A detailed description
The HTTP X-XSS-Protection response header is a feature of Internet Explorer, Chrome and Safari that stops the browser from loading a page when a cross-site scripting attack (XSS) is detected.
The absence of the X-XSS-Protection response header makes the target URL more vulnerable to cross-site scripting attacks.
Solution
Configure your server to send an "X-XSS-Protection" header with a value of "1" (e.g. enabled) on all outgoing requests. For Apache see:
http://httpd.apache.org/docs/2.2/mod/mod_headers.html
For IIS see:
https://technet.microsoft.com/pl-pl/library/cc753133%28v =ws.10%29.aspx
For nginx see:
http://nginx.org/en/docs/http/ngx_http_headers_module.html
combat
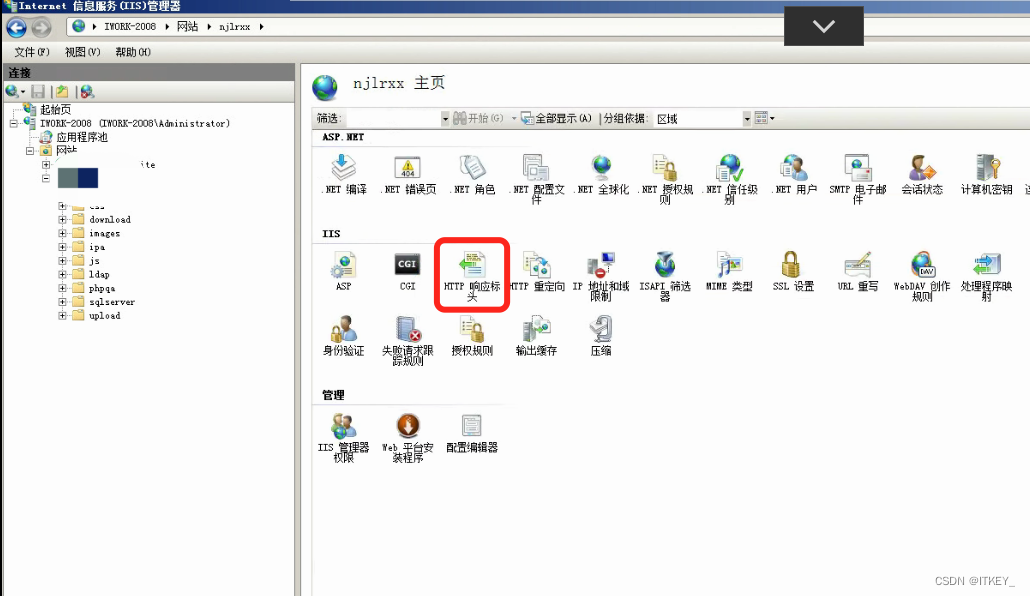
The solution under IIS
IIS solution
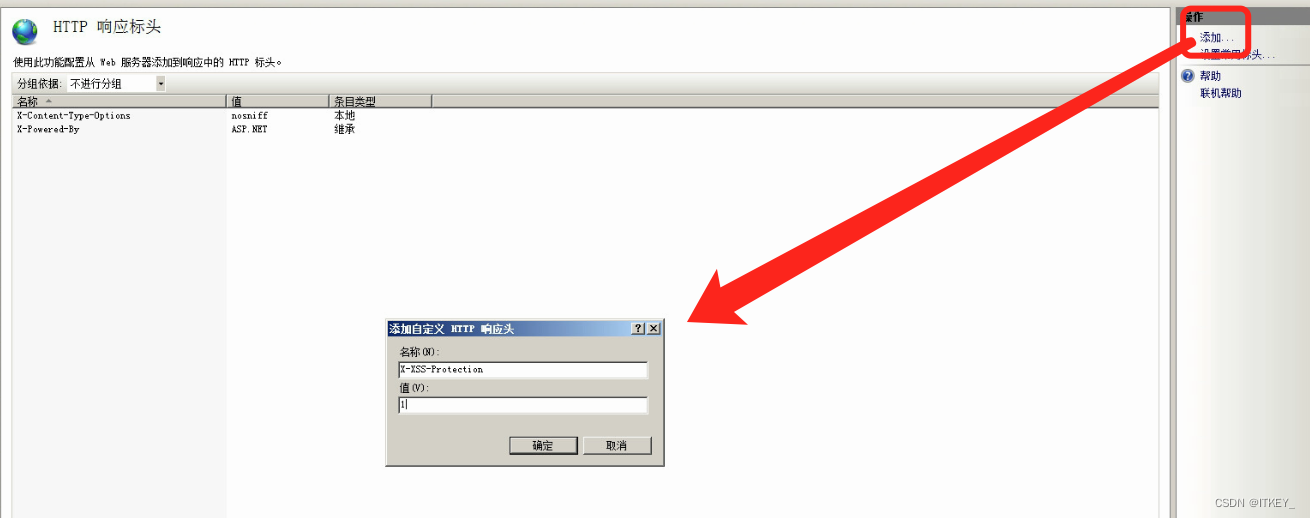
The operation method is as follows:
X-XSS-Protection = 1
Apache's solution
Skip it here, you can refer to:
https://blog.csdn.net/lxyoucan/article/details/131725900
Calibration method
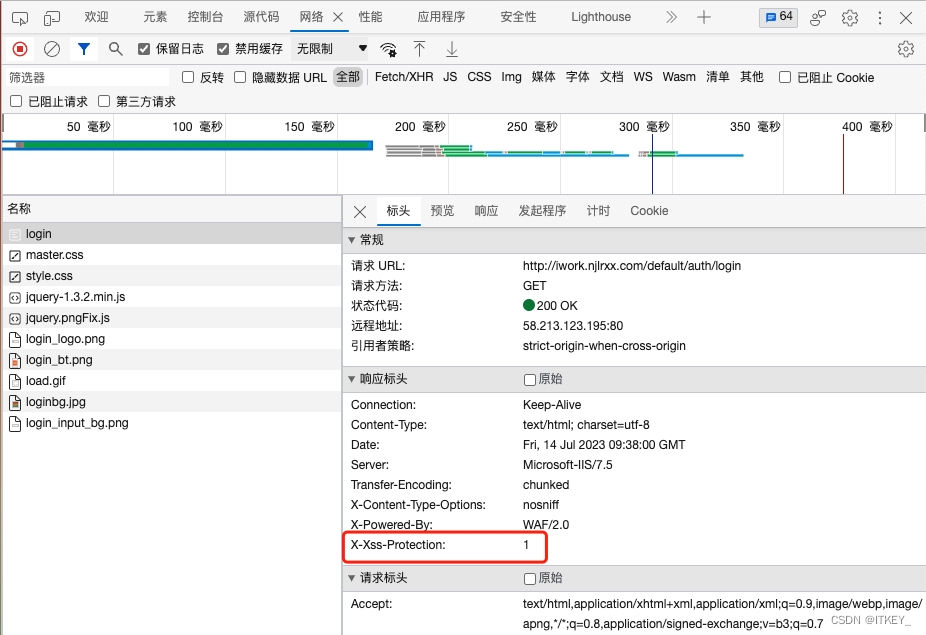
Browser F12, view the network request, as follows: