Author: JD Logistics Chen Wei
I. Introduction
In this article, we will focus on the improvement of system security quality and describe the practical process of functional security testing & security penetration testing .
I hope this article will help you gain a deeper and more thorough understanding of security testing.
2. Security Penetration Testing Practice
Security pre-scanning is mainly to identify white-box vulnerabilities and black-box vulnerabilities. For JSRC problems, vulnerabilities need to be discovered through penetration testing.
1. Safety test category
According to different stages and different test objects, security testing can be divided into: functional security testing and security penetration testing .
The following are the definitions and differences between the two:
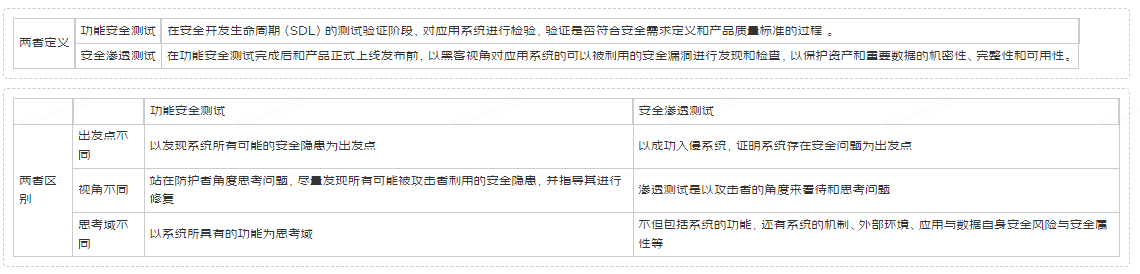
Specific content:
Functional Safety Testing:
In the functional testing stage, it is carried out by test engineers of each business line, mainly including the following aspects:
• Personnel permission setting, whether it meets the description in the requirements document:
1). Whether all roles are initialized;
2). Whether each role is configured according to the minimum authority;
• Authority testing: horizontal override, vertical override, cross override;
• Whether the handling of sensitive information complies with regulations;
1). Encrypted storage;
2). Display shielding;
3). Desensitized export;
4). Operation safety log records;
Security penetration testing:
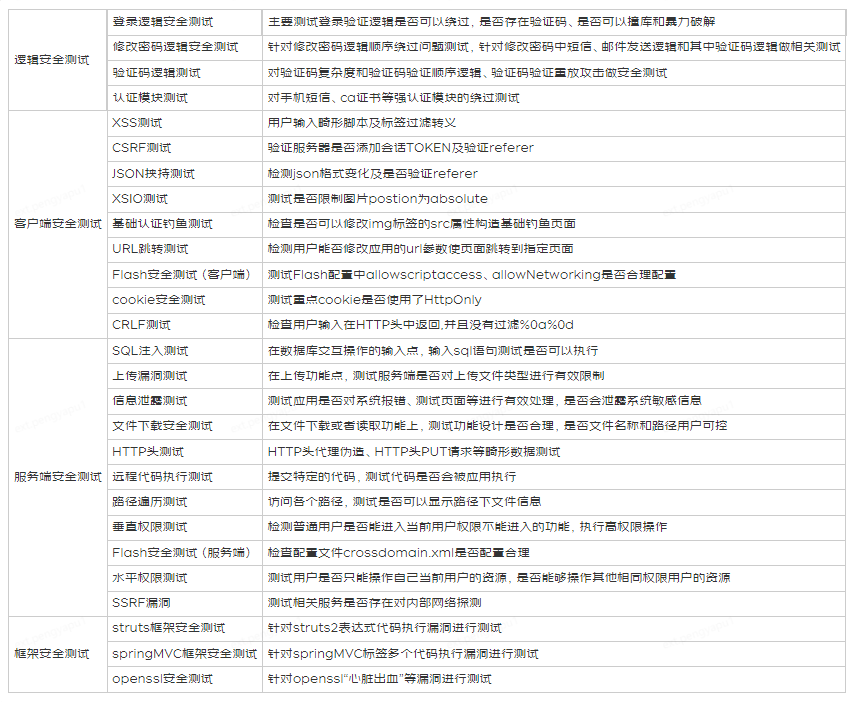
1. Functional safety test
(1) Carry out functional safety testing
Step1: Determine whether the project needs a security review
Reference standard (source safety department):
• The company's key strategic projects
• New extranet system
• Intranet system used by a large number of external personnel (recommended more than 15 people)
• Contains important commercial secrets, special sensitive systems;
• Newly purchased Party B projects or outsourced projects;
• The above types of systems are undergoing major upgrades.
Step2: Carry out security testing based on the SDL process:
Step3: Functional safety testing in the testing phase:
Security Use Case Design -> Test Execution -> Vulnerability Report
Step4: Submit penetration test before going online
(2) Functional safety is carried out in the project
Carry out functional safety testing during the SDL testing phase:
① Determine the test plan : functional safety test, security penetration test, code white box scanning, application black box scanning.
②Safety use case design
**③Functional security use cases: **Based on function points, use case design is carried out from the dimensions of authority control, ultra vires, and data.
Submit security penetration testing before SDL goes online.
2. Security penetration testing
(1) Carry out penetration testing
Step1: Use the test tool:
• BurpSuite installation:
Download address: https://portswigger.net/burp/communitydownload
Proxy SwitchyOmega (proxy plugin): Proxy plugin download address
• Browser proxy configuration:
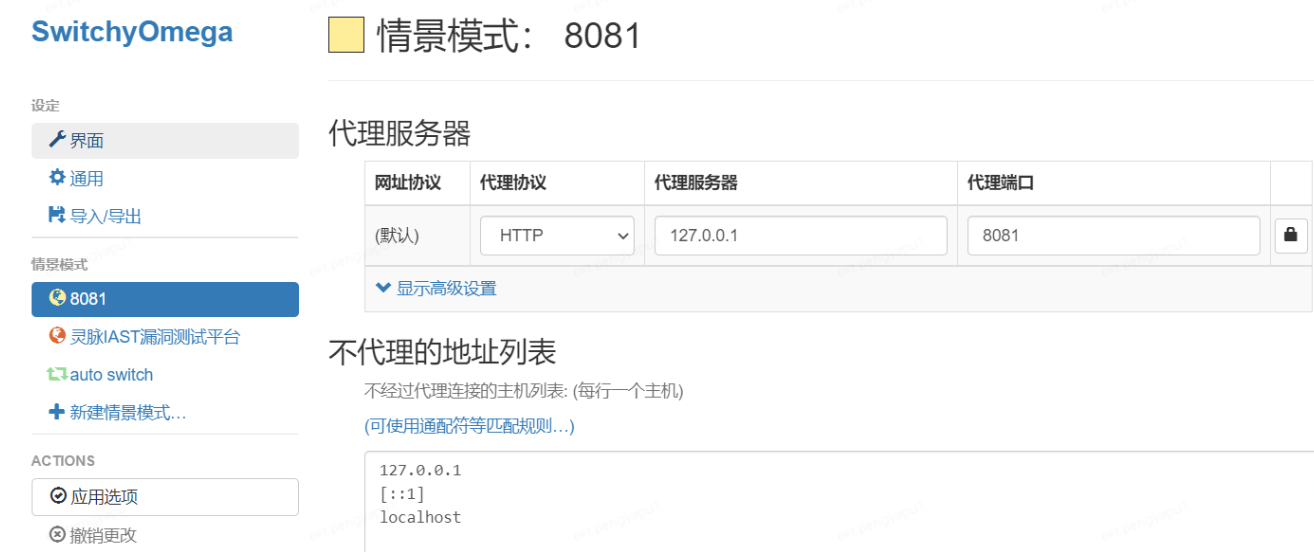
• BurpSuite -Proxy monitoring configuration:

• BurpSuite uses:
The browser enables Proxy for proxying, and data capture through BurpSuite:
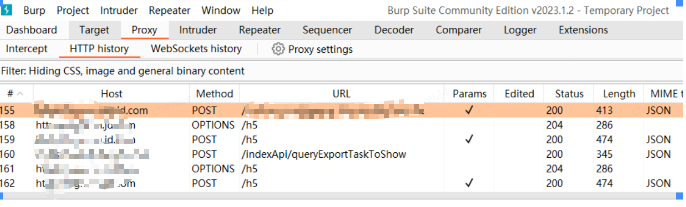
Proxy-Repeater retransmits the request packet:
Proxy-Intruder conducts violent blasting:
Select variable parameters--parameterization--batch resend request--result acquisition analysis.
Step2: Test execution
Step3: Organize the report
(2) Common vulnerability testing
permission bypass
Definition: It means that the authority control function is not rigorous, and system users can access or operate unauthorized functions or data.
Horizontal unauthorized access scenario: When there are multiple users with the same authorization in the system, user A accesses or operates the resources of user B without authorization.
Vertical overprivilege scenario: When users with different permissions exist in the system, low-privileged users access or operate resources of high-privileged users without authorization.
Unauthorized access: Users can directly access pages or information that require authentication without authorization.
A large amount of proof information was submitted:
SSRF (Server Side Request Forgery)
Definition: The attacker constructs the request and the server initiates the security vulnerability of the request. The target of the SSRF attack is the internal system that cannot be accessed by the external network (because the request is initiated by the server, the server can request to connect to itself and connect with internal system isolated from the external network).
Stored XSS Vulnerabilities
Definition: Cross-site scripting attack is a security vulnerability attack technology for website applications, and it is a type of code injection. Allow malicious users to inject code into web pages, and other users will be affected when browsing the web pages. After a malicious user exploits XSS code to attack successfully, it is likely to obtain very high authority.
XSS is divided into: reflection type, storage type, DOM type.
3. Summary
This article mainly describes the definition, difference, development plan, and practical examples of functional safety testing & security penetration testing.
These two security tests can be carried out during the SDL process of the project, and at the same time, the security penetration test can also be taken out separately, and the penetration test is specially conducted for the internal and external network systems of the group.
Through such a test, the number of white hat issues missed outside JSRC can be reduced.