1. SIT module function introduction
The SIT module supports two tunnel modes: ISATAP tunnel and 6to4 tunnel
Both ISATAP and 6to4 are relatively popular transition technologies for automatically establishing tunnels. Both can connect IPv6 isolated islands isolated by IPv4. Both of them embed IPv4 addresses into IPv6 addresses and encapsulate IPv6 packets in IPv4 for transmission. Extract the IPv4 address from the mutual communication to build a tunnel. However, the specific implementation process, IPv6 address and application range are not the same.
The full name of ISATAP is Intra-Site Automatic Tunnel Addressing Protocol, which sandwiches IPv4 addresses into IPv6 addresses. When two ISATAP hosts communicate, they can automatically extract IPv4 addresses and establish a tunnel to communicate without other channels. Special network equipment, as long as the IPv4 network between each other is unobstructed.
After the dual-stack host supports ISATAP, it will automatically generate a local link prefix (beginning with fe80::) and a 64-bit interface identifier::0:5EFE:XXXX (here XXXX is the IPv4 singleton of the dual-stack host) on the tunnel interface. Broadcast address), so that you can communicate with other ISATAP clients in the same subnet; if you need to communicate with ISATAP clients on other networks or IPv6 networks, you must obtain the global unicast address prefix (2001:, 2002:, 3ffe:), communicate with other IPv6 hosts and networks through routers.
The ISATAP transition technology does not require that the tunnel end node must have a globally unique IPv4 address, as long as the dual-stack host has an IPv4 unicast address, no matter whether the address is public or private.
The 6to4 ( RFC3056 ) mechanism is defined for IPv6 communication between sites. Each site must have at least one "6to4" router as the entrance and exit, using a special address format, the address prefix is (2002:), and the IPv4 address of the router Insert the IPv6 address, so when the hosts in different 6to4 sites communicate with each other, the IPv4 address can be automatically extracted to establish a tunnel between routers.
Through 6to4 router, hosts in different 6to4 sites can communicate with each other. When communicating with general IPv6 hosts, 6to4 relay router must be used. The 6to4 relay router must have both 6to4 and IPv6 interfaces, and provide packet forwarding for these interfaces.
6to4 needs a globally legal IPv4 address, so it doesn't help much to solve the shortage of IPv4 addresses. But it does not need to apply for an IPv6 address, through which the site can be quickly upgraded to IPv6
2. 6to4 tunnel construction
Connect the network according to the experiment diagram. The two firewalls are connected through a 6 to 4 tunnel. The global IPV4 address of the interface of FW1 is 202.205.88.55, and the IPV6 address prefix is: 2002:cacd:5837::/64, yes This address is then divided into subnets, set the sit1 interface to use 2002:cacd:5837:1::/64 and the eth1 interface connected to the PC to use the prefix 2002:cacd:5837:2::/64, and the eth0 interface of FW2 The global IPV4 address of port is 202.205.88.66, which is converted into the prefix of IPV6 2002:cacd:5842::/64, and the prefix of sit1 is set to 2002:cacd:5842::/64, while the eth1 interface is used to use 2002:cacd:5842 :2::/64.. The address configuration of each device in the figure is as follows:

| Firewall FW1 |
eth2 202.205.88.55/24 |
eth1 2002:cacd:5837:2::1/64 |
sit1 2002:cacd:5837:1::1/64 |
| Firewall FW2 |
eth1 202.205.88.66/24 |
eth2 2002:cacd:5842:2::1/64 |
sit1 2002:cacd:5842:1::1/64 |
| Host PC1 |
ens19 2002:cacd:5837:2::2/64 |
||
| Host PC2 |
ens19 2002:cacd:5842:2:2/:64 |
After creating the tunnel and configuring IP according to the above table, you must also configure a static route on the router to direct all other traffic destined for the IPv6 prefix 2002::/16 to the 6 to 4 tunnel interface.
1. The configuration on the firewall FW1 is as follows:
ifconfig eth2 add 202.205.88.55/24 //Configure the address of Eth2 of FW1
ifconfig eth1 add 2002:cacd:5837:2::1/64 //Configure the Eth1 address of FW1
echo "1">/proc/sys/net/ipv4/ip_forward ///Open route forwarding
echo "1" >/proc/sys/net/ipv6/conf/all/forwarding
insmod /lib64/modules/2.6.30-gentoo-r8/kernel/net/ipv4/tunnel4.ko
insmod /lib64/modules/2.6.30-gentoo-r8/kernel/net/ipv6/sit.ko
Ip tunnel add sit1 mode sit remote 202.205.88.66 local 202.205.88.55 //Establish a tunnel
ifconfig sit1 up //Activate the tunnel
ip -6 addr add 2002:cacd:5837:1::1/64 dev sit1
route –A inet6 add 2002::/16 sit1 //add IPV6 route
2. The configuration on the firewall FW2 is as follows:
ifconfig eth1 add 202.205.88.66/24 //Configure the address of Eth1 of FW2
ifconfig eth2 add 2002:cacd:5842:2::1/64 //Configure the Eth2 address of FW2
echo "1">/proc/sys/net/ipv4/ip_forward ///Open route forwarding
echo "1" >/proc/sys/net/ipv6/conf/all/forwarding
insmod /lib64/modules/2.6.30-gentoo-r8/kernel/net/ipv4/tunnel4.ko
insmod /lib64/modules/2.6.30-gentoo-r8/kernel/net/ipv6/sit.ko
ip tunnel add sit1 mode sit remote 202.205.88.55 local 202.205.88.66 //establish tunnel
ifconfig sit1 up //Activate the tunnel
ip -6 addr add 2002:cacd:5842:1::1/64 dev sit1
route –A inet6 add 2002::/16 sit1 //add IPV6 route
3. The settings on the host PC1 are as follows:
#ifconfig ens19 add 2002:cacd:5837:2::2/64
ip -6 route add 2002::/16 via 2002:cacd:5837:2::1 dev ens19
4. The settings on the host PC2 are as follows:
#ifconfig ens19 add 2002:cacd:5842:2:2/:64
ip -6 route add 2002::/16 via 2002:cacd:5842:2::1 dev ens19
3. Istatp tunnel construction
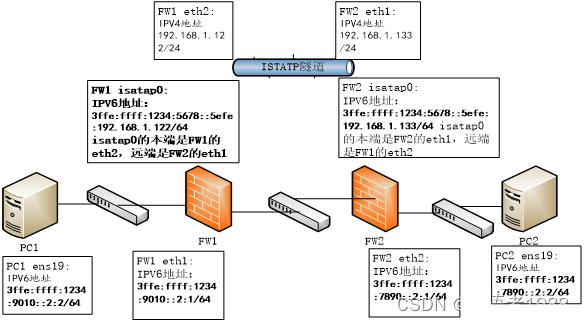
1. The configuration on the firewall FW1 is as follows:
ip addr add 192.168.1.122/24 dev eth2
//Configure the address of Eth2 of AF1
ip -6 addr add 3ffe:ffff:1234:9010::2:1/64 dev eth1 //Configure the Eth1 address of FW1
echo "1">/proc/sys/net/ipv4/ip_forward ///Open route forwarding
echo "1" >/proc/sys/net/ipv6/conf/all/forwarding
insmod /lib64/modules/2.6.30-gentoo-r8/kernel/net/ipv4/tunnel4.ko
insmod /lib64/modules/2.6.30-gentoo-r8/kernel/net/ipv6/sit.ko
ip tunnel add isatap0 mode isatap remote 192.168.1.133 local 192.168.1.122//establish tunnel
ip link set isatap0 up
echo "0" > /proc/sys/net/ipv6/conf/all/disable_ipv6
ip addr add 3ffe:ffff:1234:5678::5efe:192.168.1.122/64 dev isatap0
ip -6 route add 3ffe::/16 via 3ffe:ffff:1234:5678:0:5efe:c0a8:185 dev isatap0
ip -6 route del 3ffe:ffff:1234:5678::/64
2. The configuration on the firewall FW2 is as follows:
ip addr add 192.168.1.133/24 dev eth1
//Configure the address of Eth1 of FW2
ip -6 addr add 3ffe:ffff:1234:7890::2:1/64 dev eth2 //Configure the Eth2 address of FW2
echo "1">/proc/sys/net/ipv4/ip_forward ///Open route forwarding
echo "1" >/proc/sys/net/ipv6/conf/all/forwarding
insmod /lib64/modules/2.6.30-gentoo-r8/kernel/net/ipv4/tunnel4.ko
insmod /lib64/modules/2.6.30-gentoo-r8/kernel/net/ipv6/sit.ko
ip tunnel add isatap0 mode isatap remote 192.168.1.122 local 192.168.1.133 //establish tunnel
ip link set isatap0 up
echo "0" > /proc/sys/net/ipv6/conf/all/disable_ipv6
ip addr add 3ffe:ffff:1234:5678::5efe:192.168.1.133/64 dev isatap0
ip -6 route add 3ffe::/16 via 3ffe:ffff:1234:5678:0:5efe:c0a8:17a dev isatap0
ip -6 route del 3ffe:ffff:1234:5678::/64
3. Set as follows on the host PC1:
iptables -F
setenforce 0
#ifconfig ens19 add 3ffe:ffff:1234:9010::2:2/64
ip -6 route add 3ffe::/16 via 3ffe:ffff:1234:9010::2:1/64 dev ens19
- The settings on the host PC2 are as follows:
iptables -F
setenforce 0
#ifconfig ens19 add 3ffe:ffff:1234:7890::2:2/64
ip -6 route add 3ffe::/16 via 3ffe:ffff:1234:7890::2:1/64
dev ens19