Email Account Compromise Incident
The e-mail business is based on the information transmission business of computers and communication networks. It uses electrical signals to transmit and store information, and transmits various types of information such as electronic letters, digital faxes of files, images and digital voices for users. The biggest feature of e-mail is that people can receive and send letters anywhere and at any time, which solves the limitation of time and space, greatly improves work efficiency, and provides great convenience for office automation and business activities. However, leaked email accounts will also lead to a large amount of information leakage.
Information Leakage Caused by Email Account
Step 1: As shown in the figure, use a search engine to search for a company’s files on the Internet

Step 2: download the XLS file, obtain the email account password of a certain enterprise employee from the file, and successfully log in to the email system as shown in the figure.
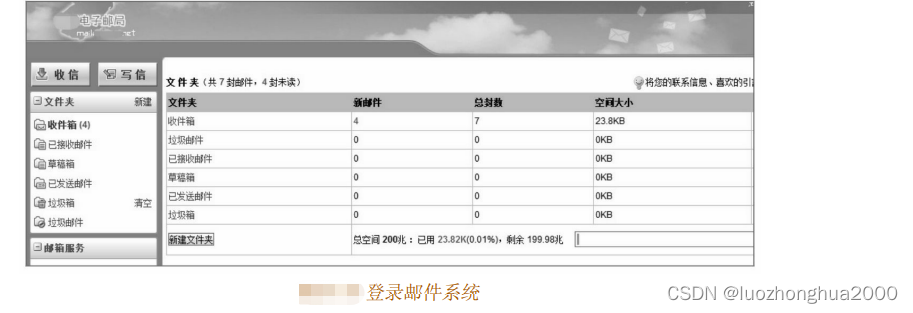
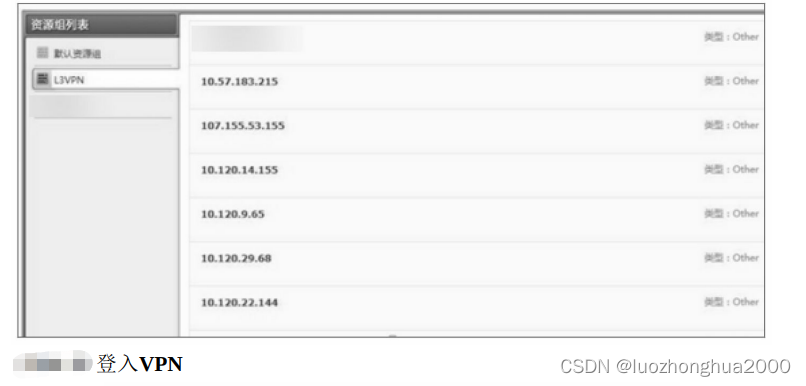
Step 2: Some information about the company was found in an email, including VPN login address, OA system, and login methods of various intranet systems. The account password of the email can be used to log in to various intranet systems, thereby obtaining a large amount of sensitive data . As shown in the figure, you can successfully dial into the VPN and access the intranet system at will.
Step 4: As shown in the figure, after successfully logging in to the OA system, you can obtain the personal information of employees, including mobile phone numbers, ID cards, job descriptions, etc.