foreword
What? You ask me why the intranet tunnel proxy technology is suddenly the thirteenth article, and the twelfth article? This, due to some irresistible forces, the twelfth blog cannot be published. If you want to read it, please add the intranet penetration qq group: 838076210
Intranet proxy introduction
Intranet proxy introduction
Intranet asset scanning is generally a proxy technology that is required for intranet penetration. If you do not use the intranet, you generally do not need this technology. Intranet proxy technology generally uses http or socks proxy
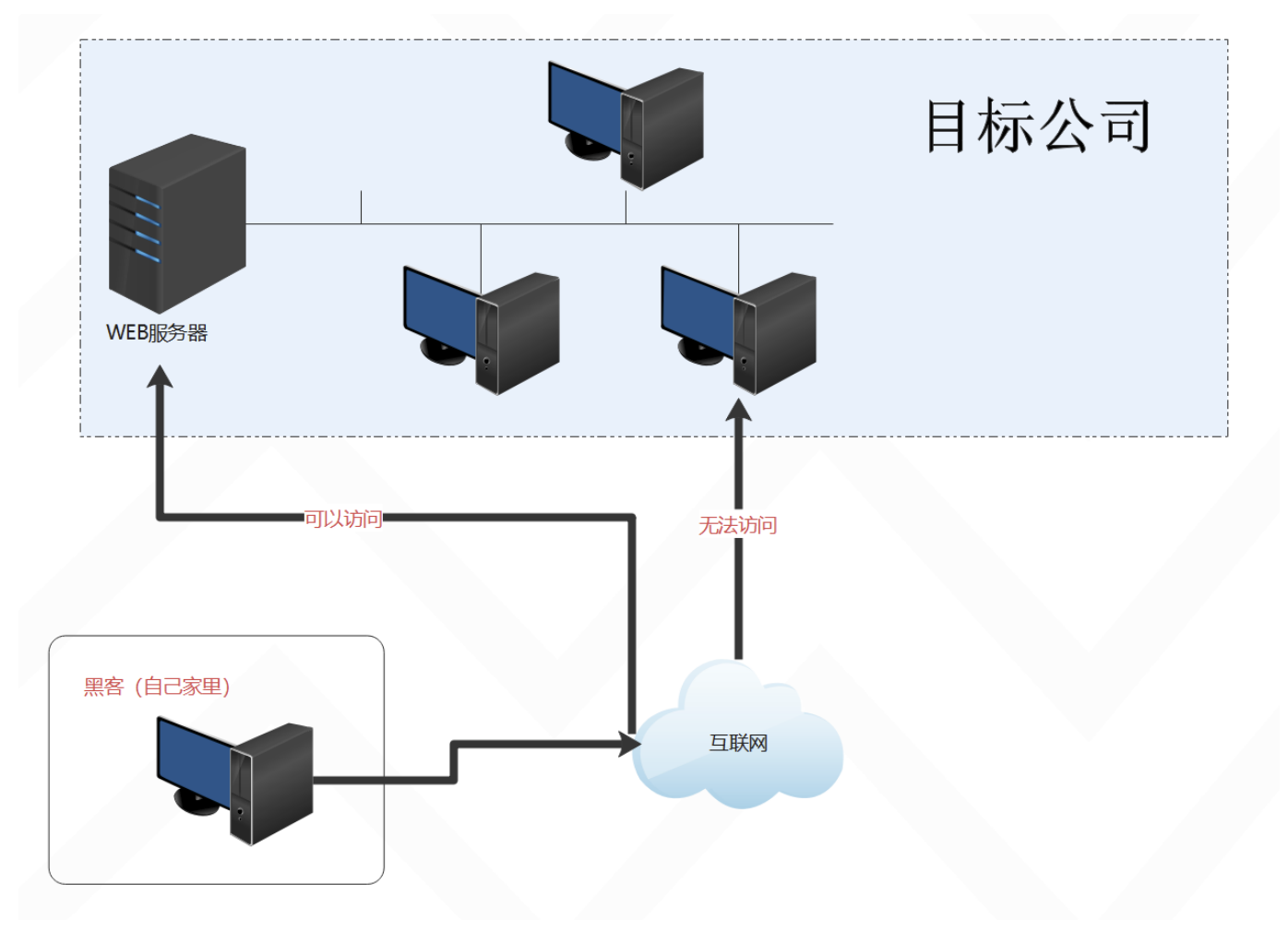
For example, many companies' OA systems require you to connect to the company's intranet network cable to access, or another example, when you work at home, you want to access the company's internal server, that is, access the intranet , the company usually gives you a VPN, and then you access the company's internal network through this VPN proxy to realize remote office
Of course, from the infiltrator's point of view, it is impossible for us to directly connect to the network cable of the company's intranet, and it is impossible to directly obtain the company's VPN server that can access the intranet (of course, you can also try to take down the The target company’s VPN server, through phishing, social work, etc., buys the company’s VPN server from the company’s internal employees... This is far away), usually, we look for loopholes on the company’s official website and take down the company’s Web server, and then further infiltrate the company's intranet through the Web server
In view of the above situation, how do we need to use tools to scan or detect the intranet?
1. Upload the tool directly to the web server, and use the tool on the web server to scan and detect the intranet
2. Put the scanning tool locally