Use of Earthworm (secondary proxy)
This article follows the previous article and continues to explain the use of Earthworm tools
(Secondary Proxy) Forward Connection
The second level of forward proxy occurs in the following situations:
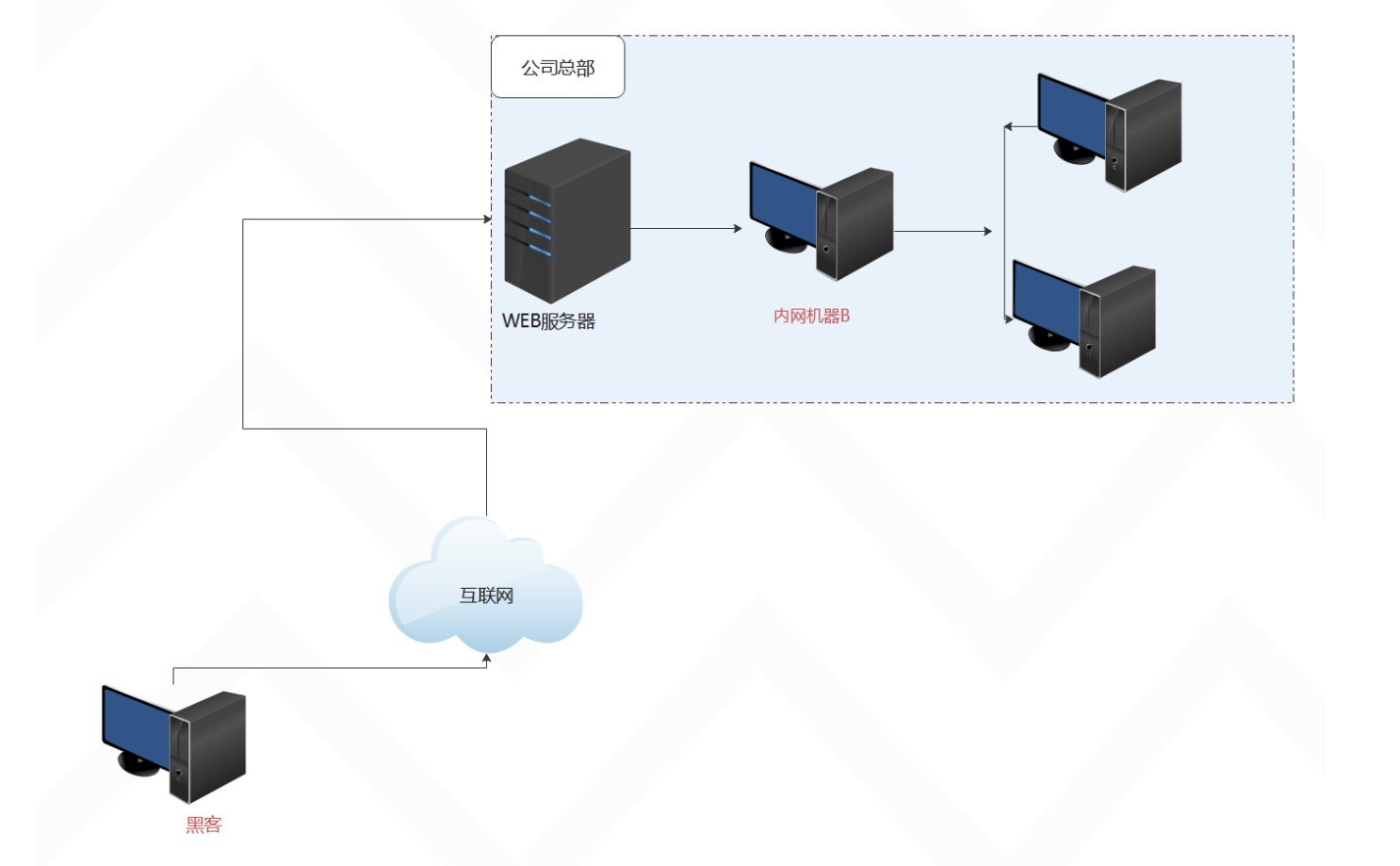
1. The web server is on the public network, and hackers can directly access it.
2. Machine B is on the intranet, and hackers cannot directly access it.
3. The web server can access machine B on the intranet.
4. Machine B on the intranet can access the company's internal machines.
In this case we can use (secondary proxy) forward connection to allow the hacker computer to access the company's internal network
The experimental topology is as follows:
The experimental environment is as follows:
| identity | IP | system |
|---|---|---|
| hacker (native) | 192.168.0.112 | Win11 |
| web server | 192.168.41.133 | Win10 |
| Intranet machine B | 192.168.41.134 | Win10 |
First, we execute the following command on the intranet machine B to listen to the local port 4444
ew.exe -s ssocksd -l