Hello, everyone, our second phase of blockchain technology sharing is here. This issue is candy sharing public key encryption, which is asymmetric encryption.
When it comes to encryption, decryption, and cryptography, many people shy away from them. They feel that they are obscure and difficult to understand.

However, it is not. You are exposed to cryptography every day, and your online security is closely related to cryptography. If you often surf the Internet, you can find that there are two types of URL links, starting with https and starting with http:
Candy uses the Chrome browser. I don’t know if you have noticed that the http picture, the browser reminds: it is not safe . Then I can tell you, it's not unsafe, it's quite unsafe !

Then let's slowly analyze why the URL starting with http is not safe to surf the Internet?
1 The phishing websites that were missed by http in those years
Many people who have suffered may not understand until now. They are obviously veterans of surfing the Internet for many years, why their access behavior and private data are known to others, and why they entered a phishing website without making mistakes ? You must have heard, emails are tapped, home routers are hacked, etc...
With the development of the Internet, security incidents such as data leakage, data tampering, traffic hijacking, and phishing attacks occur frequently.

All of this is caused by the http transmission protocol that was open to free Internet at the beginning of the Internet .
The reason why the http protocol has caused so many security problems is that the biggest shortcoming is that the data transmitted by the http protocol is all in plain text . To put it bluntly, your data is running naked in the network~~
Think about those years when I was young, I clicked on the small pornographic websites, small video websites...

Then we can't help asking, why didn't we consider security issues when we first designed it? There are two reasons:
-
First, the original intention of the designer is to have first, which is similar to the law of the development of all things: first there is first, and then the best.
-
Second, I have to talk about the origin of the Internet. The Internet began in 1969 with Arpanet in the United States. It was first used for military connections, and then the University of California, Los Angeles, Stanford University Research Institute, UCSB (University of California) and The four main computers at the University of Utah are connected. The main application is in universities, where people instinctively believe that all participants are honest.

With the development of the Internet, everyone can connect to the Internet, and the above methods will fall apart. All kinds of network security problems come one after another...
Find problems and solve them. Since the http protocol is transmitted in clear text, it is fine if we don't encrypt it. Thinking right, then we can't help but ask what encryption to use? How to encrypt it?
2 An annoying key distribution problem in https
Let's review again, the problem with the http protocol: the communication messages between the client and the server are completely transmitted on the link in plain text .
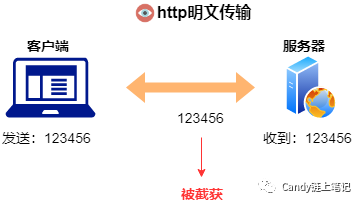
At this time, we want to encrypt the message. In this case, even if the message is intercepted, the encrypted information is obtained, and there is no way to decrypt it. The idea is completely correct.
We can abstract the communication between the client and the server into two people, Alice and Bob, so before analyzing, let's talk about two types of encryption methods in cryptography: symmetric cryptography and public key cryptography (asymmetric cryptography).
● Symmetric encryption: use the same key for encryption and decryption.
How to understand it? Alice wants to date Bob this Sunday, but she doesn't want others to know, so Alice negotiates with Bob to encrypt the information with a symmetric cipher.
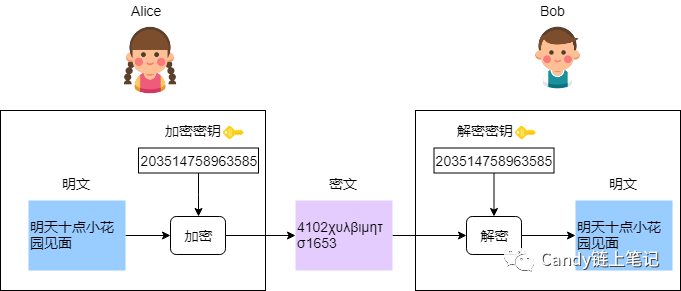
As can be seen from the figure, Alice encrypts the plaintext with a key to ensure that the message is encrypted during transmission. At the same time, after Bob receives the ciphertext, he decrypts it with the same key to obtain the plaintext. Alice and Bob can happily date~~

● Public key cryptography: the method of using different keys for encryption and decryption.
How to understand it? Alice wants to date Bob this Sunday, but she doesn't want to be known by others, so Alice negotiates with Bob to encrypt the information with public key cryptography.
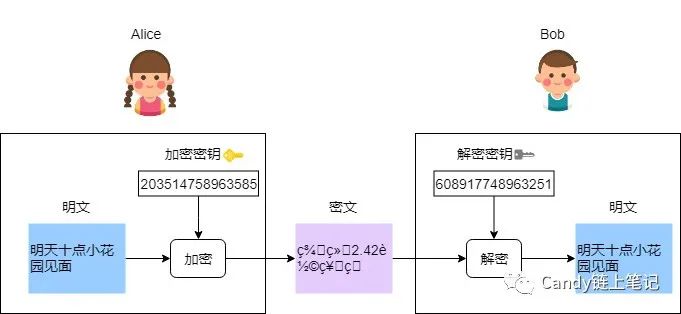
It can be seen from the figure that Alice encrypts the plaintext with an encryption key to ensure that the message is encrypted during transmission. At the same time, after Bob receives the ciphertext, he decrypts it with a different key to obtain the plaintext. Alice and Bob are happily dating again~~

So when communicating with https, which encryption method is used to encrypt the plaintext? The answer is: symmetric encryption . The reason is that symmetric encryption is suitable for encrypting a large amount of content. Since public key encryption involves complex operations, if the encrypted plaintext is too long, the operation speed will be very slow.
But at this time, the question arises, how does Alice tell Bob the key 203514758963585, so that Bob can use this key to decrypt the message she sent? That is the problem of key distribution.
At this time, public key cryptography must be explained again. What does public key cryptography mean? Bob has two keys, one is called the public key and the other is called the private key. As the name implies, the public key can be made public, and the private key is to be hidden secretly.
Anyone who wants to send a message to Bob can encrypt it with Bob's public key, and after Bob receives it, he can decrypt it with his private key. Just like the way Alice and Bob communicate in a public key encryption graph.
Then the whole process of Alice and Bob passing messages and passing keys is as follows:
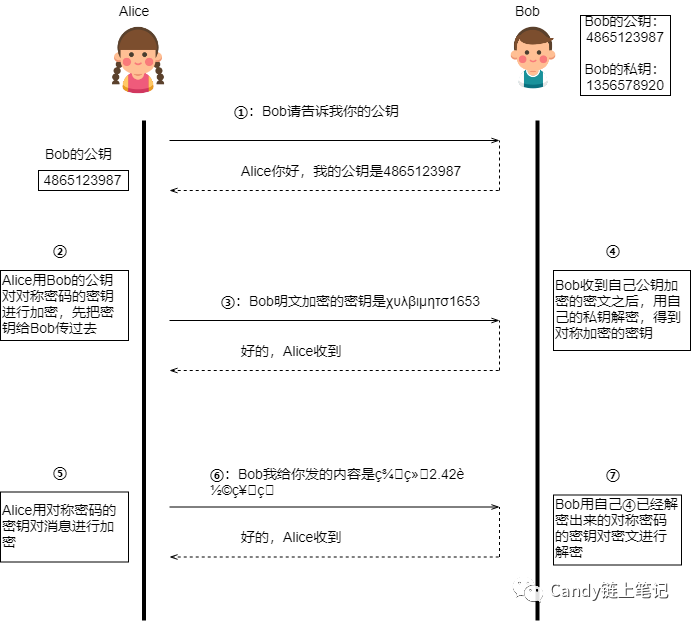
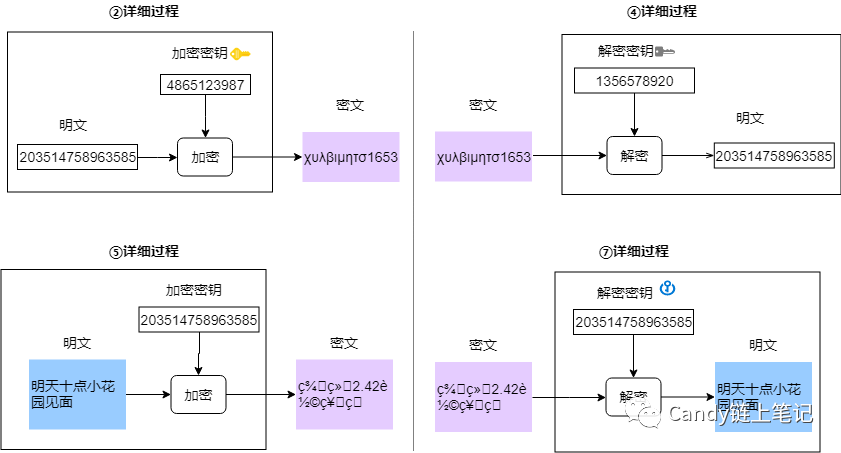
But some people may be curious, if the information in step ③ is hijacked by the attacker, won’t the encrypted key be leaked later? In fact, it doesn’t matter, even if the information in step ③ is hijacked, the hijacker can’t decrypt it, because only Bob’s private key can decrypt the information encrypted by Bob’s public key, but only Bob has Bob’s private key.
Alice and Bob can finally date with peace of mind~~

In fact, the above process is the process of https communication, Alice is the client, and Bob is the server.
HTTPS: It is an HTTP channel with the goal of security. Simply put, it is a secure version of HTTP, that is, an SSL layer is added under HTTP. The security basis of HTTPS is SSL, so the detailed content of encryption requires SSL.
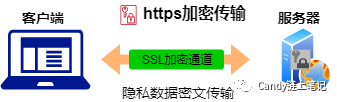
Of course, in addition to encrypting the communication content, SSL also confirms the reliability of the website, which is the CA we often hear. This is another topic, so I won't talk about it today.
Therefore, both symmetric cryptography and public key cryptography are used in https. The public key cryptography involved in https is the RSA algorithm. Therefore, it can be seen that cryptography is a very useful basic subject, not only in the field of information security, but also in the field of blockchain.
I don’t know if you are curious. I originally wanted to share the public key encryption in the blockchain. Why do I say https and http? Because when it comes to public key encryption, there is no way to avoid symmetric encryption, and https is the best combination of the two.

Let’s get down to business and focus on the application of cryptography in the blockchain.
3 Those public keys, private keys and addresses in the blockchain
In public-key cryptography, two keys appear in pairs: a public key and a private key. The public key can be made public, and the private key is kept by itself and cannot be leaked.
So public key cryptography serves two purposes, encryption and signing. Public key encryption, private key decryption; private key signature, public key verification.
Public key encryption, private key decryption
Because Bob's public key can be made public, anyone who wants to send a message to Bob can encrypt it with Bob's public key, and after Bob receives it, he can decrypt it with his private key.
Private key signature, public key verification
And because Bob’s private key is only owned by Bob himself (like Bob’s fingerprint), then Bob can sign the message if he wants to prove that he wrote it (just like we sign a contract and press fingerprint), and the reception of the message After the recipient receives it, he can use Bob's public key to verify it. If successful, it proves that the message was really sent by Bob.

address? is derived from the public key. These derivations are one-way irreversible. For this piece of knowledge, please refer to the previous sharing. Is your password safe? | Hash of blockchain technology ![]() https://blog.csdn.net/koudan567/article/details/120091236
https://blog.csdn.net/koudan567/article/details/120091236
The public-private key pair establishes the account system of the blockchain and the ownership of assets (Token, etc.). The assets of the blockchain are locked on the public key, which represents the identity, and the private key is used to unlock the asset before it can be used.

For example, if I want to transfer assets to you, I use my private key to sign a transaction (including assets, quantity, etc.) that I transfer assets to you and submit it to the blockchain network, and the nodes will verify the signature. Then unlock the asset from my public key and lock it to your public key.
There are a lot of sharing today, including information security content and blockchain content, but in fact it is still a matter of cryptography. It needs to be distinguished, the RSA encryption algorithm is used in https, and the elliptic curve encryption algorithm is used in the blockchain. Different public key encryption algorithms are used.
So far, the public key, private key, and hash involved in the blockchain have been shared. I hope everyone can gain something. This topic will continue, please continue to pay attention.

If you are also interested in the blockchain, you can follow the WeChat public account "Candy Chain Notes", let's move forward together~~