content
- past situation
- Cybersecurity is theoretical, results are practical. is it possible?
- Our current efforts
- in conclusion
This article explains why enterprises must rethink their approach to cybersecurity: Are the old approaches effective enough and fully applicable? What actions should companies take to achieve internal information security maturity? We explain how the market seeks to establish cybersecurity processes that produce clear, measurable results.
past situation
What did the term "information security specialist" conjure up a few years ago? Complying with regulatory agency paperwork, passing audits and other checks, and purchasing and installing information protection systems come to mind first, without a deep understanding of the actual need for these measures. Network security is more of a formal task, and enterprises have not worked hard to ensure the real security of information resources. Responsibility also varies: cybersecurity is not a top priority for corporate CEOs.
In 2021, a Positive Technologies survey found that most enterprises have only basic defense tools in their cyber arsenal, and these tools are not designed to detect complex threats. Meanwhile, one in ten respondents lacks an antivirus system. Not all organizations are adopting advanced solutions: For example, 27 percent of respondents said they have traffic analysis systems in place, and only one in five plan to implement such protections.
Only one in 10 respondents to the 2021 survey said their business has a professional turnkey solution.
Typically, organizations deploy resources to improve system security and fix vulnerabilities after an attack has occurred. It's important to ask a question: Can action be taken in advance to prevent negative consequences?
Cybersecurity is theoretical, results are practical. is it possible?
First and foremost, securing the enterprise means protecting the security and continuity of the business, and maintaining the reputation and needs of the enterprise. The main task of implementing an information security system is to ensure the adaptability of business processes to external factors.
Number of successful cyberattacks per year In our study, large-scale attacks (for example, attackers sending phishing emails to many addresses) were treated as a single attack, rather than a series of attacks. Now more than ever, the question of ensuring safety is more urgent. Cybersecurity is becoming an increasingly burgeoning field because of the constant changes in corporate infrastructure and the evolution of attacker attack methods that require rapid adaptation. For example, the 2020 pandemic, the rapid changes in how businesses operate and how employees interact, and the challenges of how cybersecurity implementations are lagging behind the times.
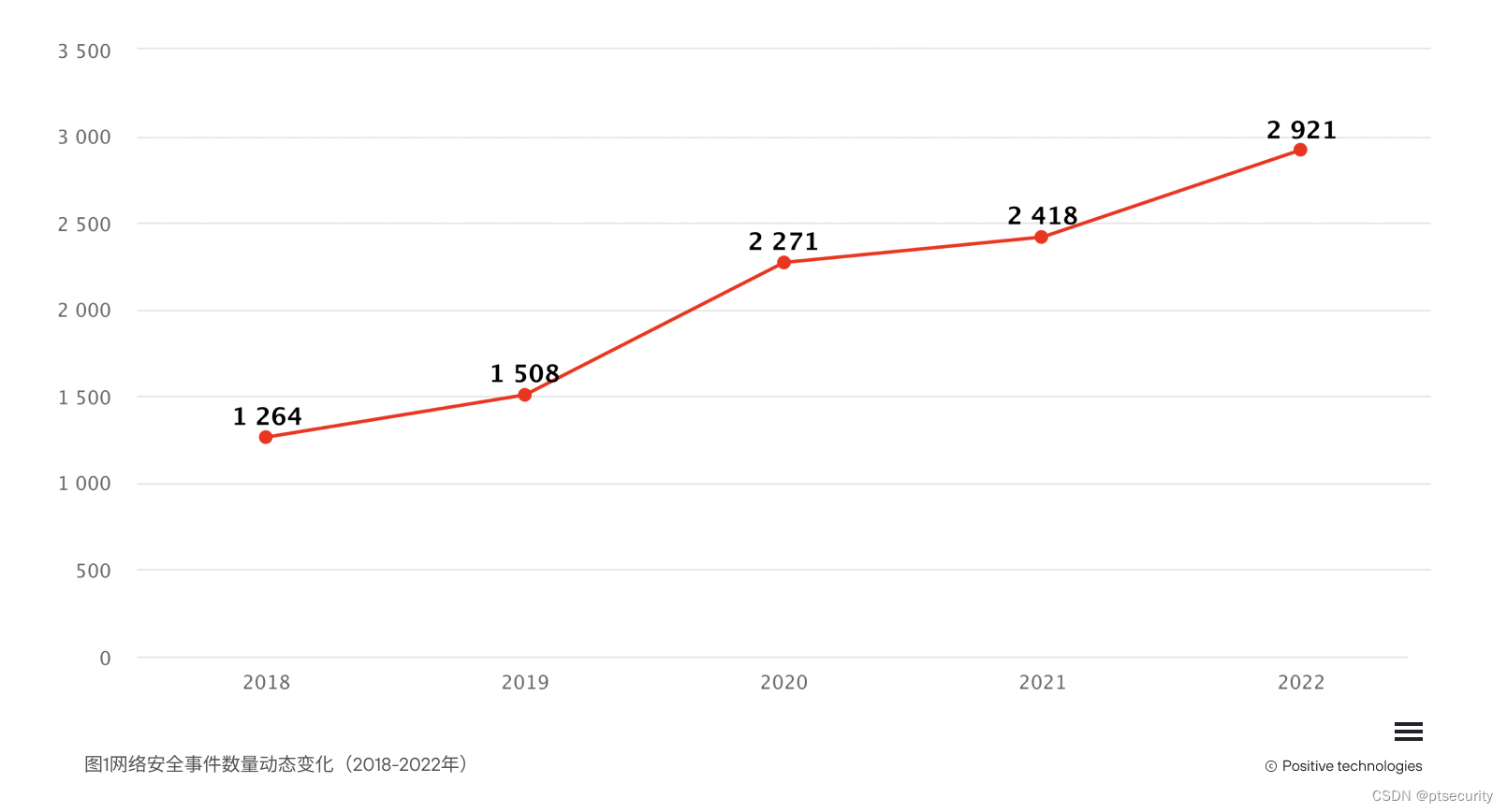
Figure 1 Dynamic changes in the number of network security incidents ( 2018-2022 )
There is growing awareness of the importance of cybersecurity practices, and businesses recognize the need to improve defenses against real-world attacks by malicious actors.
The requirements for enterprises to run multiple penetration testing projects are also changing, as it becomes increasingly difficult to correlate the results of five tests with real-world business impact. According to our data, in 2021, there is a requirement for the verification of corporate intolerable events: in every three projects the customer specified the target system, it was necessary to verify some capabilities of the attacker. These systems include automated process control systems, ATM management systems, SWIFT interbank transfer systems, 1C and website management interfaces. In 2022, 47% of enterprises specify specific goals to achieve when carrying out their work , and 27% of enterprises have experts verify intolerable events.
An intolerable event is an event that occurs as a result of malicious behavior that prevents an enterprise from achieving its operational and strategic objectives, or causes a long-term disruption of its core business.
Often, the nature of corporate activity does not allow it to test the viability of risks on real infrastructure, as this could negatively impact its technical and business processes. Cyber proving grounds, systems that simulate parts of an enterprise's actual infrastructure and are designed to train experts and hone defense skills, are on the rise. A cyber proving ground can verify the list of intolerable events and their achieved consequences, and assess the possible damage without interrupting the actual process.
Our current efforts
Today, it is impossible to protect against absolute cyber threats, and more and more organizations realize the need to establish business-oriented cyber security. Its main goal is to protect the most important assets of the enterprise from the occurrence of intolerable events. Effective cybersecurity is on the rise, a completely different approach unique to organizations with mature information security.
Effective cybersecurity is the security posture of an enterprise that ensures that the enterprise is protected from cyber-attacks and that it is practical to confirm at any time that attackers cannot carry out events that are unacceptable to the enterprise.
Outcome-based security means a qualitatively and quantitatively measurable information protection system that protects enterprise assets from intolerable events. This approach implies that top management is directly involved in the development of enterprise information security and needs to be involved in developing a list of intolerable events. The real concerns and needs of the enterprise become the basis for formulating the specific information security goals of the enterprise.
This approach is being validated over time: According to PwC research , in 2022, more than 70 percent of respondents noted a significant improvement in cybersecurity due to joint investment and collaboration with senior management. For example, 71 percent of respondents said organizations are able to anticipate and respond to new cyber risks associated with digital initiatives before they negatively impact partners or customers.
More than half (51%) of executives say they need a cyber risk management program to implement any major business or operational change. In addition, more than half (52%) of executives said they intend to take the lead on important initiatives such as optimizing supply chains and phasing out products that would weaken the company's network position.
Russia is currently actively promoting the concept of effective cybersecurity. In the first half of 2023, we surveyed the audience of several forums dedicated to information security.
After investigation, Positive Technologies came up with the following results:
71% of the audience are familiar with the general concept of influential cybersecurity.
59% know what an intolerable incident means in the context of effective security.
" Intolerable event " does not seem to be a new term anymore, and some companies are already improving their internal processes according to the new method.

Figure 2 Status of Organizations Implementing Effective Security Elements (Percentage of Respondents)
One in five (22%) respondents said their companies have been able to establish processes that support cyber stability, such as monitoring and responding to cyber threats. Some respondents also indicated that their companies have been able to conduct online training, or start bug bounty programs to find vulnerabilities for a fee.
A bug bounty program is a program that hires various freelance cybersecurity researchers to find vulnerabilities in software, web applications, and IT infrastructure.
Participating in a bug bounty program can further increase a company's information security maturity and strengthen security development. When the human cost of finding vulnerabilities manually by in-house employees is too high, the involvement of external experts can help to find weaknesses more effectively. At the same time, companies can make better use of their budgets by only paying for the vulnerabilities they find, not for the time spent searching for them.
Previously, it was thought that only technology companies could launch such programs. For example, back in 2019, on HackerOne, one of the most popular platforms, such companies accounted for 60% of all attack plans . The most popular industry categories are online services (28%) and software development (21%). Things will be different in 2022. In our bug bounty market study , we analyzed the 24 largest active platforms and found that the industries with the greatest demand for paid bug hunting services are: IT companies (16%), online services (14%), services (13%) , business (11%), financial institutions (9%) and blockchain projects (9%). We expect segments such as government organisations, insurance and transportation to buck this trend.

Figure 3 Industry distribution of bug bounty platform participants
Today, tech companies are distinguished from other industry groups by the fact that the former clearly understand that they want to profit from bug bounty platforms as a tool to improve the security of their services. When choosing a platform, tech companies look at metrics such as the number of active researchers and opportunities for planned outreach. Companies in other industries are only just starting to get into bug bounty platforms. These companies often already have basic information security processes in place and now hope to set a new direction for themselves by engaging a large number of third-party experts.
In the near future, we expect to develop new schemes in which white hat hackers can be paid not only for discovering vulnerabilities, but also for demonstrating the implementation of corporate intolerance events. For example, Positive Technologies launched a program in late 2022 with the main goal of transferring funds from its accounts. Currently, we see that companies understand the need for this approach and are already waiting for the first success stories of other market players implementing this approach.

Figure 4 Stages of establishing effective cybersecurity
in conclusion
Today, the operations of any business can be disrupted not only by economic factors but also by cyber-attacks. Cybercriminal attacks are one of the potential causes of business slowdown and failure to achieve strategic goals.
The direction of cybersecurity is to establish and maintain systems and processes so that attackers have no opportunity to cause intolerable events to the business. Changes at the regulator level are also evident: Decree 250 forces many Russian companies to rethink their approach to cybersecurity and, for the first time, indicates that responsibility for cybersecurity now rests with management and top management. We can also feel a growing emphasis on the protection of citizens' personal data: for example, new requirements of Federal Law No. 152-FZ obligate companies to notify the Federal Security Service and the Russian state news agency of personal data breaches within 24 hours. In early February 2023, the Ministry of Digital Development, Communications and Mass Media of the Russian Federation launched a large-scale project to search for vulnerabilities in the Gosuslugi portal , attracting more than 8,000 hunters from all over the country. We also note experiments by the Ministry of Digital Development, Communications and Mass Media of the Russian Federation, described by Russian Government Decree No. 860 as a method aimed at assessing effective security. The topics of safety assessment and industry regulation have taken on new life, and we look forward to regulators continuing to develop these trends in the future.
The role of cybersecurity in the stability of businesses and governments is becoming increasingly important, and the need for effective security is proving to be one of the key concepts in achieving a high level of security. Currently, there is a growing demand in the market for measurable cybersecurity with the aim of achieving a guaranteed outcome – cyberattacks with intolerable consequences cannot be achieved.
In our research, large-scale attacks (e.g., attackers sending phishing emails to multiple addresses) were treated as a single attack, rather than a series of attacks.
Research includes findings from a survey of information security professionals and agency leaders. The survey was conducted in 2023 at the main Russian forums: Infoforum , Digital Stability and Information Security in Russia , CISO-FORUM .
Hardening is the process of improving security by reducing the attack surface and eliminating potential attack vectors, including eliminating vulnerabilities, insecure configurations, and weak passwords