I. Overview
File contains, it is a function. In various development languages provide built-in file containing function, which allows developers include direct a code file (introducing) a further code file. For example, in PHP, there is provided:
the include (), include_once ()
the require (), require_once ()
These files contain functions that are frequently used in the code design.
In most cases, the file containing the code file that contains the function is fixed, and therefore will not be security problems. However, in some cases, the code contained in the file is written as a variable, and this variable can pass by the front-end user in, in this case, if you do not have enough security considerations, it may lead to a file that contains the vulnerability. Attack with a specified "unexpected" file contains the function will allow to execute, causing malicious actions. Depending on the configuration environment, the file containing the vulnerability divided into the following two situations:
1. Local file contains Vulnerability:
Only servers can be a local file containing the file since the attacker is not able to control the servers, so in this case, the attack will contain some additional fixed system configuration file, so that sensitive information reading system. Many times local file that contains the vulnerability will be combined with some special file upload vulnerability, to form more powerful.
2. Remote File Inclusion Vulnerabilities:
Can through url address of a remote file contains, which means that an attacker can pass arbitrary code, this is nothing to say, ready wounded.
Therefore, in the functional design web application front-end system, try not to let the user to directly pass variable contains the function, if you must do so, it must be done in strict whitelist filtering strategies.
二、File Inclusion(local)
① after we free to choose, in the url I found a file name
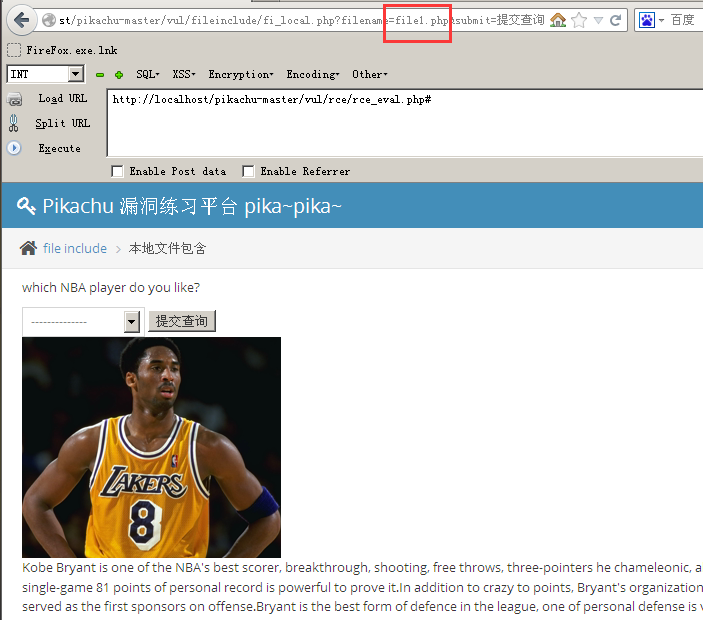
② contain significant information file, we will try to replace other files file1.php information, I created on a parent directory content you are good 1.txt
Change ../../1.txt

三、File Inclusion(remote)
Remote File Inclusion Vulnerability form contains loopholes almost like a local file inclusion vulnerability in the remote, a remote attacker can load code by accessing the external address.
It includes remote vulnerability premise: If you use includer and require, you need to php.ini configuration is as follows:
allow_url_fopen = on // by default
allow_url_include = on // off by default
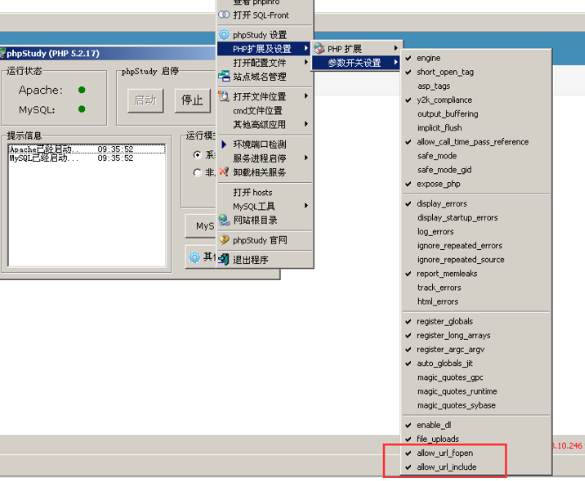
①