vertical overreach
An office system ordinary user privileges are elevated to system privileges
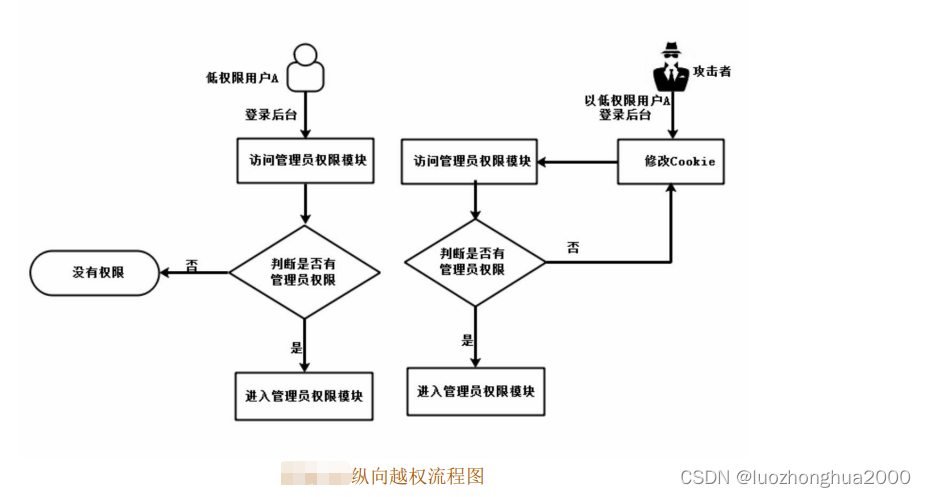
In order to identify the client browser session and identity information, the server will store the user identity information in the cookie and send it to the client for storage. The attacker attempts to modify the identity in the cookie to be an administrator, tricking the server into assigning administrator privileges, and achieves the purpose of vertical escalation, as shown in the figure. There is a vertical overreach vulnerability in an office system. By modifying cookies, the privileges of ordinary users can be directly upgraded to system privileges.
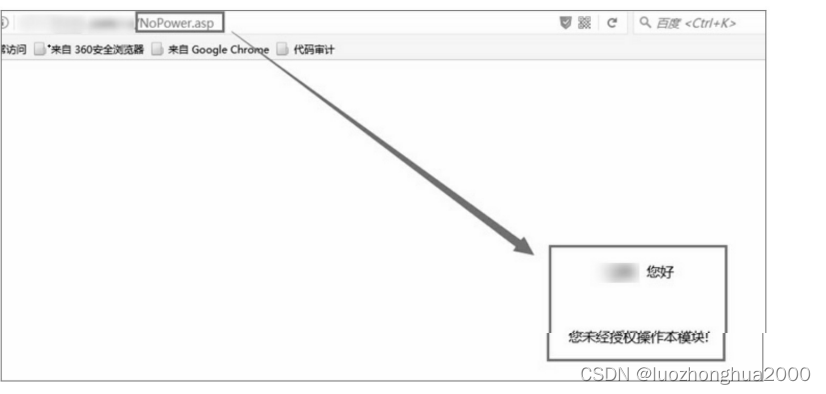
Step 1: Log in to the office system with the account a02 with normal authority. After successful login, visit the link http://host/aaa/bbb/editUser.asp?iD=2 and try to modify the authority. Since ordinary users cannot access the modification authority module, the system will jump to the NoPower page to prompt the user to have no operation authority, as shown in the figure.
Step 2: Use Burp Suite to modify the Tname parameter in the cookie to admin, trick the server that the request is sent by the system administrator, and successfully upgrade account a02 to the system administrator, as shown in the figure.

Step 3: Modify the modifyuser page with access rights again http://host/aaa/bbb/editUser.asp?iD=2, as shown in the figure, it can be accessed successfully.