Network layer
- 1 Overview
- 2. Two services provided by the network layer
- 3. IPv4 address and its application
- 4. The process of sending and forwarding IP datagrams
- 5. Routing
- 6. IPv4 datagram header format
- 7. Internet Control Message Protocol ICMP
- 8. Virtual Private Network VPN
- 9. Network Address Translation NAT
1 Overview
- Main tasks: realize network interconnection and complete the task of transmitting data packets between networks;
- The main problems to be solved:
1) What kind of service (reliable transmission/unreliable transmission) does the network layer provide to the transport layer;
2) Network layer addressing;
3) Routing selection; - The Internet is currently the most widely used Internet, using the TCP/IP protocol stack;
- The network layer in the TCP/IP protocol stack uses the Internet Protocol IP, so the network layer in the TCP/IP protocol stack is also called the Internet layer;
2. Two services provided by the network layer
- Connection-oriented virtual circuit services can provide connection-oriented reliable transmission services for the transport layer;
- Connectionless datagram service, which can provide connectionless and unreliable transmission services for the transport layer;
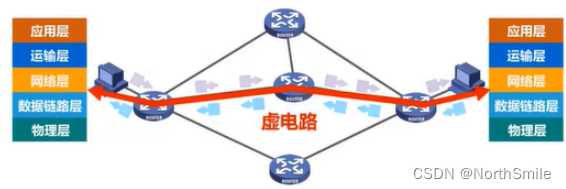
2.1 Connection-oriented virtual circuit service
- In this method, the reliable communication of the network is guaranteed by the network, and the network layer connection must be established before the communication between the two parties, and the virtual circuit connection must be released after the communication ends;
- The network layer connection is a logical connection, called virtual circuit VC (Virtual Circuit);
- Both communicating parties send packets along the established virtual circuit;
- The address of the destination host is only used when establishing a virtual circuit connection, and then the header of each packet only needs to carry a virtual circuit number;
- Combined with reliable transmission network protocols, it can provide connection-oriented reliable transmission services to the transport layer;
- Many wide-area packet-switched networks use connection-oriented virtual circuit services;
2.2 Connectionless Datagram Service
- This method believes that the reliable communication of the network should be guaranteed by the communication host, and the communication between the two parties does not need to establish a network layer connection;
- The network itself does not provide reliable transmission services;
- Packets can take different paths through the routing mechanism;
- Each packet must provide the complete destination host address;
- This communication method may have packet error, loss, repetition and out-of-sequence problems;
- The Internet design uses connectionless datagram services, placing complex network processing functions at the edge of the Internet (user hosts and transport layers);
- The network layer delivers datagrams on a best-effort basis;

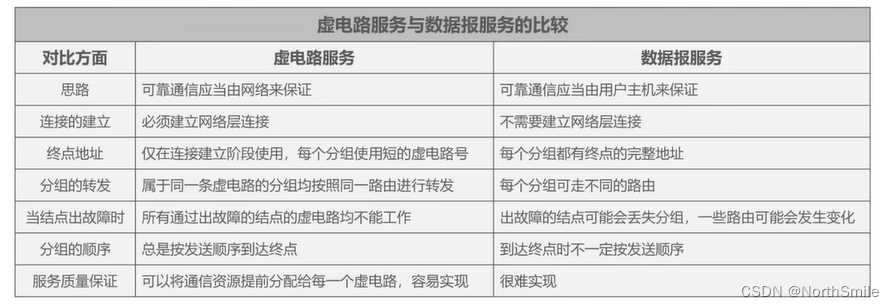
2.3 Virtual Circuit Service VS Datagram Service
3. IPv4 address and its application
- IP addresses are assigned by ICANN (Internet Corporation for Assigned Names and Numbers);
- An IPv4 address is a unique identifier assigned to each interface of each host (or router) on the Internet;
- The IPv4 address is 32 bits;
- The IPv4 address is expressed in dotted decimal notation, such as abcd, where every 8 bits represent a number;
- The dotted decimal method represents the IP address, which involves the conversion between binary and decimal;
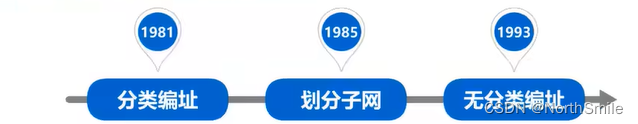
- The IPv4 addressing method has gone through three historical stages:
3.1 Classified addressing IPv4 addresses
- Divide IP addresses into the following five categories:

- Only A/B/C class addresses can be assigned to each interface of the host or router in the network;
- The address whose host number is all 0 is a network address, which cannot be assigned to each interface of the host or router in the network;
- The address with the host number of all 1s is a broadcast address, which cannot be assigned to each interface of the host or router in the network;
3.1.1 Class A address
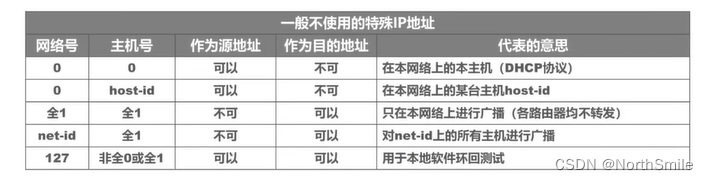
- Remember that in class A addresses, except for the IP addresses with all 0s and all 1s, which cannot be assigned to hosts, IP addresses with network numbers 0 and 127 cannot be assigned;
- The IP whose network number is 0 is a reserved network and cannot be allocated;
- The IP with network number 127 is a local loopback test network and cannot be assigned;

3.1.2 Class B address
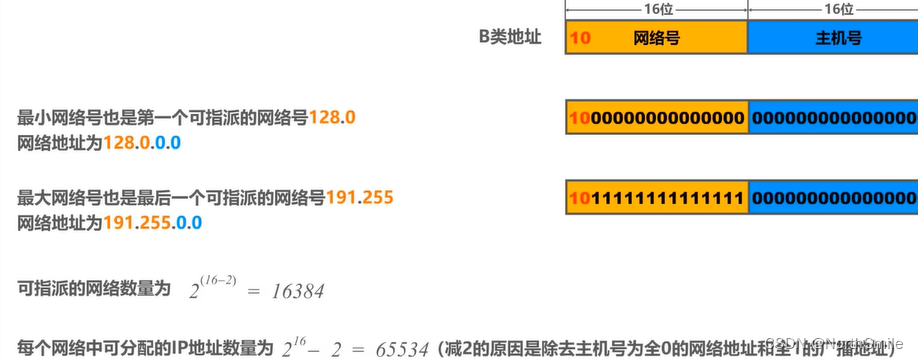
3.1.3 Class C address
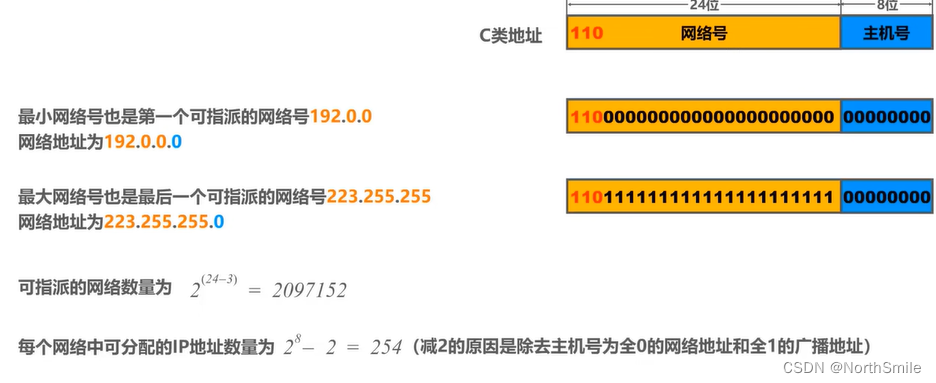
3.2 IPv4 addresses for subnetting
- On the classified addressing IPv4 address, the subnet number is introduced to divide the subnet;
- The subnet number occupies part of the host number ;
- Using a 32-bit subnet mask can indicate how many bits are used as the subnet number for the host number in the classified IP address;
- The subnet mask uses continuous bit 1 to correspond to the network number and subnet number, and uses continuous bit 0 to correspond to the host number ;
- The subnet network address where the IP address is located can be obtained by doing a logical AND operation on the subnet mask and the IP address ;
- The default subnet mask refers to the subnet mask used when no subnet is divided . For example, the default subnet mask corresponding to a class A address is 255.0.0.0;
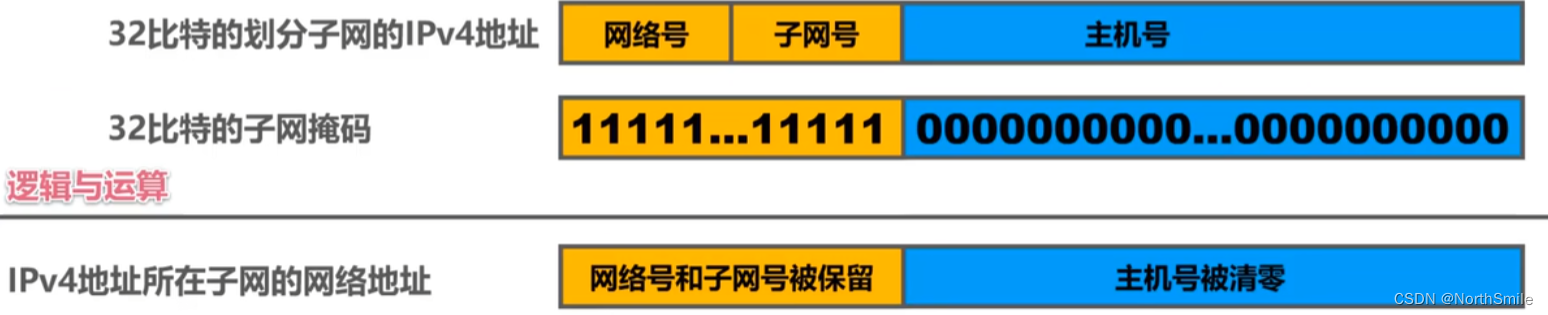
3.3 IPv4 addresses without classful addressing
- Use classless inter-domain routing to select CIDR (Classless Inter-Domain Routing) for classless addressing;
- CIDR eliminates the traditional concept of classifying addresses and the concept of subnetting ;
- CIDR can allocate IPv4 address space more effectively ;
- CIDR uses slash notation , add a slash / after the IPv4 address , and indicate the number of bits occupied by the network prefix after the slash , such as 128.14.35.7/20;
- CIDR is actually a CIDR address block composed of consecutive IP addresses with the same network prefix ;

- CIDR can achieve route aggregation, that is, construct a supernet: find the common network prefix of multiple routes, and express it as an aggregated address block ;
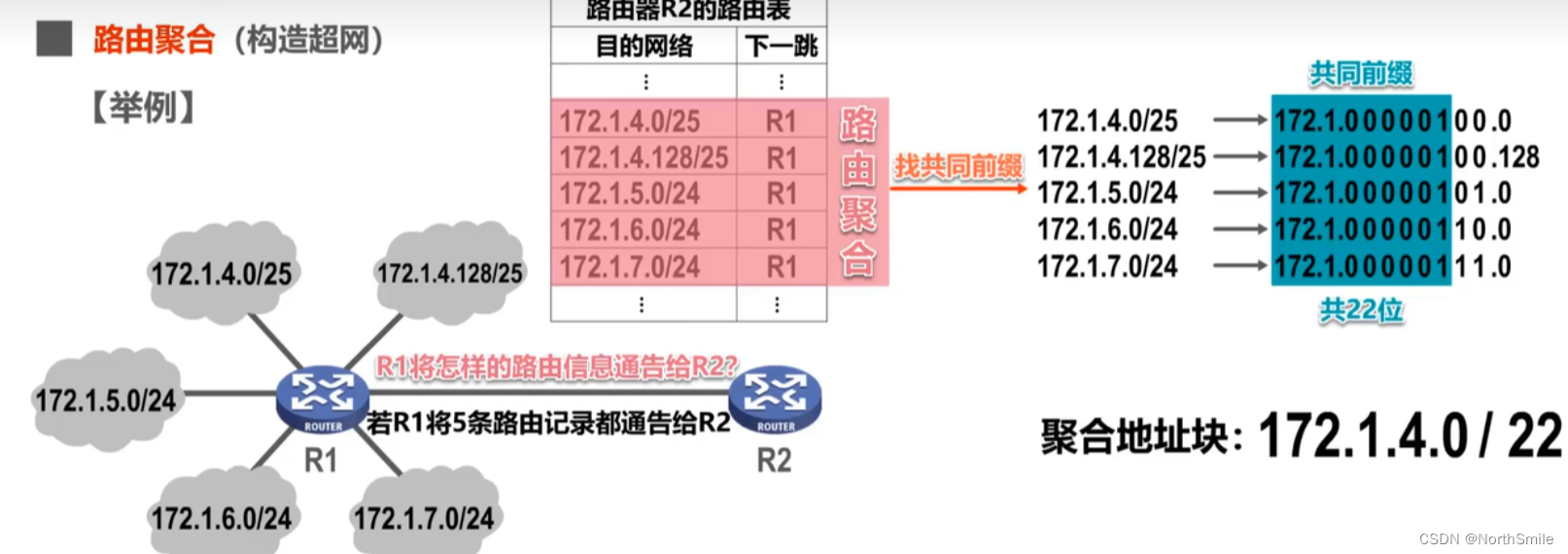
- The longer the network prefix, the smaller the address block and the more specific the route ;
- If there are multiple routes to choose from when the router looks up the table and forwards packets, the route with the longest network prefix is selected according to the longest prefix matching principle ;
3.4 Application Planning of IPv4 Addresses
- The method of subnetting can be used to make full use of IP addresses to avoid waste of IP addresses;
- Subnetting is achieved by using some bits in the host number as the subnet number;
- Using the subnet mask can indicate how many bits are used as the subnet number for the host number in the IP address;
- Subnets can be divided using fixed-length subnet mask FLSM (Fixed Length Subnet Mask) and variable-length subnet mask VLSM (Variable Length Subnet Mask);

4. The process of sending and forwarding IP datagrams
- The process of sending and forwarding IP datagrams involves: 1) the source host sends IP datagrams; 2) routers forward IP datagrams;
- When communicating with hosts in the same network, IP datagrams are delivered directly;
- When hosts in different networks communicate, IP datagrams are delivered indirectly and need to be forwarded by routers;
- The router isolates the broadcast domain and will not forward any broadcast IP datagrams;
- Only hosts in this network will receive broadcast IP datagrams;
- If the user host wants to communicate with other networks, it needs to configure a router to forward datagrams, which is called the default gateway;
- By ANDing the subnet mask corresponding to the destination address and the source address, it is judged whether the two hosts are in the same network;
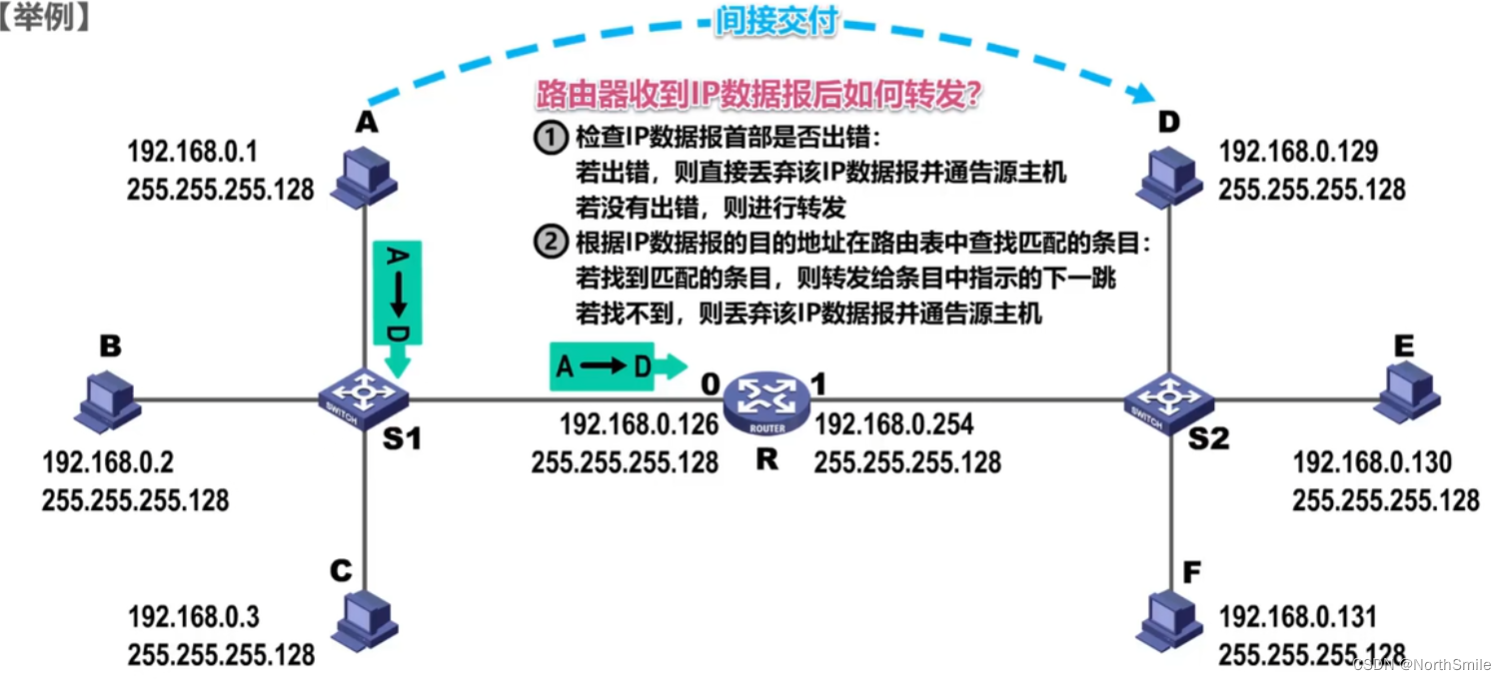

5. Routing
- Routing methods are divided into: 1) static routing; 2) dynamic routing;
- Types of routing entries: 1) Directly connected network; 2) Static routing (manual configuration); 3) Dynamic routing (routing protocol);
- When multiple routes are available in the routing table, use the longest prefix matching principle (the longer the network prefix, the more specific the route)! !
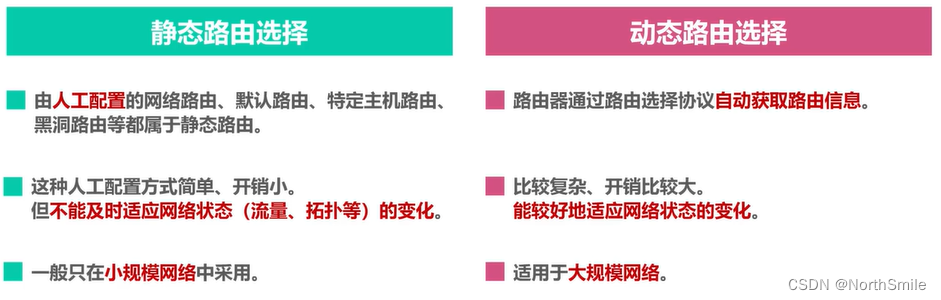
5.1 Static routing selection
- Static routing means that users or network administrators use related commands to manually configure routing tables;
- The manual configuration method is simple and has low overhead, but it cannot adapt to changes in network status (traffic, topology) in time;
- Suitable for small-scale networks;
- The manual configuration method may lead to routing loop problems. The reasons for routing loops are: 1) routing configuration errors; 2) aggregation of non-existing networks; 3) network failures;
- Special static route entries:
1) Default route (destination address is 0.0.0.0, address mask is 0.0.0.0), if no suitable forwarding route is found in the routing table, the default route will be used; 2)
Black hole route (below One hop is null0): the virtual interface inside the router, indicating that the IP datagram is discarded;
3) Specific host routing (the destination address is the specific host IP address, and the address mask is 255.255.255.255): indicates the detailed route to the specific host ;
5.1.1 How to solve the routing loop problem
- Routing loop: Routing in different routers forms a loop, and IP datagrams are forwarded circularly in the routing loop;
5.1.1.1 Routing configuration error
- When manually configuring the routing table, the routes in different routers are incorrectly configured, and these routes form a routing loop;
- Solution: Set the time-to-live TTL field in the header of the IP datagram. When the IP datagram arrives at the router, TTL-=1. If TTL!=0 at this time, the IP datagram will be forwarded, otherwise it will be discarded;
5.1.1.2 Aggregating non-existing networks
- The route aggregation operation can be performed by extracting the common prefix in the routing table, but the aggregation of non-existent networks combined with the default route leads to routing loops;
- Solution: Configure the corresponding black hole route for the non-existent network address in the routing table;
5.1.1.3 Network failure
- A network failure causes the corresponding route in the routing table to be deleted, and then the default route is used to cause a routing loop;
- Solution: Configure the corresponding black hole route for the faulty network in the routing table;
5.2 Dynamic Routing Selection
- Dynamic routing means that routers automatically obtain routing information through routing protocols;
- The dynamic acquisition method is complex and expensive, but it can adapt to changes in network status (traffic, topology) in a timely manner;
- Suitable for large-scale networks;
5.2.1 Routing Protocols
- Features:
1) Adaptive: Dynamic routing selection, which can adapt to the change of network status in time;
2) Distributed: Each router on the network jointly completes the acquisition and update of routing information through mutual information interaction;
3) Hierarchical: The entire Internet can be divided into many smaller autonomous systems AS (Autonomous System); - Intra-AS routing is called intra-domain routing, using the interior gateway protocol IGP or IRP;
- Inter-AS routing is called inter-domain routing, using the Exterior Gateway Protocol EGP or ERP
5.2.2 Common Routing Protocols

5.2.3 Router structure
- The basic mechanism of the router is divided into: 1) routing selection part; 2) packet forwarding part;
- Routing protocols run on routers;
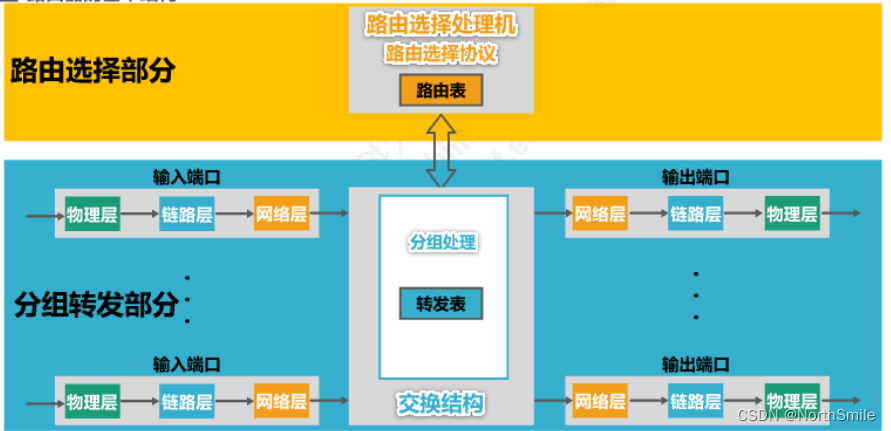
5.2.3.1 Routing section
- Core components: routing processor;
- Function: According to the routing protocol used by itself, it periodically exchanges routing information with other routers to complete routing table updates;
5.2.3.2 Packet forwarding part
- Forwarding content: 1) Routing message; 2) Ordinary data packet;
- Constructed by three parts: 1) switch fabric; 2) input port; 3) output port;
- Ordinary data packets are forwarded or discarded according to the content of the forwarding table; the routing message is sent to the routing processor, and the routing table is updated according to the content of the message;
- The content of the forwarding table comes from the routing table, which includes the destination network and the next hop address;
- The input port has an input buffer, which is used to temporarily store packets that enter the router but is too late to process; the output port has an output buffer, which is used to temporarily store packets that have been processed but are not yet sent;
5.3 Static Routing VS Dynamic Routing
5.4 Routing Information Protocol RIP
- RIP:Routing Information Protocol;
- RIP is based on distance vectors;
- RIP requires that each router in the autonomous system AS must record the distance between the router itself and other networks in the AS. This group of distances is called the distance vector DV (Distance-Vector);
- RIP uses the number of hops to measure the distance from the router to the destination network:
1) Directly connected network: the distance is 1;
2) Non-directly connected network: the distance is the number of intermediate routers + 1;
3) RIP limits a path to contain up to 15 routers, that is, the maximum distance is 15, and when the distance is 16, it is equivalent to being unreachable ; - RIP is only suitable for small Internet;
- RIP prefers the "short distance" route, that is, the route with the least number of routers. If there are multiple equal-cost routes (equal distances), RIP will perform equal-cost load balancing to evenly distribute traffic to multiple equal-cost routes;
- There are three main points involved in RIP:
1) Exchanging information only with adjacent routers;
2) Exchanging routing table information;
3) Periodic exchange;
5.4.1 Working principle
-
work process:
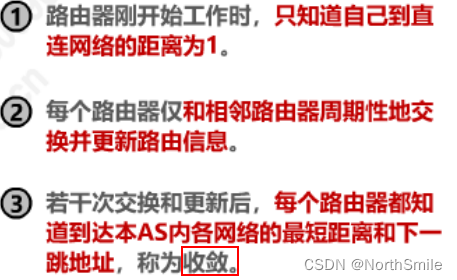
-
Routing table update principle: After router B receives the routing table information of neighboring router A, it updates the routing table information sent by A: ①The next hop is set to A; 2) The distance is increased by 1;

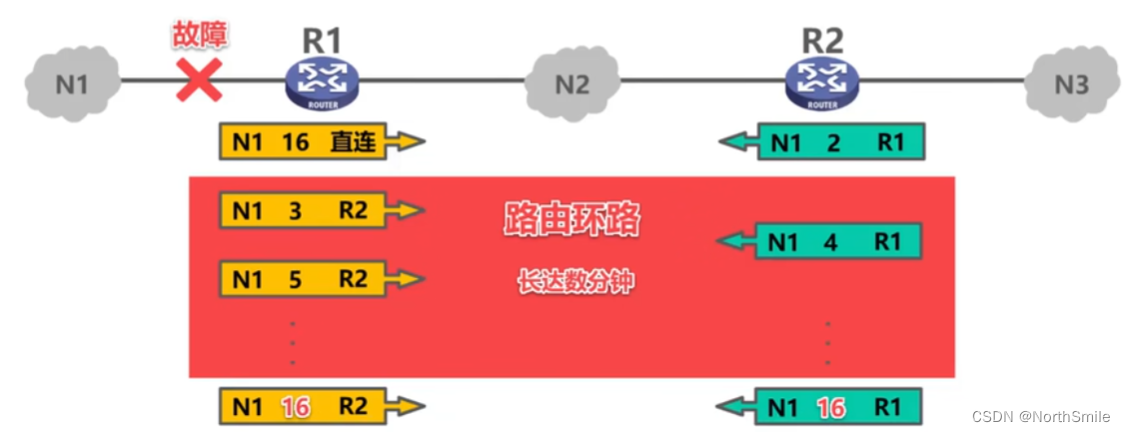
5.4.2 "Bad news is slow to travel" problem
- The "slow delivery of bad news" problem, also known as the routing loop or the distance counting to infinity problem , is an inherent problem with distance vector algorithms;
- RIP is based on distance vectors, so there is a problem of "slow transmission of bad news";
- The following methods can be used to alleviate the problem of "slow transmission of bad news":
1) Limit the maximum path distance to 15 , 16 means unreachable;
2) Send an update message (" triggered update ") immediately when the routing table changes, instead of periodically
3) Let the router record the interface that received a specific routing information, and prevent the routing information from being transmitted in the opposite direction through the interface (“ horizontal split ”);
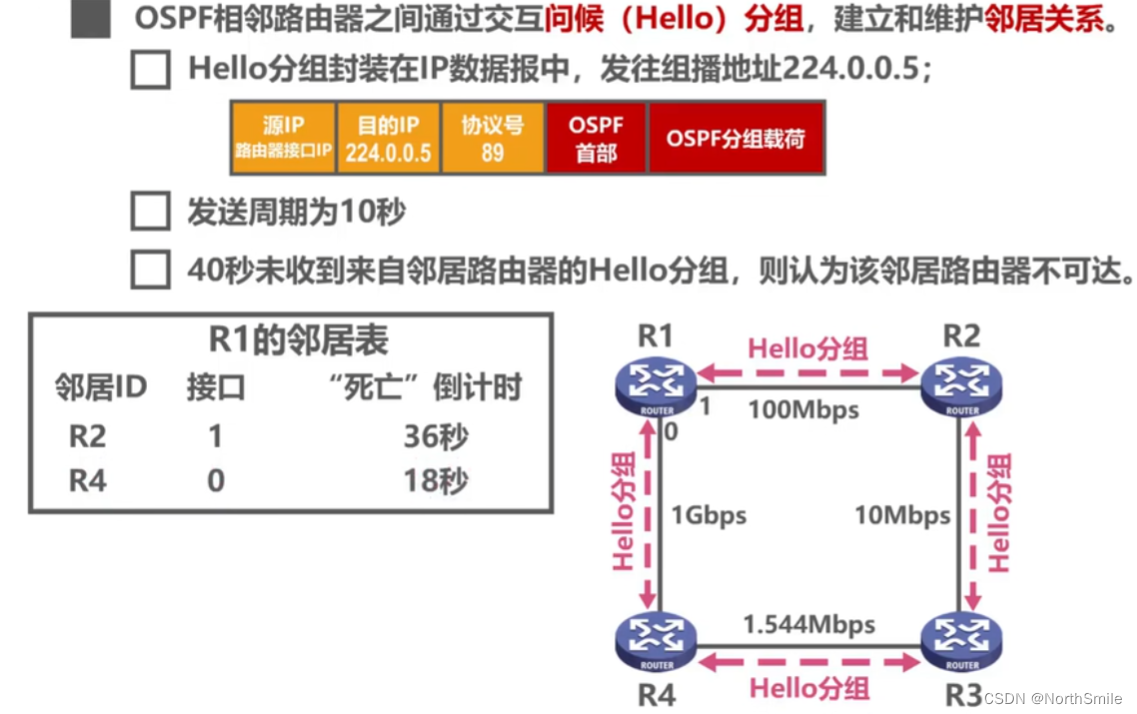
5.5 Open Shortest Path First Protocol OSPF
- OSPF:Open Shortest Path First;
- The underlying implementation is based on the shortest path algorithm SPF based on weighted directed graph proposed by Dijkstra ;
- OSPF is based on the link state and solves the shortcomings of RIP;
- OSPF uses the SPF algorithm to calculate routes, which guarantees that there will be no routing loops from the algorithm;
- OSPF does not limit the network scale, is widely used, has high update efficiency and fast convergence speed;
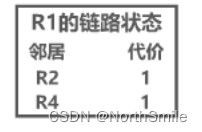
- The link state refers to which routers are adjacent to the router, and the "cost" of the link. "Cost" means cost, distance, etc., defined by the network manager; for example:
5.5.1 Basic working principle
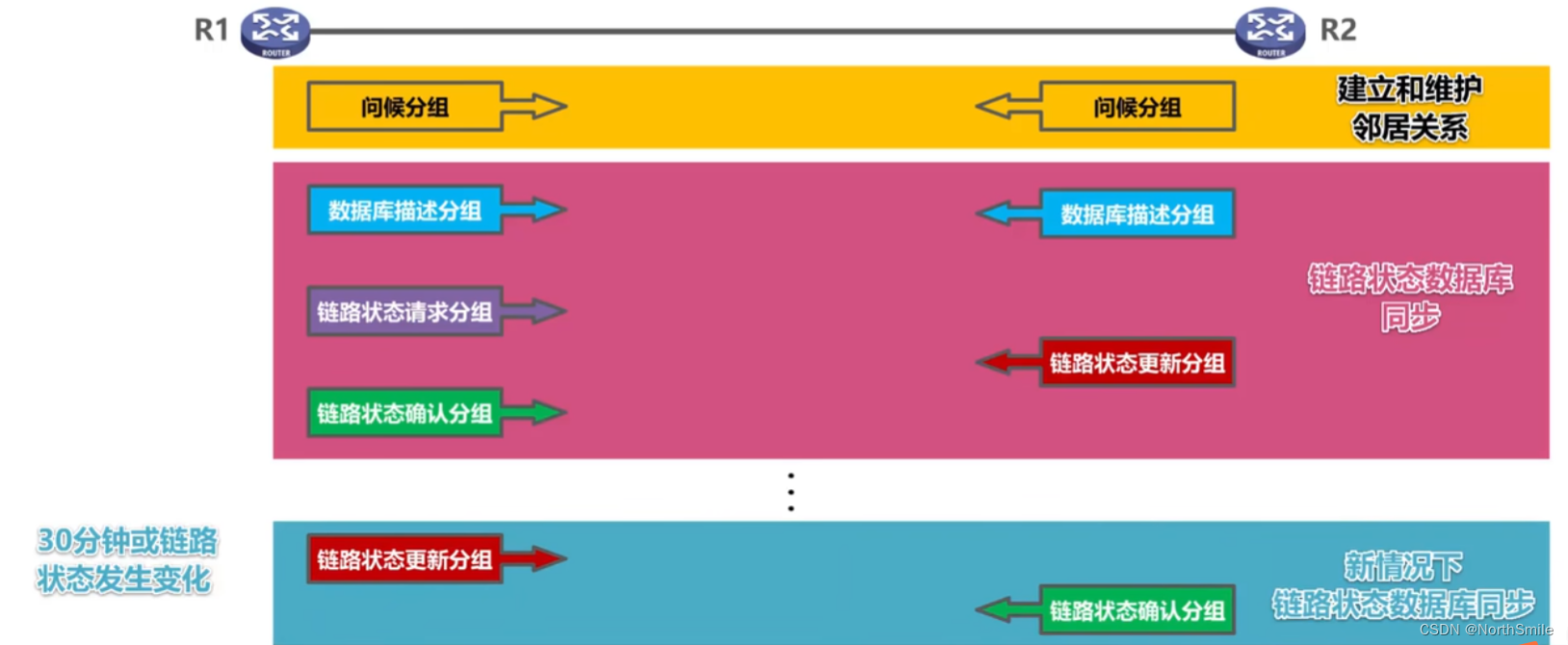
- Each router will establish and maintain its own neighbor table and maintain neighbor relationships ;
- LSU will be forwarded by all interfaces of the router, so routers in an autonomous system AS will eventually record the link state advertisement LSA of all routers ;


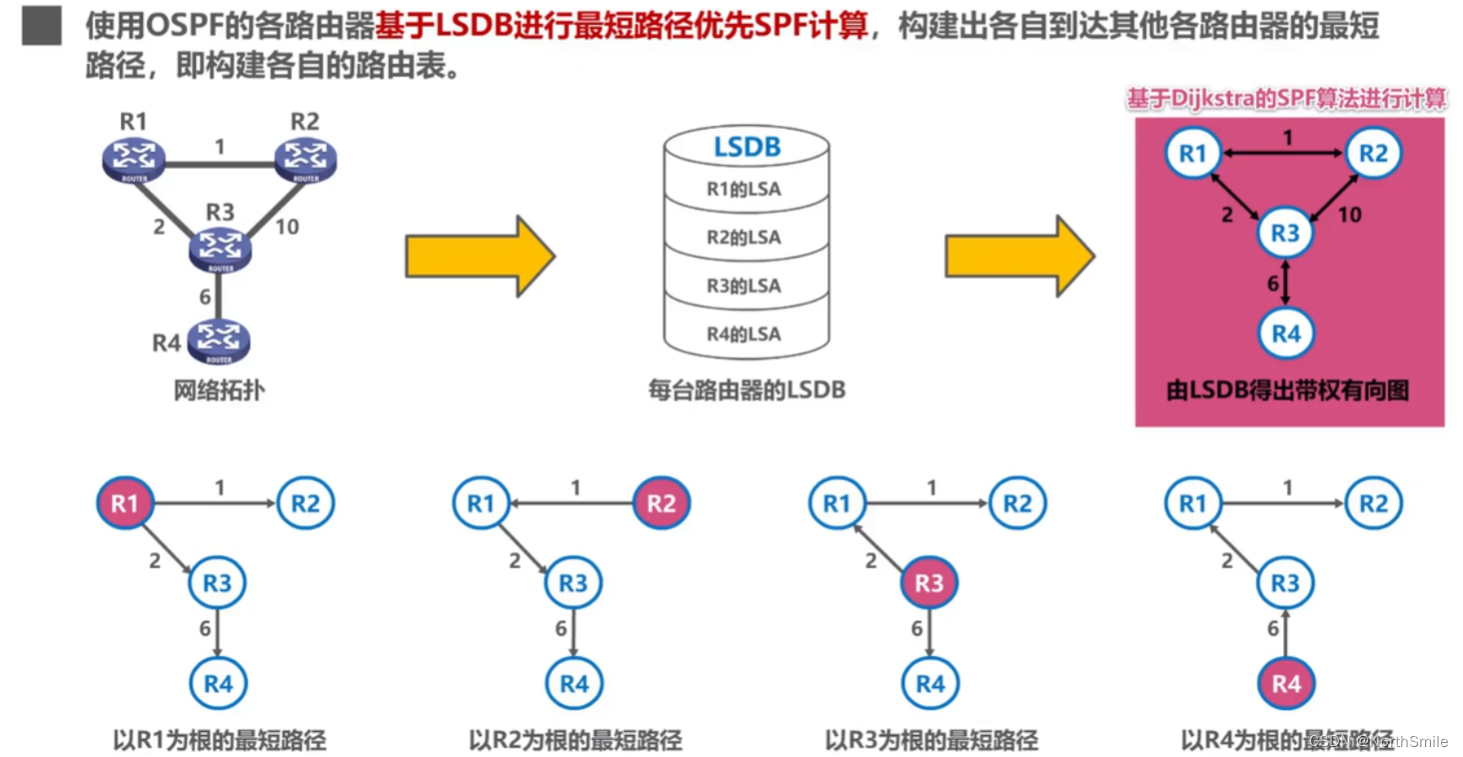
5.5.2 Five groups of OSPF

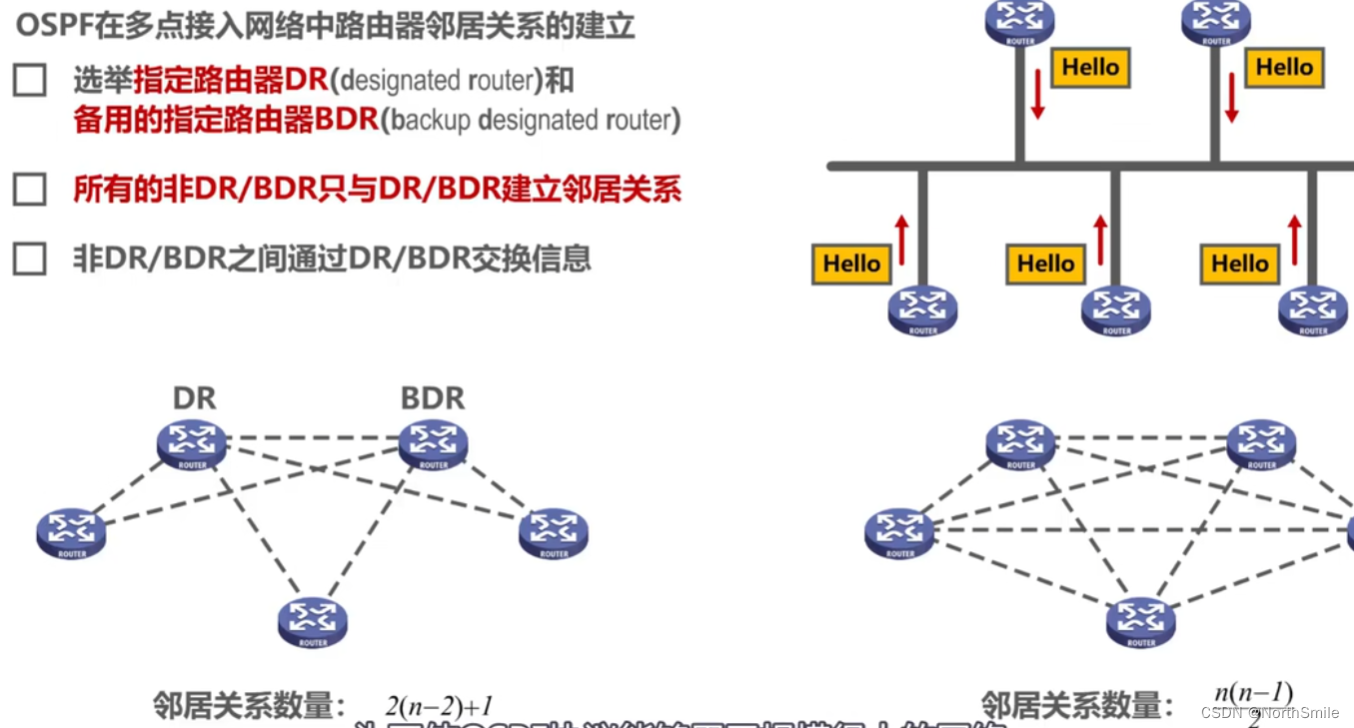
5.5.3 OSPF Establishment of Neighbor Relationships in Multipoint Access Networks
- Purpose: to reduce the number of packets sent by routers;
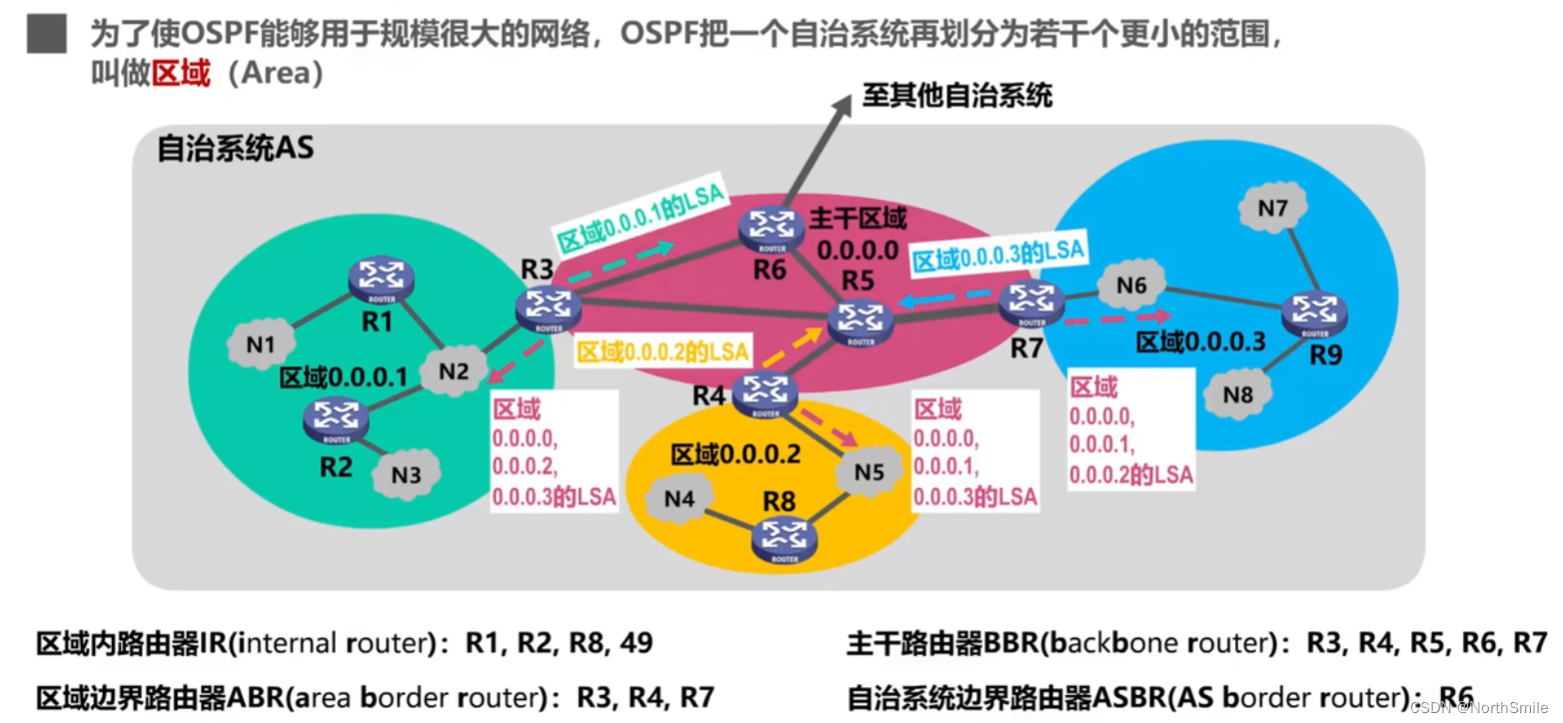
5.5.4 OSPF Divides an AS into Multiple Areas
- Purpose: To make OSPF suitable for larger networks;
5.6 Border Gateway Protocol BGP
- BGP is an inter-domain routing protocol, and cannot calculate the shortest path by measuring the "cost" to determine the optimal route;
- BGP is applied to routing selection between different AS (autonomous systems), and relevant strategies (such as politics, economy, security, etc.) need to be considered;
- The purpose of BGP is to determine a better route that can reach the destination network (it will not go around and send routing loops), not the best route;
- BGP is suitable for the Internet with multi-level structure;
5.6.1 Basic working principle
-
When configuring BGP, the administrator of each autonomous system needs to select at least one router as the "BGP spokesperson" ;
-
BGP speakers of different autonomous systems need to exchange routing information. First, establish a TCP connection with port number 179 :
1) Exchange BGP packets on this TCP connection to establish a BGP session;
2) Use the BGP session to exchange routing information;
3) Use The two BGP speakers that are connected by TCP to exchange routing information are neighbors or peers of each other ; -
In addition to running BGP, the BGP speaker also runs the routing protocol RIP used in the autonomous system;
-
BGP speakers exchange information about network reachability (a series of autonomous systems to reach a certain network);
-
After the BGP speakers exchange network reachability messages with each other, each BGP speaker finds a better route to each autonomous system from the received routing information according to the strategy adopted (that is, constructs a tree structure, does not exist autonomous system connectivity graph for loops ).

-
BGP only exchanges the complete BGP routing table between neighboring stations during the initial operation, and then only exchanges the changed part of the routing table, which can save network bandwidth and reduce the processing overhead of routers ;
5.6.2 Four types of packets of BGP

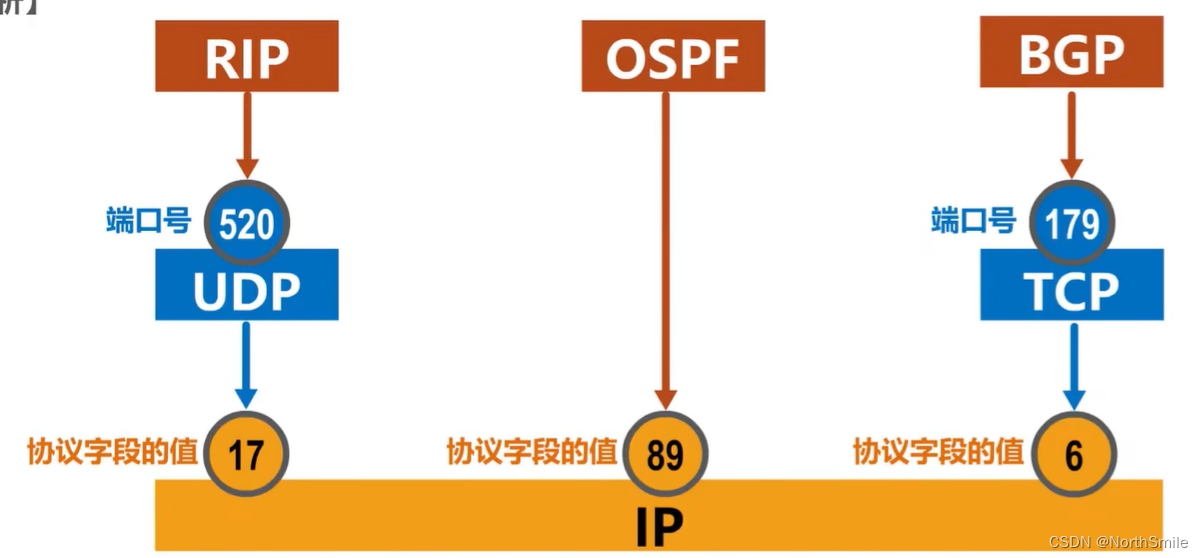
5.7 Protocols for encapsulating packets of different routing protocols
6. IPv4 datagram header format
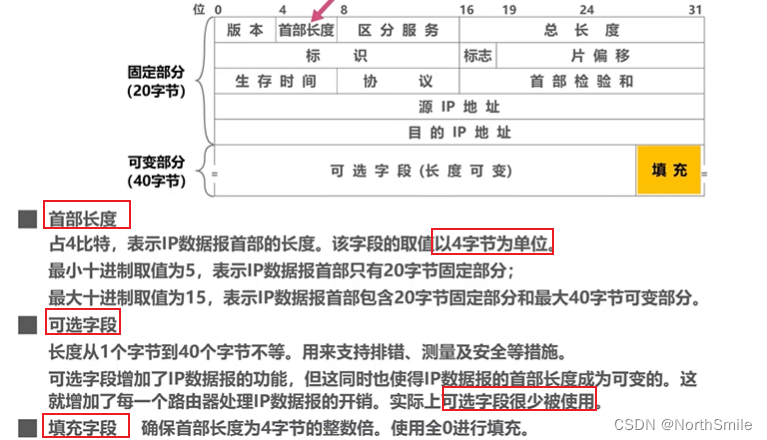



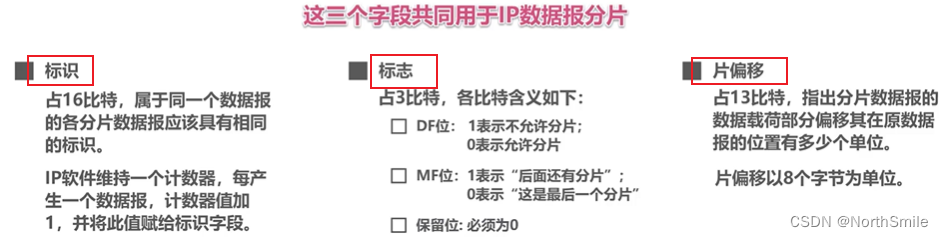
- TTL can prevent the IP datagram from permanently circling in the network (routing loop): the router will reduce the value of the TTL field in the IP datagram header by 1, if it is 0, it will be discarded, otherwise the datagram will be forwarded!

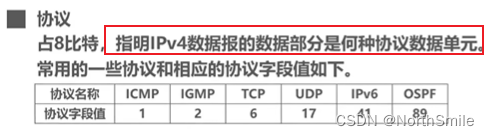
- The header checksum only performs error detection on the header of the datagram ;


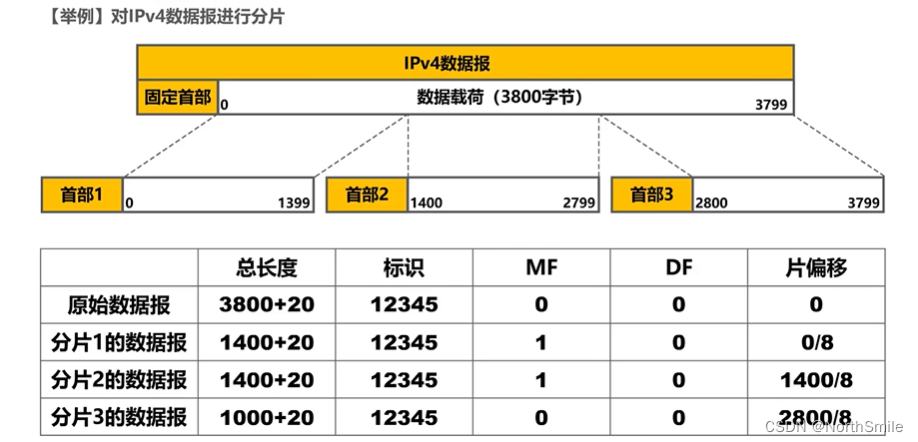
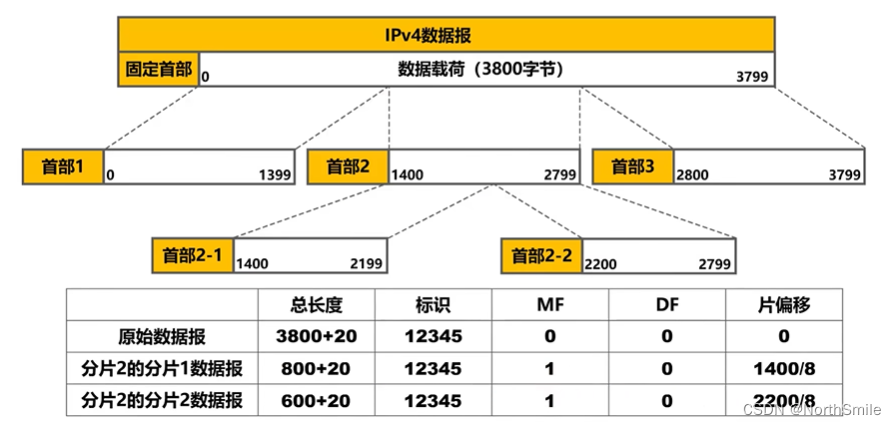
6.1 IP datagram fragmentation
- The data link layer encapsulates IP datagrams into frames, but the data payload part of the frame has a size limit (MTU), so too large IP datagrams will be divided into multiple small datagrams and then encapsulated into frames separately, and then to transmit;
7. Internet Control Message Protocol ICMP
- ICMP:Internet Control Message Protocol;
- Purpose: To forward IP datagrams more efficiently and improve the chances of successful delivery;
- Hosts or routers use ICMP to send error report messages and query messages ;
- ICMP messages are encapsulated and sent in IP datagrams ;
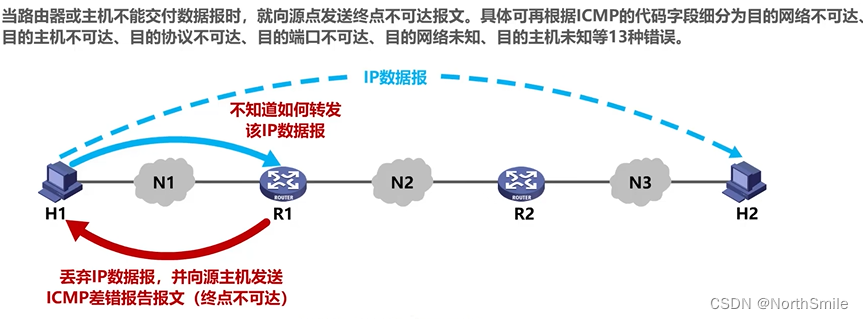
7.1 Five types of ICMP error report messages
-
1) The end point is unreachable :
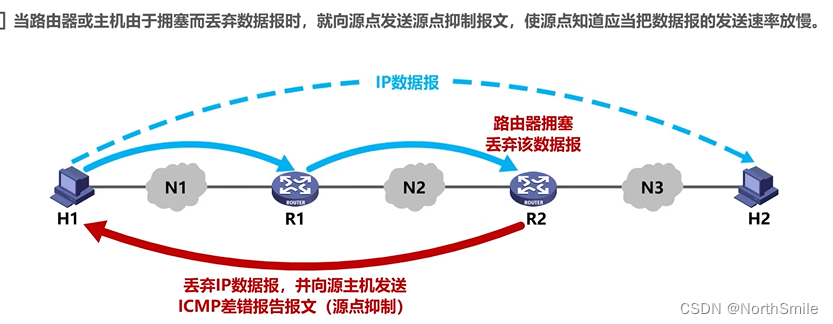
-
2) Source suppression :
-
3) The time exceeds :


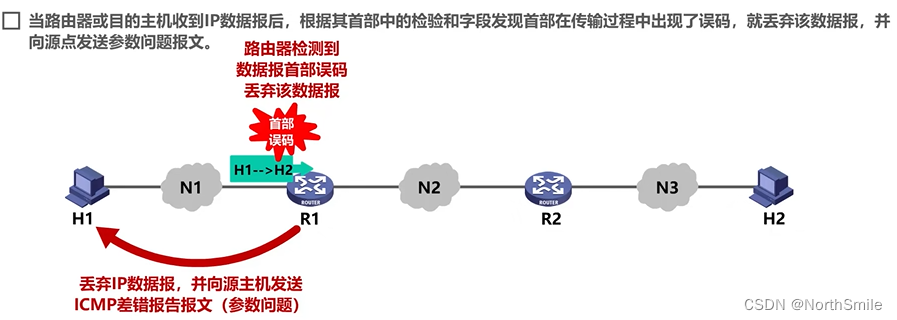
-
4) Parameter problem :
-
5) Change the route :
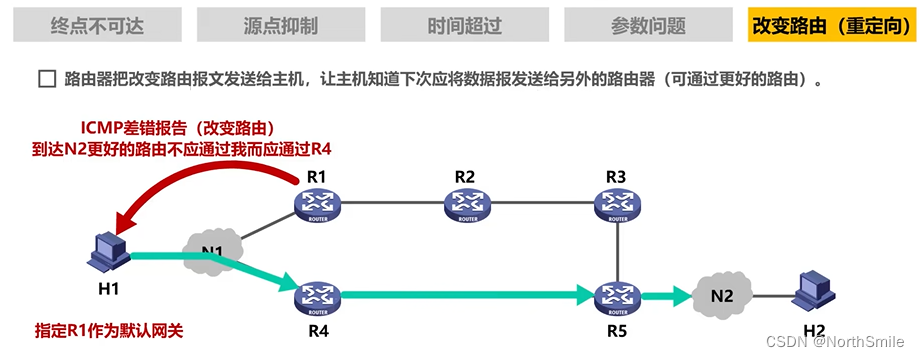
7.2 Situations when ICMP Error Report messages should not be sent

7.3 Two commonly used ICMP query messages

7.4 ICMP Application
- 1) Packet network detection PING: test the connectivity between the local machine and the destination host;
- 2) traceroute: check which routers the host needs to pass through to send datagrams to the destination host;
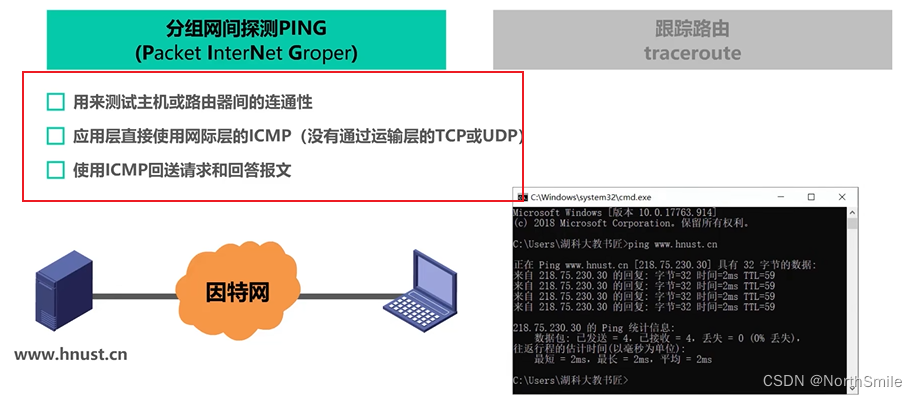
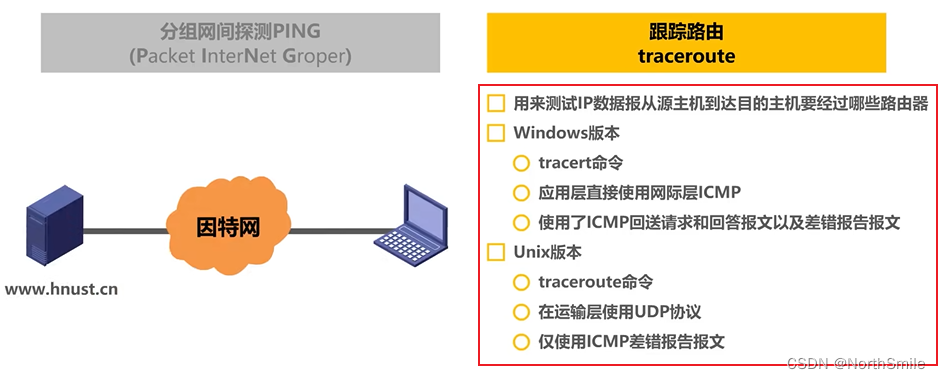
8. Virtual Private Network VPN
-
VPN:Virtual Private Network;
-
Virtual private network: use the public Internet as the communication carrier between the private networks of the organization , such a private network is called a virtual private network ;
-
The number of IP addresses that an organization can apply for is much smaller than the number of hosts in the organization, so the addresses allocated by each host in the virtual private network should be private addresses that can be freely assigned by the organization (no application required, non-public address) ,like:
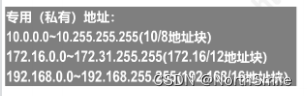
-
Classification of virtual private network:
1) Intranet VPN: a virtual private network composed of internal networks of different departments within the same organization;
2) Extranet VPN: sometimes an organization's VPN requires the participation of some external organizations, such a VPN is called Extranet VPN;
3) Remote access VPN: When employees want to access the company's private network outside, as long as the PC is connected to the Internet and runs the VPN software in the PC, a VPN tunnel can be established between the PC and the company host, and then Access to resources in the private network, this kind of VPN is called remote access VPN; -
The basic process of communication between private network A and B (at least one router in the private network has a legal global IP address):
1) The host in A encapsulates the data into an internal IP datagram and sends it to router R1;
2) Router R1 communicates with the internal The IP datagram is encrypted, and the encrypted IP datagram is sent using the public address of the router as the new source address; 3)
According to the new destination address in the datagram (the public address of the router R2), the router R2 of the private network B can Receive the datagram;
4) The R2 router decrypts the datagram to obtain the original internal IP datagram, and then obtains the original source address and destination address, and finally sends the datagram to the host corresponding to the destination address;
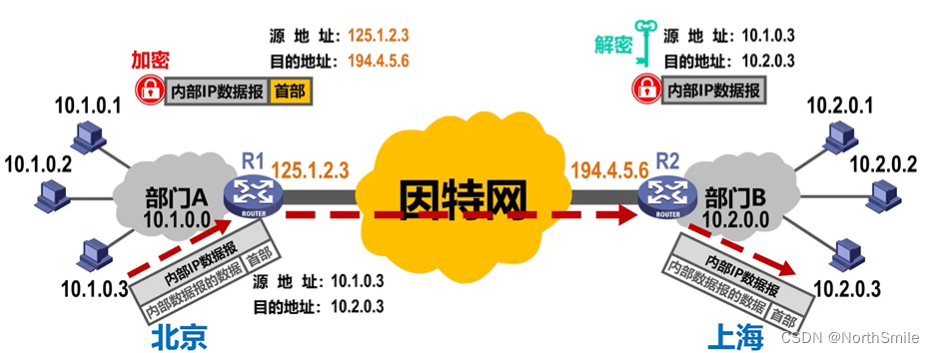
- IP tunneling technology: Communication between private networks requires the use of the public Internet as an information carrier. The transmission process may pass through many different networks and routers, but logically there is a direct point-to-point link between private networks, so it is also called For IP tunneling technology ;

9. Network Address Translation NAT
9.1 Network Address Translation NAT
- NAT:Network Address Translation;
- Purpose: To alleviate the problem that the IPv4 address space is about to be exhausted ;
- Effect: A large number of private network users using internal private addresses can share a small number of external global addresses to access hosts and resources on the Internet ;
- Disadvantage: If the NAT router has only N global IP addresses, there can only be at most N intranet hosts that can communicate with hosts on the Internet at the same time ;
- NAT software is installed in the router connected to the Internet in the private network. Such a router is called a NAT router and has at least one valid external global IP address;
- The basic working process of NAT:
1) The key lies in the translation of the internal network address and the external address: when the internal network sends data, it needs to convert the internal network address to the external address (source address), and when the internal network receives data, it needs to convert the external address to the internal address. Network address (destination address);
2) The translation work is completed by the NAT router by looking up the internal translation table;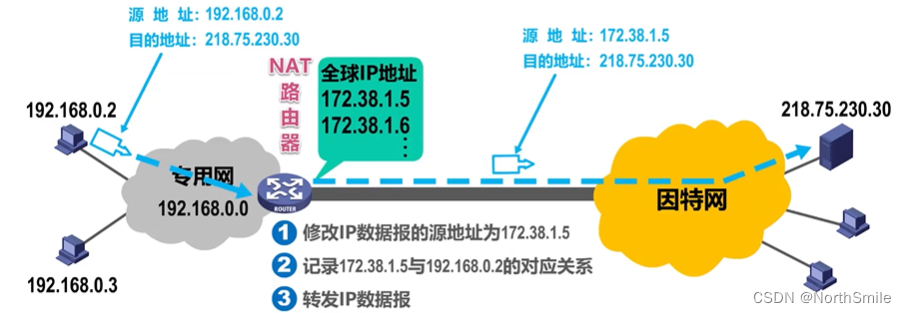
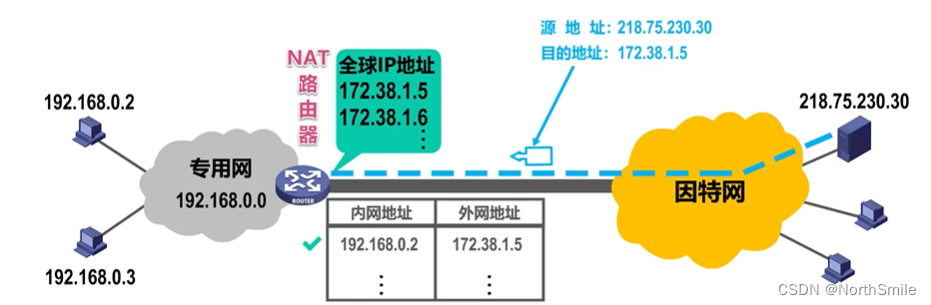
9.2 Network address and port number conversion NAPT
- NAPT:Network Address and Port Translation;
- Purpose: To solve the shortcomings of NAT;
- Solution: convert the port number and IP address of the transport layer together ;
- Effect: Multiple intranet hosts using the same external global IP address can communicate with hosts on the Internet at the same time ;
- The basic workflow is similar to that of NAT, the difference is that the records in the NAPT translation table include both IP addresses and port numbers;
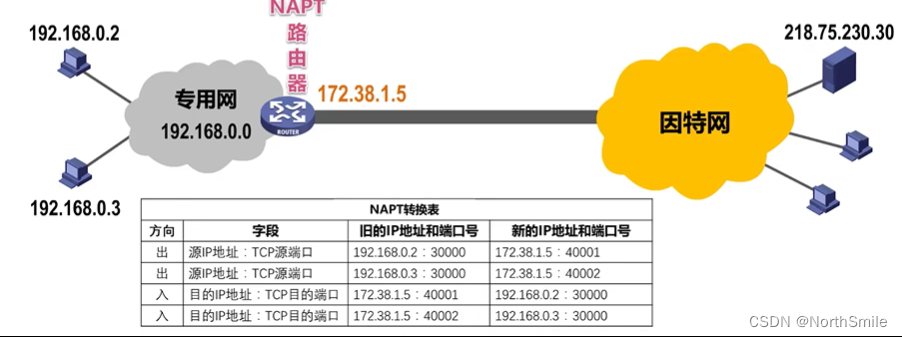
9.3 Precautions
- 1) Generally, hosts on the external network cannot actively initiate communication with hosts on the internal network, so internal hosts cannot directly act as Internet servers ! For some P2P network applications, external network hosts need to actively initiate communication to internal network hosts, and at this time there will be problems when performing NAT. To establish communication, network applications need to use special NAT penetration technology to achieve! !
- 2) Since NAT shields the network address of the internal network host from the external network, it can provide certain security protection for the internal network host! !
Reference: "Computer Network Micro Classroom"