A detailed description
Web 服务器对于 HTTP 请求的响应头中缺少 Strict-Transport-Security,这将导致浏览器提供的安全特性失效。 当 Web 服务器的 HTTP 头中包含 Strict-Transport-Security 头时,浏览器将持续使用 HTTPS 来访问 Web 站点,可以用来对抗协议降级攻击和 Cookie 劫持攻击。
Its optional values are: max-age=SECONDS, indicating the effective time of this command in the future includeSubDomains, which can be used to specify whether to take effect on subdomains. Vulnerability hazard: The web server lacks Strict-Transport- Security, which will invalidate the security features provided by the browser, making it easier to be affected by web front-end hackers.
Solution
1) Modify the server program and add Strict-Transport-Security to the HTTP response header. If it is a java server, you can use the following method to add the HTTP response header response.setHeader(“Strict-Transport-Security”, “value”) If it is For the php server, you can use the following method to add the HTTP response header header(“Strict-Transport-Security: value”) If it is the asp server, you can use the following method to add the HTTP response header Response.AddHeader “Strict-Transport-Security”, “ value” If it is a python django server, you can use the following method to add an HTTP response header response = HttpResponse() response[“Strict-Transport-Security”] = “value” If it is a python flask server, you can use the following method to add an HTTP response Header response = make_response() response.headers[“Strict-Transport-Security”] = “value”;
2) Modify the load balancer or reverse proxy server, add Strict-Transport-Security to the HTTP response header if using Nginx, Tengine , Openresty, etc. as a proxy server, write the following content in the configuration file to add the HTTP response header: add_header Strict-Transport-Security value; If Apache is used as the proxy server, write the following content in the configuration file to add the HTTP response Header: Header add Strict-Transport-Security "value".
combat
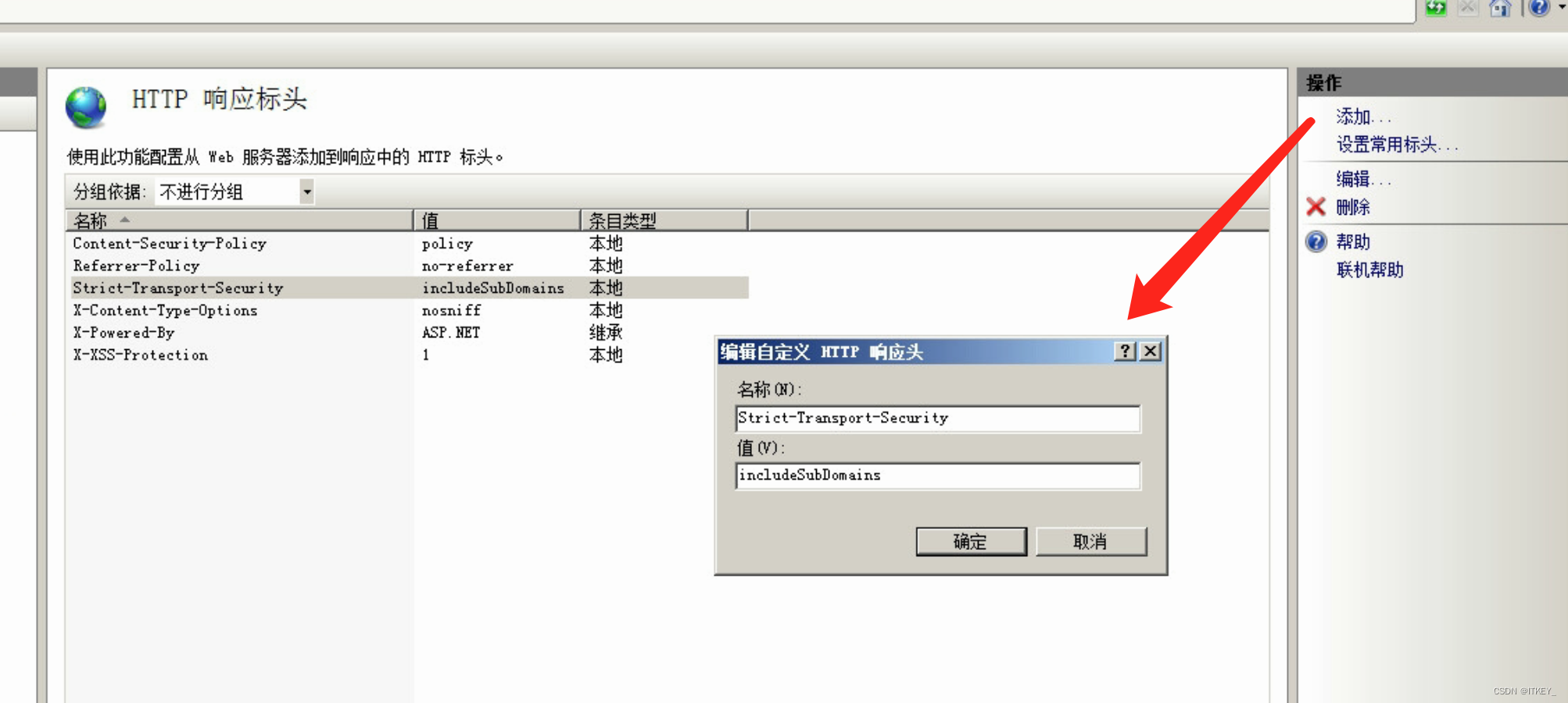
Strict-Transport-Security: includeSubDomains
specific reference:
https://blog.csdn.net/lxyoucan/article/details/131725900