sent to the recipient. The recipient can successfully decrypt it through its private key. Others who receive the encrypted ciphertext cannot correctly interpret it, thereby achieving the purpose of confidential communication.
RSA
The security of RSA relies on the decomposition of large prime numbers. The public and private keys are both functions of two large prime numbers. So inferring the plaintext from a key and ciphertext is as difficult as factoring the product of two large prime numbers. Due to the need for large number calculations, the efficiency is very slow compared with DES. RSA is only used for encryption of small amounts of data.
Can be used for digital encryption and digital signatures.
digital certificate
hash function
The hash function is a public mathematical function. The input information of the hash function operation is called the message, and the result obtained after the operation is called the hash code or the message digest. The characteristics of the hash function are as follows:
- Messages with different contents have different hash codes. Given M, it is difficult to find another message M, making H(M) = H(M`); 2. The
hash function is one-way, given M It is easy to calculate h, but given h, it is difficult to infer M according to h=H(M);
3. For any message, its hash code cannot be predicted
4. The hash code has a fixed length, regardless of the original What is the length of the message? The hash code calculated by the hash function has the same length.
MD5
The MD5 hash algorithm produces a 128-bit (16-byte) hash code for an input message of any length. The MD5 algorithm has the following 4 steps:
- To add padding bits, first pad the input message so that the padded data length modulo 512 exceeds 448. If the data length is exactly modulo 512 + 448, you need to add 512 padding bits, that is, the number of padding bits is 1 to 512. The first bit of the padding bit is 1 and the others are 0.
- Complement the length and represent the data length as binary. If the length exceeds 64 bits, the lower 64 bits are truncated; if the length is less than 64 bits, 0 is added to the high bits. The 64-bit message length is appended to the padded message so that the final data is an integer multiple of 512 bits.
- Initialize the MD cache. The MD5 operation uses a 128-bit MD5 cache to store intermediate variables and final results. The cache can see four 32-bit registers A, B, C, and D.
- To process data segments, define 4 non-linear functions F, G, H, and I. The input message operation is processed in units of 512-bit data segments. Each data segment must undergo 4 rounds of logical processing. In 4 rounds Four different functions FGHI are used in each round. Each round takes ABCD and the current 512-bit block as input, and sends it to ABCD after processing.
SHA
SHA is similar to M5D, but the code length is 160 bits. SHA is also calculated using 512-bit long data blocks through complex operations. SHA is more secure than MD5, but the calculation is slower than MD5.
HMAC
HMAC is a message authentication code, usually used together with MD5 or SHA.
Message summary
Message digests are used to ensure data integrity. Once the transmitted data is modified, the calculated digest will be different. Just compare the digests twice to determine whether the data has been modified. The purpose is therefore to prevent the sent message from being tampered with. The purpose of encrypting the digest is to prevent repudiation.
RSA+MD5
The main process of combining RSA with MD5 digital signature is:
the sender of the information generates a message digest by hashing the information, and then the sender encrypts the message digest with its own private key to form the sender's number sign.
This digital signature is then sent as an attachment to the message to the recipient of the message. After receiving the information, the receiver first performs the same hash operation on the received information as the sender to obtain a message digest, and then uses the sender's public key to decrypt the digital signature attached to the information to obtain the sender's calculated hash code. If the two hash codes are the same, the receiver can confirm that the message and digital signature were sent by the sender. Through digital signatures, the integrity of the original information can be identified and the non-repudiation of the information sent by the sender can be achieved.
Certification
PKI/CA
Refer to the PKI/CA system introduction .
Kerberos
Kerberos is a network authentication protocol designed to provide strong authentication services to client/server applications through a key system. The implementation of this authentication process does not rely on the authentication of the host operating system, does not require trust based on the host address, does not require the physical security of all hosts on the network, and assumes that the data packets transmitted on the network can be arbitrarily read, modified and inserted into the data . In the above case, Kerberos, as a trusted third-party authentication service, performs authentication services through traditional cryptography technology (such as shared keys).
Add timestamps to packets to prevent replay attacks.
A computer network authorization protocol used to securely authenticate personal communications in non-secure networks.
AS (Authentication Server) = Authentication Server
KDC (Key Distribution Center) = Key Distribution Center
TGT (Ticket Granting Ticket) = Ticket Authorization Ticket, Ticket of Ticket
TGS (Ticket Granting Server) = Ticket Authorization Server
SS (Service Server) = Specific service provider
protocol
IPSec
In order to ensure secure and confidential communication on IP networks, the IETF developed a set of open standard network security protocols IPSec (IP Security). This protocol applies cryptographic technology at the network layer to provide source address verification, data transmission integrity, access control, confidentiality and other security services to the sender and receiver of information, protecting communications from eavesdropping and resisting network attacks. Moreover, higher-layer application layer protocols can also use these security services directly or indirectly to provide transparent security protection services for their upper-layer protocols such as TCP, UDP, etc., and provide security guarantees for communications in insecure networks such as the Internet. The data in the data packet is encrypted at the IP layer. For IPv4 and IPv6, there are two working modes: transmission mode and tunnel mode.
The basic working principle of the IPSec protocol is: the sender encrypts the data before sending it, and then sends the ciphertext data to the network to start transmission. During the entire transmission process, data is transmitted in ciphertext. Until the data reaches the destination node, the receiver decrypts the ciphertext and extracts the plaintext information. IPSec is not a separate protocol. It includes a complete set of protocols applied to network data security at the IP layer, mainly including AH (Authentication Header, IP authentication header protocol), ESP (Encapsulating Security Payload, encapsulating security payload protocol), IKE ( Internet Key Exchange, Internet Key Exchange Protocol) and some algorithms used for network authentication and encryption, etc.
AH provides data integrity and authentication, but does not include confidentiality; ESP only provides confidentiality in principle, but you can also select appropriate algorithms and modes in the ESP Header to achieve data integrity and authentication. AH and ESP can be used separately or together. IKE provides negotiation of encryption algorithms, keys, etc.
SSL
Secure Sockets Layer, Secure Sockets Layer, SSL is a communication protocol used to securely transmit data. It uses public key encryption technology, symmetric key encryption technology, etc. to protect the confidentiality and integrity of information transmission between two applications. Disadvantages of SSL: It cannot guarantee the non-repudiation of transmitted information.
The SSL protocol includes several aspects such as server authentication, client authentication, data integrity on the SSL link, and data confidentiality on the SSL link. It ensures Internet data transmission by establishing a secure channel between the browser and the Web server. security. Currently, SSL technology using public key encryption has become the industry standard for secure communication on the Internet. The SSL protocol is often used to enhance the security of Web services.
Its successor TLS (Transport Layer Security) is a security protocol that provides security and data integrity for network communications. TLS and SSL encrypt network connections at the transport layer.
PGP
Pretty Good Privacy is an email encryption scheme proposed by American Phil Zimmermann in 1995. It can be used to encrypt emails to prevent unauthorized persons from reading them, and can also add digital signatures to emails so that the recipient can confirm that the email was actually sent by the sender.
PGP is not a new encryption algorithm or protocol. It uses a variety of encryption algorithms: the IDEA algorithm is used to encrypt email content, the RSA public key encryption algorithm is used to encrypt information, and the message digest algorithm for digital signatures is used before encryption. A set of software that uses compression processing and other technical means to encrypt emails. By combining these encryption methods, the good encryption effect of the RSA public key encryption system and the high speed of the symmetric key encryption system are combined, and through the ingenious design of the digital signature and key authentication management mechanism, PGP becomes an excellent of powerful data encryption procedures.
Due to its powerful functions, fast processing, easy use, and open source code, PGP has been widely used in many industries such as IT and has become popular rapidly. Nowadays, in addition to common email encryption, PGP can also be used to encrypt important files. Use PGP instead of UUencode to generate encoded files in RADIX64 format (that is, MIME's BASE64 format) to ensure their safe transmission on the network, or for Documents are digitally signed to prevent tampering and forgery.
PPTP
It is a network technology that supports multi-protocol virtual private networks and works at the data link layer.
HTTPS
Hypertext Transfer Security Protocol, HTTPS = HTTP + SSL
SET
Secure Electronic Transaction, a secure electronic transaction protocol, is used in instant electronic payment scenarios. It is mainly used to ensure the security of payment information in the B2C model. The SET protocol itself is relatively complex, has a strict design, and is highly secure. It can ensure the confidentiality, authenticity, integrity, and non-repudiation of information transmission.
SSH
SSH protocol is a secure shell protocol. It is a security protocol based on the application layer. SSH is a reliable protocol designed to provide security for remote login sessions and other network services.
MIME
MIME is Common Internet Mail Extensions, a widely used email technical specification and security protocol.
Summarize
| protocol | Hierarchy | describe |
|---|---|---|
| IPSec | Network layer | IPSec is a protocol suite, not a single protocol |
| SSL | transport layer | Acts between HTTP at the transport layer and application layer |
| TLS | transport layer | It is an upgraded version based on SSL. |
| SET | transport layer | Protocol for secure electronic transactions |
| HTTPS | Application layer | Hypertext Transfer Protocol, a secure version of HTTP |
| PGP | Application layer | Security package for email |
| SSH | Application layer | Remote session protocol |
Attack and defense
attack
A classification:
- Active attacks: data tampering, identity impersonation, denial of service, replay attacks, spreading viruses, subjective denial
- Passive attacks: network monitoring, illegal login, information interception
Land attack, Ping of Death attack and Teardrop attack are all attacks launched by exploiting TCP/IP vulnerabilities.
Replay Attacks
Replay attacks, also known as replay attacks, replay attacks or freshness attacks, refer to the attacker sending a packet that has been received by the destination host to achieve the purpose of deceiving the system. It is mainly used in the identity authentication process to destroy authentication. correctness. The Kerberos system uses a timestamp scheme to prevent replay attacks. The server can determine whether it is a replay packet based on the timestamp to prevent replay attacks.
ARP attack
ARP attack is an attack technology against the Ethernet Address Resolution Protocol (ARP). This attack allows attackers to obtain data packets on the LAN and even tamper with the packets, and can prevent a specific computer or all computers on the network from connecting normally. The reason why ARP attacks prevent networks from communicating across network segments is that gateway ARP packets are forged so that data packets cannot be sent to the gateway.
SQL Injection
SQL injection attack means that the user submits a database query code and obtains the data the attacker wants based on the results returned by the program. This attack method is achieved by analyzing the database query code and returned results.
Land
Land attack means that the attacker sets the source address and destination address of a packet to the address of the target host, and then sends the packet to the attacked host through IP spoofing. This kind of packet can cause the attacked host to try to communicate with itself. The connection is established and falls into an infinite loop, thus greatly reducing system performance.
Ping of Death
The Ping of Death attack is when the attacker sends a ping packet of more than 65536 bytes to the attacked party. Because the receiver cannot handle such a large ping packet, the attacked system crashes, hangs up, or restarts.
Teardrop
The Teardrop attack is an error in system implementation that utilizes the segmentation/reassembly technology of IP packets. That is, when assembling IP packets, it only checks whether each piece of data is too long, but does not check whether the length of the valid data in the packet is too small. When the data When the effective data length in the packet is a negative value, the system will allocate a huge storage space. Such allocation will cause a large consumption of system resources until it is restarted.
defense
Web page anti-tampering technology
Including time polling technology, core embedded technology, event triggering technology, file filtering driver technology, etc.
Web page anti-tampering means protecting website files and directories, intercepting hackers' tampering operations, and achieving the purpose of preventing web pages from being tampered with. There are three main ways:
- Plug-in polling technology: Use a web page to read and detect the program, then use polling to read the web page to be monitored, compare the web page with the real web page and then determine the integrity of the web page content. If the web page is found to have been tampered with, Alert and restore tampered web pages. However, the obvious shortcomings of this web page anti-tampering technology are: when the web page is very large, the algorithm is very time-consuming and difficult to run, and for a specific web page, the time interval between every two checks is very long, and criminals have every opportunity to do it. Tampering will have a serious impact on the web page.
- Core embedded technology: The tamper detection module is embedded in the WEB server software to check the integrity of each web page when it flows out. If the web page is tampered with, access will be blocked in real time, and the tampered web page will be alerted and restored. . The advantage of this webpage anti-tampering technology is that every webpage is checked when it flows out, so webpages that may have been tampered with are completely impossible to be discovered by readers; however, this method also has shortcomings, because it needs to be detected when the webpage flows out, so Web pages will be delayed for a certain amount of time when flowing out.
- Event triggering technology: Utilize the driver interface or file system (in the operating system) to check the legality of web page files when they are modified, and provide alarms and recovery for illegal operations - that is, tampered web pages. The advantage is that the cost of prevention is very low; the disadvantage: the structure of the WEB server is very complex, and criminals often do not choose to attack from the front. They will attack from the weaknesses of the WEB server or places that are difficult to find and detect, and there will continue to be new attacks. Vulnerabilities have been discovered, so the above defense strategies cannot be foolproof. In addition, once the tampered web page is mixed into the WEB server, there will no longer be a chance to conduct security checks on it.
Intrusion detection methods
The intrusion detection system consists of 4 modules: event generator, event analyzer, event database and response unit. Among them, the event analyzer is responsible for receiving event information and analyzing it to determine whether it is an intrusion or abnormal phenomenon. There are three analysis methods:
- Pattern matching: Compare the collected information with a database of known network intrusions to discover violations of security policies;
- Statistical analysis: First, establish a characteristic file (Profile) of normal use for system objects (such as users, files, directories, devices, etc.). These characteristic values will be used to compare with the behavior that occurs in the network. When the observed value exceeds the normal value range, it is considered that an intrusion may occur;
- Data integrity analysis: It mainly focuses on whether the attributes of files or system objects have been modified. This method is often used for post-event audit analysis.
honey jar
Honeypot technology is an active defense technology and a trap to trap attackers.
firewall
It mainly implements security strategies for network security, and this strategy is a pre-defined, static security technology. Network access behaviors involved in the policy can be effectively managed, while network access behaviors outside the policy cannot be controlled. A firewall's security policy is represented by security rules.
VPN
Virtual private network is to establish a dedicated and secure data communication channel in the public network. It refers to a network technology that uses unsafe public networks such as the Internet as a transmission medium and uses a series of security technology processes to ensure the safe transmission of important information, similar to the security performance of private networks.
Advantages: secure network communication, easy expansion, convenient management, significant cost savings
The principle of VPN
- Safe tunnel technology
- User authentication technology
- access control technology
other
Intrusion detection systems focus on monitoring network security conditions, and most IDS systems are passive.
other
security threats
Common:
- Information Breach: Information is leaked or disclosed to an unauthorized entity.
- Destruction of information integrity: Data is lost due to unauthorized addition, deletion, modification or destruction.
- Denial of Service: Unconditional blocking of legitimate access to information or other resources.
- Illegal use: A resource is used by an unauthorized person or in an unauthorized manner.
- Eavesdropping: Using all possible legal or illegal means to steal information resources and sensitive information in the system.
- Business flow analysis: By long-term monitoring of the system and using statistical analysis methods to study parameters such as communication frequency, communication information flow direction, and changes in total communication volume, valuable information and patterns can be discovered.
- Impersonation: By deceiving the communication system, an illegal user impersonates a legitimate user, or a user with low privileges impersonates a user with high privileges. This is the main attack behavior of hackers.
- Bypass control: An attacker exploits a system's security flaws or vulnerabilities to gain unauthorized rights and privileges.
- Authorization infringement: A person who is authorized to use the Wooden Chair system or resources for a certain purpose uses this permission for other unauthorized purposes.
- Trojan Horse: Software containing an undetectable or harmless segment of a program that, when executed, compromises the user's security.
- Trap door: A "chasm" is set up in a system or component that allows security policy to be violated when specific input data is provided.
- Denial: Attack from the user.
- Replay: A legal backup of intercepted communication data is resent for illegal purposes.
- Computer viruses: divided into viruses that destroy functions and viruses that implant attack capabilities.
- Careless Personnel: An authorized person delegates authority to an unauthorized person for profit or carelessness.
- Media Abandonment: Information is obtained from discarded disks or printed storage media.
- Physical Intrusion: An intruder gains access to a system by bypassing physical controls.
- Theft: Important security items are stolen.
- Business deception: A fake system deceives legitimate users or system resources into giving up sensitive information.
SNMPv3
SNMPv3 divides security threats to network protocols into two categories: primary and secondary. The two main threats against which the standard stipulates that security modules must provide protection are:
- Modification of Information: Some unauthorized entities change incoming SNMP messages in an attempt to perform unauthorized management operations or provide false management objects.
- Masquerade: An unauthorized user impersonates the identity of an authorized user in an attempt to perform management operations.
The SNMPv3 standard also stipulates that the security module must provide protection against two secondary threats:
- Modify the message stream (Message Stream Modificatiqn): Since the SNMP protocol is usually based on a connectionless transmission service, threats of reordering the message stream, delaying or replaying the message may occur. The danger of this threat is that illegal management operations may be implemented through modification of the message flow.
- Message leakage (Disclosure): Information exchanged between SNMP engines may be eavesdropped, and local strategies should be adopted to protect against this threat.
There are two types of threats that the security architecture does not need to protect against because they are not critical or such protection would not be of much use:
- Denial of Service: Because in many cases denial of service is indistinguishable from network failure, it can be handled by the network management protocol and the security subsystem does not need to take measures.
- Traffic Analysis: A third party analyzes the communication rules between management entities to obtain the required information. Since the entire network is usually managed by a small number of management stations, the communication patterns of the management system are predictable, and protective communication analysis is of little use.
computer virus
- Characteristics: contagious, unauthorized, latent and destructive
- Composition: infection module, trigger module, destruction module, main control module
- Detection and removal: signature detection, checksum detection, behavior detection, heuristic scanning, virtual machines
Identity Authentication and Access Control
- Access control technology: user identification and authentication, logical access control, auditing and tracking, public access control
- Identity authentication technology: password authentication, public key signature authentication, card authentication, human biometric authentication, dynamic password, PPP
WPA
Wired Equivalent Privacy WEP is designed to provide confidentiality equivalent to that of a wired LAN.
WEP uses the RC4 protocol for encryption and uses CRC-32 checksum to ensure data integrity. The original WEP standard used an Mbit initialization vector and a 40-bit string to form a 64-bit WEP key.
Wi-Fi Alliance manufacturers use a subset of the 802.11i draft as a blueprint to develop a security certification scheme called WPA (Wi-Fi Protected Access). The design of WPA contains three components: authentication, encryption and data integrity verification.
The first is that WPA uses the 802.1X protocol to authenticate the user's MAC address;
the second is that WEP increases the length of the key and initial vector, using a 128-bit key and a 48-bit initial vector (V) for RC4 encryption.
WPA also uses the Temporary Key Integrity Protocol TKIP, which can dynamically change keys, to change keys more frequently to reduce security risks.
WPA strengthens data integrity protection, uses message integrity coding to detect forged data packets, and contains a frame counter in the message authentication code to prevent replay attacks.
Access control
DAC: Discretionary Access Control. Discretionary Access Control
is managed by the owner of the object. The owner decides whether to grant access rights or partial access rights to other subjects. This control method is autonomous. In other words, under discretionary access control, users can selectively share their files with other users according to their own wishes.
Decisions are made based on the identity of the subject and the access rights allowed.
- Autonomy means that a subject with certain access capabilities can autonomously grant a subset of access rights to other subjects
- High flexibility and widely used
Disadvantages:
The access rights relationship of information will be changed during the movement process. For example, user A can pass its access permission to target O to user B, so that B who does not have access permission to O can access O.
ACL: Access Control List, Access Control List,
MAC: Mandatory Access Control.
Each user and file of Mandatory Access Control is given a certain security level. Users cannot change the security level of themselves or any objects. That is, individual users are not allowed to determine access rights. Only system administrators can determine users and group access rights. The system determines whether a user can access a file by comparing the security levels of the user and the file being accessed.
There are generally five levels of security from highest to lowest:
- Top Secret (T)
- Secret level (Secret, S)
- Confidential (Confidential, C)
- Restricted (R)
- Unclassified (U)
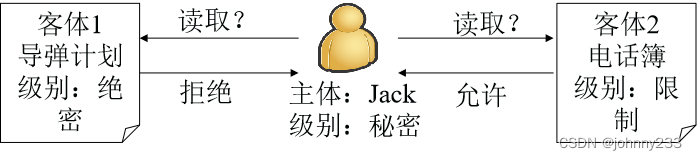
RBAC: Role Based Access Control, Role Based Access Control
- Basic idea: Assign access permissions to certain roles, and users obtain the access permissions owned by the roles by playing different roles.
- Roles become a bridge between access subjects and controlled objects in access control.
- Roles are defined by the system administrator, and the addition or deletion of role members can only be performed by the system administrator. That is, only the system administrator has the authority to define and assign roles.
- The user has no direct connection with the object. He only enjoys the permissions corresponding to the role through the role, thereby accessing the corresponding object. Therefore, users cannot autonomously grant access rights to other users.
TBAC: Task Based Access Control
- Object access control is not static, but changes with the context in which tasks are performed.
- The TBAC model consists of four parts: workflow, authorization structure, trustee set, and permission set.
- The TBAC model is generally represented by a five-tuple (S, O, P, L, AS), where S represents the subject, O represents the object, P represents permission, L represents life (Lifecycle), and AS represents the authorization step.
- TBAC is modeled from the perspective of tasks in the workflow, and can dynamically manage permissions based on different tasks and task statuses. TBAC is well suited for information processing control in distributed computing and multi-point access control and decision making in workflow, distributed processing and transaction management systems.
OBAC: Object-based Access Control, Object-based Access Control,
- Associate access control lists with controlled objects or attributes of controlled objects, and design access control options as a collection of users, groups, or roles and their corresponding permissions.
- Allows reuse, inheritance, and derivation of policies and rules. Derived objects can inherit the access control settings of the parent object.
- It can reduce the workload of allocation, setting role permissions, etc. caused by the derivation, evolution and reorganization of information resources.
Network security system
- OSI security services: object authentication service, access control service, data confidentiality service, data integrity service, non-denial service
- OSI security mechanism: encryption mechanism, digital signature mechanism, access control mechanism, data integrity mechanism, authentication exchange mechanism, traffic filling mechanism, route verification mechanism, justice mechanism
The following functional modules of the security gateway support PKI function:
IKE VPN: When establishing IKE VPN, PKI authentication is supported.
HTTPS/SSH: When using HTTPS or SSH to access the security gateway, PKI authentication is supported.
An email consists of an email header and an optional email body. The email header contains information about the sender and receiver of the email. For the email body, MIME defined by IETF in RFC 2045~RFC 2049 stipulates that the email body can also contain various data types in addition to ASCII character types. Users can use MIME to add non-text objects, such as images, audio, formatted text, or Microsoft Word files, to the body of the email. The security functions of S/MIME have been expanded. It can encapsulate MIME entities (such as digital signatures and encrypted information) into secure objects. RFC 2634 defines enhanced security services, such as the ability for the recipient to confirm receipt, which ensures that the recipient cannot deny receipt of the email.
Information Security Level Protection Management Measures
For reference , the security protection level of information systems is divided into the following five levels:
- After the information system is damaged, it will cause damage to the legitimate rights and interests of citizens, legal persons and other organizations, but will not damage national security, social order and public interests.
- It will cause serious damage to the legitimate rights and interests of citizens, legal persons and other organizations, or damage to social order and public interests, but will not damage national security.
- It will cause serious damage to social order and public interests, or cause damage to national security.
- It will cause particularly serious damage to social order and public interests, or cause serious damage to national security.
- It will cause particularly serious damage to national security.